Glossary
A space to share our views and insights on the industry.
Infrastructure Kickbacks and Laundering via Public Works
Definition
Infrastructure kickbacks and laundering via public works refer to the misuse of large-scale government-funded infrastructure projects — such as road construction, public housing, water systems, or digital connectivity programmes — as vehicles for bribery, embezzlement, and money laundering. In this typology, public officials and private contractors collude to inflate project costs, manipulate procurement processes, and channel illicit profits through complex financial transactions that disguise the true origin of funds.
Public infrastructure projects in Southeast Asia and Australia involve billions of dollars annually, creating an environment vulnerable to corruption and financial crime. When oversight gaps or opaque procurement systems exist, these projects become ideal channels for siphoning public funds and reintegrating them into the legitimate economy. The schemes often operate under the guise of legitimate payments to contractors, consultants, or subcontractors, masking kickbacks and illicit enrichment as normal business expenses.
This typology is not limited to developing economies. Even in advanced jurisdictions like Singapore and Australia, corruption risks persist through subcontracting networks, shell companies, and professional enablers who facilitate fund layering. The complexity of public works — involving multiple agencies, cross-border suppliers, and high transaction volumes — allows bad actors to exploit loopholes in procurement oversight and anti-money laundering controls.
How It Works (Modus Operandi)
At its core, this typology blends public-sector corruption with financial system exploitation. It typically follows a multi-stage process:
1. Procurement Capture and Tender Manipulation
The process begins with collusion between public officials and contractors to secure inflated tenders or exclusive contracts. Officials in charge of tender design, bidding, or approval manipulate criteria to favour pre-selected firms. In some cases, project budgets are padded during the planning phase, ensuring excess funds that can later be diverted.
In the Philippines, investigations into flood control and road improvement projects have revealed the use of ghost contractors — paper entities created to win bids and issue fake invoices for work never performed. These entities are often registered under relatives or associates of public officials, allowing the diversion of millions in public funds.
In Malaysia, procurement capture has been linked to politically connected contractors who dominate bidding for infrastructure works. Reports have highlighted inflated pricing for highway and public transport projects, with excess funds funnelled through consultancy fees and overseas accounts.
2. Use of Intermediary and Shell Entities
Once contracts are awarded, payments flow to legitimate contractors who then distribute portions to shell subcontractors or consultants. These intermediaries issue invoices for fabricated or overpriced services. The layering process begins here — funds are moved through multiple accounts, disguised as payments for materials, design work, or logistics.
In Singapore, while public procurement integrity remains high, vulnerabilities arise from cross-border subcontractors involved in foreign development projects. Offshore companies, especially those registered in low-tax jurisdictions, can act as fronts for laundering proceeds through consultancy payments or licensing fees.
In Australia, regulators have identified cases where contractors transferred funds to “associated entities” under the pretext of equipment leasing or subcontracting, masking the real flow of bribes. These transactions often involve large cash withdrawals, transfers to personal accounts, or conversions into real assets like vehicles and properties.
3. Integration of Illicit Proceeds
The final stage involves integrating the laundered funds into the legitimate economy. This can take the form of property investments, luxury asset purchases, or reinvestment into new business ventures. Some funds are recycled back into political campaigns or used to finance future projects, perpetuating a cycle of corruption and influence.
The Australian Federal Police have uncovered cases where kickbacks from regional construction projects were channelled through real estate investments in Sydney and Melbourne, using nominee owners to obscure beneficial ownership. Similarly, Philippine investigations have traced misappropriated infrastructure funds to casino junkets and offshore bank accounts, showing how illicit proceeds move fluidly between corruption and laundering typologies.

Red Flags / Risk Indicators
Financial institutions, auditors, and regulators play a crucial role in identifying anomalies tied to this typology. Common red flags and risk indicators include:
Transactional Red Flags
- Repeated payments to newly incorporated entities that have limited operational history or no online presence.
- Large payments classified as “consultancy,” “advisory,” or “subcontracting” services without clear supporting documentation.
- Round-number transactions or multiple payments just below reporting thresholds.
- Cross-border transfers to accounts in jurisdictions unrelated to the project’s scope.
- Frequent cash withdrawals following government disbursements or project payments.
- Unusual flow of funds between contractors, shell entities, and politically exposed persons (PEPs).
Behavioural and Operational Indicators
- Bidding patterns where a small group of companies repeatedly win public tenders.
- Similar language, formatting, or submission errors across different bidders, suggesting collusion.
- Family or business links between contractors and public officials involved in procurement.
- Rapid formation of subcontractors immediately before a project tender.
- Involvement of politically connected intermediaries or consultants with no technical role in the project.
Institutional Risk Factors
- Weak procurement oversight and insufficient post-award auditing.
- Decentralised project management structures that obscure accountability.
- Lack of beneficial ownership disclosure in contractor registration.
- Overreliance on paper-based or manual invoicing systems vulnerable to manipulation.
In Singapore, strong anti-corruption frameworks and digital procurement systems have mitigated several of these risks. However, financial institutions remain alert to foreign-linked transfers and politically exposed clients engaged in large-scale contracting.
In Malaysia and the Philippines, ongoing anti-corruption drives have revealed systemic issues, from weak supplier vetting to manipulation of project milestones.
In Australia, the integration of AML controls into public procurement compliance frameworks is improving, yet private contractors remain a high-risk node for laundering schemes.
Why It Matters (Industry Impact or Relevance)
The impact of infrastructure kickbacks and laundering via public works extends far beyond immediate financial loss. It erodes public trust, diverts funds from essential development, and undermines governance integrity. From an AML perspective, these schemes reveal how corruption and money laundering are intertwined, requiring cross-sector collaboration to detect and disrupt.
Economic and Reputational Costs
In the Philippines, the misuse of infrastructure funds in flood control and bridge projects has contributed to persistent development bottlenecks, while also fuelling public scepticism towards government spending. In Malaysia, scandals surrounding major transport projects have shaken investor confidence and triggered calls for procurement reform. Even in Australia, local government procurement audits have flagged conflicts of interest and weak contractor due diligence, highlighting vulnerabilities in mature economies.
Regulatory and Compliance Implications
For financial institutions, the typology underscores the importance of identifying corruption-linked laundering. Transactions linked to infrastructure contracts may appear legitimate but can conceal illicit activity. Banks and payment providers must enhance their risk assessment of clients involved in public-sector contracting, particularly those dealing with high-value projects, cash-intensive transactions, or politically exposed entities.
Regulators in Singapore and Australia have emphasised the need for beneficial ownership transparency and enhanced due diligence for government-linked payments. Meanwhile, initiatives in the Philippines and Malaysia are focusing on digital procurement platforms and e-payment monitoring to improve traceability and reduce human discretion in tender processes.
A Growing Regional Priority
Across the region, public infrastructure spending is accelerating — from the Philippines’ “Build Better More” initiative to Malaysia’s new transport corridors and Australia’s renewable energy projects. As investment scales up, so too does the incentive for illicit actors to capture these funds. The cross-border nature of supply chains and financial transactions makes collaborative intelligence essential to prevention.
The AFC Ecosystem and similar industry collectives play an important role in sharing red flags, typologies, and real-world scenarios that bridge the gap between anti-corruption enforcement and AML compliance. By democratising access to intelligence on how such schemes operate, financial institutions can strengthen early detection and prevent the integration of corrupt proceeds into legitimate channels.
Conclusion
Infrastructure kickbacks and laundering via public works exemplify how corruption, procurement fraud, and financial crime converge in high-value, high-impact sectors. For compliance professionals, detecting such schemes requires not only transactional vigilance but also contextual understanding — of who is being paid, for what purpose, and through which intermediaries.
As countries like Singapore, Malaysia, the Philippines, and Australia continue to invest heavily in infrastructure, this typology serves as a critical reminder: every road, bridge, or power plant is not just an economic asset — it’s a potential test of integrity, governance, and accountability. Strengthening financial oversight, data-sharing, and scenario-based monitoring is the surest path to ensuring that public wealth is protected from private corruption.
Tornado Cash
Introduction
In an era where financial privacy is increasingly valued, Tornado Cash has emerged as a powerful tool for preserving anonymity in cryptocurrency transactions. Tornado Cash leverages the principles of decentralization and cryptographic technology to provide users with a reliable and secure method of obfuscating their digital asset transactions.
In this article, we will explore the concept of Tornado Cash, its unique features, and its implications for privacy-conscious individuals in the cryptocurrency space. Let's dive into the world of Tornado Cash and unlock the potential of decentralized privacy.
Key Takeaways
- Tornado Cash is a decentralized privacy solution for cryptocurrency transactions.
- It offers trustless and non-custodial privacy through the use of smart contracts and anonymity pools.
- Tornado Cash provides financial privacy, protects against surveillance and tracking, and enhances the fungibility of cryptocurrencies.
- Users can access the Tornado Cash interface, deposit and withdraw funds, and should be aware of gas fees and transaction confirmation times.
- Regulatory considerations, such as OFAC compliance, and diversifying privacy options are crucial when using Tornado Cash.
- The Tornado Cash ecosystem includes the TORN token, support on various blockchains, and integration partnerships.
Introducing Tornado Cash: Understanding the Need for Privacy in Cryptocurrency Transactions
Tornado Cash addresses the growing demand for financial privacy in the cryptocurrency space. It allows users to obfuscate their transaction history and retain their anonymity while engaging in digital asset transfers. Privacy-focused tools like Tornado Cash raise concerns about money laundering risks, requiring enhanced due diligence (EDD) for users.
How Tornado Cash Works: Unveiling the Decentralized Privacy Protocol
- Trustless and Non-custodial Nature: Tornado Cash operates in a trustless and non-custodial manner, ensuring that users retain full control of their funds throughout the process.
- The Role of Smart Contracts: Tornado Cash utilizes smart contracts, particularly zero-knowledge proofs, to achieve privacy without requiring users to disclose sensitive information.
- The Anonymity Pool Concept: Tornado Cash pools users' funds together, making it difficult to trace individual transactions, thereby preserving privacy.
Benefits of Tornado Cash: Exploring the Advantages of Decentralized Privacy
- Preserving Financial Privacy: Tornado Cash allows users to shield their transaction history, protecting their financial privacy from prying eyes.
- Protecting against Surveillance and Tracking: By obfuscating transaction trails, Tornado Cash helps users mitigate the risk of surveillance and tracking by third parties.
- Ensuring Fungibility of Cryptocurrencies: Tornado Cash enhances the fungibility of cryptocurrencies by making individual tokens indistinguishable from one another, ensuring they are equally interchangeable.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Tornado Cash in Action: Navigating the Process of Privacy-enhanced Transactions
- Accessing the Tornado Cash Interface: Users can access the Tornado Cash interface through supported wallets and connect to compatible networks.
- Depositing and Withdrawing Funds: The process involves depositing funds into the anonymity pool and later withdrawing them while maintaining privacy.
- Understanding Gas Fees and Transaction Confirmation Times: Users should be aware of gas fees associated with their transactions and the time required for confirmation on the blockchain network.
Tornado Cash and Regulatory Considerations: OFAC Compliance and Alternatives
- OFAC Compliance and Mitigating Risks: Users must be mindful of regulatory compliance and potential risks associated with using Tornado Cash, particularly regarding Office of Foreign Assets Control (OFAC) requirements.
- Exploring Alternatives and Diversifying Privacy Options: Users may consider diversifying their privacy-enhancing strategies by exploring alternative privacy solutions and combining different protocols.
Tornado Cash and Its Ecosystem: Insights into the Tornado Cash Coin
- The Role of TORN Tokens: TORN is the native governance token of Tornado Cash, allowing holders to participate in the protocol's decision-making process.
- Tornado Cash on Different Blockchains: Tornado Cash operates on multiple blockchains, providing users with flexibility and options for their privacy needs.
- Tornado Cash Integrations and Partnerships: The protocol actively seeks integrations and partnerships to expand its reach and offer enhanced privacy features to a wider user base.
Coupon Fraud
Introduction
Coupons have long been a popular method for consumers to save money on their purchases. However, where there are opportunities for savings, there are also those who seek to exploit them. Coupon fraud is a deceptive practice that undermines the integrity of the couponing system and poses significant challenges for retailers, manufacturers, and consumers alike.
In this article, we delve into the world of coupon fraud, examining its various forms, the consequences it entails, and the measures taken to combat this illicit activity.
Key Takeaways
- Coupon fraud affects manufacturers, retailers, and consumers alike. It leads to financial losses for businesses and erodes consumer trust in the couponing system.
- Coupon fraud can take multiple forms, including counterfeiting coupons, altering valid coupons, and using coupons on products for which they are not intended (known as coupon glittering).
- Engaging in coupon fraud is illegal and can result in fines, imprisonment, and a criminal record. The severity of the punishment varies depending on the jurisdiction and the scale of the fraud.
- To combat coupon fraud, manufacturers are continually enhancing security features on coupons, such as unique barcodes, holograms, and watermarks.
- Retailers and consumers play a crucial role in combating coupon fraud. Retailers are implementing point-of-sale systems that can detect fraudulent coupons, while consumers are encouraged to verify the authenticity of coupons and understand their terms and conditions.
Understanding Coupon Fraud
Coupon fraud encompasses a range of deceptive practices aimed at obtaining discounts or benefits that individuals are not entitled to. It can involve counterfeiting coupons, altering valid coupons, using expired coupons, or misrepresenting product purchase requirements. Fraudsters employ various techniques to manipulate the couponing system, costing manufacturers and retailers millions of dollars each year.
Examples of Coupon Fraud
- Counterfeiting Coupons: Fraudsters create fake coupons that resemble legitimate ones, often using advanced graphic design software. These counterfeit coupons can be distributed online or through illicit channels, deceiving both retailers and consumers.
- Coupon Glittering: Also known as "code stripping," this form of fraud involves using coupons on products for which they are not intended. By exploiting coding loopholes in the coupon system, fraudsters can use coupons on items other than those specified, leading to improper discounts.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Impacts of Coupon Fraud
Coupon fraud has far-reaching consequences for all parties involved. Let's explore some of the key impacts:
- Financial Losses: Coupon fraud costs manufacturers and retailers substantial financial losses. Fraudulent redemptions drain revenue, disrupt inventory management, and erode profitability.
- Consumer Trust: Coupon fraud erodes consumer trust in the couponing system. When individuals encounter fake or invalid coupons, it diminishes their confidence in the effectiveness and fairness of legitimate coupons.
Legal Implications of Coupon Fraud
Coupon fraud is not only unethical but also illegal. Engaging in coupon fraud can result in serious legal consequences, including fines, imprisonment, and criminal records. While the severity of the punishment may vary depending on the jurisdiction and the scale of the fraud, it is essential to understand that coupon fraud is a punishable offence.
Notorious Coupon Fraud Cases
One notable coupon fraud case is that of Lori Ann Talens, who masterminded a large-scale counterfeit coupon operation. Talens created fake coupons and sold them online, resulting in significant financial losses for manufacturers. Her case highlighted the impact of coupon fraud and the need for robust measures to combat such criminal activities.
Combating Coupon Fraud
Coupon fraud is a pervasive issue that requires the collective effort of manufacturers, retailers, and consumers to combat it effectively. Here are some measures taken to address coupon fraud:
Advanced Coupon Security Features
Manufacturers continually enhance coupon security features, making them harder to counterfeit or misuse. These may include unique barcodes, holograms, watermarks, or embedded security threads.
Retailer Vigilance
Retailers play a crucial role in combating coupon fraud by training their employees to recognize counterfeit or altered coupons. Additionally, implementing point-of-sale systems that can detect fraudulent coupons helps prevent their redemption.
{{cta('bdd96089-cde2-43f3-95a3-3f6d7b74af38','justifycenter')}}
Conclusion
Coupon fraud is a detrimental practice that undermines the integrity of the couponing system, causing financial losses to manufacturers and eroding consumer trust. The consequences of engaging in coupon fraud can be severe, both legally and reputationally. It is crucial for individuals to understand the ethical and legal implications associated with coupon fraud and support efforts to combat this illicit activity. By promoting awareness, implementing robust security measures, and fostering a culture of integrity, we can preserve the effectiveness and fairness of the couponing system. Manufacturers, retailers, and consumers must work together to combat coupon fraud and uphold the integrity of the couponing process.
While coupon fraud poses significant challenges, there are measures in place to address and mitigate this issue. Manufacturers are constantly improving the security features of coupons, making them more difficult to counterfeit or misuse. Unique barcodes, holograms, watermarks, and embedded security threads are just some of the advancements in coupon security.
Retailers also play a vital role in the fight against coupon fraud. They train their employees to identify counterfeit or altered coupons and implement point-of-sale systems that can detect fraudulent coupons. By maintaining vigilance and staying informed about emerging fraudulent tactics, retailers can prevent the redemption of fake coupons and protect their business.
For consumers, it is essential to be vigilant and cautious when using coupons. Verify the authenticity of coupons before use, ensuring they are obtained from reputable sources. Familiarize yourself with the terms and conditions of coupons to avoid unintentional misuse. By practicing responsible couponing, consumers can help prevent the perpetuation of coupon fraud.
In conclusion, coupon fraud is a deceptive practice that undermines the integrity of the couponing system. It leads to financial losses for manufacturers, erodes consumer trust, and carries legal implications. Through collaborative efforts between manufacturers, retailers, and consumers, we can combat coupon fraud and maintain the effectiveness and fairness of the couponing process. By promoting awareness, implementing robust security measures, and exercising responsible couponing practices, we can protect the integrity of the couponing system and ensure its benefits for all stakeholders involved.
Frequently Asked Questions
What is Coupon Fraud?
Coupon fraud involves deceptive practices aimed at obtaining unauthorized discounts or benefits. This can include counterfeiting coupons, altering valid coupons, or using expired coupons.
What are Some Examples of Coupon Fraud?
Examples include counterfeiting coupons, altering the terms on valid coupons, and "coupon glittering," which involves using coupons on products for which they are not intended.
What are the Financial Impacts of Coupon Fraud?
Coupon fraud leads to significant financial losses for manufacturers and retailers. It disrupts inventory management and can erode profitability.
What are the Legal Implications of Coupon Fraud?
Coupon fraud is illegal and can result in fines, imprisonment, and a criminal record. The severity of the punishment can vary depending on the jurisdiction and the scale of the fraud.
How Can Coupon Fraud be Prevented?
Prevention measures include advanced security features on coupons, retailer vigilance in identifying fraudulent coupons, and consumer awareness about the terms and conditions of coupon use.
FedRAMP
Introduction
As government agencies increasingly embrace cloud computing, ensuring the security and integrity of sensitive data becomes paramount. The Federal Risk and Authorization Management Program (FedRAMP) has emerged as a crucial framework for evaluating and authorizing cloud service providers (CSPs) to ensure they meet rigorous security standards.
In this article, we will delve into the world of FedRAMP, understand its compliance requirements, explore the certification process, and examine the key controls that CSPs must adhere to. Let's explore the vital aspects of FedRAMP and its significance in safeguarding sensitive government data. In the realm of cloud security, compliance with FedRAMP standards is crucial to avoid operational risk and potential breaches.
Key Takeaways
- FedRAMP sets rigorous security standards for cloud service providers seeking authorization to handle federal data.
- Compliance with FedRAMP controls, mapping to NIST 800-53, and continuous monitoring are essential requirements.
- The certification process involves documentation, engagement with a 3PAO, and submission of the authorization package.
- The approved list and FedRAMP Marketplace showcase authorized CSPs for government agencies.
- FedRAMP compliance offers enhanced security, cost reduction, efficiency gains, and expanded business opportunities.
Introducing FedRAMP: Defining Compliance for Cloud Service Providers
FedRAMP is a government-wide program that standardizes the security assessment, authorization, and continuous monitoring of cloud services. Its objective is to provide a consistent and risk-based approach to ensure the security and privacy of federal data stored and processed in cloud environments.
Understanding FedRAMP Compliance: Key Requirements and Guidelines
- FedRAMP Controls Framework: The FedRAMP controls framework outlines the security controls that CSPs must implement and document in their systems. These controls align with the National Institute of Standards and Technology (NIST) Special Publication 800-53.
- Mapping Security Controls to NIST 800-53: CSPs must demonstrate how they meet the security control requirements outlined in NIST 800-53, which covers various security domains such as access control, incident response, and system integrity.
- Continuous Monitoring and Assessment: FedRAMP requires CSPs to implement continuous monitoring practices to ensure ongoing compliance with security requirements. Regular assessments, audits, and reporting are essential elements of this process.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The FedRAMP Certification Process: Navigating the Authorization Journey
- Documentation and System Security Plan (SSP): CSPs are required to create a System Security Plan (SSP) that documents their security controls, processes, and procedures. This plan serves as the foundation for the certification process.
- Third-Party Assessment Organization (3PAO) Engagement: CSPs engage with a FedRAMP-accredited 3PAO to conduct an independent assessment of their systems and security controls. The 3PAO evaluates the implementation of security controls and provides an assessment report.
- FedRAMP Authorization Package Submission: CSPs compile the necessary documentation, including the SSP, assessment report, and other supporting materials, and submit the FedRAMP authorization package for review by the Joint Authorization Board (JAB) or an agency-specific authorizing official.
The Approved List and the FedRAMP Marketplace: Showcasing Trusted Cloud Service Providers
The FedRAMP Program Management Office maintains an approved list of cloud service offerings that have successfully achieved FedRAMP compliance. This list serves as a resource for government agencies to identify and select trusted CSPs. Additionally, the FedRAMP Marketplace provides a platform for CSPs to showcase their authorized offerings.
FedRAMP in Action: Realizing the Benefits of Compliance
- Enhanced Security and Risk Management: FedRAMP compliance ensures robust security measures, risk management practices, and continuous monitoring, reducing the risk of data breaches and unauthorized access.
- Cost Reduction and Efficiency Gains: FedRAMP streamlines the authorization process, allowing CSPs to reuse security assessment artifacts across multiple agencies, reducing duplication efforts and costs.
- Expansion of Business Opportunities: Achieving FedRAMP compliance opens doors to lucrative opportunities in the government sector, as agencies prioritize authorized CSPs for their cloud computing needs.
Frequently Asked Questions
What is FedRAMP and what is its purpose?
FedRAMP is a government-wide program that standardizes the security assessment, authorization, and continuous monitoring of cloud services for the protection of federal data stored and processed in the cloud.
What are the key requirements and guidelines for FedRAMP compliance?
The FedRAMP controls framework outlines the security controls that Cloud Service Providers (CSPs) must implement, which align with the NIST 800-53 standards.
How does the FedRAMP certification process work?
The FedRAMP certification process involves creating a System Security Plan (SSP), engaging with a FedRAMP-accredited third-party assessment organization (3PAO) for an independent assessment, and submitting the authorization package for review.
What is the significance of the approved list and the FedRAMP Marketplace?
The approved list maintained by the FedRAMP Program Management Office helps government agencies identify and select trusted CSPs, while the FedRAMP Marketplace allows CSPs to showcase their authorized offerings.
What are the benefits of achieving FedRAMP compliance?
FedRAMP compliance ensures enhanced security and risk management, cost reduction through streamlined authorization processes, and increased business opportunities in the government sector.
Wire Fraud
Introduction
Wire fraud has become a prevalent form of cybercrime that poses significant risks to individuals, businesses, and financial institutions. Perpetrators of wire fraud employ various deceptive tactics to manipulate victims into wiring funds or providing sensitive information for illicit purposes.
In this article, we will delve into the realm of wire fraud, understand its implications, explore the legal framework surrounding it, and discuss proactive measures to prevent and report such fraudulent activities. Robust wire fraud prevention measures include identity verification, phishing awareness, and suspicious activity reporting.
Key Takeaways
- Wire fraud involves deceptive tactics to manipulate victims into wiring funds or providing sensitive information.
- Wire fraud is a felony offence, punishable by fines and imprisonment.
- Law enforcement agencies such as the FBI, U.S. Secret Service, and FinCEN play a crucial role in investigating wire fraud.
- Protect yourself from wire fraud by strengthening cybersecurity practices, recognizing common red flags, and educating yourself and your employees.
- Report instances of wire fraud to the FBI through the IC3 platform and coordinate with your financial institution.
Understanding Wire Fraud: Unveiling the Threat Landscape
Wire fraud involves the use of electronic communications or wire transfers to deceive victims into providing money, sensitive information, or other valuable assets to fraudulent entities. Perpetrators often employ social engineering techniques, phishing emails, or compromised communication channels to manipulate victims.
The Legal Landscape: Wire Fraud and its Consequences
- Wire Fraud as a Felony: Wire fraud is a federal crime in the United States and is classified as a felony. It carries severe penalties, including fines and imprisonment, depending on the nature and scale of the fraudulent activity.
- Wire Fraud Statute and Prosecution: The wire fraud statute is encompassed within Title 18, Section 1343 of the United States Code. It provides the legal framework for prosecuting individuals engaged in wire fraud.
- Punishment for Wire Fraud: The punishment for wire fraud varies depending on several factors, such as the amount of money involved, the level of sophistication, and the impact on victims. Convicted individuals may face substantial fines and imprisonment, often exceeding several years.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Investigating Wire Fraud: The Role of Law Enforcement Agencies
- Federal Bureau of Investigation (FBI): The FBI is a primary federal law enforcement agency responsible for investigating and combating various cybercrimes, including wire fraud. They collaborate with other agencies and coordinate efforts to apprehend and prosecute fraudsters.
- U.S. Secret Service: While primarily known for protecting high-ranking officials, the U.S. Secret Service also investigates financial crimes, including wire fraud. They focus on cases involving counterfeit currency, financial institution fraud, and computer crimes.
- Financial Crimes Enforcement Network (FinCEN): FinCEN is a bureau of the U.S. Department of the Treasury that collects and analyzes financial transaction data to combat money laundering, terrorist financing, and other financial crimes. They work in conjunction with other agencies to identify patterns and track illicit funds.
Read More: Understanding Social Security Fraud and Its Impact on Society
Protecting Yourself from Wire Fraud: Proactive Measures
- Strengthening Cybersecurity Practices: Implement robust cybersecurity measures, including multi-factor authentication, encryption, and regular software updates. Conduct regular employee training on recognizing and preventing wire fraud.
- Recognizing Common Red Flags: Be vigilant for warning signs of wire fraud, such as unsolicited requests for money or personal information, suspicious email addresses or phone numbers, and urgent requests for immediate wire transfers.
- Educating Yourself and Employees: Stay informed about the latest techniques used in wire fraud and educate yourself and your employees about potential threats. Encourage a culture of cybersecurity awareness and promote a proactive approach to fraud prevention.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Reporting Wire Fraud: Taking Action Against Fraudsters
- Reporting to the FBI: If you fall victim to wire fraud, report the incident to the FBI through their Internet Crime Complaint Center (IC3) website. Provide all relevant details and evidence to aid in their investigation.
- Utilizing the Internet Crime Complaint Center (IC3): The IC3 is a partnership between the FBI, the National White Collar Crime Center (NW3C), and the Bureau of Justice Assistance (BJA). It serves as a central hub for reporting cybercrimes, including wire fraud.
- Coordinating with Financial Institutions: Notify your financial institution immediately if you suspect wire fraud. They can assist in freezing accounts, recovering funds if possible, and launching their internal investigations.
Read More: Cyber Fraud: Real-Life Examples and Prevention Strategies
Impersonation
Introduction
In today's digital age, where online interactions are increasingly common, the risk of impersonation has become a pressing concern. Impersonation refers to the act of pretending to be someone else with the intent to deceive or defraud others. Whether it's assuming another person's identity online or imitating a public figure, impersonation can have serious consequences for individuals and society as a whole.
This article delves into the world of impersonation, shedding light on its examples, the full meaning behind it, the act of impersonating, and the distinction between impersonation and impersonating. By understanding the intricacies of impersonation, we can better protect ourselves and navigate the digital landscape with vigilance.
Key Takeaways
- Impersonation involves intentionally assuming another person's identity with the intent to deceive, defraud, or harm others, often exploiting various mediums like social media, email, or phone calls.
- Impersonation can manifest in various forms, such as online identity theft, phishing scams, caller ID spoofing, and impersonating public figures. Techniques used by impersonators can range from social engineering to identity theft and spoofing.
- Impersonation poses significant risks, including financial loss, reputation damage, identity theft, and emotional distress. Legal consequences can include criminal charges, civil lawsuits, and actions by online platforms.
- While both terms are often used interchangeably, "impersonation" refers to the overarching concept, and "impersonating" focuses on the specific actions or behaviors involved in assuming another's identity.
- Individuals can protect themselves by strengthening online security, adjusting privacy settings, and verifying identities. Reporting impersonation incidents to law enforcement and online platforms is crucial for taking appropriate action.
What is Impersonation?
Impersonation involves assuming another person's identity or pretending to be someone you're not. It is an intentional act carried out with the motive to deceive, defraud, or harm others. Impersonators often utilize various mediums, such as social media platforms, email, or phone calls, to engage with their targets and manipulate them for personal gain. By adopting another person's identity, they aim to exploit trust, gain access to sensitive information, or carry out fraudulent activities.
The Meaning of Impersonation
The term "impersonation" refers to the act of assuming or mimicking the identity of another individual or entity. It involves deliberately portraying oneself as someone else, often with the intention to deceive, mislead, or manipulate others. Impersonation can occur in various contexts, both online and offline, and is driven by different motivations, ranging from financial gain to personal gratification or even malicious intent.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Examples of Impersonation
Impersonation can take many forms, and its examples are diverse. Some common instances of impersonation include:
- Online Identity Theft: Impersonating someone on social media or creating fake profiles to deceive others.
- Phishing Scams: Sending fraudulent emails or messages pretending to be a trusted entity to extract personal information.
- Caller ID Spoofing: Manipulating caller identification to make it appear as if the call is coming from a different person or organization.
- Impersonating Public Figures: Pretending to be a well-known personality, such as a celebrity or public official, to gain attention or spread false information.
- Business Impersonation: Presenting oneself as an employee or representative of a legitimate company to deceive customers or partners.
The Act of Impersonating: Delving Deeper
To understand the act of impersonating, it is essential to explore its underlying aspects. Impersonating involves more than just imitating someone's physical appearance or mannerisms. It requires a comprehensive understanding of the individual being impersonated, including their behaviours, communication style, and personal information.
Impersonators often invest time and effort in studying their targets to convincingly assume their identity. They may gather information from public sources, social media profiles, or even engage in social engineering tactics to gain access to sensitive details. The act of impersonating goes beyond mere imitation and involves a level of deception that can be highly sophisticated.
Impersonators may employ various techniques to enhance their impersonation, such as:
- Social Engineering: Manipulating individuals or situations to extract personal information or gain trust.
- Identity Theft: Stealing personal data, such as social security numbers or login credentials, to assume someone's identity.
- Spoofing: Falsifying digital footprints, such as IP addresses or email headers, to appear as someone else.
- Psychological Manipulation: Exploiting emotions, vulnerabilities, or relationships to deceive or control others.
By understanding the intricacies of the act of impersonating, individuals can be more vigilant and better equipped to identify and prevent potential impersonation attempts.
Impersonation vs. Impersonating: Understanding the Difference
While the terms "impersonation" and "impersonating" are often used interchangeably, there is a subtle distinction between the two. Impersonation refers to the overarching concept of assuming another person's identity, while impersonating focuses on the specific action or behavior of pretending to be someone else.
Impersonation can involve various activities, including creating fake profiles, assuming a false identity, or deceiving others by imitating someone's characteristics or traits. On the other hand, impersonating refers to the active engagement in the act of assuming another person's identity, whether online or in person, with the intent to deceive or defraud others.
Understanding this distinction is important as it helps us navigate discussions surrounding impersonation and enables clearer communication when addressing specific aspects of the practice.
The Risks of Impersonation
Impersonation poses significant risks to individuals, organizations, and society as a whole. Some key risks associated with impersonation include:
- Financial Loss: Impersonators may use stolen identities to carry out fraudulent financial transactions, leading to substantial monetary losses for victims.
- Reputation Damage: By impersonating someone, malicious actors can tarnish their target's reputation by engaging in illegal or unethical activities under their name.
- Identity Theft: Impersonation can result in the theft of personal information, which can be used for identity theft or further fraudulent activities.
- Privacy Invasion: Impersonators may intrude upon an individual's privacy by accessing their personal accounts, private messages, or confidential information.
- Emotional Distress: Being impersonated can cause significant emotional distress, including feelings of violation, betrayal, or powerlessness.
These risks highlight the importance of proactive measures to detect and prevent impersonation attempts, protecting individuals and organizations from potential harm.
Consequences of Impersonation
The consequences of impersonation can be severe, both legally and personally. Depending on the jurisdiction and the nature of the impersonation, the following consequences may apply:
- Legal Ramifications: Impersonation is considered a criminal offense in many jurisdictions, and perpetrators can face criminal charges, fines, and imprisonment if convicted.
- Civil Lawsuits: Impersonation victims may choose to pursue civil litigation to seek compensation for financial losses, damages to their reputation, or emotional distress.
- Online Platform Actions: Social media platforms, online marketplaces, and other digital platforms often have policies in place to address impersonation. Impersonators can face account suspension, content removal, or permanent bans from these platforms.
- Damage to Relationships: Impersonation can lead to strained relationships, trust issues, and the erosion of personal and professional connections. Victims may experience a breakdown in trust with friends, family, or colleagues who were deceived by the impersonation.
- Reputational Damage: Impersonation can have long-lasting effects on a person's reputation. The actions carried out by impersonators, especially if they involve illegal or unethical behaviour, can stain the reputation of the individual being impersonated. Rebuilding trust and repairing a damaged reputation can be a challenging and time-consuming process.
Protecting Yourself from Impersonation
While it may not be possible to completely eliminate the risk of impersonation, there are several measures individuals can take to protect themselves:
- Strengthen Online Security: Use strong, unique passwords for all online accounts and enable two-factor authentication when available. Regularly update software and be cautious of phishing attempts.
- Privacy Settings: Adjust privacy settings on social media platforms to restrict access to personal information and posts. Be mindful of the information shared publicly, as it can be used by impersonators for their advantage.
- Verify Identity: Be cautious when interacting with individuals or organizations online. Verify the identity of unknown contacts through independent channels or official websites before sharing personal information or engaging in financial transactions.
- Educate Yourself: Stay informed about the latest impersonation techniques and scams. Be skeptical of suspicious requests for personal information or financial transactions, especially from unfamiliar sources.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Reporting Impersonation Incidents
If you believe you have been a victim of impersonation or have come across an impersonation attempt, it is essential to report the incident to the relevant authorities or platforms:
- Law Enforcement: Contact your local law enforcement agency and provide them with detailed information about the impersonation incident. They can guide you on further steps to take and investigate the matter.
- Online Platforms: If the impersonation occurred on a social media platform, online marketplace, or other digital platform, report the incident to the platform's support or abuse team. They can take appropriate action, such as suspending the impersonator's account or removing malicious content.
Legal Implications of Impersonation
Impersonation can have significant legal consequences, as it is considered a form of fraud and deception. The exact legal implications may vary depending on the jurisdiction, but some common legal considerations related to impersonation include:
- Criminal Charges: Impersonation can result in criminal charges, such as identity theft, fraud, or false impersonation. Penalties may include fines, probation, or imprisonment, depending on the severity of the offense.
- Civil Lawsuits: Impersonation victims may choose to pursue civil litigation against the impersonator to seek compensation for damages, financial losses, or emotional distress. Successful lawsuits can result in monetary judgments or court-ordered injunctions against the impersonator.
Conclusion
Impersonation is a deceptive practice with serious consequences for individuals and society. By understanding the risks, examples, and implications of impersonation, individuals can take proactive steps to protect themselves and mitigate the potential damage caused by impersonators. It is crucial to remain vigilant, practice good online security habits, and report any suspected impersonation incidents to the appropriate authorities or platforms. By staying informed and proactive, we can navigate the digital landscape with greater confidence and protect ourselves from the threats of impersonation.
Frequently Asked Questions
What is Impersonation?
Impersonation is the act of intentionally assuming another person's identity to deceive, defraud, or harm others.
How Does Impersonation Differ from Impersonating?
"Impersonation" refers to the general concept of assuming another's identity, while "impersonating" focuses on the specific actions or behaviors involved in doing so.
What are Some Common Types of Impersonation?
Common types include online identity theft, phishing scams, caller ID spoofing, impersonating public figures, and business impersonation.
What Risks are Associated with Impersonation?
Risks include financial loss, reputation damage, identity theft, invasion of privacy, and emotional distress.
How Can One Protect Themselves from Impersonation?
Protective measures include using strong, unique passwords, enabling two-factor authentication, adjusting social media privacy settings, and verifying the identity of people or organizations before sharing personal information.
Fraudster
Introduction
In an interconnected world driven by technology and online interactions, the presence of fraudsters and scammers poses a significant threat to individuals and organizations alike. These cunning individuals employ various tactics to deceive and manipulate their targets for personal gain. Understanding the modus operandi of fraudsters is crucial in safeguarding ourselves and our communities against their deceptive schemes.
In this article, we will explore the world of fraudsters, shed light on their typical characteristics, explore the meaning of acting fraudulently, and uncover how they exploit social media platforms to steal valuable information. By being aware of their strategies and taking proactive measures, we can effectively protect ourselves from falling victim to their fraudulent acts.
Key Takeaways
- Fraudsters engage in deceptive practices with the intention of deceiving others for personal gain.
- Fraudsters employ various tactics such as impersonation, scamming, and fraudulent actions to exploit individuals and gain financial or personal information.
- Social media platforms have become popular avenues for fraudsters to target victims due to their wide user base and ease of communication.
- Common scams perpetrated by fraudsters on social media include phishing, romance scams, and identity theft.
- To protect yourself from fraudsters on social media, it is important to exercise caution, verify profiles and websites, and avoid sharing personal information with unknown individuals.
- Strong passwords, two-factor authentication, and regular privacy settings review are essential for enhancing online security.
Who is a Fraudster?
Typical Characteristics
Fraudsters exhibit certain common traits and behaviors that enable them to carry out their deceptive activities. These individuals are often highly manipulative and skilled at gaining the trust of their targets. They are opportunistic and exploit vulnerabilities for personal gain. Fraudsters can be charming and persuasive, adept at disguising their true intentions behind a façade of legitimacy. They may display a lack of empathy and have a propensity for taking advantage of others for financial or personal gain.
Synonyms for Scammer
When discussing individuals engaged in fraudulent activities, various terms are used to describe them. A scammer is one such synonym commonly used to refer to fraudsters. Scammers are individuals who use deceit and trickery to defraud others, often through schemes that appear legitimate but are designed to extract money or valuable information. These individuals exploit the trust of their victims and employ tactics such as phishing, identity theft, or fake investment schemes to carry out their fraudulent activities.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Understanding Fraudulent Actions
Defining Fraudulently
Acting fraudulently refers to engaging in deceptive practices with the intention of deceiving others for personal gain. It involves intentionally misrepresenting information or manipulating circumstances to exploit unsuspecting victims. Fraudulent actions can take various forms, such as financial fraud, insurance fraud, or online scams. These actions can have severe consequences, including financial loss, damage to reputations, and emotional distress for the victims.
The Impact of Fraud
Fraudulent actions have far-reaching implications for both individuals and society as a whole. Victims of fraud may experience significant financial losses, leading to financial instability and stress. The aftermath of fraud can also result in emotional distress, mistrust, and a sense of violation. Furthermore, fraudulent activities undermine the integrity of financial systems and erode public trust in institutions. They contribute to increased costs for businesses, governments, and individuals, as efforts are made to combat and prevent fraud.
Infamous Fraudsters in History
Notorious Fraudsters
Throughout history, there have been notable cases involving infamous fraudsters who have gained notoriety for their elaborate schemes. These individuals have orchestrated large-scale frauds, often targeting financial institutions or investors. Examples include figures like Bernie Madoff, who orchestrated one of the largest Ponzi schemes in history, and Charles Ponzi himself, who gave rise to the term "Ponzi scheme." These cases serve as reminders of the significant impact fraudsters can have on individuals and the financial system.
Alleged Fraudsters
The term "alleged fraudster" refers to individuals who have been accused of engaging in fraudulent activities but have not yet been proven guilty in a court of law. Allegations of fraud can be levelled against individuals in various contexts, including corporate fraud, securities fraud, or internet scams. It is important to recognize that until proven guilty, individuals should be considered innocent, and legal processes should be followed to establish their culpability.
Unraveling Social Media Exploitation
Social Media and Fraud
Fraudsters have adapted to the digital age by exploiting social media platforms to carry out their deceitful activities. They leverage the vast reach and interconnectedness of these platforms to target potential victims and gain access to their personal information. Social media provides fraudsters with a means to create fake profiles, initiate phishing attacks, spread malware, or engage in identity theft. They may also use social engineering techniques to manipulate individuals into revealing sensitive information.
Stealing Information
Fraudsters employ various methods to steal valuable information from unsuspecting victims on social media. This can include impersonating trusted individuals or organizations, creating fake accounts or websites, or enticing individuals to click on malicious links or download malicious attachments. By tricking users into sharing personal details, such as login credentials or financial information, fraudsters can gain unauthorized access to accounts or carry out identity theft.
Protecting Yourself
To safeguard against social media exploitation by fraudsters, it is crucial to adopt security measures and exercise caution while using these platforms. Here are some steps to protect yourself:
- Be wary of unsolicited friend requests or messages from unknown individuals.
- Verify the authenticity of profiles and websites before sharing personal information.
- Use strong, unique passwords and enable two-factor authentication for added security.
- Regularly review your privacy settings and limit the amount of personal information visible to the public.
- Avoid clicking on suspicious links or downloading files from untrusted sources.
- Educate yourself about common social media scams and stay updated on the latest fraud techniques.
- Report any suspicious activity or accounts to the platform administrators.
By staying vigilant and taking proactive steps to protect your online presence, you can reduce the risk of falling victim to social media fraud and thwart fraudsters' attempts to exploit your information.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
Fraudsters are individuals who engage in deceptive practices with the aim of deceiving others for personal gain. They often possess manipulative skills and exploit vulnerabilities to carry out their fraudulent activities. Whether it's impersonation, scamming, or engaging in fraudulent actions, these individuals can cause significant harm to individuals and society. It is important to understand the tactics employed by fraudsters and take proactive measures to protect ourselves from their schemes. By staying informed, exercising caution, and adopting security measures, we can mitigate the risk of falling victim to fraudsters and contribute to a safer digital environment.
Fraudsters and scammers continue to exploit unsuspecting individuals and organizations with their deceptive tactics. By understanding their typical characteristics, the meaning of acting fraudulently, and how they utilize social media to steal information, we can equip ourselves with the knowledge needed to stay vigilant and protect against their schemes. It is essential to educate ourselves about the red flags of fraudulent activities and implement robust security measures to safeguard our personal information. By working together to expose and combat fraud, we can create a safer digital landscape for everyone.
Frequently Asked Questions
What is a Fraudster?
A fraudster is an individual who engages in deceptive practices with the intent to deceive or defraud others for personal gain. They often possess traits like manipulativeness, opportunism, and a lack of empathy.
Is "Scammer" the Same as "Fraudster"?
While the terms are often used interchangeably, a scammer is a type of fraudster who uses deceit and trickery to defraud others. Scammers often employ tactics like phishing, identity theft, or fake investment schemes.
What Does "Acting Fraudulently" Mean?
Acting fraudulently refers to engaging in deceptive practices intentionally to deceive others for personal gain. This can take various forms, such as financial fraud, insurance fraud, or online scams.
What is the Impact of Fraudulent Actions?
Fraudulent actions can lead to significant financial losses, emotional distress, and a loss of trust for the victims. They also undermine the integrity of financial systems and contribute to increased costs for businesses, governments, and individuals.
What Does "Alleged Fraudster" Mean?
An "alleged fraudster" refers to someone accused of fraudulent activities but not yet proven guilty. It's important to note that these individuals are considered innocent until proven guilty in a court of law.
How Do Fraudsters Exploit Social Media?
Fraudsters use social media platforms to create fake profiles, initiate phishing attacks, spread malware, or engage in identity theft. They may also use social engineering techniques to manipulate individuals into revealing sensitive information.
How Can I Protect Myself from Social Media Exploitation?
To protect yourself, be cautious of unsolicited friend requests or messages, verify the authenticity of profiles, use strong passwords, enable two-factor authentication, and educate yourself about common social media scams.
What Should I Do If I Suspect I've Been Targeted by a Fraudster?
If you suspect you've been targeted, report the incident to the relevant authorities and the platform where the fraudulent activity occurred. Take steps to secure your accounts and monitor for any unauthorized activities.
Are There Legal Consequences for Fraudsters?
Yes, depending on the jurisdiction and the nature of the fraud, legal consequences can range from fines and probation to imprisonment. Victims may also pursue civil litigation for compensation.
Ban Evasion
Introduction
In the realm of online platforms, maintaining a safe and inclusive environment is paramount. To achieve this, platforms implement various measures, including the use of bans to restrict access for individuals who violate their terms of service or community guidelines. However, some individuals resort to ban evasion as a means to circumvent these restrictions and regain access to platforms they were previously banned from.
In this article, we will delve into the intricacies of ban evasion, explore its legal implications, examine its workings on popular platforms like Twitch and Reddit, and discuss how to report instances of ban evasion.
Key Takeaways
- Ban evasion involves circumventing bans or restrictions imposed by online platforms.
- Ban evasion can have legal consequences depending on the jurisdiction and platform policies.
- Platforms employ various measures to detect and combat ban evasion, including IP tracking and pattern recognition.
- Twitch, a popular live streaming platform, has its own ban evasion detection mechanisms.
- Reddit takes a strong stance against ban evasion and provides tools for reporting such incidents.
Understanding Ban Evasion
What is Ban Evasion?
Ban evasion refers to the act of evading a ban or restriction imposed by an online platform. It involves using different tactics to bypass the measures put in place by the platform to prevent banned individuals from accessing their services. By evading the ban, these individuals aim to regain entry to the platform and continue their activities.
Legality of Ban Evasion
The legality of ban evasion varies depending on the jurisdiction and the platform's terms of service. In many cases, ban evasion is considered a violation of the platform's policies, leading to potential legal consequences. Engaging in ban evasion can result in account suspensions, permanent bans, or even legal action, especially if it involves activities that infringe upon laws, such as harassment or cybercrime.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Ban Evasion on Twitch
How Does Ban Evasion Work on Twitch?
Twitch, a popular live streaming platform, employs various techniques to detect and prevent ban evasion. These techniques include IP tracking, device fingerprinting, and pattern recognition algorithms. Twitch takes ban evasion seriously and continuously enhances its systems to stay ahead of those attempting to bypass bans. Additionally, the Twitch community plays a crucial role in reporting suspicious activities and helping the platform identify potential ban evaders.
Ban Evasion on Reddit
What Happens if You Ban Evade on Reddit?
Reddit, a renowned social media platform, has a strict policy against ban evasion. If a user is found to be evading a ban on Reddit, their new account is likely to be banned as well. The Reddit administration actively monitors and investigates reports of ban evasion, taking appropriate action against violators. Reporting instances of ban evasion on Reddit is essential to maintain a healthy and safe community.
Reporting Ban Evasion on Twitter and Reddit
Platforms like Twitter and Reddit provide reporting mechanisms for users to report instances of ban evasion. Reporting ban evasion helps the platform administrators identify and take action against those attempting to evade bans. On both platforms, the reporting process involves providing relevant information and evidence to support the claim.
Consequences and Prevention
Consequences of Ban Evasion
The consequences of ban evasion can be severe. They range from temporary suspensions to permanent bans, loss of privileges, and even legal repercussions. Platforms are committed to maintaining a fair and safe environment for their users, and ban evasion undermines these efforts. Therefore, engaging in ban evasion can result in serious consequences that impact an individual's access to the platform and their online reputation.
Preventing Ban Evasion
To prevent ban evasion, online platforms employ various measures and technologies. These may include IP tracking, device identification, machine learning algorithms, and pattern recognition. By continuously monitoring user behavior and employing advanced detection systems, platforms can identify suspicious activities and take appropriate action to prevent ban evasion. Additionally, user reporting plays a vital role in detecting and reporting instances of ban evasion, as the collective effort of the community contributes to maintaining a robust and secure online environment.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Conclusion
Ban evasion poses significant challenges to online platforms striving to create safe and inclusive communities. It involves individuals attempting to bypass bans or restrictions imposed by these platforms, often with the intent to continue engaging in inappropriate or prohibited activities. However, platforms are proactive in detecting and addressing ban evasion, employing various technologies and relying on user reporting to maintain a fair and secure online environment.
It is crucial for users to understand the legal implications of ban evasion and support the platform's efforts by reporting instances of ban evasion when encountered. By collectively combatting ban evasion, we can uphold the integrity and trustworthiness of online platforms for the benefit of all users.
Frequently Asked Questions
What is Ban Evasion?
Ban evasion refers to the act of circumventing a ban or restriction imposed by an online platform. Individuals use various tactics to bypass these measures and regain access to the platform, often to continue engaging in prohibited activities.
Is Ban Evasion Legal?
The legality of ban evasion varies by jurisdiction and the platform's terms of service. Generally, it's considered a violation of the platform's policies and can lead to account suspensions, permanent bans, or even legal action if it involves activities like harassment or cybercrime.
How is Ban Evasion Detected on Twitch?
Twitch employs multiple techniques to detect and prevent ban evasion, including IP tracking, device fingerprinting, and pattern recognition algorithms. The Twitch community also plays a role in reporting suspicious activities to help identify potential ban evaders.
What are the Consequences of Ban Evasion on Reddit?
Reddit has a strict policy against ban evasion. If caught, the new account is likely to be banned as well. Reddit's administration actively monitors and investigates reports of ban evasion and takes appropriate action against violators.
How Can Ban Evasion be Prevented?
Online platforms use various technologies like IP tracking, device identification, machine learning algorithms, and pattern recognition to prevent ban evasion. User reporting also plays a crucial role in identifying and taking action against those attempting to evade bans.
Fraud Ring
Introduction
Fraud rings pose a significant threat to individuals, businesses, and financial institutions. These organized criminal networks employ sophisticated techniques to carry out large-scale fraudulent activities, resulting in substantial financial losses. Detecting and dismantling fraud rings requires a comprehensive understanding of their operations and proactive measures to prevent their illicit activities.
In this article, we delve into the world of fraud rings, exploring their detection methods, the impact of credit card fraud, elements of larceny by debit or credit card theft, and the evolving nature of organized fraud.
Key Takeaways
- Fraud rings are organized criminal networks that engage in large-scale fraudulent activities.
- Detecting fraud rings requires advanced analytical tools, data analysis, and collaboration between law enforcement agencies, financial institutions, and technology experts.
- Credit card fraud is one of the most common types of fraud associated with fraud rings, causing substantial financial losses to individuals and businesses.
- The elements of larceny by debit or credit card theft involve unauthorized use, intent to defraud, and taking possession of someone else's card without consent.
- Credit and debit card fraud have replaced traditional types of crimes due to the increasing popularity and convenience of electronic payments.
- Organized fraud rings are categorized under various criminal statutes, depending on the nature of their activities.
Understanding Fraud Rings
Fraud rings are complex criminal networks that operate with the intent to commit large-scale fraudulent activities. These organizations typically consist of multiple individuals who collaborate in carrying out various types of fraud, such as identity theft, credit card fraud, insurance fraud, or online scams. Fraud rings exhibit a hierarchical structure, with individuals assigned specific roles and responsibilities to maximize their illicit gains. By understanding the definition, characteristics, and common types of fraud perpetrated by these rings, we can gain valuable insights into their modus operandi and the potential risks they pose.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Detecting Fraud Rings
Detecting fraud rings requires a combination of advanced analytics, data analysis techniques, and collaborative efforts between law enforcement agencies, financial institutions, and technology experts. Sophisticated algorithms and machine learning models are employed to identify patterns, anomalies, and correlations in financial transactions and behaviours. By analyzing large volumes of data, such as transactional records, social network connections, and geographical information, investigators can uncover suspicious activities indicative of fraud ring operations. Collaborative efforts, information sharing, and the use of shared intelligence platforms play a crucial role in identifying and dismantling these criminal networks.
The Impact of Credit Card Fraud
Credit card fraud is a prevalent form of fraudulent activity associated with fraud rings, resulting in significant financial losses for individuals and businesses. Fraudsters employ various techniques, including card skimming, identity theft, and unauthorized transactions, to exploit vulnerabilities in the credit card payment ecosystem. The impact of credit card fraud extends beyond monetary losses, as victims often endure emotional distress, damage to their credit scores, and the inconvenience of resolving fraudulent charges. Moreover, credit card fraud has broader economic implications, leading to increased costs for financial institutions, retailers, and consumers.
Elements of Larceny by Debit or Credit Card Theft
Larceny by debit or credit card theft involves specific elements that constitute the crime. Unauthorized use of someone else's credit or debit card without their consent is a key element of this offense. Fraudsters typically obtain stolen cards through various means, such as theft, phishing, or purchasing them from illegal sources. Intent to defraud and deceptive practices, such as using stolen cards to make fraudulent purchases or withdrawing cash, are essential components of larceny by debit or credit card theft. Finally, the possession and control of stolen cards without lawful authority complete the elements of this crime.
Evolving Trends in Organized Fraud
Organized fraud rings constantly adapt and evolve their tactics to exploit technological advancements and shift consumer behaviours. The rise of electronic payments and online transactions has led to a shift from traditional crimes to credit and debit card fraud. Fraudsters leverage advanced technologies, such as data breaches, malware, and phishing attacks, to acquire personal and financial information for fraudulent purposes. Emerging fraud schemes include account takeover fraud, synthetic identity theft, and virtual currency fraud. Staying informed about these evolving trends is crucial for individuals, businesses, and law enforcement agencies to effectively combat organized fraud.
Combating Fraud Rings
Combating fraud rings requires a multi-faceted approach that focuses on strengthening security measures, enhancing collaboration and information sharing, and educating the public on fraud awareness and prevention. Financial institutions and businesses should implement robust fraud detection systems, transaction monitoring tools, and identity verification protocols to mitigate risks. Collaborative efforts between law enforcement agencies, industry organizations, and technology providers facilitate the sharing of intelligence, identification of emerging fraud trends, and the prompt investigation and prosecution of fraud ring members. Furthermore, educating the public about fraud risks, safe online practices, and recognizing common fraud indicators can empower individuals to protect themselves from falling victim to fraudulent activities.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
Fraud rings pose a significant threat to individuals, businesses, and financial institutions, perpetrating large-scale fraudulent activities with sophisticated techniques. Detecting, preventing, and combating fraud rings require a multi-faceted approach involving advanced analytics, collaboration between stakeholders, and proactive security measures. By understanding the workings of fraud rings, raising awareness about fraud prevention, and implementing robust fraud detection systems, we can mitigate the impact of organized fraud and safeguard the financial well-being of individuals and businesses.
Frequently Asked Questions
What are fraud rings and how do they operate?
Fraud rings are intricate criminal networks aiming to carry out extensive fraudulent activities, involving various types of fraud such as identity theft and credit card fraud.
How are fraud rings detected?
Detecting fraud rings requires a blend of advanced analytics, data analysis techniques, and collaborative efforts among law enforcement, financial institutions, and tech experts.
What impact does credit card fraud have?
Credit card fraud is a common form of fraudulent activity linked to fraud rings, causing significant financial losses for individuals and businesses. Beyond monetary loss, victims face emotional distress, credit score damage, and the hassle of resolving fraudulent charges, leading to higher costs for financial institutions and consumers.
What constitutes larceny by debit or credit card theft?
Larceny by debit or credit card theft involves unauthorized use of someone else's card, obtained through means like theft or phishing. Intent to defraud and deceptive practices, such as making fraudulent purchases or withdrawals, are crucial elements.
How are organized fraud trends evolving?
Fraud rings adapt to technological advancements and changing consumer behaviours, shifting focus to credit and debit card fraud due to electronic payments. They employ technologies like data breaches and phishing for personal and financial info.
How can fraud rings be combated?
Combating fraud rings involves strengthening security measures, collaborative efforts, and public education. Implementing fraud detection systems, transaction monitoring, and identity verification protocols in businesses helps mitigate risks.
What's the significance of understanding fraud rings?
Understanding fraud rings is essential to grasp their complex operations, methods, and impact. This knowledge helps stakeholders, from individuals to businesses, take proactive measures against organized fraud, ensuring financial security.
Promotion Abuse
Introduction
Promotions and discounts have become an integral part of our consumer culture, providing enticing opportunities to save money and enjoy special offers. However, with the increasing prevalence of promotion abuse, businesses face challenges in maintaining the integrity and profitability of their marketing initiatives.
Promotion abuse refers to the misuse or exploitation of promotional offers, such as promo codes or discounts, for personal gain or fraudulent purposes. In this article, we delve into the concept of promotion abuse, explore its implications, and provide valuable insights into how businesses can effectively combat this issue.
Key Takeaways
- Promotion abuse involves the improper use of promotional offers, such as promo codes or discounts, for personal gain or fraudulent activities.
- Promotion abuse can lead to financial losses for businesses, dilution of brand reputation, and negative customer experiences.
- Businesses can implement various strategies to prevent and address promotion abuse, such as robust terms and conditions, customer validation processes, and monitoring and enforcement mechanisms.
- Effective communication and education regarding the appropriate use of promotions can help minimize the occurrence of abuse.
- Collaborative efforts among businesses, industry organizations, and law enforcement agencies play a crucial role in combating promotion abuse.
Understanding Promotion Abuse
Definition and Types of Promotion Abuse
Promotion abuse encompasses various activities where individuals exploit promotional offers for personal gain or fraudulent purposes. These activities can include unauthorized sharing of promo codes, exploiting promotion stacking loopholes, engaging in manufactured purchases and returns, and falsifying eligibility criteria. Understanding the different types of promotion abuse is crucial for businesses to identify and address potential vulnerabilities in their promotional campaigns.
Impact of Promotion Abuse on Businesses
The impact of promotion abuse on businesses can be significant. Financial losses are one of the primary consequences, as promotions that are exploited or misused can result in reduced revenue and profitability. Moreover, promotion abuse can dilute a company's brand reputation, as customers may associate the brand with unfair practices or feel deceived by false promises. Additionally, negative customer experiences arising from promotion abuse can lead to decreased trust and loyalty, further harming the long-term success of the business.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Common Forms of Promotion Abuse
Unauthorized Sharing of Promo Codes
One prevalent form of promotion abuse is the unauthorized sharing of promo codes. This occurs when individuals distribute or use promo codes without the intended recipient's permission or outside the specified terms and conditions. Unauthorized sharing not only undermines the targeted nature of promotions but also allows individuals to benefit from discounts or benefits they are not entitled to.
Exploiting Promotion Stacking Loopholes
Promotion stacking refers to the practice of combining multiple promotions or discounts to maximize savings or obtain additional benefits. However, some individuals exploit promotion stacking loopholes to gain undue advantages. They may manipulate the system by using multiple accounts, creating false transactions, or exploiting technical glitches to stack promotions in a manner that was not intended by the business.
Manufactured Purchases and Returns
Manufactured purchases and returns involve the deliberate manipulation of buying and returning products to exploit promotions. Individuals engaging in this form of promotion abuse may purchase items solely for the purpose of benefiting from a promotion, such as receiving a discount or qualifying for a free gift. After reaping the benefits, they then return the purchased items, effectively obtaining the promotion without genuine intent to keep the products.
Falsifying Eligibility Criteria
Promotions often have specific eligibility criteria, such as being a new customer, meeting certain spending thresholds, or belonging to a particular target audience. Falsifying eligibility criteria involves individuals misrepresenting themselves or their circumstances to qualify for promotions they would otherwise not be eligible for. This can include providing false information, using fake identities, or employing other deceptive tactics.
Implications of Promotion Abuse
Financial Losses for Businesses
Promotion abuse can result in significant financial losses for businesses. When promotions are abused, businesses may experience reduced revenue, lower profit margins, and increased operational costs. Unanticipated or excessive usage of promotions can strain inventory management and logistics, leading to additional expenses without corresponding sales.
Dilution of Brand Reputation
One of the critical implications of promotion abuse is the potential dilution of a business's brand reputation. When customers encounter instances of promotion abuse, it erodes their trust in the brand and can negatively impact their perception of the company's values and integrity. This loss of trust can have long-lasting consequences, making it challenging for businesses to regain the loyalty and confidence of their customer base.
Negative Customer Experiences and Trust Issues
Promotion abuse can result in negative customer experiences and trust issues. Customers who encounter promotion abuse, such as finding that a promo code they received does not work due to unauthorized sharing or witnessing others exploiting promotions, may feel deceived or frustrated. Such experiences can create a sense of unfairness and erode the trust customers have in the company, potentially leading to reduced engagement, repeat purchases, and advocacy.
Strategies to Prevent and Address Promotion Abuse
Robust Terms and Conditions
Developing clear and comprehensive terms and conditions for promotions is essential to prevent abuse. These terms should outline eligibility criteria, usage limits, and any restrictions or prohibitions on sharing or exploiting promotions. By clearly communicating the rules and expectations, businesses can discourage potential abusers and provide a basis for taking action when abuse occurs.
Secure Promo Code Distribution
Implementing secure promo code distribution methods can help mitigate unauthorized sharing and misuse. Businesses can limit code distribution to specific channels or targeted recipients, such as email subscribers or registered users. Implementing unique or personalized codes can also help track and identify individuals engaging in unauthorized sharing or misuse.
Monitoring and Analytics
Regular monitoring and analysis of promotion usage patterns can help detect potential abuse. By monitoring key metrics such as redemption rates, order patterns, and returns associated with promotions, businesses can identify anomalies or suspicious activities. Data analytics tools can aid in identifying patterns that indicate abuse and enable timely intervention.
Account Verification and Authentication
Implementing account verification and authentication processes can deter individuals from creating multiple accounts to exploit promotions. By verifying user identities and linking promotions to authenticated accounts, businesses can mitigate the risk of abuse and ensure that promotions are used by genuine customers.
Customer Education and Communication
Proactively educating customers about the proper use of promotions and the consequences of abuse can help foster a culture of responsible engagement. Clear communication through various channels, such as website banners, email newsletters, or social media posts, can raise awareness about promotion policies, guidelines, and the importance of ethical use.
Consequences of Promotion Abuse
Penalties and Restrictions
To discourage promotion abuse, businesses can implement penalties and restrictions for those found guilty of abuse. These may include disqualifying individuals from future promotions, suspending or closing accounts, or even pursuing legal action in cases of severe abuse or fraudulent activities.
Loss of Customer Trust and Loyalty
Promotion abuse can lead to the loss of customer trust and loyalty. When customers witness or experience abuse, it undermines their confidence in the fairness of promotions and the company's commitment to providing genuine value. As a result, they may choose to disengage from future promotions or seek alternatives from more reputable businesses.
Reputational Damage
Promotion abuse can have long-term reputational consequences for businesses. Negative experiences and perceptions shared by customers can spread through word-of-mouth, online reviews, or social media, tarnishing the brand's reputation and deterring potential customers from engaging with the company.
{{cta('bdd96089-cde2-43f3-95a3-3f6d7b74af38','justifycenter')}}
Conclusion
In conclusion, promotion abuse poses significant challenges for businesses, impacting their financial well-being and brand reputation. Implementing preventive measures, such as robust terms and conditions, secure code distribution, monitoring and analytics, account verification, and customer education, can help mitigate the risk of abuse. By addressing promotion abuse effectively, businesses can protect their interests, maintain customer trust, and ensure the integrity of their promotional activities.
Promotion abuse poses significant challenges for businesses aiming to provide value to their customers while safeguarding their bottom line. By understanding the various forms of promotion abuse and implementing effective prevention strategies, businesses can protect their interests and maintain the integrity of their promotional initiatives. Additionally, educating customers on responsible promotion use and fostering collaboration among industry stakeholders and law enforcement agencies can contribute to a more secure and trustworthy promotional landscape. By staying vigilant and proactive, businesses can mitigate the risks associated with promotion abuse and create a positive environment for both themselves and their customers.
Frequently Asked Questions
What is promotion abuse, and how can it affect businesses?
Promotion abuse refers to exploiting promotional offers for personal gain or fraud, impacting businesses through reduced revenue and brand reputation damage.
What are common forms of promotion abuse?
Common forms include unauthorized sharing of promo codes, exploiting stacking loopholes, manufactured purchases/returns, and falsifying eligibility criteria.
What are the implications of promotion abuse on businesses?
Implications include financial losses, brand reputation dilution, and negative customer experiences leading to decreased trust and loyalty.
How can businesses prevent and address promotion abuse?
Strategies include clear terms and conditions, secure promo code distribution, monitoring, account verification, and customer education.
What are the consequences of promotion abuse?
Consequences range from penalties and account restrictions to loss of customer trust, loyalty, and reputational damage.
Marketplace Risk
Introduction
With the surge of digital platforms, the concept of marketplaces has significantly evolved. Today, marketplaces aren't just physical venues for trade, but also vibrant virtual spaces where millions of transactions occur daily.
With this great opportunity comes great challenges - the most pressing of which is 'marketplace risk.' Understanding and managing this risk is crucial for marketplace operators seeking success in this bustling ecosystem.
Key Takeaways
- Marketplace risk refers to potential threats that could disrupt the normal functioning of a marketplace, leading to financial losses, a damaged reputation, or loss of trust among users.
- Transaction risks, regulatory risks, and data security risks are some of the main dimensions of marketplace risk that businesses need to be aware of.
- Real-world examples of marketplace risk can be found across different sectors, including e-commerce platforms and financial marketplaces like stock exchanges or cryptocurrency platforms.
- Mitigating marketplace risk involves implementing robust verification processes, ensuring regulatory compliance, and deploying strong data protection strategies.
- Understanding and mitigating marketplace risk is crucial for the success of any marketplace, as it ensures smoother transactions, satisfied users, and a thriving business.
Defining Marketplace Risk: Beyond the Basics
Marketplace risk refers to potential threats that could disrupt the normal functioning of a marketplace, leading to financial losses, damaged reputation, and loss of trust among users. These risks could be due to various factors like fraudulent transactions, non-compliance with regulations, data breaches, or even market volatility.
The Many Facets of Marketplace Risk: A Comprehensive Look
While the term 'marketplace risk' seems straightforward, it encompasses several dimensions. From transaction risks, regulatory risks, to data security risks and more, it's a term that holds much gravity in the commercial landscape.
Transaction Risks
In every marketplace, the core activity revolves around transactions. Any issue that hinders the smooth processing of transactions - such as fraud, non-payment, delivery failures, or disputes - falls under transaction risk.
Regulatory Risks
Regulations guide the functioning of any marketplace, ensuring fair trade practices. Non-compliance with these regulations can lead to penalties, legal consequences, and damage to reputation.
Data Security Risks
In the digital era, data is the backbone of any online marketplace. Breaches can lead to severe implications such as loss of user trust, legal liabilities, and financial damages.
Marketplace Risk in Real-World Contexts: Use Cases
Understanding marketplace risk involves analyzing real-world examples. Let's explore how this risk unfolds across various industries and sectors.
E-commerce Marketplaces
In e-commerce platforms, marketplace risk can manifest in various forms, such as fraudulent transactions, counterfeit products, or data breaches, affecting both the platform operator and the users.
Financial Marketplaces
In financial marketplaces like stock exchanges or cryptocurrency platforms, marketplace risk includes price volatility, cyber threats, and regulatory compliance issues, impacting investors and the platform itself.
Safeguarding the Marketplace: Mitigation Strategies
Minimizing marketplace risk involves proactive planning and robust strategies. Here are some key measures.
Robust Verification Processes
Implementing stringent verification for sellers and buyers can prevent fraudulent activities, enhancing the marketplace's credibility and safety.
Regulatory Compliance
Ensuring adherence to all applicable regulations is crucial to avoid legal ramifications and maintain a trustworthy marketplace environment.
Data Protection Measures
Deploying strong data protection strategies, including encryption, secure payment gateways, and regular audits, can prevent data breaches.
Conclusion
Understanding and mitigating marketplace risk is crucial for creating a thriving and secure marketplace. As marketplaces continue to evolve and expand, managing these risks will remain a critical task for marketplace operators, ensuring smoother transactions, satisfied users, and a successful marketplace.
Duplicate Account
Introduction
In the ever-evolving financial world, the term 'duplicate account' might seem straightforward at first glance, yet it holds significant implications. Simply put, a duplicate account refers to having two or more accounts that belong to the same customer, unintentionally created due to various reasons.
These could range from technical glitches, user errors, or even fraud. The existence of duplicate accounts can lead to confusion, misinformation, and potential security breaches, making it a matter of concern for both businesses and customers.
Key Takeaways
- A duplicate account refers to two or more accounts connected to one individual or entity. This situation could arise due to various reasons, including technical errors, customer mistakes, or even fraudulent activities.
- Duplicate accounts can have far-reaching implications such as data distortion, customer dissatisfaction, and in cases of fraud, severe financial and reputational damage.
- Understanding how duplicate accounts are created, whether by accident or malicious intent, is crucial in tackling their presence.
- Duplicate accounts can be either accidental, created due to a system glitch or a user error, or fraudulent, intentionally created by impostors using stolen information.
- In various sectors such as banking and e-commerce, duplicate accounts can lead to operational inefficiencies, customer dissatisfaction, data breaches, and potential financial loss.
- Preventing duplicate accounts involves robust identity verification processes, careful data management, regular audits, and the use of advanced systems to automatically detect and flag potential duplicate accounts.
Definition and Overview of Duplicate Accounts
A 'duplicate account' essentially means that multiple accounts are connected to one individual or entity. This could occur in various sectors, such as banking, telecommunications, or any service industry that maintains customer accounts. While the creation of a duplicate account might be an innocent mistake in some instances, it could also hint towards more malicious activities like identity theft or fraud. Therefore, understanding the dynamics of duplicate accounts is crucial for maintaining efficient and secure operations.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Implications of Duplicate Accounts
Duplicate accounts can have far-reaching implications. On an operational level, they can distort data, leading to inaccurate reporting and analysis. They could also lead to customer dissatisfaction due to mishandled transactions or communication. On a more serious note, if duplicate accounts are the result of fraudulent activity, they could lead to monetary losses and reputational damage.
Understanding How Duplicate Accounts are Created
Duplicate accounts could arise from various scenarios. For instance, a customer may accidentally create a new account instead of accessing their existing one, or a system glitch might cause a duplicate entry. In more alarming cases, fraudsters might intentionally create duplicate accounts using stolen customer information.
Role of Digital Identity Verification
A significant part of dealing with duplicate accounts involves verifying the digital identity of customers. Ensuring that the person creating an account is who they claim to be can prevent unintentional duplication and curb fraudulent activities. Various technologies, such as biometric verification, can be employed for this purpose.
Types of Duplicate Accounts
Duplicate accounts could take different forms depending on the circumstances surrounding their creation. These could include:
- Accidental Duplicate Accounts: Created inadvertently by customers or due to system errors.
- Fraudulent Duplicate Accounts: Intentionally created by fraudsters using compromised personal data.
Use Cases and Potential Risks
Understanding the concept of duplicate accounts is best achieved by examining a few use cases:
- Banking: Duplicate accounts could lead to problems in maintaining accurate financial records, impacting a bank's operations and customer trust.
- E-commerce: Duplicate accounts could cause confusion with order tracking and delivery, impacting customer satisfaction and business reputation.
The potential risks associated with duplicate accounts range from operational inefficiencies to data breaches, financial loss, and damage to brand reputation.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Prevention of Duplicate Accounts
Preventing the creation of duplicate accounts primarily involves robust identity verification processes, careful handling of customer data, and regular audits to identify and resolve duplicate entries. Advanced AI-driven systems can also be employed to automatically detect and flag potential duplicate accounts.
Conclusion
While duplicate accounts might seem like a minor hiccup, they carry significant implications in the financial and service sectors. By understanding their nature, potential risks, and prevention methods, businesses can better safeguard their operations and maintain customer trust. Awareness and proactive action are the first steps towards mitigating the issues surrounding duplicate accounts.
Proactive Detection
Introduction
In today's rapidly evolving digital landscape, where cyber threats continue to grow in complexity and sophistication, organizations need to adopt proactive measures to safeguard their systems and data. One such approach is proactive detection, which plays a vital role in identifying and mitigating potential threats before they cause significant harm.
This article delves into the concept of proactive detection, its working principles, various types, and practical use cases. By understanding the significance and application of proactive detection, businesses can strengthen their security posture and effectively combat emerging threats.
Key Takeaways
- Proactive detection involves actively identifying potential threats and vulnerabilities in systems before they lead to security incidents.
- Proactive detection employs continuous monitoring, threat intelligence integration, behaviour-based anomaly detection, and advanced technologies like machine learning.
- Proactive detection includes network-based, endpoint-based, and application-based approaches.
- Proactive detection has diverse applications, including threat detection and prevention in banking, cybersecurity, e-commerce, healthcare, and government sectors.
- Organizations can strengthen security through strong access controls, regular updates, employee education, network segmentation, and incident response planning.
Definition of Proactive Detection
Proactive detection refers to the practice of actively searching for and identifying potential threats or vulnerabilities in a system or network. It involves implementing advanced technologies, tools, and strategies to anticipate and respond to security incidents before they manifest. Unlike reactive approaches that primarily rely on incident response after an attack, proactive detection focuses on early threat identification and prevention, enabling organizations to take proactive measures to mitigate risks and minimize potential damages.
Explanation of Proactive Detection
Proactive detection involves a combination of methodologies, technologies, and security practices aimed at identifying potential threats before they exploit vulnerabilities. It relies on continuous monitoring, analysis of network traffic, behaviour-based anomaly detection, and threat intelligence to identify patterns indicative of malicious activity. By leveraging proactive detection mechanisms, organizations can enhance their overall security posture and respond swiftly to emerging threats.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
How It Works: The Mechanism of Proactive Detection
- Continuous Monitoring: Proactive detection relies on real-time monitoring of network activity, system logs, and user behaviour to identify potential indicators of compromise (IOCs). It involves deploying security solutions and employing techniques like intrusion detection systems (IDS), security information and event management (SIEM), and log analysis tools.
- Threat Intelligence Integration: Proactive detection leverages threat intelligence feeds from trusted sources to identify emerging threats and trends. By staying up-to-date with the latest threat intelligence, organizations can proactively identify potential risks and take necessary preventive actions.
- Behaviour-Based Anomaly Detection: Proactive detection utilizes behavioural analysis techniques to establish baseline patterns of normal system behaviour. Any deviation from these patterns is flagged as a potential threat, enabling security teams to investigate and mitigate the risk.
- Machine Learning and Artificial Intelligence: Advanced technologies like machine learning and artificial intelligence are employed in proactive detection to automate threat detection processes. These technologies can analyze large volumes of data, identify complex patterns, and detect anomalies that may indicate malicious activity.
Types of Proactive Detection
- Network-Based Proactive Detection: This approach focuses on monitoring network traffic and identifying potential threats, such as unusual network behaviours, unauthorized access attempts, or suspicious network activities. It often involves technologies like intrusion detection systems (IDS), intrusion prevention systems (IPS), and network behavior analysis (NBA) tools.
- Endpoint-Based Proactive Detection: Endpoint-based proactive detection involves monitoring individual endpoints, such as computers, servers, or mobile devices, for signs of malicious activity. It relies on endpoint security solutions like antivirus software, host intrusion detection systems (HIDS), and endpoint detection and response (EDR) tools.
- Application-Based Proactive Detection: This type of proactive detection involves monitoring applications and their behaviours to identify potential vulnerabilities or unauthorized activities. It employs techniques like application security testing, code review, and runtime application self-protection (RASP) to detect and mitigate threats at the application layer.
Use Cases: Practical Applications of Proactive Detection
Proactive detection finds wide application across various industries and sectors. Here are some practical use cases:
- Banking and Finance: Financial institutions employ proactive detection to identify fraudulent activities, such as account takeover attempts, money laundering, or unauthorized transactions. By monitoring customer transactions, user behaviour, and patterns of financial activity, banks can proactively detect and prevent potential financial crimes.
- Cybersecurity: Proactive detection is a crucial component of robust cybersecurity strategies. It enables organizations to identify and thwart cyber threats, including malware infections, phishing attacks, and data breaches. By continuously monitoring network traffic, analyzing system logs, and employing advanced threat detection technologies, cybersecurity teams can proactively defend against evolving threats.
- E-commerce and Retail: In the online retail sector, proactive detection helps identify and prevent fraudulent transactions, account compromises, and identity theft. By analyzing customer purchase patterns, transaction history, and user behaviour, e-commerce platforms can detect anomalies and take immediate action to protect both customers and the business.
- Healthcare: Proactive detection plays a vital role in safeguarding sensitive healthcare data and protecting patient privacy. Healthcare organizations utilize advanced monitoring tools and behaviour-based analytics to identify potential data breaches, unauthorized access attempts, or malicious activities within their systems. This helps ensure compliance with regulatory requirements and maintains patient trust.
- Government and Public Sector: Governments employ proactive detection to combat cyber threats, protect critical infrastructure, and secure sensitive information. By monitoring network traffic, analyzing security logs, and leveraging threat intelligence, government agencies can proactively identify and respond to potential cyber-attacks, espionage attempts, or unauthorized access.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Prevention Methods: Strengthening Security with Proactive Measures
To enhance proactive detection efforts and minimize security risks, organizations can adopt the following prevention methods:
- Implement Strong Access Controls: Ensure proper user authentication and authorization mechanisms are in place to prevent unauthorized access to systems and sensitive data.
- Regular Patching and Updates: Keep software, applications, and systems up to date with the latest security patches and updates to address known vulnerabilities.
- Employee Education and Awareness: Provide comprehensive training to employees regarding cybersecurity best practices, including identifying phishing attempts, practising safe browsing habits, and maintaining strong passwords.
- Network Segmentation: Divide networks into logical segments to isolate critical assets and restrict unauthorized access between segments, reducing the impact of potential breaches.
- Incident Response Planning: Develop a robust incident response plan that outlines clear procedures for detecting, containing, and mitigating security incidents.
Conclusion
Proactive detection is a crucial aspect of modern cybersecurity, enabling organizations to stay ahead of evolving threats and protect their systems and data. By adopting proactive measures, such as continuous monitoring, threat intelligence integration, and behaviour-based anomaly detection, businesses can identify and respond to potential threats before they escalate. Implementing strong prevention methods and staying proactive in cybersecurity practices are key to maintaining a secure digital environment. With proactive detection as an integral part of their security strategies, organizations can effectively safeguard their assets, maintain customer trust, and mitigate potential damages from cyber threats.
USA PATRIOT Act
Introduction
The USA PATRIOT Act stands as a significant piece of legislation that has shaped the landscape of national security and civil liberties in the United States. Enacted in response to the 9/11 terrorist attacks, the act introduced a range of measures aimed at enhancing counterterrorism efforts.
In this article, we will delve into the USA PATRIOT Act, its main components, the concept of Patriot Act compliance, and the biggest criticisms it has faced. Join us as we explore the intricacies of this controversial law and its implications for national security and individual privacy.
Key Takeaways
- The USA PATRIOT Act was enacted to enhance counterterrorism efforts in the aftermath of the 9/11 attacks.
- It introduced expanded surveillance powers, enhanced information sharing, and strengthened regulations on money laundering and terrorist financing.
- Compliance with the act involves obligations for financial institutions, including customer due diligence and reporting of suspicious activities.
- The act has been subject to significant criticism, particularly regarding potential privacy violations and the erosion of civil liberties.
- Ongoing debates surround the balance between national security priorities and the protection of individual rights and freedoms.
The USA PATRIOT Act: Understanding the Context and Purpose
The USA PATRIOT Act, enacted in response to the 9/11 attacks, aimed to provide law enforcement agencies with enhanced tools and authority to combat terrorism.
The Main Components of the USA PATRIOT Act
- Expanded Surveillance Powers: The act granted broader surveillance capabilities to intelligence and law enforcement agencies, including the collection of business records and access to electronic communications.
- Enhanced Information Sharing: The act promoted increased collaboration and information sharing among government agencies to improve the flow of intelligence and strengthen national security efforts.
- Strengthened Money Laundering and Terrorist Financing Regulations: The act imposed stricter regulations on financial institutions to prevent money laundering and terrorist financing activities.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
USA PATRIOT Act Compliance: Requirements and Obligations
- Financial Institutions and Customer Due Diligence: Financial institutions are required to implement robust customer due diligence processes to identify and verify the identity of their customers.
- Reporting Suspicious Activities: The act mandates the reporting of suspicious activities that may be linked to terrorism or money laundering to appropriate authorities.
- Maintaining Adequate Records: Financial institutions must maintain proper records of transactions and customer information to facilitate law enforcement investigations when necessary.
The USA PATRIOT Act's Impact on National Security and Civil Liberties
- Balancing National Security Priorities: The act aimed to strike a balance between national security imperatives and the protection of civil liberties, although critics argue that it leans heavily towards the former.
- Controversies Surrounding Surveillance Programs: Surveillance programs authorized under the act, such as the collection of metadata and bulk data collection, have sparked debates about privacy infringement and government overreach.
- Evaluating the Efficacy of Counterterrorism Measures: The effectiveness of the act's provisions in preventing terrorist attacks remains a subject of ongoing discussion and analysis.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
The Biggest Criticisms of the USA PATRIOT Act: Privacy Concerns and Civil Liberties
- Potential Abuse of Surveillance Powers: Critics argue that the act's broad surveillance powers have the potential for abuse, leading to unwarranted invasions of privacy and the targeting of innocent individuals.
- Lack of Transparency and Oversight: Concerns have been raised regarding the lack of transparency and inadequate oversight mechanisms to ensure the responsible use of the act's provisions.
- Impact on Privacy Rights and Constitutional Protections: The act has been criticized for its impact on privacy rights and the erosion of constitutional protections, such as Fourth Amendment rights against unreasonable searches and seizures.
Banking as a Service
Introduction
Banking as a Service (BaaS) has emerged as a transformative concept in the financial industry, revolutionizing the way banking services are delivered and consumed. This innovative model allows non-banking companies, such as fintech startups and technology firms, to offer banking services to their customers by leveraging the infrastructure and capabilities of established financial institutions.
In this article, we will explore the concept of Banking as a Service, understand its significance, delve into real-world examples, discuss the top BaaS banks, explore pricing models, and highlight leading BaaS providers.
Key Takeaways
- Banking as a Service (BaaS) enables non-banking entities to offer banking services to their customers by leveraging the infrastructure and capabilities of established financial institutions.
- Real-world examples of BaaS include fintech companies, e-commerce platforms, and technology companies integrating banking services into their products.
- Top BaaS banks include Green Dot Corporation, Solarisbank, and Railsbank.
- Pricing models in BaaS vary, with some providers charging transaction-based fees and others using subscription-based pricing.
- Leading BaaS providers include Marqeta, Synapse, and Cambr.
- BaaS offers benefits such as faster time-to-market and improved customer experience, but also poses challenges related to regulation and data security.
- The future of BaaS is expected to drive innovation and reshape the financial industry.
Introduction to Banking as a Service (BaaS)
Banking as a Service (BaaS) refers to the provision of banking products and services by a financial institution to non-banking entities. BaaS enables these entities to integrate banking services seamlessly into their own platforms, providing their customers with access to essential financial services such as payments, lending, and account management.
Understanding the BaaS Model
The BaaS model allows non-banking companies to leverage the infrastructure, licenses, and expertise of established banks. These non-banking entities act as intermediaries, creating a seamless banking experience for their customers while relying on the underlying banking infrastructure provided by BaaS partners.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Real-World Examples of BaaS
Examples of BaaS include:
- Fintech companies partnering with traditional banks to offer digital banking services through mobile apps or web platforms.
- E-commerce platforms incorporating financial services, such as digital wallets and payment processing, into their offerings.
- Technology companies embedding banking features, such as issuing debit cards or providing savings accounts, into their products.
Top BaaS Banks in the Industry
The top BaaS banks include:
- Green Dot Corporation: Known for its Banking as a Service platform, Green Dot provides the underlying banking infrastructure to various fintech and technology companies.
- Solarisbank: A German banking platform that enables businesses to offer fully licensed financial services to their customers.
- Railsbank: A global BaaS provider that enables companies to offer banking services and embed financial products into their own platforms.
Pricing Models in Banking as a Service
Pricing models in BaaS vary depending on the provider and the specific services offered. Some BaaS providers charge a fee per transaction or per account, while others have subscription-based pricing models. The pricing structure is typically tailored to meet the needs of the non-banking entity and its customer base.
Leading BaaS Providers
Leading BaaS providers in the industry include:
- Marqeta: A BaaS platform that offers modern card issuing and payment infrastructure solutions.
- Synapse: A BaaS provider that specializes in enabling fintech companies to build financial products and services.
- Cambr: A BaaS platform focused on simplifying payment experiences and providing scalable banking solutions.
Benefits and Challenges of Banking as a Service
BaaS offers several benefits, such as accelerated time-to-market, enhanced customer experience, and access to banking expertise. However, it also presents challenges related to regulatory compliance, data security, and maintaining a seamless integration between the non-banking entity and the BaaS partner.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
The Future of BaaS
The future of BaaS looks promising, with increasing collaborations between financial institutions and non-banking entities. As technology continues to advance, BaaS is expected to drive innovation and reshape the financial landscape, providing customers with more accessible and personalized banking experiences.
Conclusion
Banking as a Service (BaaS) is reshaping the financial industry by enabling non-banking entities to offer banking services to their customers. Through strategic partnerships with established financial institutions, BaaS providers are accelerating innovation, enhancing customer experiences, and driving the evolution of financial services. As BaaS continues to gain momentum, the collaboration between traditional banks and non-banking entities is expected to shape the future of banking, providing customers with more accessible and tailored financial solutions.
OFAC
Introduction
The Office of Foreign Assets Control (OFAC) plays a vital role in maintaining national security and promoting U.S. foreign policy objectives. As part of the U.S. Department of the Treasury, OFAC administers and enforces economic and trade sanctions against targeted individuals, entities, and countries.
In this article, we will explore the Office of Foreign Assets Control, its responsibilities, the significance of OFAC compliance, the process of OFAC screening, and the latest OFAC sanctions list. Join us as we delve into the intricacies of this important regulatory body and its impact on global financial transactions.
Key Takeaways
- The Office of Foreign Assets Control (OFAC) is a division of the U.S. Department of the Treasury responsible for administering and enforcing economic and trade sanctions.
- OFAC sanctions list identifies individuals, entities, and countries subject to sanctions and restrictions due to their involvement in illicit activities or threats to national security.
- Compliance with OFAC regulations and obligations is crucial for businesses and financial institutions to prevent engaging with prohibited parties.
- OFAC screening is a necessary process to ensure compliance and prevent transactions with sanctioned individuals and entities.
- Businesses may seek an OFAC license to conduct transactions that would otherwise be prohibited under the sanctions programs.
- OFAC plays a significant role in maintaining national security, combating terrorism, promoting non-proliferation efforts, and supporting U.S. foreign policy goals.
- Staying updated on the latest OFAC sanctions list is essential to avoid engaging in prohibited transactions.
OFAC: Ensuring National Security and Compliance
The Office of Foreign Assets Control (OFAC) is a division of the U.S. Department of the Treasury responsible for administering and enforcing economic and trade sanctions.
Understanding OFAC Sanctions: Targeting Individuals, Entities, and Countries
- OFAC Sanctions List: The OFAC sanctions list identifies individuals, entities, and vessels that are subject to sanctions and restrictions due to their involvement in illicit activities or threats to national security.
- OFAC Sanctions List Countries: Certain countries and regions are subject to comprehensive or targeted sanctions, prohibiting or limiting financial transactions with entities and individuals from these jurisdictions.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
OFAC Compliance: Navigating Regulatory Requirements and Obligations
- OFAC Screening: Financial institutions and businesses are required to screen their customers, partners, and transactions against the OFAC sanctions list to ensure compliance and prevent engaging with prohibited parties.
- OFAC License: In some cases, businesses may apply for an OFAC license to conduct transactions or engage in activities that would otherwise be prohibited under the sanctions programs.
The Role of the Office of Foreign Assets Control
- Combating Terrorism and Transnational Threats: OFAC plays a crucial role in targeting and disrupting the financial networks of terrorist organizations and other transnational threats.
- Promoting Non-Proliferation Efforts and Human Rights: OFAC supports efforts to prevent the proliferation of weapons of mass destruction and combat human rights abuses by imposing sanctions on violators.
- Supporting U.S. Foreign Policy Goals: OFAC sanctions are often used as a tool to advance U.S. foreign policy objectives, including promoting democracy, peace, and stability worldwide.
OFAC Sanctions List: Staying Updated on Designated Individuals and Entities
Financial institutions and businesses must regularly check and monitor the latest OFAC sanctions list to ensure they are not engaging in prohibited transactions with designated parties.
Read More: What Are the Repurcussions of Breaching OFAC Sanctions
Regulated Entities
Introduction
Regulated entities play a critical role in maintaining the integrity and stability of the financial sector. In the banking industry, regulatory bodies enforce specific rules and guidelines to ensure that financial institutions operate in a responsible and compliant manner. These regulated entities serve as the key players responsible for adhering to and implementing these regulations.
In this article, we will delve into the concept of regulated entities, their significance in the banking sector, examples of regulated entities, and their role in ensuring compliance. Join us as we explore the world of regulated entities and their impact on the financial industry.
Key Takeaways
- Regulated entities play a crucial role in maintaining compliance and stability in the banking sector.
- Examples of regulated entities include commercial banks, credit unions, investment banks, mortgage lenders, insurance companies, and brokerage firms.
- Compliance with regulations ensures consumer protection and mitigates systemic risks.
- Regulated entities operate under the supervision of regulatory authorities.
- Understanding the role of regulated entities is essential for stakeholders in the financial industry.
Introduction to Regulated Entities
Regulated entities refer to financial institutions and organizations that operate within the framework of specific regulations set by regulatory authorities.
Understanding the Importance of Regulation in the Banking Sector
Regulation in the banking sector is crucial for ensuring the stability and integrity of the financial system, protecting consumers, and preventing financial crimes.
Examples of Regulated Entities
- Commercial Banks: Commercial banks are regulated entities that offer various financial services, including accepting deposits, granting loans, and facilitating transactions.
- Credit Unions: Credit unions, which are member-owned financial cooperatives, are also regulated entities that provide banking services to their members.
- Investment Banks: Investment banks engage in activities such as underwriting securities, facilitating mergers and acquisitions, and providing financial advisory services, all within regulatory frameworks.
- Mortgage Lenders: Mortgage lenders, whether traditional banks or specialized institutions, are regulated entities involved in providing mortgage loans to individuals and businesses.
- Insurance Companies: Insurance companies, responsible for providing coverage and managing risks, are subject to regulatory oversight to ensure solvency and consumer protection.
- Brokerage Firms: Brokerage firms facilitate the buying and selling of securities on behalf of clients and are subject to regulations to ensure fair and transparent transactions.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Compliance and Regulation in the Banking Industry
- Regulatory Frameworks and Authorities: Regulated entities must comply with regulations established by regulatory bodies such as central banks, financial regulatory agencies, and government entities.
- Ensuring Consumer Protection: Regulatory frameworks aim to protect consumers by establishing standards for transparency, fair practices, and dispute resolution mechanisms.
- Mitigating Systemic Risks: Regulated entities contribute to the stability of the financial system by implementing risk management practices and adhering to prudential regulations.
The Role of Regulated Entities in Maintaining Financial Stability
Regulated entities act as gatekeepers, ensuring compliance with regulations, conducting due diligence, and implementing measures to prevent financial crimes, such as money laundering and fraud.
List of Regulated Entities
While the specific list of regulated entities may vary across jurisdictions, it typically includes banks, credit unions, insurance companies, investment firms, and other financial service providers.
Regulated Entities in the UK: Compliance and Supervision
In the UK, regulated entities operate under the supervision of regulatory bodies such as the Financial Conduct Authority (FCA) and the Prudential Regulation Authority (PRA).
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Conclusion
Regulated entities form the foundation of a well-functioning and compliant financial sector. These entities, ranging from commercial banks to insurance companies and investment firms, play a pivotal role in maintaining stability, protecting consumers, and adhering to regulatory frameworks.
By understanding the significance of regulated entities, stakeholders in the banking industry can work together to create a robust and secure financial environment. Compliance with regulations not only safeguards the interests of customers but also contributes to the overall integrity and trustworthiness of the financial system.
FDIC
Introduction
The Federal Deposit Insurance Corporation (FDIC) is a vital institution in the United States responsible for insuring deposits in banks and promoting stability in the banking system. Established during the New Deal era in response to the Great Depression, the FDIC plays a crucial role in maintaining public confidence in the financial system.
In this article, we will explore the purpose and functions of the FDIC, its role in protecting depositors, the history of its creation, and how to contact the FDIC for assistance. Join us as we delve into the details of this essential regulatory agency and its contribution to the stability of the banking industry.
Key Takeaways
- The Federal Deposit Insurance Corporation (FDIC) insures deposits in banks and promotes stability in the banking system.
- The FDIC safeguards deposits, promotes public confidence, and resolves failed banks.
- The FDIC was created in response to the Great Depression to restore trust in the banking system.
- Understanding FDIC deposit insurance coverage limits is crucial for depositors.
- FDIC member banks must comply with regulations and sound banking practices.
- The FDIC plays a vital role in maintaining stability in the banking industry.
Introduction to the Federal Deposit Insurance Corporation (FDIC)
The Federal Deposit Insurance Corporation (FDIC) is an independent agency of the U.S. federal government that provides deposit insurance to depositors in banks and savings associations.
Purpose and Functions of the FDIC
- Safeguarding Deposits: The primary purpose of the FDIC is to protect depositors by insuring their deposits in member banks against loss in the event of bank failure.
- Promoting Public Confidence in the Banking System: The FDIC works to maintain public confidence in the banking system by providing stability and reassurance to depositors.
- Resolving Failed Banks: In cases of bank failures, the FDIC steps in to resolve the issues and minimize disruptions to depositors and the financial system.
The Creation of the FDIC: Responding to the Great Depression
The FDIC was established in 1933 as part of the Banking Act, also known as the Glass-Steagall Act, during the New Deal era in response to the widespread bank failures and economic turmoil of the Great Depression.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
FDIC Deposit Insurance: Understanding Coverage Limits and Protections
The FDIC provides deposit insurance coverage up to certain limits per depositor, per ownership category, in member banks. Understanding the coverage limits and protections is essential for depositors to ensure the safety of their funds.
FDIC Member Banks: Ensuring Compliance and Sound Banking Practices
Banks that accept FDIC deposit insurance must comply with specific regulations and adhere to sound banking practices to ensure the safety and stability of the financial system.
The Role of the FDIC in Maintaining Banking Stability
The FDIC works closely with other regulatory bodies to supervise and regulate member banks, conduct risk assessments, monitor emerging risks, and implement measures to maintain stability in the banking industry.
Contacting the FDIC for Assistance
Individuals can contact the FDIC for assistance, including inquiries about deposit insurance, reporting concerns or complaints about a bank, or seeking information on banking regulations and consumer protection.
Financial Action Task Force
Introduction
The Financial Action Task Force (FATF) is a global intergovernmental organization that plays a crucial role in combating money laundering, terrorist financing, and other threats to the international financial system.
In this article, we will delve into the functions and impact of the FATF, exploring its recommendations, the significance of the grey list, and the broader implications for countries around the world.
Key Takeaways
- The FATF is an intergovernmental organization focused on combating money laundering and terrorist financing.
- It sets global standards and provides guidance to countries on AML and CTF measures.
- The FATF's recommendations form the basis for effective AML and CTF frameworks worldwide.
- Inclusion on the FATF grey list can have significant implications for a country's financial reputation and international relationships.
- FATF membership demonstrates a country's commitment to global financial security and cooperation.
- The FATF's impact extends beyond its members, as its recommendations influence international AML and CTF efforts.
Introduction to the Financial Action Task Force (FATF)
Established in 1989, the FATF is an intergovernmental organization comprising 38 member countries and jurisdictions, along with several regional organizations. Its primary goal is to develop and promote policies and standards to combat money laundering, terrorist financing, and other illicit activities.
The Role of FATF in Combating Money Laundering and Terrorist Financing
The FATF sets international standards and provides guidance to countries on implementing effective measures to prevent money laundering and terrorist financing. It conducts evaluations to assess countries' compliance with these standards and works to identify and address emerging threats and vulnerabilities in the global financial system.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
FATF Recommendations: Strengthening AML and CTF Measures
The FATF has developed a series of 40 recommendations that provide a comprehensive framework for countries to implement robust anti-money laundering and counter-terrorist financing measures. These recommendations cover areas such as customer due diligence, reporting suspicious transactions, international cooperation, and the regulation of virtual assets and virtual asset service providers.
The Significance of the FATF Grey List
The FATF maintains a list of countries and jurisdictions that have strategic deficiencies in their anti-money laundering and counter-terrorist financing regimes. Referred to as the grey list, inclusion on this list can have significant implications for a country's financial reputation, international business relationships, and access to global financial systems.
FATF Membership and Global Commitment
Membership in the FATF is based on a country's commitment to implement the FATF recommendations and undergo mutual evaluations to assess their compliance. Member countries actively participate in the development of international standards and collaborate to combat money laundering and terrorist financing on a global scale.
{{cta('31af77a9-1ccc-4abd-a9f1-28412872c7a2','justifycenter')}}
FATF's Impact on Countries and Financial Systems
The FATF's influence extends beyond its member countries. Its recommendations and evaluations have become a benchmark for international AML and CTF efforts. Non-member countries often align their policies and measures with FATF standards to maintain international credibility and foster cooperation in combating illicit financial activities.
Addressing Challenges and Advancing Global Financial Security
The FATF continuously monitors evolving money laundering and terrorist financing risks and adjusts its recommendations accordingly. It collaborates with member countries and stakeholders to address emerging challenges, such as the rise of virtual assets and the use of innovative technologies in illicit activities.
In conclusion, the Financial Action Task Force (FATF) plays a vital role in shaping international efforts to combat money laundering and terrorist financing. Its recommendations, evaluations, and influence have a profound impact on countries' financial systems and their ability to maintain global credibility. By fostering collaboration and setting high standards, the FATF contributes to the collective goal of safeguarding the integrity of the global financial system.
FinCEN
Introduction
The Financial Crimes Enforcement Network (FinCEN) is a crucial agency within the United States Department of the Treasury that plays a pivotal role in combatting financial crimes.
In this article, we will delve into the functions and responsibilities of FinCEN, its role in enforcing regulations, its relationship with Know Your Customer (KYC) practices and its significance in safeguarding the integrity of the financial system.
Key Takeaways
- FinCEN is an essential agency within the Department of the Treasury that combats financial crimes.
- It plays a key role in setting AML standards, enforcing regulations, and promoting transparency in the financial system.
- FinCEN collaborates with other agencies and international partners to combat money laundering and terrorist financing.
- Financial institutions must adhere to FinCEN's reporting requirements, including filing CTRs and SARs.
- Non-compliance with FinCEN regulations can result in penalties and legal action.
Introduction to the Financial Crimes Enforcement Network (FinCEN)
Established in 1990, FinCEN serves as the primary financial intelligence unit in the United States. It collects and analyzes information on financial transactions to combat money laundering, terrorist financing, and other financial crimes.
The Purpose and Functions of FinCEN
FinCEN's primary purpose is to safeguard the financial system from illicit activities by promoting transparency and enhancing collaboration among government agencies, financial institutions, and international partners. It collects, analyzes, and disseminates financial intelligence to combat financial crimes effectively.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
FinCEN Rule: Enhancing Anti-Money Laundering (AML) Efforts
Through its rulemaking authority, FinCEN issues regulations to strengthen anti-money laundering efforts and combat illicit financial activities. These regulations impose obligations on financial institutions to implement robust AML programs, report suspicious activities, and maintain effective customer due diligence practices.
FinCEN's Role in Know Your Customer (KYC) Practices
FinCEN plays a crucial role in setting standards and guidance for Know Your Customer (KYC) practices. It emphasizes the importance of verifying customer identities, assessing customer risks, and conducting ongoing monitoring to prevent financial crimes and maintain the integrity of the financial system.
The Relationship between FinCEN and the Department of the Treasury
FinCEN operates within the United States Department of the Treasury and collaborates closely with other agencies, such as the Office of Foreign Assets Control (OFAC). This relationship enables FinCEN to coordinate efforts to combat financial crimes, enforce regulations, and ensure compliance with international standards.
Read More: What is Financial Industry Regulatory Authority & What Do They Do?
FinCEN Form and Reporting Requirements
FinCEN requires financial institutions to file various reports, including Currency Transaction Reports (CTRs) and Suspicious Activity Reports (SARs), to provide critical information on potentially illicit financial activities. These reporting requirements assist in detecting and deterring financial crimes.
Read More: All You Want to Know about the FinCEN Files
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
FinCEN's Enforcement of Financial Crime Regulations
FinCEN has the authority to enforce compliance with AML and counter-terrorist financing regulations. It conducts investigations, imposes penalties, and takes legal action against individuals and entities that violate these regulations, ensuring accountability and deterring illicit activities.
In conclusion, the Financial Crimes Enforcement Network (FinCEN) serves as a vital component of the United States' efforts to combat financial crimes. Through its intelligence gathering, rulemaking, and enforcement functions, FinCEN plays a crucial role in safeguarding the integrity of the financial system and promoting global financial security. Financial institutions must understand and comply with FinCEN's regulations to effectively combat money laundering, terrorist financing, and other financial crimes.
Case Management
Introduction
In the ever-evolving landscape of financial crime, effective Anti-Money Laundering (AML) efforts are crucial for financial institutions to protect themselves and the global financial system. AML case management plays a pivotal role in managing and streamlining investigations related to suspicious activities and potential money laundering.
In this article, we will delve into the world of AML case management, its significance in the fight against financial crime, and explore examples, templates, and AML compliance solutions that can enhance the effectiveness of AML operations. Join us as we uncover the key components and best practices of AML case management.
Key Takeaways
- AML case management is essential for financial institutions to detect, investigate, and prevent money laundering activities.
- Key components of AML case management include identification and assessment of suspicious activities, case assignment and prioritization, investigation and data gathering, collaboration and communication, and documentation and reporting.
- AML case management examples include investigating suspicious transactions, analyzing customer behaviour patterns, and conducting enhanced due diligence.
- AML case management templates provide standardized frameworks for documenting and managing cases.
- AML compliance solutions, such as technology platforms, automated monitoring systems, and risk assessment tools, enhance the effectiveness of AML case management.
- Challenges in AML case management include data quality and integration, staff training, and continuous process improvement.
Introduction to AML Case Management
AML case management refers to the systematic process of managing and investigating suspicious activities and potential instances of money laundering within a financial institution. It involves identifying, assessing, and documenting cases, as well as coordinating investigations and reporting to regulatory authorities.
Importance of AML Case Management
Effective AML case management is vital for financial institutions to ensure compliance with regulations, detect and prevent money laundering, and mitigate the risks associated with financial crime. It provides a structured approach to managing investigations, facilitating collaboration, and maintaining proper documentation.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Key Components of AML Case Management
a. Identification and Assessment of Suspicious Activities: A robust AML case management system enables the identification and assessment of suspicious activities through transaction monitoring and customer due diligence.
b. Case Assignment and Prioritization: Cases need to be assigned to investigators based on their expertise and workload. Prioritization ensures that high-risk cases are given appropriate attention and resources.
c. Investigation and Data Gathering: AML case management involves conducting thorough investigations, gathering evidence and data, and analyzing transaction patterns to identify potential money laundering activities.
d. Collaboration and Communication: Effective communication and collaboration among different departments within the financial institution, as well as with external stakeholders such as law enforcement agencies, are essential for successful AML case management.
e. Documentation and Reporting: AML case management requires accurate and comprehensive documentation of investigations, including supporting evidence and analysis. This information is used to generate reports for regulatory reporting and compliance purposes.
AML Case Management Examples
Examples of AML case management include investigating suspicious transactions, analyzing customer behaviour patterns, conducting enhanced due diligence on high-risk customers, and tracking financial flows to identify potential money laundering activities.
AML Case Management Templates
AML case management templates provide a standardized framework for documenting and managing AML cases. These templates often include fields for case details, evidence collection, investigation updates, and reporting.
AML Compliance Solutions for Case Management
a. Technology Solutions: AML compliance software and platforms offer advanced case management functionalities, including automated alerts, case tracking, data analysis, and reporting capabilities.
b. Automated Monitoring Systems: Integrating automated monitoring systems into the AML case management process enables real-time monitoring of transactions and the detection of suspicious activities based on predefined rules and algorithms.
c. Risk Assessment Tools: Risk assessment tools help in identifying high-risk customers and transactions, allowing financial institutions to allocate resources effectively and prioritize investigations.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Challenges and Best Practices in AML Case Management
a. Data Quality and Integration: Ensuring the accuracy and integrity of data is crucial for effective AML case management. Integration of data from various sources and systems can present challenges but is essential for comprehensive investigations.
b. Staff Training and Expertise: Continuous training and development programs are necessary to equip AML investigators with the knowledge and skills required to effectively manage cases and stay updated with the latest AML trends and techniques.
c. Continuous Process Improvement: Regular evaluation and improvement of AML case management processes help identify bottlenecks, streamline operations, and enhance the efficiency of investigations.
Conclusion
AML case management is a critical aspect of the fight against financial crime, enabling financial institutions to effectively detect, investigate, and prevent money laundering activities. By implementing robust case management processes, leveraging technology solutions, and fostering collaboration, financial institutions can enhance their AML operations and ensure compliance with regulatory requirements. Effective AML case management not only protects institutions from financial and reputational risks but also contributes to the integrity and stability of the global financial system.
RegTech
Introduction
In the fast-paced and highly regulated world of finance, staying compliant with ever-changing regulations is a top priority for financial institutions. This is where RegTech (Regulatory Technology) comes into play. RegTech solutions leverage technology and data analytics to streamline and enhance compliance processes, revolutionizing the way organizations meet their regulatory obligations.
In this article, we will explore the concept of RegTech, delve into RegTech companies, provide examples of RegTech use cases, and discuss the evolving RegTech ecosystem. Join us as we uncover how RegTech is transforming compliance in the financial industry.
Key Takeaways
- RegTech (Regulatory Technology) leverages technology to streamline compliance processes and meet regulatory requirements.
- RegTech companies develop innovative solutions to address specific compliance challenges in the financial industry.
- RegTech use cases include regulatory reporting, KYC/CDD, AML/CTF, risk management, and cybersecurity.
- The RegTech ecosystem thrives on collaboration, integration, and regulatory support.
- Benefits of RegTech adoption include increased efficiency, improved risk management, and cost reduction.
- Challenges in RegTech implementation include data privacy, regulatory complexities, and integration considerations.
Introduction to RegTech
RegTech, short for Regulatory Technology, refers to the use of technology-driven solutions to streamline compliance processes and ensure adherence to regulatory requirements. It encompasses a range of technologies, including artificial intelligence (AI), machine learning (ML), data analytics, blockchain, and cloud computing.
The Role of RegTech in the Financial Industry
RegTech plays a pivotal role in helping financial institutions navigate complex regulatory landscapes efficiently and effectively. By automating manual processes, improving data accuracy, and providing real-time monitoring and reporting capabilities, RegTech empowers organizations to mitigate risks, reduce costs, and enhance overall compliance effectiveness.
Read more: Importance of RegTech in the Modern Era
Read more: The Rising Case for RegTech to Address AML Risks
Read more: Reasons Behind the Rise of RegTech Companies
Read more: Combining RegTech and AML
RegTech Companies: Driving Innovation in Compliance
A growing number of RegTech companies are emerging to address the compliance challenges faced by financial institutions. These companies develop innovative solutions that leverage cutting-edge technologies to tackle specific compliance requirements.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
RegTech Use Cases: Enhancing Compliance Processes
RegTech solutions have a wide range of applications across various compliance domains. Here are some key use cases:
- Regulatory Reporting and Data Management: RegTech tools automate data collection, aggregation, and reporting, ensuring timely and accurate submission of regulatory reports.
- Know Your Customer (KYC) and Customer Due Diligence (CDD): RegTech solutions simplify and streamline KYC and CDD processes, leveraging advanced data analytics and AI to verify customer identities, screen for risks, and ensure compliance with anti-money laundering (AML) regulations.
- Anti-Money Laundering (AML) and Counter-Terrorist Financing (CTF): RegTech helps financial institutions enhance their AML and CTF efforts through real-time transaction monitoring, suspicious activity detection, and risk-based approaches.
- Risk Management and Assessment: RegTech solutions provide advanced risk assessment tools, enabling organizations to identify, measure, and manage risks effectively.
- Cybersecurity and Data Privacy: RegTech aids in strengthening cybersecurity and data privacy measures, ensuring compliance with regulations and protecting sensitive information from breaches.
The Evolving RegTech Ecosystem
The RegTech ecosystem is constantly evolving, driven by collaboration, integration, and regulatory engagement.
- Collaboration and Partnerships: RegTech companies often collaborate with financial institutions, technology providers, and regulatory bodies to develop comprehensive solutions and address industry-wide compliance challenges.
- Integration with Financial Institutions' Systems: Seamless integration of RegTech solutions with existing systems is crucial for maximizing their effectiveness. APIs and data standardization enable smooth data exchange and integration.
- Regulatory Support and Engagement: Regulators are increasingly recognizing the value of RegTech in improving compliance outcomes. They engage with industry stakeholders, provide guidance, and establish sandboxes to foster innovation in the RegTech space.
Benefits of RegTech Adoption
The adoption of RegTech offers several benefits to financial institutions, including:
- Increased efficiency and accuracy in compliance processes
- Timely detection and prevention of regulatory violations
- Cost reduction through automation and streamlined workflows
- Enhanced risk management and improved decision-making
- Greater transparency and auditability of compliance activities
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Challenges and Considerations in RegTech Implementation
While RegTech offers significant advantages, there are challenges to consider during implementation, such as data privacy and security concerns, regulatory complexities, integration with legacy systems, and the need for skilled resources to manage and leverage RegTech solutions effectively.
Conclusion
RegTech is revolutionizing compliance in the financial industry by harnessing the power of technology to streamline processes, enhance efficiency, and ensure adherence to regulatory requirements. As the regulatory landscape continues to evolve, financial institutions must embrace RegTech solutions to stay ahead, mitigate risks, and foster a culture of compliance. By leveraging RegTech, organizations can navigate complex compliance challenges with ease, while achieving cost savings and improving overall compliance effectiveness.
False Positives
Introduction
In the realm of Anti-Money Laundering (AML) compliance, false positives are a common challenge faced by financial institutions. False positives occur when an AML system or process flags a transaction or activity as suspicious or non-compliant, but upon further investigation, it is determined to be legitimate. False positives can lead to inefficiencies, increased costs, and resource strain.
In this article, we will delve into the concept of false positives in the AML context, understand their meaning, explore their impact, discuss methods to minimize errors and differentiate between false positives and false negatives.
Key Takeaways
- False positives in the AML context refer to legitimate transactions or activities flagged as suspicious or non-compliant.
- False positives can have an impact on operational costs, compliance efficiency, and customer satisfaction.
- Strategies to minimize false positives include enhancing data quality and analysis, fine-tuning AML systems, leveraging advanced technologies, and providing staff training and education.
- Differentiating between false positives and false negatives is crucial for effective risk management.
- Striking a balance between minimizing false positives and false negatives is essential for optimal AML compliance.
Introduction to False Positives in AML
False positives in the AML context refer to instances where transactions or activities are flagged as suspicious or non-compliant, but upon further investigation, they are found to be legitimate and pose no actual risk. AML systems and processes are designed to identify potential money laundering or terrorist financing activities, but the inherent complexity of financial transactions can lead to false positives.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Understanding False Positives and False Negatives
False positives and false negatives are two possible errors in AML screening processes. While false positives occur when legitimate activities are flagged as suspicious, false negatives happen when actual risks go undetected and are not flagged. Achieving the right balance between minimizing false positives and false negatives is crucial for effective AML compliance.
The Impact of False Positives in AML Compliance
False positives can have significant implications for financial institutions. They result in increased operational costs, as additional resources are required to investigate and clear flagged transactions. Moreover, false positives can strain compliance teams and delay legitimate transactions, leading to customer dissatisfaction and potential loss of business opportunities.
Examples of False Positives in AML
Examples of false positives in AML include:
- A legitimate business transaction flagged as suspicious due to unusual patterns, but later determined to be a one-time occurrence.
- Transactions involving customers with common names that match names on government watchlists, resulting in false hits.
- International wire transfers triggering alerts due to high-value amounts, even if they are legitimate business transactions.
Minimizing False Positives in AML
Financial institutions can adopt several strategies to minimize false positives in their AML processes:
- Enhanced Data Quality and Analysis: Ensuring accurate and comprehensive data collection and analysis helps reduce false positives by providing a clearer picture of customer behavior and transaction patterns.
- Fine-tuning AML Systems and Parameters: Regularly reviewing and refining AML systems and parameters based on the institution's risk profile and industry best practices can help reduce false positives without compromising compliance.
- Leveraging Advanced Technologies: Embracing advanced technologies such as machine learning, artificial intelligence, and natural language processing can enhance AML systems' accuracy, enabling better identification of true risks and minimizing false positives.
- Conducting Ongoing Staff Training and Education: Providing comprehensive training and ongoing education to AML compliance staff ensures they have the knowledge and skills to effectively interpret alerts, investigate potential risks, and differentiate between true risks and false positives.
Differentiating False Positives and False Negatives
Differentiating between false positives and false negatives is crucial in AML compliance. While false positives result in legitimate activities being flagged, false negatives represent missed or undetected risks. Striking the right balance between the two is essential to mitigate financial crime risks effectively.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
The Importance of Striking a Balance
Striking a balance between minimizing false positives and false negatives is crucial in AML compliance. Aiming for zero false positives may lead to an increase in false negatives, leaving potential risks undetected. Financial institutions must fine-tune their AML systems and processes to achieve an optimal balance based on their risk appetite and regulatory requirements.
Conclusion
False positives present a significant challenge in AML compliance, requiring financial institutions to adopt proactive measures to minimize their occurrence. By employing advanced technologies, fine-tuning systems and parameters, and investing in staff training, financial institutions can strike a balance between identifying true risks and minimizing false positives. Achieving this balance is crucial to enhancing compliance effectiveness, reducing operational costs, and maintaining customer satisfaction.
White-Box Machine Learning
Introduction
White-box machine learning is a concept that emphasizes transparency and explainability in the field of artificial intelligence. Unlike black-box models, which are often complex and difficult to interpret, white-box models provide insights into how decisions are made, enabling users to understand and validate the reasoning behind AI predictions.
In this article, we will delve into the world of white-box machine learning, explore real-world examples, discuss the difference between white-box and black-box models, and highlight the importance of transparency in AI.
Key Takeaways
- White-box machine learning emphasizes transparency and explainability in AI.
- White-box models provide insights into the decision-making process, making them interpretable and auditable.
- Examples of white-box machine learning include linear regression, decision trees, and rule-based systems.
- Transparency and explainability are essential for fairness, accountability, and compliance in various industries.
- Python offers libraries and frameworks for implementing white-box machine learning models.
- White-box models have advantages such as interpretability and auditability, but they may face challenges with complex data.
- The future of white-box machine learning holds promise as transparency becomes a critical requirement in AI systems.
What is White-Box Machine Learning?
White-box machine learning refers to the approach where models are designed with transparency and explainability in mind. It focuses on providing interpretable insights into how the model makes predictions, allowing users to understand the factors and features influencing the outcomes.
Understanding White-Box Models
White-box models are designed to be transparent, allowing users to inspect and understand their internal workings. They provide visibility into the decision-making process, making it easier to identify the key features and rules contributing to predictions.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Examples of White-Box Machine Learning
Examples of white-box machine learning include linear regression, decision trees, and rule-based systems. These models provide clear rules and explanations, making them suitable for use cases where interpretability and compliance are crucial.
White-Box vs. Black-Box Machine Learning
The primary difference between white-box and black-box machine learning lies in their interpretability. While white-box models are transparent and offer explainability, black-box models, such as deep neural networks, are complex and less interpretable.
Importance of Transparency and Explainability
Transparency and explainability are crucial in various domains, including finance, healthcare, and legal industries. White-box models allow stakeholders to understand and validate the decision-making process, ensuring fairness, accountability, and compliance.
White-Box Machine Learning in Python
Python provides several libraries and frameworks for implementing white-box machine learning models. Popular libraries such as sci-kit-learn and TensorFlow offer transparent algorithms and tools for interpreting and visualizing model outputs.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Advantages and Challenges of White-Box Models
The advantages of white-box models include interpretability, auditability, and the ability to detect biases. However, they may face challenges in handling complex and high-dimensional data, requiring careful feature engineering and model selection.
The Future of White-Box Machine Learning
As the demand for trustworthy AI increases, white-box machine learning is expected to play a vital role. Innovations in model explainability and interpretability techniques will further advance the field, enabling the widespread adoption of transparent AI systems.
Conclusion
White-box machine learning brings transparency and explainability to the forefront of AI systems. By enabling users to understand and validate the decision-making process, white-box models foster trust, accountability, and compliance. As organizations strive to deploy ethical and responsible AI, white-box machine learning techniques will continue to evolve and play a crucial role in shaping the future of transparent and interpretable AI systems.
Black-Box Machine Learning
Introduction
Black-box machine learning refers to the use of complex algorithms that produce predictions or decisions without providing explicit insights into their internal workings. While these models often achieve high accuracy, they lack transparency and interpretability.
In this article, we will delve into the world of black-box machine learning, discuss its implications, explore real-world examples, and compare it to white-box algorithms. Understanding the strengths and challenges of black-box models is crucial in the pursuit of responsible and transparent AI.
Key Takeaways
- Black-box machine learning involves complex algorithms that lack transparency and interoperability.
- Deep neural networks and ensemble methods are common examples of black-box models.
- Transparency challenges include understanding decisions, addressing biases, and complying with regulations.
- Python provides libraries like TensorFlow and PyTorch for implementing black-box machine learning models.
- White-box algorithms prioritize explainability, while black-box algorithms prioritize accuracy.
- Researchers are actively working on methods for model interpretability and explainability.
- The future of black-box machine learning lies in developing techniques that balance accuracy and transparency.
What is Black-Box Machine Learning?
Black-box machine learning involves the use of algorithms that operate as opaque systems, making it challenging to understand how predictions or decisions are made. These models are commonly employed in areas where accuracy is paramount, such as image recognition or natural language processing.
Understanding Black-Box Models
Black-box models, such as deep neural networks, are characterized by their complexity and lack of interpretability. They consist of multiple layers of interconnected nodes, making it difficult to discern the specific relationships between inputs and outputs.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Challenges and Implications of Black-Box Machine Learning
The lack of transparency in black-box models poses challenges in various domains. Understanding the reasoning behind decisions becomes challenging, raising concerns about bias, fairness, and accountability. Additionally, compliance with regulatory frameworks, such as GDPR, becomes more complex when working with opaque systems.
Examples of Black-Box Machine Learning
Examples of black-box machine learning include deep neural networks, support vector machines (SVMs), and ensemble methods like random forests and gradient boosting. These models excel in complex tasks such as speech recognition, autonomous driving, and recommendation systems.
Black-Box Machine Learning in Python
Python offers numerous libraries and frameworks for implementing black-box machine learning models. Popular libraries like TensorFlow and PyTorch provide powerful tools for building and training complex neural networks.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Comparing Black-Box and White-Box Algorithms
Black-box algorithms prioritize predictive performance over interpretability, while white-box algorithms, like decision trees or linear regression, prioritize explainability. White-box models offer clear insights into their decision-making process, whereas black-box models focus on achieving high accuracy.
Addressing the Transparency Challenge
To mitigate the lack of transparency in black-box models, researchers are actively developing methods for model interpretability and explainability. Techniques like feature importance analysis, model-agnostic methods, and visualizations aim to shed light on the decision-making process.
The Future of Black-Box Machine Learning
Efforts are underway to strike a balance between accuracy and interpretability in black-box models. The development of explainable AI and transparent machine-learning techniques will play a vital role in addressing the challenges associated with black-box algorithms.
Conclusion
Black-box machine learning has revolutionized various fields by achieving remarkable predictive performance. However, the lack of transparency and interpretability raises concerns regarding biases, fairness, and accountability. As the field advances, the development of techniques for model interpretability and explainability will be pivotal in ensuring responsible and transparent AI systems.
Penetration Testing
Introduction
In the ever-evolving landscape of cybersecurity, organizations face continuous threats from malicious actors seeking to exploit vulnerabilities. To proactively identify and address these vulnerabilities, penetration testing has emerged as a vital practice.
In this article, we will delve into the world of penetration testing, understanding its purpose, exploring various types, and gaining insights into the role of a penetration tester. By embracing penetration testing, organizations can strengthen their cybersecurity defenses and safeguard sensitive data.
Key Takeaways
- Penetration testing is a proactive approach to identify and address vulnerabilities in systems and networks.
- Penetration testers play a vital role in conducting security assessments and identifying weaknesses.
- The five stages of penetration testing include reconnaissance, scanning, exploitation, post-exploitation, and reporting.
- Different types of penetration testing, such as black-box, white-box, and gray-box testing, cater to varying levels of information access.
- Penetration testing certifications validate expertise and enhance career prospects in the field.
What is Penetration Testing?
Penetration testing, also known as ethical hacking, is a controlled process of actively assessing the security of systems, networks, and applications. It involves simulating real-world attacks to identify vulnerabilities and provide recommendations for enhancing security.
The Role of a Penetration Tester
A penetration tester is a skilled professional responsible for conducting security assessments and identifying vulnerabilities in an organization's systems. They use a combination of manual techniques and specialized tools to exploit vulnerabilities and assess the overall security posture.
The Five Stages of Penetration Testing
The penetration testing process typically involves five stages: reconnaissance, scanning, exploitation, post-exploitation, and reporting. Each stage plays a crucial role in identifying vulnerabilities, exploiting them, and providing actionable recommendations.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Types of Penetration Testing
Penetration testing can be categorized into three main types: black-box testing, white-box testing, and gray-box testing. Each type differs in terms of the tester's knowledge about the system and the level of information available.
Penetration Testing Examples
Examples of penetration testing include web application testing, network infrastructure testing, wireless network testing, social engineering assessments, and mobile application testing. These tests simulate real-world attack scenarios to identify vulnerabilities and potential entry points.
Penetration Testing Certifications
Various certifications validate the skills and knowledge of penetration testers, including Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Penetration Testing Engineer (CPTE). These certifications enhance credibility and demonstrate expertise in the field.
Career Opportunities in Penetration Testing
The demand for skilled penetration testers is growing rapidly. Career opportunities exist in industries such as cybersecurity consulting firms, government agencies, financial institutions, and large corporations. Professionals in this field can continuously enhance their skills and knowledge to stay ahead in the evolving cybersecurity landscape.
Conclusion
Penetration testing is an essential practice in cybersecurity, enabling organizations to identify vulnerabilities, mitigate risks, and strengthen their defense against cyber threats. By embracing different types of penetration testing and leveraging the skills of certified professionals, businesses can enhance their security posture and protect valuable assets. Stay ahead of the evolving threat landscape by incorporating penetration testing into your cybersecurity strategy.
Biometric Authentication
Introduction
In an era where data breaches and identity theft are rampant, traditional authentication methods such as passwords and PINs fall short of providing robust security. Enter biometric authentication, a revolutionary technology that leverages unique physical or behavioural traits to verify individuals' identities. From fingerprints to facial recognition, biometric authentication offers a seamless and secure approach to access control and identity verification.
In this comprehensive guide, we will explore the world of biometric authentication, its various types, advantages, disadvantages, and its implementation in mobile applications. Join us on this exciting journey as we unravel the power and potential of biometrics in safeguarding our digital lives.
Key Takeaways
- Biometric authentication utilizes unique physical or behavioural traits for identity verification.
- The four main types of biometrics are fingerprints, facial recognition, iris/retina scans, and voice recognition.
- Biometric authentication offers enhanced security and convenience compared to traditional methods.
- Mobile apps leverage biometric authentication to provide seamless and secure access to sensitive information.
- Enabling biometric authentication on Android devices is a straightforward process.
- Biometric authentication presents advantages such as increased security, reduced reliance on passwords, and improved user experience.
- However, there are also disadvantages to consider, including privacy concerns and potential vulnerabilities.
What is Biometric Authentication?
Biometric authentication has revolutionized the way we verify and authenticate identity in today's digital landscape. By leveraging unique physical or behavioural traits, biometric authentication provides a highly secure and convenient method of access control. With the advancements in technology, several biometric modalities have emerged, including fingerprints, facial recognition, iris scans, and voice recognition.
These modalities offer distinct advantages, such as the ability to accurately identify individuals and prevent unauthorized access. Biometric authentication not only enhances security but also improves the user experience by eliminating the need for traditional passwords or PINs. By simply presenting a biometric trait, users can gain seamless access to their devices, accounts, or facilities.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
The Four Main Types of Biometrics
Biometric authentication relies on various physical or behavioural characteristics to establish identity. There are four main types of biometrics used for authentication:
- Fingerprint Recognition: The most widely recognized biometric modality, fingerprints offer high accuracy and reliability. Each person has a unique fingerprint pattern that can be captured and compared for authentication purposes.
- Facial Recognition: This modality analyzes facial features and patterns to verify identity. Facial recognition systems use algorithms to compare the captured image with stored templates to grant or deny access.
- Iris Scanning: By examining the intricate patterns in the iris, iris scanning provides a highly accurate method of identification. Iris recognition systems use near-infrared light to capture detailed images of the iris, which can be compared for authentication.
- Voice Recognition: Voice biometrics analyzes vocal characteristics, such as pitch, tone, and speech patterns, to verify identity. Voice recognition systems capture and analyze the unique voiceprint of individuals for authentication purposes.
- Retina Scanning: Retina scanning biometrics involve capturing the blood vessel patterns in the back of the eye. This modality offers a high level of accuracy but requires specialized hardware for capturing the retina image.
Each of these biometric modalities has its own strengths and considerations, and organizations may choose the most suitable option based on their specific security requirements and user experience goals.
Advantages and Disadvantages of Biometric Authentication
Biometric authentication offers several advantages over traditional authentication methods, but it also has some limitations. Here are the key advantages and disadvantages of biometric authentication:
Advantages
- Enhanced Security: Biometric traits are unique to individuals, making it difficult for unauthorized individuals to impersonate or replicate.
- Convenience: Biometric authentication eliminates the need to remember passwords or carry physical tokens, providing a seamless user experience.
- Speed and Efficiency: Biometric authentication is quick and efficient, reducing the authentication process time and enhancing productivity.
- Scalability: Biometric systems can handle a large number of users, making them suitable for organizations of all sizes.
Disadvantages
- Privacy Concerns: Biometric data is highly personal and raises privacy concerns, as it involves capturing and storing sensitive information.
- Vulnerability to Spoofing: Biometric systems can be susceptible to spoofing attempts, where attackers try to replicate or manipulate biometric traits to gain unauthorized access.
- Cost and Implementation: Implementing biometric authentication systems can be expensive, requiring specialized hardware, software, and infrastructure.
- Cultural and Social Acceptance: Some individuals may have cultural or social reservations about providing their biometric information, leading to resistance or reluctance to adopt biometric authentication.
- False Acceptance and False Rejection: Biometric systems may experience false acceptance (authenticating an imposter) or false rejection (rejecting a legitimate user), impacting the overall accuracy and reliability.
Organizations considering the implementation of biometric authentication should carefully evaluate these advantages and disadvantages to ensure a balanced approach that addresses security concerns while considering user privacy and acceptance.
Biometric Authentication in Mobile Apps
Biometric authentication has become increasingly prevalent in mobile apps, offering a secure and seamless user experience. Here's how biometric authentication works in mobile apps:
- Enrollment: Users are prompted to register their biometric data, such as fingerprints or facial features, during the app setup process.
- Biometric Data Capture: The mobile device's biometric sensor captures the user's biometric traits, converting them into unique digital templates.
- Template Storage: The digital templates are securely stored within the device's hardware or protected enclave, ensuring the privacy and integrity of the biometric data.
- Authentication Process: When a user attempts to access the app, they are prompted to authenticate using their enrolled biometric trait. The device compares the captured biometric data with the stored templates for verification.
- Access Grant or Denial: If the biometric data matches the stored templates, access is granted, and the user can proceed with using the app. Otherwise, access is denied, and alternative authentication methods may be required.
Biometric authentication in mobile apps enhances security, eliminates the need for passwords, and provides a convenient and frictionless user experience, making it a preferred choice for many app developers and users.
Biometric Devices: Enabling Secure Authentication
Biometric devices play a crucial role in enabling secure authentication through the use of biometric traits. These devices are equipped with specialized sensors and algorithms to capture and process biometric data. Here are some commonly used biometric devices:
- Fingerprint Scanners: These devices capture fingerprint images and convert them into digital templates for authentication.
- Facial Recognition Cameras: Equipped with high-resolution cameras and facial recognition algorithms, these devices capture and analyze facial features for authentication purposes.
- Iris Scanners: Iris scanning devices use near-infrared light to capture detailed images of the iris, enabling accurate authentication based on unique iris patterns.
- Voice Recognition Systems: These devices capture and analyze vocal characteristics to authenticate users based on their unique voiceprints.
- Retina Scanners: Retina scanning devices capture and analyze the blood vessel patterns in the back of the eye for authentication.
Biometric devices vary in terms of form factor, functionality, and integration capabilities. They can be integrated into various systems and applications, such as smartphones, access control systems, and time and attendance solutions, to provide secure and reliable authentication methods.
Biometric Identification: Advancing Authentication Methods
Biometric identification is a powerful technology that enables precise and efficient authentication. It involves the process of recognizing individuals based on their unique biometric traits. Here's how biometric identification works:
- Enrollment: During the enrollment phase, an individual's biometric data is captured and recorded in a database. This can involve scanning fingerprints, capturing facial features, or other applicable biometric modalities.
- Template Creation: The captured biometric data is processed to create a digital template that represents the unique characteristics of the individual's biometric traits. This template serves as a reference for future comparisons.
- Matching and Comparison: When authentication is required, the individual's biometric trait is captured again and compared to the stored template. Algorithms analyze the captured data and measure its similarity to the template.
- Authentication Decision: Based on the comparison results, the system determines whether the captured biometric trait matches the stored template within an acceptable threshold. If the match is successful, authentication is granted. Otherwise, access is denied.
Biometric identification offers numerous applications, including access control to secure facilities, unlocking devices, authenticating transactions, and verifying identities in various industries, such as banking, healthcare, and law enforcement. It provides a reliable and efficient method of establishing identity while minimizing the vulnerabilities associated with traditional authentication methods.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Conclusion
In a world where digital security is of utmost importance, biometric authentication emerges as a powerful solution. By harnessing unique physical or behavioural traits, biometrics provides a robust and convenient method of identity verification. Whether through fingerprints, facial recognition, iris scans, or voice recognition, biometric authentication offers enhanced security and user experience across various industries and applications.
However, it's essential to consider the advantages, disadvantages, and potential risks associated with this technology. As we continue to explore and embrace biometric authentication, we must strike a balance between security, privacy, and usability to ensure a safer and more seamless digital future.
Transport Layer Security
Introduction
In today's digital landscape, secure communication is paramount to safeguarding sensitive information. Transport Layer Security (TLS) is a crucial technology that provides encryption and authentication for data transmission over computer networks.
In this article, we will explore the fundamentals of TLS, its relationship with SSL (Secure Sockets Layer), and how it ensures secure connections. We will delve into the inner workings of TLS, discuss its role in cryptography, and shed light on TLS security best practices. By the end, you will have a comprehensive understanding of TLS and its importance in maintaining secure communication.
Key Takeaways
- TLS is a cryptographic protocol that ensures secure communication over computer networks.
- TLS and SSL are closely related protocols, with TLS superseding SSL due to security enhancements.
- TLS provides encryption, authentication, and data integrity to protect sensitive information.
- Enabling TLS involves configuring the appropriate protocols, certificates, and cipher suites.
- Understanding TLS security is essential to mitigate risks and safeguard against vulnerabilities.
Understanding Transport Layer Security (TLS)
Transport Layer Security (TLS) is a cryptographic protocol that ensures secure communication over computer networks. It operates at the transport layer of the TCP/IP protocol suite and provides encryption, authentication, and data integrity mechanisms. By establishing a secure connection between communicating entities, TLS prevents eavesdropping, tampering, and unauthorized access to sensitive information.
The Role of TLS in Network Security
TLS plays a crucial role in network security by providing a secure channel for data transmission. It protects against various types of attacks, including eavesdropping, man-in-the-middle attacks, and data tampering. By encrypting the data, TLS ensures that only the intended recipients can access and decipher the information, keeping it confidential and secure. Additionally, TLS employs authentication mechanisms to verify the identities of communicating parties, preventing unauthorized entities from gaining access to sensitive data.
The Difference between TLS and SSL
TLS and SSL (Secure Sockets Layer) are cryptographic protocols that provide secure communication. While SSL was the predecessor of TLS, TLS has largely replaced SSL due to security vulnerabilities in older SSL versions. TLS and SSL share many similarities in terms of functionality and purpose, but TLS offers more robust security features and stronger encryption algorithms. It is important to note that the terms "TLS" and "SSL" are often used interchangeably, but TLS is the more modern and secure protocol.
Enabling and Configuring TLS
To enable and configure TLS, several steps need to be followed. First, the TLS protocol version must be selected, considering both security and compatibility requirements. The choice of cypher suites, which determine the encryption algorithms and key exchange mechanisms, should be carefully considered to ensure a balance between security and performance.
Additionally, proper certificate management, including obtaining and renewing digital certificates from trusted certificate authorities (CAs), is essential for establishing the authenticity of the communicating parties. Regular updates to TLS versions and patches are necessary to address any security vulnerabilities that may arise.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Best Practices for TLS Security
Implementing TLS correctly requires adherence to best practices to maximize its effectiveness. Some key practices include:
- Strong Cipher Suites: Choose cypher suites that provide robust encryption and key exchange algorithms, avoiding weak or deprecated options.
- TLS Version Updates: Stay up-to-date with the latest TLS versions and apply patches promptly to address security vulnerabilities.
- Certificate Validation: Validate certificates using trusted certificate authorities to ensure the authenticity of the communicating parties.
- Perfect Forward Secrecy: Enable Perfect Forward Secrecy (PFS), which ensures that session keys are ephemeral and cannot be compromised even if the long-term private key is compromised.
- HSTS and HPKP: Implement HTTP Strict Transport Security (HSTS) and HTTP Public Key Pinning (HPKP) to enforce the use of secure connections and protect against certificate-related attacks.
- Regular Auditing and Monitoring: Perform regular audits and monitoring of TLS configurations to detect and mitigate any potential security issues.
By following these best practices, individuals and organizations can enhance the security of their network communications and protect sensitive data from unauthorized access and tampering.
The Future of TLS and Emerging Trends
As technology evolves and new security threats emerge, the TLS protocol continues to evolve as well. Some emerging trends in TLS include the adoption of TLS 1.3, which offers improved security and performance enhancements. Additionally, the development of post-quantum cryptography aims to address the potential threats posed by quantum computers to existing cryptographic algorithms. As the Internet of things (IoT) expands, ensuring secure communication through TLS becomes even more critical to safeguard sensitive data transmitted between IoT devices.
In conclusion, understanding Transport Layer Security (TLS) and its role in network security is essential for protecting sensitive information and ensuring secure communication. TLS provides encryption, authentication, and data integrity mechanisms that safeguard data transmission from eavesdropping, tampering, and unauthorized access. By establishing a secure channel between communicating entities, TLS prevents security breaches and maintains the privacy and integrity of data.
Two-Factor Authentication
Introduction
In today's digital landscape, securing online accounts is of paramount importance. With cyber threats becoming more sophisticated, relying solely on passwords for authentication is no longer sufficient. This is where Two-Factor Authentication (2FA) comes into play. 2FA provides an additional layer of security by requiring users to provide two separate authentication factors before accessing their accounts.
This article explores the concept of 2FA, its working principles, and the benefits it offers in safeguarding sensitive information.
Key Takeaways
- Two-Factor Authentication (2FA) adds an extra layer of security to online accounts.
- It requires users to provide two authentication factors: something they know (password) and something they have (e.g., a mobile device or security token).
- 2FA helps protect against unauthorized access, even if passwords are compromised.
- Popular examples of 2FA include authentication apps, SMS codes, and biometrics.
- Enabling 2FA is a proactive step to enhance account security and mitigate the risks of data breaches.
How Does Two-Factor Authentication (2FA) Work?
Two-Factor Authentication (2FA) functions on the principle of using two separate factors to verify a user's identity. These factors fall into three categories:
- Knowledge Factors: This includes something the user knows, such as a password, PIN, or security questions.
- Possession Factors: This involves something the user possesses, such as a mobile device, security token, or smart card.
- Inherence Factors: This relates to something the user is, such as biometric traits like fingerprints, facial recognition, or iris scans.
By combining factors from different categories, 2FA significantly enhances account security. Even if an attacker manages to obtain the user's password, they would still need the second factor to gain access, making unauthorized access much more challenging.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Workflow of 2FA
The workflow of 2FA typically involves the following steps:
- User Initiation: When logging into an account, the user enters their username and password as the first authentication factor.
- Second-Factor Verification: Once the username and password are verified, the system prompts the user to provide the second authentication factor. This can be done through various methods, such as receiving an SMS code, using an authentication app, or scanning a QR code.
- Authentication and Access: The system validates the second factor and, if successful, grants access to the account. If the second factor is not provided or fails verification, access is denied.
By implementing this two-step authentication process, 2FA adds an additional layer of security and reduces the risk of unauthorized access.
Benefits of Two-Factor Authentication (2FA)
Enhanced Account Security
2FA offers several benefits that significantly strengthen account security:
- Protection Against Password-Based Attacks: 2FA mitigates the risks of password-based attacks, such as brute-force attacks or credential stuffing. Even if an attacker obtains the user's password, they would still need the second factor to gain access.
- Mitigation of Phishing Attacks: Phishing attacks aim to trick users into revealing their credentials on fake websites. With 2FA, even if users unknowingly enter their passwords on fraudulent sites, the attackers would still require the second factor to gain access, providing an extra layer of protection against phishing attempts.
- Securing Multiple Online Accounts: Many individuals use the same or similar passwords across multiple online accounts, making them vulnerable to credential breaches. By enabling 2FA for each account, users add an additional barrier that significantly reduces the risk of unauthorized access.
Convenience and User Experience
While enhancing security, 2FA also offers convenience and a positive user experience:
- Flexible Authentication Methods: 2FA supports various authentication methods, allowing users to choose the option that best suits their preferences and devices. Popular methods include authentication apps, SMS codes, email verification, hardware tokens, and biometric authentication.
- Seamless Integration: 2FA can be seamlessly integrated into existing login processes without causing major disruptions. Many online platforms and service providers offer built-in 2FA features, simplifying the implementation process for users.
- One-Time Setup: Once users set up 2FA for their accounts, the additional authentication step becomes a seamless part of the login process. Users can choose to remember trusted devices, making subsequent logins even more convenient.
Examples of Two-Factor Authentication (2FA) in Practice
Popular 2FA Methods
- Authentication Apps: Apps like Google Authenticator, Microsoft Authenticator, and Authy generate one-time verification codes that users enter during the login process.
- SMS Codes: Users receive a unique verification code via SMS, which they enter to complete the authentication.
- Biometric Authentication: This method uses unique biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify the user's identity.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Major Online Platforms and 2FA
- Google: Google offers 2FA through its Google Authenticator app, SMS codes, or prompts sent to trusted devices. Users can enable 2FA for their Google accounts, including Gmail, Google Drive, and Google Workspace.
- Facebook: Facebook provides 2FA options such as SMS codes, authentication apps, and hardware security keys. Users can enable 2FA to protect their Facebook accounts from unauthorized access.
- Apple: Apple offers 2FA for Apple ID accounts, ensuring enhanced security for iCloud, App Store, and other Apple services. Users can enable 2FA and receive verification codes on trusted devices.
Conclusion
Two-Factor Authentication (2FA) is an essential security measure that significantly strengthens account protection in an increasingly digital world. By combining multiple authentication factors, such as passwords, authentication apps, or biometrics, 2FA provides an additional layer of security and reduces the risks of unauthorized access and data breaches. With its convenience and compatibility with various online platforms, enabling 2FA is a proactive step towards safeguarding your online activities.
Public Key Infrastructure
Introduction
In today's digital landscape, where information security is paramount, Public Key Infrastructure (PKI) plays a critical role in ensuring secure communication and safeguarding sensitive data. PKI is a comprehensive system that enables the encryption, authentication, and integrity of digital information through the use of cryptographic keys. This article dives deep into the world of PKI, exploring its components, examples, and the significance of this technology in modern cryptography.
Key Takeaways
- PKI consists of various components such as Certificate Authority (CA), Registration Authority (RA), Certificate Repository, and Certificate Revocation List (CRL) which together help in ensuring secure communication.
- The PKI infrastructure carries out responsibilities such as key generation, certificate issuance, certificate validation, and certificate revocation.
- PKI finds applications in securing web communications via TLS/SSL protocols and in facilitating the digital signing of documents, ensuring their authenticity and integrity.
- While PKI is a powerful tool for enhancing security, it comes with challenges like the potential compromise of private keys.
- PKI systems must comply with the X.509 standard, which defines the format and structure of digital certificates.
Understanding PKI: How It Works
The Components of PKI
PKI consists of several key components that work together to establish trust and enable secure communication:
Certificate Authority (CA)
- Responsible for issuing and managing digital certificates.
- Verifies the identity of entities requesting certificates.
- Signs and binds the public key to the entity's identity.
Registration Authority (RA)
- Assists the CA in verifying the identity of certificate applicants.
- Performs administrative tasks related to certificate enrollment.
Certificate Repository
- Stores and manages issued certificates.
- Allows users to access and retrieve certificates when needed
Certificate Revocation List (CRL)
- Contains a list of revoked or expired certificates.
- Provides a mechanism for entities to check the validity of certificates.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Examples of PKI Implementation
PKI finds applications in various domains where secure communication and data integrity are crucial:
Secure Email Communication
- PKI enables the use of digital signatures to verify the authenticity and integrity of email messages.
- Recipients can validate the sender's identity and ensure the message hasn't been tampered with.
Secure Web Communication
- PKI is utilized in the implementation of Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols.
- Websites use SSL/TLS certificates to establish secure connections and encrypt data transmitted between the server and client.
Secure Document Signing
- PKI facilitates the signing of digital documents with a unique digital signature.
- Digital signatures provide non-repudiation, ensuring the integrity and authenticity of the signed document.
The Responsibilities of PKI
A PKI infrastructure carries out four key responsibilities to ensure secure communication:
Key Generation
- PKI generates pairs of cryptographic keys: public and private keys.
- Public keys are freely distributed, while private keys remain securely held by the key owner.
Certificate Issuance
- The CA issues digital certificates after verifying the identity of certificate applicants.
- These certificates contain the public key and other relevant information, digitally signed by the CA.
Certificate Validation
- PKI enables the validation of digital certificates during communication.
- Recipients can verify the certificate's authenticity, integrity, and validity before establishing secure connections.
Certificate Revocation
- PKI provides mechanisms to revoke certificates if they are compromised, expired, or no longer valid.
- Certificate revocation ensures that entities relying on certificates are not misled by compromised or outdated keys.
Risks Associated with PKI: Mitigating Security Challenges
While PKI enhances security, certain risks and challenges are associated with its implementation:
- Compromised Private Keys: If private keys fall into the wrong hands, attackers can impersonate the legitimate key owner and decrypt encrypted data.
- Weak Certificate Validation
Strengthening Security Measures
To mitigate the risks associated with PKI, several measures can be implemented:
Secure Key Management
- Implement robust key management practices to protect private keys.
- Store private keys in secure hardware devices or encrypted containers.
Regular Certificate Revocation Checks
- Maintain up-to-date Certificate Revocation Lists (CRL) and Online Certificate Status Protocol (OCSP) services.
- Perform regular checks to ensure the validity of certificates before establishing secure connections.
Two-Factor Authentication
- Combine PKI with additional authentication factors, such as passwords or biometrics, to add an extra layer of security.
- This approach reduces the risk of unauthorized access even if a private key is compromised.
{{cta('31af77a9-1ccc-4abd-a9f1-28412872c7a2','justifycenter')}}
PKI Compliance and Standards
X.509 Compliance
PKI systems must adhere to the X.509 standard, which defines the format and structure of digital certificates:
X.509 Certificate Format
- X.509 specifies the format for public key certificates, including the data fields and encoding rules.
- It ensures interoperability and compatibility among different PKI systems.
X.509v3 Extensions
- X.509v3 introduces extensions that provide additional information within the digital certificate.
- Extensions can include details such as subject alternative names, key usage, and certificate policies.
Importance of PKI in Cryptography
PKI plays a crucial role in modern cryptography, offering significant benefits and addressing key challenges:
Secure Communication
- PKI ensures the confidentiality, integrity, and authenticity of digital information exchanged between parties.
- It provides a secure foundation for secure email communication, web browsing, and document signing.
Trust and Identity Verification
- PKI enables entities to verify the identity of users and establish trust in digital transactions.
- Digital certificates issued by trusted CAs validate the authenticity of entities' public keys.
Non-Repudiation
- PKI enables non-repudiation, ensuring that the originator of a digital message cannot deny its authenticity or integrity.
- Digital signatures generated with private keys provide strong evidence of the message's origin.
Conclusion
Public Key Infrastructure (PKI) is a critical technology in ensuring secure communication and establishing trust in the digital world. With its components, such as Certificate Authorities, Registration Authorities, and Certificate Repositories, PKI enables the issuance, validation, and revocation of digital certificates. Implementing PKI safeguards against risks and enables secure applications like email communication, web browsing, and document signing.
Adherence to standards like X.509 ensures interoperability and compatibility among different PKI systems. PKI's importance in modern cryptography lies in secure communication, trust verification, and non-repudiation. By leveraging PKI, organizations can enhance security and protect sensitive information in today's digital landscape.
Multi-Factor Authentication
Introduction
In an increasingly digital world, securing sensitive information has become more critical than ever. Cyberattacks and data breaches are on the rise, making traditional username and password authentication vulnerable. This is where Multi-Factor Authentication (MFA) comes into play. MFA adds an extra layer of security by requiring users to provide multiple factors to prove their identity.
In this article, we will delve into the world of Multi-Factor Authentication, exploring its purpose, benefits, and practical applications across various platforms.
Key Takeaways
- Multi-factor authentication (MFA) provides an additional layer of security beyond username and password authentication.
- MFA helps protect against unauthorized access, phishing attacks, and credential theft.
- Popular platforms like Google and Office 365 offer MFA options to enhance user security.
- Two-factor authentication (2FA) is a common form of MFA that uses two different factors to verify identity.
- MFA plays a significant role in securing login processes, especially in sensitive sectors like banking.
What is MFA and How Does it Work?
Multi-factor authentication (MFA) is a security measure that goes beyond the traditional username and password authentication method. It requires users to provide multiple factors or credentials to verify their identity and gain access to a system or platform. These factors can include something you know (such as a password or PIN), something you have (such as a mobile device or security token), and something you are (such as a fingerprint or facial recognition).
The combination of these factors enhances the security of the authentication process by adding an extra layer of protection. When a user attempts to log in, they must successfully provide the required factors, which are verified by the system, before they are granted access. This multi-layered approach significantly reduces the risk of unauthorized access and strengthens the overall security posture.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Benefits of MFA
Multi-factor authentication (MFA) offers several key benefits that make it an essential security measure in today's digital landscape.
- Firstly, MFA provides an additional layer of protection against unauthorized access and cyber threats. Even if an attacker manages to obtain a user's password, they would still need to possess the other required factors to gain access, making it much more difficult for them to compromise the account.
- Secondly, MFA enhances the security of sensitive data and systems, particularly in industries like finance, healthcare, and government where the protection of confidential information is paramount. By implementing MFA, organizations can significantly reduce the risk of data breaches and unauthorized data access.
- Additionally, MFA can help prevent or mitigate the impact of phishing attacks, as the attacker would not have access to the user's physical device or other verification factors.
Overall, MFA strengthens the authentication process, safeguards user accounts, and provides peace of mind in an increasingly interconnected world.
Implementing MFA in Different Environments
Multi-Factor Authentication (MFA) can be implemented in various environments, including personal devices, online platforms, and enterprise systems. In personal devices, such as smartphones or laptops, users can enable MFA by setting up biometric authentication methods like fingerprint or facial recognition, in addition to a passcode or PIN. Many popular online platforms, such as social media sites and email providers, offer MFA as an option for users to enhance the security of their accounts. This often involves linking a mobile phone number or email address to the account and receiving a verification code during the login process.
In enterprise settings, MFA can be integrated into the authentication systems of employee access controls. This can include the use of smart cards, security tokens, or mobile apps that generate one-time passwords. By implementing MFA across different environments, individuals and organizations can create a consistent and robust security framework that protects against unauthorized access.
Challenges and Considerations of MFA Implementation
While Multi-Factor Authentication (MFA) offers significant security advantages, there are some challenges and considerations to keep in mind during implementation. One challenge is user adoption and convenience. MFA adds an extra step to the authentication process, which some users can perceive as cumbersome or time-consuming. Organizations should focus on providing user-friendly MFA methods and educating users about the importance of this security measure to encourage adoption.
Another consideration is the management of MFA credentials. Organizations must establish robust procedures for managing and securely storing authentication factors, such as encryption keys or tokens. Additionally, compatibility and integration with existing systems can be a challenge when implementing MFA across different platforms and applications. It is crucial to choose MFA solutions that can seamlessly integrate with the existing technology stack to ensure a smooth user experience.
Lastly, organizations should regularly evaluate and update their MFA strategies to address evolving security threats and stay up to date with industry best practices.
The Future of MFA: Emerging Trends and Technologies
The field of Multi-Factor Authentication (MFA) continues to evolve as technology advances and new threats emerge. One emerging trend is the use of biometric authentication as an MFA factor. Biometrics, such as fingerprint, iris, or voice recognition, offer unique and highly secure identifiers that are difficult to replicate. The widespread adoption of biometric-enabled devices, such as smartphones and tablets, has facilitated the integration of biometric MFA methods into various applications and systems.
Another emerging technology is the use of behavioural biometrics, which analyzes user behaviour patterns to authenticate their identity. This includes factors like typing speed, mouse movement, and touchscreen gestures, which can be unique to each individual. As artificial intelligence and machine learning algorithms improve, behavioural biometrics have the potential to provide seamless and continuous authentication without requiring explicit user actions.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Furthermore, the use of hardware tokens or security keys, such as Universal Second Factor (U2F) devices, is gaining popularity due to their enhanced security and ease of use. These devices generate unique cryptographic codes for each authentication attempt, adding an extra layer of protection. As the technology landscape continues to advance, we can expect to see further innovations in MFA that prioritize security, convenience, and user experience
Conclusion
As cyber threats continue to evolve, adopting robust security measures is crucial for safeguarding sensitive information. Multi-factor authentication (MFA) offers an effective defense against unauthorized access, phishing attacks, and credential theft. By requiring users to provide multiple factors to verify their identity, MFA adds an extra layer of security that significantly reduces the risk of data breaches.
Two-factor authentication (2FA) further enhances login security by combining two different factors. In the banking sector, MFA plays a vital role in securing online banking transactions and protecting customer data. Embracing Multi-Factor Authentication empowers individuals and organizations to take control of their online security and enjoy a safer digital experience.
Secure Sockets Layer
Introduction
In an era where data is the new oil, protecting it becomes paramount. As we navigate the digital world, carrying out various online transactions, visiting numerous websites, and sharing personal information, we are often oblivious to the invisible security blanket that keeps our data safe from prying eyes. This blanket is known as Secure Sockets Layer (SSL), a cornerstone in the foundation of digital security.
This article delves into the intricacies of SSL, shedding light on its purpose, functioning, various types, and its role in fortifying digital communication.
Key Takeaways
- Secure Sockets Layer (SSL) is a vital protocol that provides a secure channel for transmitting sensitive data over the internet. Its primary role is to encrypt the data before transmission and decrypt it upon receipt.
- While SSL is commonly referred to, the technology in use today is its successor, Transport Layer Security (TLS). The latest version of TLS, TLS 1.3, provides the most secure communication.
- The SSL/TLS process begins with an 'SSL Handshake', a negotiation phase where the server and client agree on the details of the secure connection.
- There are three primary types of SSL certificates - Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV). Each has varying levels of validation and trust, catering to different business needs.
- SSL is crucial in sectors like e-commerce, finance, healthcare, and education, securing user data and building trust and credibility among users.
- Implementing SSL is a proactive measure that businesses and website owners need to take, along with other robust security practices, for a comprehensive and secure digital environment.
Understanding the Secure Sockets Layer (SSL)
At its core, SSL is a standard security protocol used to establish an encrypted link between a web server and a browser. This digital armour ensures that all data passed between the server and browser remains private and integral, protecting it from potential eavesdropping, data tampering, or message forgery.
SSL, short for Secure Sockets Layer, is the predecessor to Transport Layer Security (TLS), both of which are commonly used interchangeably. Together, SSL and TLS form the bedrock of secure internet communication, providing the necessary encryption for sensitive data like credit card numbers, Social Security numbers, and login credentials.
Is Secure Sockets Layer (SSL) Still Considered Secure?
The rapid advancement in cyber threats has led to the evolution of SSL to Transport Layer Security (TLS), an improved, more secure protocol. While SSL versions are now largely deprecated due to vulnerabilities, the term SSL is still widely used to describe both SSL and TLS. The last version of SSL, SSLv3, is considered insecure and its use is not recommended. Today's secure web uses TLS, the successor to SSL, with TLS 1.3 being the latest and most secure version. However, for the purpose of common parlance, 'SSL' is often used to refer to these secure connections.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Mechanism Behind Secure Sockets Layer (SSL): How Does it Work?
The strength of SSL lies in its complex architecture, which, despite its intricacy, ensures smooth and secure online interactions. The process begins with an 'SSL Handshake,' a silent communication occurring within milliseconds that establishes a secure connection between the server and the client.
To put it simply, the handshake involves a series of steps:
- The client sends a 'ClientHello' message to the server, indicating its willingness to establish a secure connection and the SSL or TLS versions it supports.
- The server responds with a 'ServerHello' message, selecting the most secure common protocol. It also sends its digital certificate, issued by a trusted third-party Certificate Authority (CA), for verification.
- The client verifies the server's certificate and generates a symmetric session key, encrypted with the server's public key, and sends it to the server.
- The server decrypts the session key using its private key, and both the server and client use this session key for encrypted communication.
This swift, behind-the-scenes process ensures that your sensitive data is securely transported in the vast ocean of digital information.
Types of Secure Sockets Layer (SSL)
SSL certificates are available in different types, catering to various business needs. The common ones are:
- Domain Validation (DV) SSL: This provides a basic level of security and is used for blogs or personal websites where the level of user trust and validation is relatively low.
- Organization Validation (OV) SSL: A step up from DV SSL, this certificate involves a more rigorous validation process and is used by businesses and organizations to authenticate their identity.
- Extended Validation (EV) SSL: This certificate requires the highest level of validation, ensuring the maximum level of user trust. It's used by large businesses and e-commerce websites dealing with sensitive customer data.
Each SSL certificate type has its unique features, catering to different needs based on the sensitivity of data handled, and consequently offering varied levels of trust and assurance.
Real-world Applications: Secure Socket Layer Examples
SSL finds extensive application across various sectors, underpinning the security infrastructure of the digital world. Whether it's online shopping, banking, webmail, or simply browsing, SSL plays a crucial role in safeguarding user data. To understand its utility better, consider the 'https' you often see in your web browser's address bar. The 's' here stands for 'secure,' indicating that the website you're visiting uses SSL encryption to protect your data.
Furthermore, businesses operating in sectors like e-commerce, finance, healthcare, and education, where the integrity and confidentiality of user data are critical, invariably leverage SSL to secure their online communications. This not only secures their customer data but also helps in building trust and credibility among their user base.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Prevention: Secure Your Online Space with SSL
While SSL encryption is integral to secure online communication, implementing it is a proactive measure that businesses and website owners need to take. To ensure your online space is secure, it's essential to procure an SSL certificate from a reliable Certificate Authority. Upon successful domain validation and based on the certificate type, the SSL certificate is issued and can then be installed on the server.
Ensuring regular updates and using the latest version of the SSL/TLS protocol also forms a part of the prevention strategy against potential cyber threats. Employing robust security practices along with SSL like secure password policies, two-factor authentication, and regular vulnerability assessments can help create a comprehensive and secure digital environment.
Conclusion
Secure Sockets Layer (SSL), despite being a term often used to encompass both SSL and its successor TLS, is an integral part of our digital interactions. This invisible security layer tirelessly works behind the scenes to protect our sensitive data from falling into the wrong hands. Whether you're an individual browsing the web or a business handling customer data, understanding SSL and its workings is the first step in appreciating the secure digital environment it provides. As we continue to move towards a more interconnected world, ensuring the implementation and proper use of SSL is no longer an option but a necessity for secure and trusted online communication.
Intrusion Detection Systems
Introduction
In the digital age, the threat of cyber attacks looms large over every enterprise, big or small. A single intrusion can result in catastrophic data loss, substantial financial hits, and immense reputational damage. An Intrusion Detection System (IDS), as a key tool in a network administrator's arsenal, is designed to identify and alert these potential threats, making them a vital component in the overarching sphere of cybersecurity.
Key Takeaways
- Intrusion Detection Systems (IDS) monitor networks or systems for potential threats, enhancing cybersecurity measures.
- IDS function based on two principles: anomaly detection and signature detection.
- There are three main types of IDS: Network Intrusion Detection Systems (NIDS), Host-Based Intrusion Detection Systems (HIDS), and Application Protocol-Based Intrusion Detection Systems (APIDS).
- IDS shares a common goal with Intrusion Prevention Systems (IPS) in identifying cyber threats, but IPS takes a more proactive approach by preventing detected threats.
- IDS plays a critical role in cybersecurity, bolstering an organization's ability to identify, respond, and remediate threats promptly.
- The future of IDS looks promising, with advancements in artificial intelligence and machine learning expected to further enhance their threat detection capabilities.
Defining Intrusion Detection Systems (IDS)
At its core, an Intrusion Detection System (IDS) is a software application or device that monitors a network or systems for malicious activity or policy violations. It serves as a digital watchtower, continuously scanning for anomalies that may signal an intrusion. By analyzing network traffic and comparing it against a database of known threat patterns, the IDS provides an extra layer of security, adding depth to a robust defense strategy.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
IDS: An Overview and Its Functioning
In essence, IDS functions on two fundamental principles - anomaly detection and signature detection. Anomaly detection involves identifying behavior that deviates from a pre-established standard 'normal' behavior. Conversely, signature detection relies on recognizing known malicious patterns in network traffic, similar to how antivirus software detects known malware.
The functioning of IDS can be encapsulated in the following steps:
- Collects and analyzes network traffic data.
- Compares data against pre-established baselines and known threat signatures.
- Generates alerts upon detection of suspicious activity.
- Records information related to the detected activity for further analysis.
Types of Intrusion Detection Systems
IDS can be broadly classified into three categories: Network Intrusion Detection Systems (NIDS), Host-Based Intrusion Detection Systems (HIDS), and Application Protocol-Based Intrusion Detection Systems (APIDS).
- NIDS: Monitors and analyzes network traffic, looking out for suspicious activity that could indicate a network attack.
- HIDS: Installed on a specific host, HIDS scans the host for unusual activity, such as changes in system files or attempts to access secure areas.
- APIDS: Targets specific application protocols to detect suspicious transactions, particularly useful in identifying attacks that conventional NIDS or HIDS might miss.
IDS vs IPS: A Comparative Perspective
While IDS and Intrusion Prevention Systems (IPS) share the same goal of identifying cyber threats, they differ in their approach. IDS is a monitoring system that detects potential threats and alerts the network administrators. In contrast, an IPS actively blocks or prevents detected threats from inflicting damage, making it a more proactive defense measure.
Key Components of IDS
An IDS comprises five core components that work together to detect, document, and deter intrusions:
- Sensors: Gather raw data, often in the form of network packets.
- Analyzers: Evaluate the collected data and compare it with known threat signatures or abnormal activity patterns.
- User interface: Allows administrators to interact with, configure, and control the IDS.
- Database: Stores event information and the IDS configuration settings.
- Alert system: Notifies administrators of potential security breaches.
Importance of IDS in Cybersecurity
In the context of ever-evolving cyber threats, IDS plays an essential role in creating a robust and resilient cybersecurity infrastructure. It enhances an organization's ability to identify potential threats promptly, empowering them to respond and remediate them before significant damage can occur. IDS also helps meet compliance requirements, providing reports and logs that serve as proof of due diligence in maintaining a secure environment.
Effective Intrusion Detection Techniques
Several techniques are used in intrusion detection, each offering its strengths and weaknesses.
- Signature-Based Detection: This method matches network activity against a database of known threat signatures. While highly effective against known threats, it may fail to detect new, unseen attacks.
- Anomaly-Based Detection: By establishing a baseline of 'normal' network behaviour, this technique identifies anomalies or deviations that might suggest an intrusion. While capable of detecting previously unseen attacks, it may generate false positives due to the dynamic nature of network behaviour.
- Policy-Based Detection: This technique flags violations of a defined security policy, ensuring all users adhere to established rules and standards.
Host-Based Intrusion Detection System (HIDS)
HIDS operates on individual hosts or devices on the network. It's capable of detecting anomalous behaviour or policy violations within the host system. HIDS monitors inbound and outbound packets from the device only and will alert the administrator if suspicious activity is detected.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Application Protocol-Based Intrusion Detection System (APIDS)
APIDS focuses on the specifics of application protocols to detect suspicious transactions. This approach allows APIDS to identify threats that conventional NIDS or HIDS may overlook. APIDS inspects and processes all traffic related to a particular application protocol, enabling it to detect protocol misuse or anomalies in the context of application use.
Future of Intrusion Detection Systems
As cyber threats continue to evolve, so too must our defences. The future of IDS lies in leveraging advancements in artificial intelligence and machine learning. By implementing these technologies, IDS can learn from each intrusion attempt, improving its ability to anticipate and respond to threats. The future will also see greater integration of IDS with other security tools, creating a more unified and comprehensive defence system.
Conclusion
Intrusion Detection Systems (IDS) are pivotal in today's digital landscape fraught with escalating and evolving cyber threats. By understanding the various aspects of IDS, including its types, components, and the role it plays in reinforcing cybersecurity, organizations can equip themselves to mitigate potential intrusions, safeguard their valuable digital assets, and ensure business continuity.
DDoS Attack
Introduction
In the vast, ever-evolving landscape of cybersecurity, Distributed Denial-of-Service (DDoS) attacks represent a significant and persistent threat. Through a DDoS attack, cybercriminals overwhelm servers, networks, or online services with an onslaught of internet traffic, causing disruption, downtime, and potential financial losses. This article provides an in-depth look at DDoS attacks, from understanding their cause and working to exploring prevention strategies.
Key Takeaways
- 👉A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt a network, service, or server by overwhelming it with a flood of internet traffic from multiple sources.
- 👉DDoS attacks represent a significant threat to cybersecurity, causing service disruption, downtime, and potential financial losses.
- 👉DDoS attacks involve the creation of a botnet, a group of compromised computers that send a flood of traffic to the target at the attacker's command.
- 👉Although challenging to prevent due to their distributed nature, several strategies can mitigate the risks posed by DDoS attacks, such as increasing network resilience, deploying anti-DDoS solutions, leveraging cloud-based protection, and creating a thorough incident response plan.
- 👉DDoS attacks often target websites, causing substantial downtime, loss of revenue and trust, and can also serve as a smokescreen for other malicious activities.
What is Distributed Denial-of-Service (DDoS) Attack?
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or server by overwhelming it with a flood of internet traffic. These attacks are "distributed" because they originate from multiple sources, often thousands of devices in a botnet, making them challenging to block.
Understanding DDoS Attacks
DDoS attacks are a prime concern in cybersecurity due to their potential to cause significant disruption. They target a wide variety of important resources, from network bandwidth to application services, intending to overload systems and prevent legitimate users' access. Despite their seemingly complex nature, understanding their basic workings and tactics can be quite straightforward.
How DDoS Attacks Work
DDoS attacks typically involve three parties: the target, the attacker, and multiple compromised computers, often referred to as a "botnet." Here's a simplified breakdown of how a DDoS attack takes place:
- Compromise: The attacker infects multiple systems with malware, effectively creating a botnet of "zombie" computers.
- Command and Control: The attacker sends instructions to the compromised systems.
- Attack: At the attacker's command, the botnet directs a deluge of requests to the target network or server, overwhelming it.
DDoS vs. DoS: Understanding the Difference
While similar in intent, a Denial-of-Service (DoS) attack differs from a DDoS attack in scale and strategy. A DoS attack originates from a single source, making it easier to block by merely identifying and limiting the source IP address. Conversely, DDoS attacks use many sources, often globally distributed, making them far more challenging to defend against due to their dispersed nature.
An Example of a DDoS Attack
An infamous example of a DDoS attack occurred in 2016 against Dyn, a major DNS provider. The Mirai botnet, composed of a vast array of IoT devices, bombarded Dyn's servers with unprecedented traffic volume. This attack led to widespread outages and sluggish performance across numerous high-profile websites, including Twitter, Reddit, and Netflix.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Mitigating DDoS Attacks: Prevention and Protection
Preventing DDoS attacks can be challenging due to their distributed nature. However, organizations can take several steps to mitigate the risks:
- Increase Network Resiliency: Implement redundancy into your network to ensure it can handle increased traffic.
- Deploy Anti-DDoS Software and Hardware: Utilize specialized solutions that can identify and mitigate DDoS attacks before they overwhelm your systems.
- Leverage Cloud-Based DDoS Protection: Cloud-based solutions offer scalability to handle sudden traffic influx and distribute traffic across multiple servers.
- Create an Incident Response Plan: Prepare a comprehensive plan that outlines the steps to take during a DDoS attack. This should include identifying the attack, escalating the issue to the appropriate personnel, and notifying stakeholders.
The Impact of DDoS Attacks on Cybersecurity
DDoS attacks pose a significant threat to the landscape of cybersecurity. They can cripple websites, causing substantial downtime and financial loss. In many instances, DDoS attacks are also used as a distraction for other malicious activities, such as data breaches or malware infection.
DDoS Attacks and Website Vulnerability
Websites are often the primary target of DDoS attacks. When a site is overwhelmed with traffic during an attack, legitimate users are unable to access the site's content, resulting in loss of revenue and trust. In extreme cases, a successful DDoS attack can lead to extended periods of downtime, causing irreversible damage to a company's reputation.
Conclusion
In the fight against Distributed Denial-of-Service (DDoS) attacks, knowledge is the first line of defense. Understanding the mechanisms behind these attacks, recognizing the signs, and implementing proactive protective measures can significantly reduce the risk they pose. As the cybersecurity landscape continues to evolve, staying one step ahead of threats like DDoS attacks is crucial in maintaining a secure digital environment.
Virtual Currencies
Introduction
The dawn of the digital age brought with it a plethora of innovations, changing the way we live, work, and transact. Among these innovations, virtual currencies have emerged as a revolutionary force, challenging traditional financial paradigms and paving the way for a new era of digital transactions.
This article provides an in-depth examination of virtual currencies, discussing their nature, examples, and their role in the broader financial ecosystem.
Key Takeaways
- Virtual currencies are digital assets that serve as a medium of exchange and exist only in the virtual realm. Examples include Bitcoin, Ethereum, and Ripple.
- Cryptocurrencies, a subset of virtual currencies, utilize blockchain technology for transparency, security, and decentralization.
- Virtual currencies present advantages like decentralization, low transaction costs, and accessibility. However, they also face challenges such as volatility, security risks, and regulatory concerns.
- Transactions with virtual currencies can have tax implications. It's important to report these transactions in tax returns, considering the capital gains or losses.
- Blockchain technology plays a vital role in many virtual currencies, providing a secure, transparent way of recording transactions.
- The cost basis of inherited virtual currency typically refers to its fair market value at the time of the benefactor's death, but specific regulations can vary, making professional advice essential.
What is a Virtual Currency?
Virtual currency is a type of digital asset designed to work as a medium of exchange. These currencies utilize cryptography for securing transactions, controlling the creation of additional units, and verifying asset transfers. Virtual currencies exist primarily in the digital realm, with no physical counterparts like coins or notes.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Examples of Virtual Currencies
Virtual currencies are abundant and diverse, each with its unique properties, use-cases, and underlying technologies.
Bitcoin
The first and most widely recognized virtual currency is Bitcoin, conceptualized by an unknown person or group of people using the name Satoshi Nakamoto. Bitcoin's creation ushered in the era of decentralized virtual currencies, inspiring a multitude of other projects.
Ethereum
Ethereum, another example, expands the concept of virtual currencies to create a full-fledged, blockchain-based platform. Ether, Ethereum's native currency, powers the network and enables a world of decentralized applications.
Ripple
Ripple, or XRP, is a virtual currency designed for efficient international money transfers, aimed at facilitating real-time, low-cost payments between financial institutions worldwide.
Comparing Virtual Currencies and Cryptocurrencies
Cryptocurrencies are a subset of virtual currencies. While all cryptocurrencies are virtual currencies, not all virtual currencies are cryptocurrencies. Cryptocurrencies utilize blockchain technology, characterized by decentralization, transparency, and immutability. Some virtual currencies, such as those used in online gaming, may not leverage blockchain technology and may not be decentralized.
Advantages and Disadvantages of Virtual Currencies
Like any innovation, virtual currencies come with both advantages and challenges.
Advantages
- Decentralization: Many virtual currencies operate on decentralized networks, free from government control or intermediaries.
- Low Transaction Costs: Virtual currencies can offer lower transaction fees, especially for international transfers.
- Accessibility: As internet-based systems, virtual currencies can bring financial services to unbanked populations.
Disadvantages
- Volatility: The value of virtual currencies can be highly volatile, leading to potential financial losses.
- Security Risks: While the currencies themselves are secure, the platforms and wallets storing them can be vulnerable to hacking.
- Regulatory Concerns: Regulatory uncertainty can pose challenges for businesses and individuals dealing with virtual currencies.
Virtual Currencies and Tax Reporting
Virtual currency transactions can have tax implications. In many jurisdictions, individuals must report their virtual currency transactions on their tax returns, including capital gains or losses. It's crucial to understand the specific regulations in your country and consult a tax professional if necessary.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Virtual Currencies and Blockchain Technology
Blockchain technology plays a critical role in many virtual currencies, especially cryptocurrencies. This technology offers a secure, transparent way of recording transactions, providing the foundation for the trustless, decentralized networks that many virtual currencies operate on. The blockchain records every transaction of a virtual currency, adding a layer of transparency and security to the digital financial world.
Inheritance and Cost Basis of Virtual Currency
Inheriting virtual currency involves more than just acquiring a new digital asset. It can also carry significant tax implications. The cost basis of inherited virtual currency usually refers to its fair market value at the time of the benefactor's death. However, tax regulations can vary widely across different jurisdictions, making it essential to consult a tax professional for advice.
Conclusion
As we navigate through the era of digital transformation, virtual currencies continue to disrupt the traditional financial landscape. With their potential to revolutionize global payments, virtual currencies bring both significant opportunities and challenges. As users and stakeholders of this new financial world, it is critical to understand the dynamics of virtual currencies to harness their benefits and mitigate their risks.
Data Loss Prevention
Introduction
In the digital era, data is the lifeblood of organizations, and its protection is paramount. An inadvertent leak of sensitive information can lead to grave consequences such as reputational damage, financial losses, and legal ramifications. This is where Data Loss Prevention (DLP) comes into play. It is an essential component of an organization's data protection strategy that guards against data leakage and ensures data confidentiality and integrity.
Key Takeaways
- Data Loss Prevention (DLP) is a set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. It plays a crucial role in preventing data breaches and meeting compliance requirements.
- DLP works by identifying sensitive data, monitoring and controlling data endpoints, network traffic, and data stored in the cloud, and triggering responses when suspicious activities are detected.
- The three main types of DLP are network-based, storage-based, and endpoint-based, each with its unique advantages and best use scenarios.
- Choosing the right DLP solution depends on factors such as the size of the organization, the nature of the data handled, and the regulatory landscape. Key aspects to consider include ease of deployment, scalability, policy management, and incident management.
- Implementing a robust DLP strategy involves classifying data, defining policies, ensuring regular updates, providing user training and awareness, and regular auditing and reporting.
- A strong DLP strategy not only protects your organization from financial and reputational damage but also builds trust with customers and stakeholders.
Understanding Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. DLP can also be defined as a strategy for making sure that end users do not send sensitive or critical information outside of the corporate network.
DLP Overview: Why is it Crucial?
DLP is vital because data breaches can be costly and destructive. With regulatory standards such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), organizations are mandated to protect sensitive data, failure of which can lead to hefty fines. DLP helps organizations adhere to these compliance requirements, avoid the adverse impact of data breaches, and foster trust among customers and partners.
Mechanism of Data Loss Prevention
Data Loss Prevention solutions work by identifying sensitive data, tracking that data as it moves through and out of the organization, and preventing unauthorized disclosure of data by creating and enforcing disclosure policies.
Step 1: Data Identification
The first step in a DLP implementation is to define and categorize data that needs protection. This could include personally identifiable information (PII), financial data, intellectual property, and other business-sensitive information.
Step 2: Data Tracking
After identifying what data to protect, the next step is tracking the data. The DLP solution monitors and controls data endpoints (workstations and servers), network traffic, and data stored in the cloud or on-premise.
Step 3: Policy Creation and Enforcement
Based on the organization's needs and regulatory requirements, policies are created to define how sensitive data should be handled. The DLP system then enforces these policies, triggering alerts or blocking activities that violate these policies.
Types of Data Loss Prevention
DLP solutions are broadly classified into three types: Network DLP, Endpoint DLP, and Datacenter or Storage DLP.
- Network DLP: This type of DLP monitors data in motion, i.e., data being transmitted over the network. It can identify sensitive data and prevent unauthorized transfers.
- Endpoint DLP: This type focuses on data at rest in user devices such as laptops, smartphones, or tablets. It prevents data leakage through device controls and encryption.
- Datacenter or Storage DLP: It protects data at rest within the organization's servers or cloud storage. It provides data discovery capabilities and helps ensure data storage in compliance with policies.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Data Loss Prevention Best Practices
Understand your Data
An effective DLP strategy starts with understanding what constitutes sensitive data for your organization. It's essential to classify data based on its sensitivity level and determine its rightful users.
Regularly Update DLP Policies
The threat landscape is always evolving. Therefore, your DLP policies need to be regularly updated to counteract emerging threats and adapt to changes in regulatory requirements. An outdated policy is an open door for data leakage.
Training and Awareness
Human error often contributes to data loss. As such, continuous user training and awareness are critical. Make sure all your employees understand the importance of data security and know the best practices to avoid unintentional data leakage.
Regular Auditing and Reporting
Implement regular audits of your DLP system to ensure its effectiveness. Moreover, robust reporting can provide insights into patterns of data usage and movement, which can aid in enhancing your DLP strategy.
Choosing the Right DLP Solution
Choosing the right DLP solution depends on various factors, such as the size of the organization, the nature of the data handled, and the regulatory landscape in which the organization operates. Here are some key considerations:
- Ease of Deployment: The DLP solution should be easy to deploy and integrate with existing systems.
- Scalability: As your organization grows, the DLP solution should be able to scale to handle increased data and network load.
- Policy Management: The solution should allow easy creation and management of DLP policies, with the ability to customize as per specific business requirements.
- Incident Management: Look for a solution that provides detailed incident reports and supports prompt and effective incident response.
Conclusion
Data Loss Prevention is a critical element in any organization's cybersecurity framework. With increasing regulatory scrutiny and rising incidents of data breaches, the importance of a robust DLP strategy cannot be overstated. Understanding the nuances of DLP and implementing it effectively can go a long way in safeguarding your organization's most valuable asset—data. By doing so, not only can you avoid financial and reputational damage, but you can also gain the trust of your customers and stakeholders, crucial for the longevity and success of your business.
Virtual Private Network
Introduction
A Virtual Private Network, popularly known as VPN, is the cyber equivalent of an invisibility cloak in the digital realm. Amid increasing concerns over data privacy and security, VPNs have emerged as a vital defence mechanism, shielding users' data from prying eyes.
This article elucidates the concept of VPN, how it operates, its diverse types, and its practical applications, providing a comprehensive guide to navigating the cyber world safely and privately.
Key Takeaways
- A Virtual Private Network (VPN) creates a secure connection to another network over the internet. It can shield browsing activity from prying eyes on public Wi-Fi and enable access to region-restricted websites.
- VPNs protect data by encapsulating and encrypting it before it's transmitted over the internet. It hides your IP address, making it appear as if your traffic is coming from the VPN server rather than your device.
- There are two main types of VPNs: Remote Access VPNs, which are used to connect individual users to a central business network, and Site-to-Site VPNs, which connect entire networks to each other.
- From maintaining privacy to accessing geo-blocked content and facilitating secure remote work, VPNs have a wide range of applications.
- Selecting the right VPN involves consideration of several factors, including privacy and security, speed, server locations, cost, and user-friendliness.
What is a Virtual Private Network (VPN)?
A VPN is a technology that creates a secure, encrypted connection over a less secure network, such as the public internet. A VPN uses virtual connections routed through the internet from a company's private network or a third-party VPN service to a remote site or person. It secures a private network, allowing users to send and receive data across shared or public networks as though their computing devices were directly connected to the private network.
Explanation or Overview: The VPN in Detail
VPNs shield your online activities from unwanted attention by encrypting your data and masking your online identity. This encryption process turns readable data into encoded information that can only be deciphered using a key. It's akin to sending secret messages where the content remains hidden unless you know the secret language. By establishing this secure virtual tunnel, VPNs provide an extra layer of privacy and anonymity, crucial in today's data-sensitive digital landscape.
How it Works: The Mechanism of a VPN
A VPN works by rerouting your device's internet connection through the VPN's private server rather than your internet service provider (ISP). This means that when your data is transmitted to the internet, it originates from the VPN rather than your computer. A VPN acts as an intermediary, hiding your IP address and protecting your online activities from being tracked or data being intercepted. Once your data reaches the VPN server, it exits onto the public internet. If the website you're visiting uses HTTPS, your data remains encrypted.
Types: Classifying VPNs
There are various types of VPNs, each designed for specific needs. Two primary categories are remote-access VPNs, often used by individual users to access a remote network or its services, and site-to-site VPNs, typically employed by businesses to connect the networks of multiple office locations.
Remote access VPNs can further be divided into two types:
- Personal VPN: A user connects to a private network remotely, often used for secure, anonymous browsing, and accessing geographically restricted content.
- Corporate VPN: A worker connects to a corporate network remotely, often used to securely access work resources when outside the office.
Site-to-site VPNs can also be classified into two:
- Intranet-based VPN: When a company has multiple remote locations that they wish to join in a single private network, they create an intranet VPN.
- Extranet-based VPN: When companies want to connect with their partners or customers, they create an extranet VPN where the resources are accessed in a controlled manner.
Use Cases: Applications of VPNs
VPNs have numerous practical applications. Personal VPN services are widely used to encrypt user data, ensuring browsing activities remain confidential and protected from potential snoopers, hackers, or even ISPs. This is especially useful when accessing the internet from public Wi-Fi networks, where your unencrypted data can be easily intercepted.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
VPNs also enable users to access geographically restricted content. Some websites or services limit their accessibility to specific regions; VPNs can overcome these blocks by masking the user's actual location.
In the business world, corporate VPNs offer employees secure remote access to office resources, irrespective of their location. This is particularly beneficial in the era of remote work, where staff need to safely access sensitive company data from home or other off-site venues.
Choosing a VPN: Key Considerations
When considering a VPN, it's essential to weigh a few key factors:
- Privacy and Security: A VPN should offer strong encryption and a no-logs policy to ensure user activities aren't recorded or stored.
- Speed: While a VPN can affect your internet speed due to data encryption, top-quality VPNs offer fast speeds with minimal impact on your internet connection.
- Server Locations: More server locations mean more options for spoofing your location, which can be critical for bypassing geoblocks.
- Cost: While free VPNs may be tempting, they often come with limitations and potential security risks. A paid VPN service often offers better security, greater server selection, and superior speed.
- Ease of Use: A user-friendly interface is essential, especially for those less technologically inclined.
VPN: A Crucial Tool in the Digital Age
In the age where data breaches and privacy invasions are commonplace, VPNs offer a robust shield, protecting your online activities from potential threats. By masking your online identity and encrypting your data, VPNs allow you to navigate the digital world with confidence, be it accessing your favourite streaming services or connecting to your office network remotely. With varied offerings and capabilities, choosing the right VPN requires an understanding of your individual or organizational needs, a factor this article aims to simplify. As we continue to embrace virtual space, the importance of VPNs in maintaining our cyber-privacy cannot be overstressed. In essence, the VPN is not just a tool, but a requisite guard in our increasingly connected world.
Conclusion
VPNs play an increasingly crucial role in today's digital landscape, offering a host of benefits, including enhanced security, improved privacy, and greater internet freedom. As data privacy becomes a pressing concern in our connected world, VPNs serve as a reliable tool to navigate the digital sphere securely. Whether you're an individual looking to protect personal data or a business seeking to secure remote work, understanding VPNs is fundamental to ensuring safe and private online experiences.
Electronic Funds Transfer
Electronic Funds Transfer (EFT) has revolutionized how we conduct financial transactions. It's an essential part of our daily lives, enabling swift and secure money transfers. This article offers a comprehensive insight into EFTs, their functioning, different types, and examples.
Key Takeaways
- Electronic Funds Transfer (EFT) is a method that facilitates the electronic transfer of money from one bank account to another.
- EFT is reliable, fast, secure, and provides a more efficient means of conducting financial transactions compared to traditional paper-based methods.
- Different types of EFT transactions include Automated Teller Machine (ATM) transactions, Direct Deposit or Withdrawal of Funds, Point of Sale (POS) Transactions, Electronic Checks (e-Checks), and Mobile Banking.
- Key factors to consider when choosing an EFT solution include security, speed, ease of use, cost, and customer support.
- Processing times for EFT transactions vary, typically completed within one to two business days. However, some factors can prolong the process.
What is an Electronic Funds Transfer (EFT)?
EFT is a system that allows money to be moved between accounts without physical cash changing hands or paperwork being exchanged. Essentially, EFT is an umbrella term that includes various types of electronic payments such as wire transfers, direct deposit, digital checks, and debit card transactions.
Explanation and Overview: EFT in the World of Banking
EFT has significantly influenced the banking sector, facilitating fast and secure fund transfers across different platforms. An EFT transfer might be performed within a single financial institution or between multiple banks. These transactions are commonly conducted through computer-based systems and without the need for physical checks or cash, making them an efficient solution for businesses and individuals alike.
How EFT Works: The Mechanism Behind Electronic Transfers
EFTs operate using computer and digital technology. When an EFT is initiated, the banking system uses Automated Clearing House (ACH) networks to route funds from one bank account to another. The transaction details, including the account numbers and the amount to be transferred, are encrypted for secure transmission. Upon receipt of the transaction details, the recipient's bank verifies the data and deposits the funds into the designated account.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
Types of EFT Transactions
Several transaction types fall under the EFT umbrella:
- Wire Transfers: These are direct account-to-account transfers, usually facilitated by a network like SWIFT.
- Direct Deposit: This involves the electronic transfer of payment from a company's account into an employee's account, typically for payroll purposes.
- Automated Teller Machines (ATMs): ATMs facilitate various EFT transactions, including cash withdrawals, deposits, and account transfers.
- Electronic Checks: These are digital versions of traditional paper checks, which are processed through an automated system.
- Debit Card Transactions: When a debit card is used for payment, the funds are electronically transferred from the cardholder's bank account to the merchant's account.
Use Cases of EFT
EFT finds broad applications in everyday life. Here are a few examples:
- Online Shopping: EFT makes online shopping seamless by enabling instant electronic payment for purchases.
- Bill Payments: Utility bills, loan installments, and credit card bills can be paid using EFT, often through automatic deductions.
- Salary Transfers: Businesses can disburse salaries to employees through direct deposit, a form of EFT.
- Government Payments: Governments use EFT to distribute benefits, pensions, and tax refunds.
Advantages and Disadvantages of Electronic Funds Transfer
EFT offers numerous benefits that have contributed to its widespread adoption. These include:
- Speed: EFT transactions are processed significantly faster than traditional methods, ensuring almost instant transfer of funds.
- Convenience: EFT can be performed anytime, anywhere, eliminating the need to visit a bank or use physical cash.
- Efficiency: Automated processes reduce the time and effort required to manage financial transactions.
- Security: The use of encryption and secure networks protects sensitive financial information during EFT transactions.
However, like any other system, EFT has its drawbacks:
- Risk of Fraud: Despite security measures, cybercriminals may attempt to intercept sensitive data during transmission.
- Technical Issues: Server crashes or network issues can delay transactions or lead to processing errors.
- Lack of Anonymity: EFT transactions are traceable, unlike cash transactions, potentially leading to privacy concerns.
Conclusion
EFT has revolutionized the financial world, offering a more efficient and secure alternative to traditional cash or check transactions. As the world moves towards a more digital future, understanding the nuances of EFT, from its functioning to its diverse use cases, can be instrumental in navigating the modern economic landscape. Whether you're a business owner, a digital consumer, or a banking enthusiast, a thorough understanding of EFTs is undoubtedly a valuable asset.
Benefit Fraud
In a world where countless individuals depend on social assistance programs to meet basic needs; benefit fraud poses a significant threat to the integrity of these systems. These programs are designed to support vulnerable populations, offering financial aid, healthcare, housing, and other essentials. However, the unfortunate reality is that some exploit these systems, diverting resources away from those who genuinely require assistance.
Understanding the different aspects of benefit fraud is crucial for policymakers, investigators, and the public. In this article, we'll delve into what is benefit fraud, the types of benefits most susceptible to fraud, common techniques used by fraudsters, the severe consequences of engaging in benefit fraud, real-world examples, and effective methods for detection and prevention.
What Is Benefit Fraud?
Benefit fraud refers to the act of individuals providing false information or engaging in deceptive practices to wrongfully obtain government assistance, such as unemployment benefits, disability benefits, housing assistance, food stamps, or healthcare benefits. It involves exploiting vulnerabilities in the system to receive financial aid or services that one is not entitled to under the established eligibility criteria.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Types of Benefits Prone to Fraud
1. Unemployment Benefits
Unemployment benefits are designed to provide financial support to individuals who find themselves without a job. Fraud in this category often involves individuals misrepresenting their employment status, either by concealing new employment or providing false information about their job search efforts. Fraudsters may exploit loopholes or weaknesses in the verification process, leading to the disbursement of benefits to those who are not genuinely unemployed.
2. Disability Benefits
Disability benefits aim to assist individuals who are unable to work due to physical or mental health challenges. Fraud in this category can take various forms, such as exaggerating or falsifying medical conditions to meet eligibility criteria. Some individuals may engage in activities inconsistent with their claimed disability, leading to undeserved benefits. The subjective nature of certain disabilities can make verification challenging, creating opportunities for exploitation.
3. Housing Assistance
Housing assistance programs provide financial support to individuals or families struggling to afford stable housing. Fraud in this context may involve providing inaccurate information about income, household composition, or housing expenses to qualify for more substantial assistance. Individuals might also fail to report changes in their financial situation or living arrangements, resulting in benefits being misallocated.
4. Food Stamps
Food stamp programs, also known as Supplemental Nutrition Assistance Programs (SNAP), aim to alleviate hunger by providing eligible individuals with funds to purchase food. Benefit fraud in this category often involves misrepresenting income, household size, or assets to qualify for a higher benefit amount. Additionally, individuals might engage in the unauthorized sale or exchange of food stamp benefits for cash.
5. Healthcare Benefits
Healthcare benefits, such as Medicaid or Medicare, provide essential medical coverage to eligible individuals. Fraud in this area can include providing false information about income or medical conditions to qualify for benefits. Additionally, healthcare providers may engage in fraudulent billing practices, overcharging for services or billing for services that were not provided.
Common Techniques Used in Benefit Fraud
Benefit fraud can take many forms, and fraudsters employ various techniques to deceive the system. Common methods include providing false information on applications, underreporting income, claiming benefits for non-existent dependents, and engaging in identity theft. Additionally, some individuals may continue to receive benefits even after their eligibility has ceased.
1. Providing False Information on Applications
One prevalent technique involves applicants providing inaccurate or entirely false information when applying for benefits. This could include misrepresenting personal details, employment status, or financial circumstances. Fraudsters strategically manipulate the application process to gain eligibility for benefits they wouldn't otherwise qualify for.
2. Underreporting Income
Underreporting income is a common method employed by individuals seeking to maximize their benefits. By intentionally providing inaccurate details about their earnings, applicants can qualify for a higher amount of financial assistance. This tactic exploits the difficulty in verifying income information promptly and accurately.
3. Claiming Benefits for Non-Existent Dependents
Another tactic involves claiming benefits for dependents who do not exist or are not eligible for assistance. This could include listing non-existent children or other dependents to inflate the benefits received. Verifying the existence and eligibility of dependents can be challenging, creating an opportunity for fraudsters to exploit this gap in the system.
4. Engaging in Identity Theft
Identity theft is a more sophisticated method where fraudsters assume the identity of someone else to access benefits. This can involve stealing personal information, such as social security numbers, and using it to submit fraudulent applications. Detecting identity theft requires advanced verification processes and collaboration between agencies to cross-reference information.
5. Continuing to Receive Benefits After Eligibility Ceases
Some individuals, even after becoming ineligible for benefits due to changes in their circumstances, continue to receive assistance by not reporting these changes. This could include getting a new job, an increase in income, or improvements in their overall financial situation. The failure to promptly update the information allows fraudsters to exploit the system beyond their legitimate eligibility period.
Consequences of Benefit Fraud
Engaging in benefit fraud is not only a breach of ethical standards but also carries severe consequences that extend beyond legal ramifications. The repercussions of fraudulent activities within social welfare systems can have a profound and lasting impact on the lives of those involved.
1. Legal Repercussions
Individuals caught committing benefit fraud can face serious legal consequences. Legal actions may include hefty fines, imprisonment, or a combination of both. The severity of the punishment often depends on the extent and nature of the fraudulent activities. Courts take benefit fraud seriously due to the potential harm it causes to the integrity of social welfare programs and the misallocation of public funds.
2. Financial Penalties
One of the immediate consequences of benefit fraud is the imposition of financial penalties. Offenders may be required to pay back the wrongfully obtained benefits, along with additional fines as a form of restitution. This financial burden can be substantial, exacerbating the economic difficulties that may have led individuals to commit fraud in the first place.
3. Imprisonment
In cases of significant or repeated benefit fraud, imprisonment is a common consequence. Serving time in prison not only separates individuals from their families and communities but also serves as a deterrent to others considering similar fraudulent activities. The duration of imprisonment is determined by the severity of the fraud and the amount of money involved.
4. Tarnished Record
A conviction for benefit fraud leaves individuals with a criminal record, which can have lasting repercussions. This tarnished record can make it challenging to secure future employment or housing. Many employers conduct background checks, and a history of fraud can significantly reduce opportunities in the job market.
5. Difficulty in Securing Employment and Housing
Individuals convicted of benefit fraud often face social stigma, making it difficult to reintegrate into society. The tarnished reputation may result in rejection by potential employers and landlords. This difficulty in securing stable employment and housing further compounds the challenges faced by those attempting to rebuild their lives after a conviction.
Examples of Benefit Fraud
1. Disability Benefits Scam (United States, 2013):
- A group of individuals, including former police officers and firefighters, orchestrated a scheme to falsely claim disabilities and receive substantial disability benefits. These individuals exploited their knowledge of the system, with some possibly using their previous professions to lend credibility to their claims.
- The fraud involved convincing medical professionals to provide misleading information about the individuals' health conditions, making it appear as though they were legitimately unable to work. This manipulation allowed the perpetrators to receive millions of dollars in disability benefits that they did not deserve.
- The case not only highlighted vulnerabilities in the disability benefits assessment process but also raised concerns about the ethical implications of individuals who had served in public safety roles engaging in fraudulent activities.
2. Housing Benefit Fraud (United Kingdom, 2014):
- In the UK, a couple was convicted of housing benefit fraud for providing false information about their living arrangements. The couple continued to claim housing benefits for a property they had vacated, deceiving authorities and resulting in significant overpayments.
- This type of fraud often involves individuals providing inaccurate details about their living situation to maximize financial assistance. In the case of the UK couple, the false information led to the wrongful disbursement of thousands of pounds in benefits, ultimately impacting the integrity of the housing assistance program.
3. Food Stamp Trafficking Ring (United States, 2016):
- Law enforcement uncovered a large-scale food stamp trafficking ring in Florida, where individuals engaged in the illegal exchange of food stamp benefits for cash. The participants in the scheme exploited the intended purpose of the food stamp program, which is designed to help individuals and families access nutritious food.
- The trafficking ring likely involved multiple participants working in concert to profit from the exchange of food stamp benefits. The criminal charges filed against those involved underscored the seriousness with which authorities approach fraud that undermines the efficacy of social assistance programs.
Detecting and Preventing Benefit Fraud
Detecting and preventing benefit fraud is a complex task that demands a comprehensive and adaptive strategy. Authorities employ a combination of advanced technologies, collaboration between government agencies, and public engagement to safeguard social welfare systems from fraudulent activities.
1. Advanced Data Analytics
Utilizing advanced data analytics is a key component of modern fraud detection. By employing sophisticated algorithms, authorities can analyze vast datasets to identify irregularities and patterns indicative of potential fraud. This includes scrutinizing claimant information, transaction histories, and other relevant data points to flag suspicious activities.
2. Cross-Referencing Information
Cross-referencing information from different sources is crucial in ensuring the accuracy of beneficiary details. Government agencies can collaborate to verify information provided on benefit applications with data from tax records, employment databases, and other official records. Discrepancies or inconsistencies can then be thoroughly investigated to identify potential fraud.
{{cta('bdd96089-cde2-43f3-95a3-3f6d7b74af38','justifycenter')}}
3. Increased Collaboration Between Government Agencies
Collaboration between different government agencies enhances the effectiveness of fraud detection efforts. Sharing information and insights across departments allows for a more comprehensive understanding of individuals' circumstances. This collaboration helps identify patterns of behavior that may indicate fraudulent activity, particularly in cases where individuals attempt to exploit multiple benefit programs simultaneously.
4. Improved Technology
Embracing and investing in cutting-edge technology is essential for staying ahead of fraudsters. Machine learning algorithms, artificial intelligence, and predictive analytics can continuously evolve to adapt to new fraud schemes. Automation can also streamline the processing of claims and improve the overall efficiency of social welfare systems.
5. Public Awareness Campaigns
Educating citizens about the consequences of fraud is a proactive approach to preventing fraudulent activities. Public awareness campaigns can inform individuals about the legal repercussions of benefit fraud, emphasizing the importance of honesty in the application process. Encouraging the public to report suspicious activities creates an additional layer of vigilance and aids authorities in identifying potential cases.
6. Whistleblower Programs
Establishing whistleblower programs can incentivize individuals with inside knowledge to come forward and report fraudulent activities. Offering protections and incentives for those who provide valuable information can significantly enhance the effectiveness of fraud prevention efforts.
Conclusion
Benefit fraud poses a significant threat to the integrity of welfare systems globally. Recognizing the types of benefits prone to fraud, understanding common techniques used by fraudsters, and being aware of the consequences are essential steps in combating this issue. By employing effective detection and prevention methods, authorities can safeguard the integrity of social assistance programs, ensuring that benefits reach those who genuinely need them.
Payroll Fraud
Payroll fraud is a serious issue that can cost companies millions of dollars every year. It occurs when employees manipulate the payroll system to receive unauthorized payments, benefits, or incentives. In order to protect their businesses, employers need to understand the different types of payroll fraud and implement effective prevention and detection measures. In this article, we will delve into the various aspects of payroll fraud and explore strategies to safeguard companies from falling victim to this deceptive practice.
Understanding Payroll Fraud
Payroll fraud can take many forms, ranging from simple schemes to more complex tactics. The perpetrators often exploit weaknesses in the payroll system or manipulate employee data to deceive employers. Understanding the techniques used in payroll fraud is crucial for employers to detect and prevent such fraudulent activities from occurring.
One common form of payroll fraud is ghost employees, where fictitious employees are added to the payroll system, and payments are made to these non-existent individuals. This type of fraud can go undetected for a long time if proper controls are not in place. Another prevalent scheme is time theft, where employees manipulate their timesheets to overstate the hours worked, resulting in higher pay than they are entitled to. Employers should implement robust time tracking systems and regularly review employee hours to combat this type of fraud effectively.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Additionally, some fraudsters engage in commission schemes, where they manipulate sales data to inflate their commissions. This form of payroll fraud can be challenging to detect, as it often involves collusion between employees and sometimes even external parties. Employers should conduct regular audits of sales data and commission calculations to identify any discrepancies that may indicate fraudulent activity. By staying vigilant and implementing strong internal controls, organizations can protect themselves from falling victim to payroll fraud.
How is Payroll Fraud carried out?
Payroll fraud can be carried out in several ways, including but not limited to:
- Advance Retention Fraud: This occurs when an employee is paid in advance for work they have not yet performed and then disappears.
- Buddy Punching Fraud (Timesheet fraud): Employees fraudulently record punches on behalf of absent colleagues to inflate their working hours.
- Ghost Employee Fraud: A fictitious employee is added to the payroll system, and the fraudster collects their wages.
- Paycheck Diversion Fraud: The fraudster diverts an employee's paycheck to their own account.
- Pay Rate Alteration Fraud: Employees manipulate their pay rates to receive higher wages without authorization.
- Commission schemes: Employees manipulate sales figures to earn higher commissions.
- Workers’ compensation fraud: Employees file false claims for workplace injuries to receive compensation they are not entitled to.
- Workers misclassification: Employers misclassify employees as independent contractors to avoid paying payroll taxes and other benefits.
One of the most common forms of payroll fraud is known as "Time Theft." This occurs when employees report hours they have not actually worked, leading to overpayment. It can be challenging for employers to detect time theft, especially in companies with manual timekeeping systems.
Another insidious form of payroll fraud is "Overtime Abuse." In this scheme, employees falsely claim overtime hours they have not worked, resulting in inflated paychecks. Overtime abuse not only affects a company's finances but also creates unfair advantages for dishonest employees over their hardworking colleagues.
The Link between Payroll Scam and Money Laundering
Payroll fraud can serve as a front for money laundering schemes. Criminals may use legitimate companies to disguise the illegal origins of funds by creating ghost employees or manipulating payroll records. Therefore, preventing payroll fraud is not only vital for financial reasons but also essential in combating money laundering and other illicit activities.
Money laundering is a complex process that involves disguising the origins of illegally obtained money to make it appear as if it comes from a legitimate source. By incorporating payroll fraud into their schemes, criminals can funnel dirty money through seemingly legitimate channels, making it difficult for law enforcement agencies to trace the illicit funds back to their criminal origins. This intricate web of deception highlights the importance of robust anti-fraud measures and thorough due diligence in financial transactions.
Moreover, the connection between payroll scams and money laundering underscores the need for companies to implement stringent internal controls and regular audits to detect any irregularities in their payroll systems. By conducting thorough background checks on employees and cross-referencing payroll records with employee attendance logs, organizations can significantly reduce the risk of falling victim to fraudulent activities that could potentially lead to money laundering charges. Staying vigilant and proactive in safeguarding against payroll fraud not only protects a company's financial health but also contributes to the broader efforts in combating financial crimes on a global scale.
Scams Through Third Party Payroll Managers
In some instances, third-party payroll managers can be involved in fraudulent activities. It is essential for companies to carefully vet and regularly monitor any outside payroll service providers to ensure they operate with integrity and maintain strict internal controls.
One common scam involving third-party payroll managers is the creation of ghost employees. This scheme typically involves the payroll manager adding fake employees to the company's payroll system and diverting their pay to dummy bank accounts controlled by the fraudster. By creating these ghost employees, the fraudster can siphon off funds from the company without raising suspicion, as these payments are often small and go unnoticed among legitimate payroll transactions.
Another deceptive tactic used by unscrupulous payroll managers is manipulating employee hours and wages. By falsifying timesheets or altering hourly rates, these individuals can embezzle funds from the company while making it appear like legitimate payroll expenses. This type of fraud can be challenging to detect, especially in larger organizations with numerous employees and complex payroll systems, highlighting the importance of thorough oversight and regular audits.
Prevention and Detection to Safeguard Employer Companies
To safeguard their businesses from payroll fraud, employers should implement the following prevention and detection measures:
Secure Database
Employers must maintain a secure and confidential payroll database accessible only to authorized personnel. Limiting access to sensitive employee information can minimize the risk of identity theft and data manipulation.
Geofencing based attendance
Geofencing is a location-based technology that allows employers to track employee movements within designated boundaries. By implementing geofencing for attendance tracking, employers can verify that employees are physically present during work hours, thereby reducing the likelihood of buddy punching fraud.
Implement Clear Policies
Clear and comprehensive policies relating to payroll management, employee classification, and reporting procedures should be established and communicated to all employees. These policies should include guidelines on timesheet submissions, reporting suspicious activities, and the consequences of engaging in payroll fraud.
Review Payroll Reports
Employers should review payroll reports regularly to identify any irregularities or discrepancies. Analyzing payroll data can reveal trends or patterns indicating potential fraudulent activities. Anomalies such as sudden spikes in overtime hours or unexpected changes in pay rates should be thoroughly investigated.
Fraud Awareness Training
Providing fraud awareness training to both employees and management is crucial in preventing payroll fraud. Educating employees about the different types of fraud, the importance of reporting suspicious activities, and the consequences of engaging in fraudulent behavior can serve as a strong deterrent.
However, it is important to note that preventing payroll fraud requires a multi-faceted approach that goes beyond these specific measures. Employers should also consider implementing additional strategies such as regular internal audits, conducting background checks on new employees, and implementing strong internal controls.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Regular internal audits can help identify any weaknesses or vulnerabilities in the payroll system, allowing employers to take corrective action before any fraudulent activities occur. Background checks on new employees can provide valuable information about their past employment history, helping employers make informed decisions and reduce the risk of hiring individuals with a history of fraudulent behavior.
In addition, implementing strong internal controls, such as segregation of duties and dual authorization for payroll transactions, can further enhance the security of the payroll process. By ensuring that no single individual has complete control over the entire payroll process, employers can minimize the risk of fraud and increase accountability.
By combining these additional strategies with the prevention and detection measures mentioned earlier, employers can create a robust and comprehensive approach to safeguarding their businesses from payroll fraud. It is important to stay vigilant and adapt to evolving threats, as fraudsters are constantly finding new ways to exploit vulnerabilities. With a proactive and diligent approach, employers can protect their financial resources and maintain the integrity of their payroll systems.
Watchlist Screening
In order to protect its financial health and build a trustworthy customer base, every company needs a solid Anti-Money Laundering (AML) compliance process, and one crucial component of this is watchlist screening.
This screening process is particularly beneficial in the financial sector because financial institutions frequently encounter individuals attempting scams or fraudulent activities.
Keep reading to get a clear understanding of everything you need to know about watchlist screening.
Key Takeaways
- Watchlist screening is a critical safety net for businesses, systematically checking if individuals or entities are on watchlists for potential risks like illegal activities or fraud.
- It plays a vital role in modern risk management by identifying individuals on watchlists, aiding financial institutions to mitigate risks and maintain compliance.
- Diverse Types of Screening includes AML, PEP, sanctions, fraudulent activity, terrorist financing, internal, and global watchlist screening, each serving a unique purpose in risk management.
- Employing sophisticated techniques like name matching algorithms, fuzzy and phonetic matching, and AI for improved accuracy in screening.
- The process faces challenges like managing false positives/negatives, ensuring data accuracy, scalability, regulatory complexity, and balancing speed with accuracy.
What Is Watchlist Screening?
Watchlist screening is a crucial safety net for businesses. It's a systematic process used by companies to check whether individuals or entities they're dealing with appear on a "watchlist." This watchlist is essentially a lineup of people marked for potential risks, often associated with illegal activities, fraud, or actions that could pose a threat to a business.
In essence, watchlist screening acts as a security checkpoint. It ensures that a company isn't unintentionally getting involved with individuals or organizations that might cause harm. It's a preventive measure, allowing businesses to vet their customers, partners, or transactions against a list of known risks.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Role of Watchlist Screening in Modern Risk Management
In modern risk management, the role of watchlist screening is pivotal for safeguarding businesses against a myriad of potential threats. One of its primary functions is to identify and flag individuals or entities on watchlists, which are compilations of those associated with illegal activities, fraud, or activities that pose a risk to the business. By cross-referencing against these watchlists, companies can detect and mitigate risks before they escalate.
Financial institutions often find themselves at the intersection of various transactions, making them susceptible to encounters with scammers and fraudsters. By integrating watchlist screening into their risk management practices, these institutions create a robust defense mechanism against financial crimes.
Moreover, watchlist screening plays a critical role in ensuring compliance with regulatory standards. Many industries are subject to strict regulations, and failure to comply can lead to severe consequences. Watchlist screening helps companies adhere to these regulations by providing a systematic way to screen individuals and entities involved in their operations.
Types of Watchlist Screening
1. AML Watchlist Screening:
AML watchlist screening focuses on identifying individuals or entities involved in money laundering activities. It helps financial institutions comply with regulations and prevents illicit funds from entering the financial system.
2. PEP (Politically Exposed Persons) Screening:
Watchlist and PEP screening is designed to pinpoint individuals holding prominent public positions. These individuals, due to their roles, may be more susceptible to corruption or financial improprieties. Screening for PEPs ensures heightened scrutiny and due diligence.
3. Sanctions Screening:
Sanctions screening involves checking against lists of individuals or entities subject to economic or trade sanctions. It helps businesses avoid engaging with parties that could lead to legal and financial repercussions.
4. Fraudulent Activity Screening:
This type of screening is broader, encompassing a range of fraudulent activities. It involves identifying individuals or entities linked to scams, financial fraud, or other deceptive practices that could harm a business.
5. Terrorist Financing Watchlist Screening:
This screening focuses on identifying entities associated with financing terrorism. It is crucial for maintaining global security and ensuring that businesses do not inadvertently support terrorism through financial transactions.
6. Internal Watchlist Screening:
Some businesses maintain their own internal watchlists based on past experiences or specific criteria. Internal watchlist screening helps companies track and manage risks unique to their operations.
7. Global Watchlist Screening:
This includes a comprehensive approach, checking against a wide range of global watchlists. It ensures a more exhaustive screening process, capturing potential risks from various jurisdictions.
Each type of watchlist screening serves as a specialized tool in risk management, allowing businesses to tailor their screening processes according to industry requirements, regulatory standards, and the specific threats they may face. By incorporating a combination of these screening types, companies can create a robust defense against a diverse range of risks.
Watchlist Screening Techniques
Effectively implementing watchlist screening requires more than a checklist approach; it involves employing advanced techniques to enhance accuracy and efficiency. Here are key watchlist screening techniques that businesses can adopt to strengthen their risk management strategies:
1. Name Matching Algorithms:
Utilizing sophisticated algorithms for name matching ensures a more nuanced approach to screening. These algorithms consider variations in spelling, order, and common aliases, minimizing the risk of false negatives or positives.
2. Fuzzy Matching and Phonetic Matching:
Fuzzy matching allows for the identification of names that are similar but not identical, accommodating for potential typos or misspellings. Phonetic matching considers the sound of names, adding another layer of precision to the screening process.
3. Data Normalization:
Standardizing and normalizing data formats across various databases and watchlists enhance the accuracy of screening. This technique streamlines the comparison process and reduces the likelihood of overlooking relevant information.
4. Watchlist Updating and Real-Time Monitoring:
Regularly updating watchlists and incorporating real-time monitoring ensure that businesses have the latest information at their disposal. This dynamic approach is crucial in identifying emerging risks promptly.
5. Behavioral Analysis:
Beyond static data comparisons, behavioral analysis involves assessing patterns and anomalies in transactions or activities. This technique adds a layer of depth, helping to detect subtle signs of fraudulent behavior or potential risks.
6. Machine Learning and Artificial Intelligence (AI):
Leveraging machine learning and AI enables systems to adapt and improve over time. These technologies can learn from historical data, continuously refining screening processes and enhancing accuracy in identifying potential risks.
7. Entity Resolution:
Entity resolution techniques focus on linking and deduplicating records, ensuring that the screening process accurately identifies distinct individuals or entities. This is particularly crucial in scenarios where multiple records may pertain to the same entity.
8. Risk Scoring:
Implementing a risk scoring system allows businesses to prioritize and focus on high-risk entities. By assigning scores based on various risk factors, companies can allocate resources efficiently and address the most pressing concerns first.
9. Cross-Referencing Multiple Data Sources:
Comprehensive screening involves cross-referencing information from various data sources. This multifaceted approach ensures a more thorough examination, reducing the chances of oversight.
Challenges in Watchlist Screening
While watchlist screening is a critical component of risk management, it comes with its own set of challenges that businesses must navigate. Here are five common challenges associated with watchlist screening:
1. False Positives and Negatives:
One of the significant challenges is the occurrence of false positives and negatives. False positives, where legitimate entities are mistakenly flagged as high risk, can lead to unnecessary disruptions and strain relationships. On the other hand, false negatives, failing to identify actual risks, can expose the business to potential threats. Striking a balance to minimize both types of errors is a constant challenge.
2. Data Accuracy and Completeness:
The effectiveness of watchlist screening relies heavily on the accuracy and completeness of the data used. Incomplete or outdated information in watchlists can result in overlooking potential risks, while inaccuracies can lead to false identifications. Regularly updating and validating watchlist data poses a perpetual challenge for businesses.
3. Scalability Issues:
As businesses grow and transaction volumes increase, scalability becomes a significant challenge. Traditional screening systems may struggle to handle large datasets efficiently, leading to delays in processing and potentially missing critical information. Ensuring that the screening process can scale with the business is an ongoing concern.
4. Regulatory Complexity:
The regulatory landscape around watchlist screening is intricate and subject to frequent changes. Businesses must stay abreast of evolving compliance requirements, which often vary across jurisdictions. Adapting to new regulations and ensuring that the screening process aligns with these standards is a constant challenge, particularly for organizations operating in multiple regions.
5. Balancing Speed and Accuracy:
Achieving a balance between the speed of screening and the accuracy of results is a perpetual challenge. Rapid processing is essential, especially in industries where time-sensitive transactions are common. However, the need for speed should not compromise the precision of the screening process. Striking this delicate balance requires careful optimization of screening algorithms and processes.
Best Practices in Watchlist Screening
Watchlist screening best practices are crucial for ensuring the effectiveness of risk management strategies while maintaining operational efficiency and regulatory compliance. Here are key best practices businesses should consider:
1. Comprehensive Training and Education:
Ensure that personnel involved in the watchlist screening process receive thorough training on the intricacies of the system, including understanding different types of risks, interpreting alerts, and responding appropriately. Continuous education helps staff stay abreast of evolving threats and improves the accuracy of screening.
2. Risk-Based Approach:
Adopt a risk-based approach to screening, prioritizing entities based on their perceived risk level. This allows businesses to allocate resources more efficiently, focusing on high-risk entities while streamlining the screening of lower-risk ones.
3. Regular Watchlist Updates:
Keep watchlists up-to-date by regularly checking for updates and additions. Staying current with the latest information ensures that the screening process reflects the most recent risk profiles, reducing the chances of overlooking potential threats.
4. Integration with Workflow:
Integrate watchlist screening seamlessly into existing workflows to minimize disruptions. The screening process should align with the organization's operational procedures, allowing for efficient checks without causing unnecessary delays in transactions or processes.
5. Continuous Monitoring:
Implement continuous monitoring rather than relying solely on periodic checks. This proactive approach helps identify emerging risks in real-time, allowing businesses to respond promptly and mitigate potential threats before they escalate.
How To Choose Best Watchlist Screening Software Provider?
Choosing the best watchlist screening solutions provider requires a detailed evaluation process. Look for a provider with a proven track record in the industry, emphasizing experience, reliability, and compliance with regulatory standards.
Consider the flexibility of the software to accommodate evolving business needs and its ability to scale with growth. Ensure the solution integrates seamlessly with existing workflows and offers user-friendly interfaces. Look for advanced features such as real-time monitoring, sophisticated algorithms, and regular updates to watchlists.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
How Tookitaki’s Smart Screening Solution Helps in Watchlist Screening?
Tookitaki's AML Smart Screening product offers a comprehensive approach to customer screening, aimed at enhancing the safety and efficiency of financial transactions. Here are the key aspects of this product:
- Comprehensive Customer Screening: It enables the growth of customer bases with continuous and accurate screening against various watchlists like sanctions, PEP, and adverse media.
- Enhanced Onboarding and Risk Detection: The product facilitates rapid customer onboarding with minimal risk by leveraging a powerful screening engine that detects risky customers in real time.
- Reputational Risk Mitigation: It offers protection against reputational damage through extensive screening coverage, employing over 50 name-matching techniques and supporting multiple customer attributes and all types of watchlists.
- Real-Time Payment Security: The solution ensures secure expansion of both domestic and cross-border payments with real-time screening, along with secure and seamless merchant acquisition.
- Advanced AI/ML Solution: The AML Smart Screening uses AI and machine learning to detect risky customers and transactions, supporting both real-time and batch screening for onboarding and ongoing due diligence.
- Customizable Solution: It can be tailored to meet specific organizational needs, aligning with individual compliance policies and risk tolerances.
- Effective Handling of False Positives: Advanced matching algorithms, including fuzzy matching, are employed to generate accurate screening hits and reduce false positives significantly.
- Suitability for Diverse Sectors: AML Smart Screening is adaptable for financial institutions across various sectors and regulatory environments, allowing customization to specific compliance requirements.
This combination of features makes Tookitaki's AML Smart Screening a robust tool for organizations looking to enhance their anti-money laundering efforts and customer screening processes.
Economic Sanctions
Economic sanctions, in essence, are punitive measures imposed by one or more countries against another in an effort to alter the targeted nation's behavior.These actions, driven by political motives, have widespread effects on the economies, societies, and politics of the countries they aim at.
Key Takeaways
- Economic sanctions are punitive measures: Imposed by countries to alter the targeted nation's behaviour, these sanctions are driven by political motives and can significantly impact economies, societies, and politics.
- Sanctions aim to induce policy changes: By inflicting economic hardships or diplomatic isolation, sanctions are strategically designed to pressure the targeted country to comply with international norms or address specific concerns.
- Various forms of sanctions exist: These include trade restrictions, asset freezes, financial penalties, diplomatic measures, arms embargoes, and travel bans, each with its own impact and methodology.
- Sanctions work by exerting economic pressure: They restrict a nation's global trade capabilities, access to financial resources, and acquisition of goods, making non-compliance more costly.
- Sanctions have broad impacts: They can significantly affect the targeted country's economy and society, leading to declines in critical exports, currency depreciation, and humanitarian challenges like healthcare and unemployment.
What Are Economic Sanctions?
Economic sanctions can be characterized as a set of punitive actions implemented by one or more nations against another, with the objective of pressuring the targeted country to reconsider its policies, comply with international norms, or address specific concerns.
These measures, often diplomatic and economic in nature, are strategically designed to induce a change in the behavior or decisions of the targeted nation by inflicting economic hardships or diplomatic isolation. Now that you know the economic sanction meaning, let us take a look at the forms of economic sanctions.
1. Trade Restrictions:
- Definition: Trade restrictions involve limitations on the exchange of goods and services between the targeted nation and the countries imposing sanctions.
- Example: Embargoes or restrictions on specific exports or imports, hindering the targeted nation's access to vital resources or markets.
2. Asset Freezes:
- Definition: Asset freezes entail the prohibition of targeted individuals, entities, or governments from accessing or transferring their financial assets held in the imposing countries.
- Example: Freezing bank accounts, seizing assets, or restricting financial transactions, thereby immobilizing financial resources and influencing decision-makers.
3. Financial Penalties:
- Definition: Financial penalties involve the imposition of fines or economic burdens on the targeted nation, either directly or indirectly, to induce compliance with specific demands or international norms.
- Example: Levying fines, restricting access to international financial institutions, or imposing penalties on entities involved in activities deemed unacceptable.
4. Diplomatic Measures:
- Definition: Diplomatic measures encompass actions that isolate the targeted nation on the international stage, limiting its diplomatic relationships and interactions.
- Example: Expelling diplomats, reducing embassy staff, or boycotting international conferences, aiming to diplomatically isolate the targeted government.
5. Arms Embargoes:
- Definition: Arms embargoes involve restrictions on the sale, purchase, or transfer of military equipment and weapons to the targeted nation.
- Example: Prohibiting the export of arms to a nation engaged in activities contrary to international peace or security.
6. Travel Bans:
- Definition: Travel bans restrict the movement of certain individuals associated with the targeted government, limiting their ability to travel internationally.
- Example: Denying visas or travel privileges to government officials or individuals involved in activities that warrant sanctions.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
How Do Economic Sanctions Work?
To comprehend the impact of economic sanctions, it is crucial to dissect the mechanics through which these measures exert influence. At their core, economic sanctions operate on the principle of economic pressure. Sanctions try to make a country follow certain rules by restricting its ability to engage in global trade, access financial resources, and obtain goods. The idea is to make not following the rules more costly than sticking to them.
This delicate dance between pressure and restraint requires a nuanced understanding of the targeted nation's vulnerabilities and dependencies. A strategic imposition of sanctions involves identifying key economic pressure points without plunging the population into a humanitarian crisis. Striking this balance demands a meticulous assessment of the targeted nation's economic structure, trade relationships, and social fabric.
Economic Sanctions Example - Venezuelan Economic Sanctions
The situation in Venezuela has been marked by a complex web of economic and political challenges. The United States, along with several other countries, has imposed a series of economic sanctions on Venezuela. These sanctions have evolved over time and targeted various aspects of the country's economy. Here's a breakdown of the mechanisms involved:
1. Oil Sector Sanctions:
The U.S. placed restrictions on Venezuela's oil industry, which is a key way the country makes money. These sanctions restricted the export and sale of Venezuelan oil, significantly impacting the nation's economic lifeline.
2. Financial Sanctions:
Measures included restrictions on access to international financial markets and freezing of assets belonging to key Venezuelan officials. This aimed to limit the government's ability to secure financing and manage its economic challenges.
3. Diplomatic Measures:
The U.S. and several other countries recognized opposition leader Juan Guaidó as the legitimate president of Venezuela, isolating the government of Nicolás Maduro diplomatically.
How Are Economic Sanctions Legislated?
The process of legislating economic sanctions is a complex interplay between domestic and international law. Nations may impose sanctions unilaterally, but multilateral sanctions orchestrated by international organizations such as the United Nations often carry more weight. Understanding the legal foundations of economic sanctions is vital for navigating the intricate landscape of international relations.
What Are Primary Economic Sanctions?
Primary economic sanctions are the initial measures taken against a targeted nation. These can include trade embargoes, restrictions on financial transactions, and the freezing of assets. The following primary economic sanctions example provides insight into the diverse strategies employed by nations to achieve their policy objectives.
Primary economic sanctions were imposed on North Korea by the United Nations in response to its nuclear weapons and ballistic missile development programs. These sanctions were designed to curb North Korea's ability to fund and advance its nuclear capabilities. Key components of the primary economic sanctions included:
1. Trade Embargoes:
The United Nations Security Council (UNSC) imposed restrictions on North Korea's trade, prohibiting the export and import of certain goods and commodities. This aimed to limit the nation's access to critical resources and technology.
2. Financial Transaction Restrictions:
The UNSC imposed measures restricting North Korea's access to the international financial system. This included limitations on foreign financial institutions engaging in transactions with North Korean banks, thereby hindering the flow of funds to support prohibited activities.
3. Freezing of Assets:
The freezing of assets targeted individuals, entities, and government officials associated with North Korea's nuclear and missile programs. This measure aimed to prevent the movement of funds and assets that could contribute to the advancement of prohibited activities.
4. Arms Embargo:
An arms embargo was instituted to prevent the transfer of military equipment, weapons, and related technology to North Korea. This restriction aimed to curb the nation's ability to enhance its military capabilities through external support.
Impact of Economic Sanctions on Targeted Countries
Putting economic sanctions on a country can cause significant effects, affecting its economy, society, and how it fits into global politics. There are sanctions against countries like Turkey and Iran. Let's explore the impact of economic sanctions on Iran as a case study.
Economic Consequences
- Decline in Oil Exports: Iran, a major oil-producing nation, faced a significant decline in oil exports due to sanctions imposed by the United States and the European Union. These sanctions restricted Iran's ability to sell oil on the global market, leading to a substantial reduction in revenue from its crucial oil industry.
- Currency Depreciation: The sanctions contributed to the depreciation of the Iranian rial, leading to economic instability. The reduced access to global financial systems made it challenging for Iran to stabilize its currency and manage inflation effectively.
- Impact on Trade: Trade restrictions hindered Iran's ability to engage in international trade, affecting various industries. Import-dependent sectors faced shortages of essential goods, and the overall trade balance of the country was adversely affected.
Humanitarian and Social Impact
- Healthcare Challenges: The sanctions created obstacles in procuring medical supplies and technology for Iran's healthcare system. This had direct consequences on the health and well-being of the Iranian population, particularly during global health crises such as the COVID-19 pandemic.
- Rise in Unemployment: Economic sanctions contributed to job losses and increased unemployment rates. Industries facing trade restrictions and financial challenges were forced to cut back on production, leading to workforce layoffs and economic hardship for families.
- Education and Social Services: The economic strain affected the funding of education and social services. Reduced government revenue impacted the ability to invest in public services, potentially limiting access to quality education and social welfare programs.
Geopolitical Implications
- Shift in Diplomatic Dynamics: Iran's response to economic sanctions included diplomatic efforts to seek relief and negotiations with the international community. The geopolitical landscape witnessed shifts in alliances and diplomatic engagements as Iran sought ways to mitigate the impact of sanctions.
- Nuclear Negotiations: Economic sanctions played a role in prompting Iran to engage in negotiations over its nuclear program. In 2015, the Joint Comprehensive Plan of Action (JCPOA) was a deal that tried to lift sanctions on Iran in return for them putting restrictions on their nuclear activities. This highlighted how diplomatic efforts can be influenced by economic pressure.
Read more about sanctions against Turkey.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Importance of Sanctions Screening for Financial Institutions
In the ever-evolving landscape of international finance, financial institutions play a pivotal role in maintaining the integrity and stability of the global financial system. The importance of sanctions screening lies in its ability to identify and prevent transactions that violate international sanctions, mitigating the risk of financial institutions inadvertently facilitating prohibited activities. By implementing robust sanctions screening processes, financial entities not only ensure compliance with regulatory frameworks but also contribute significantly to the broader efforts of preventing illicit financial activities and safeguarding the integrity of the international financial system.
Conclusion
Economic sanctions are potent instruments in the realm of international diplomacy, with far-reaching consequences. A nuanced understanding of their definition, mechanisms, legislation, and impact is essential for policymakers, scholars, and anyone navigating the complex web of global affairs.
Forex Compliance
EIn the ever-evolving landscape of Forex trading, where currencies are bought and sold globally, understanding and implementing Forex compliance standards are not just prudent; they are imperative. In this comprehensive guide, we'll explore the details of Forex compliance, delving into its significance, regulatory requirements, and steps for traders and brokers to ensure adherence.
Key Takeaways
- Forex Trading Compliance is Crucial: It ensures market fairness, protects against manipulation, and is a legal requirement for brokers and traders globally.
- Compliance Includes Various Requirements: This involves obtaining licenses, adhering to AML and KYC procedures, providing risk disclosure statements, and segregating client funds.
- Non-Compliance Leads to Severe Consequences: Ignoring Forex regulations can result in hefty financial penalties and damage to reputation, as seen in the 2015 case of major banks.
- Comprehensive Measures for Compliance: These include setting leverage limits, ensuring transparent order execution, meticulous record-keeping, and robust cybersecurity measures.
- Education and KYC are Integral: Educating investors and thorough customer due diligence (CDD) are essential for a secure and informed trading environment.
What is Forex Trading and its Compliance?
Forex trading, short for foreign exchange trading, involves the exchange of currencies on the global market. It operates 24 hours a day, five days a week, making it one of the most accessible and liquid financial markets in the world. Unlike traditional stock markets, Forex doesn't have a central exchange control; instead, it functions as an over-the-counter (OTC) market where currencies are traded electronically through a network of banks, financial institutions, corporations, governments, and individual traders.
In this vast and decentralized market, adherence to Forex compliance is not just a legal requirement but a fundamental necessity. It makes sure the market is fair, clear, and reliable for everyone involved. While compliance standards may differ in various regions, they all have the same aim: protecting the interests of traders and investors while maintaining the market's integrity.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Why is Forex Compliance Essential?
Forex compliance acts as a shield, protecting the market from manipulation and ensuring a level playing field for all participants. Market manipulation, such as spoofing or pump-and-dump schemes, distorts prices and erodes investor confidence. Compliance standards act as a deterrent, discouraging unscrupulous actors from engaging in such practices. By adhering to these standards, the market remains stable, and investors can make decisions based on genuine market dynamics, fostering trust and confidence.
Non-compliance with Forex regulations can have severe repercussions, leading to financial penalties and reputational damage. One notable example occurred in 2015 when five major banks, including JPMorgan Chase and Citigroup, pleaded guilty to manipulating the foreign exchange market and collectively paid fines totaling more than $2.5 billion. This incident not only showed the severe outcomes of not following the rules but also underlined how crucial it is to stick to Forex compliance standards.
Compliance Requirements for Forex Brokers and Traders
1. Regulatory Licensing and Registration
Obtaining the necessary licenses and registrations is the cornerstone of Forex compliance. Regulatory authorities, such as the Financial Conduct Authority (FCA) in the UK and the Commodity Futures Trading Commission (CFTC) in the United States, oversee and regulate Forex brokers and traders. These licenses serve as a testament to the broker's credibility and adherence to industry standards.
2. AML and KYC Procedures
Anti-Money Laundering (AML) and Know Your Customer (KYC) procedures are integral components of Forex compliance. AML regulations are created to stop illegal financial activities like money laundering and funding terrorism. Brokers and traders can ensure their clients are not involved in fraud by putting strict checks in place to verify their identities. KYC procedures provide an additional layer of security, enabling brokers to understand their clients' financial backgrounds, risk tolerance, and trading objectives.
3. Risk Disclosure Statements
Forex compliance mandates the provision of clear and comprehensive risk disclosure statements to traders. These documents explain the possible dangers of Forex trading, like market ups and downs, global events, and economic factors that can affect the value of currencies. By empowering traders with this information, brokers enable them to make well-informed decisions, mitigating the risk of unexpected losses.
4. Client Fund Segregation
Segregating client funds from the broker's operational funds is a fundamental practice mandated by Forex compliance. This separation ensures that clients' investments remain protected, even in the unlikely event of the broker facing financial challenges or bankruptcy. By ring-fencing client funds, brokers demonstrate their commitment to the security of their clients' investments.
5. Margin and Leverage Limits
Forex trading offers significant opportunities, but it also carries inherent risks. Forex compliance sets limits on margin trading and leverage to prevent excessive risk-taking. These limits protect traders from substantial losses and maintain market stability. By enforcing responsible trading practices, regulatory authorities strike a balance between market participation and risk mitigation.
6. Order Execution Policies
Transparent and fair order execution policies are at the core of Forex compliance. Compliance guidelines specify the procedures for order execution, ensuring that all traders, regardless of their account size or trading volume, receive equal and fair treatment. By minimizing the scope for manipulation, these policies uphold market integrity, fostering trust between traders and brokers.
7. Reporting and Record-Keeping
Accurate record-keeping and timely reporting of foreign currency transaction is an essential component of compliance. Brokers and traders are required to maintain meticulous documentation of all trading activities, including order placements, executions, and account statements. These records serve as a valuable resource for regulatory authorities, enabling them to monitor market activities and investigate discrepancies effectively. The New York Fed has provided guidelines for foreign exchange trading activities.
8. Cybersecurity Measures
Brokers and trading platforms handle vast amounts of sensitive data, including clients' personal information and financial details. Forex compliance mandates the implementation of robust cybersecurity measures to protect this data from unauthorized access, breaches, or cyber-attacks. Encryption protocols, secure authentication processes, and regular security audits are essential components of a comprehensive cybersecurity strategy.
9. Forex Trading Restrictions
The Forex market operates globally, but specific geographical regions may have unique restrictions on Forex trading. In 2015, for instance, the Chinese government implemented strict restrictions on Forex trading for its citizens. The government put these restrictions in place to manage the flow of money leaving the country and to keep the country's currency, the yuan (CNY), stable. Compliance requires brokers and traders to be aware of these restrictions and adhere to the applicable regulations.
10. Disclosure of Trading Risks
Brokers are obligated to disclose potential risks associated with specific trading strategies or investments to their clients. These disclosures empower traders to make well-informed decisions, aligning their trading activities with their risk tolerance and financial goals. By providing comprehensive risk disclosures, brokers establish a foundation of trust with their clients.
11. Investor Education and Information Dissemination
Educating investors about Forex trading and disseminating relevant information is an integral part of compliance. Informed investors contribute significantly to a healthy market environment. Brokers are responsible for providing educational resources, market analysis, and trading guides to their clients. By enhancing traders' knowledge and understanding of the Forex market, brokers empower them to make educated trading decisions.
12. Tax Compliance
Forex traders are obligated to comply with tax regulations in their respective jurisdictions. Adhering to tax laws ensures legal compliance and financial transparency. Brokers and traders must accurately report their trading profits and losses, as well as adhere to tax payment deadlines. Failure to comply with tax regulations can lead to legal consequences, including fines and penalties. Additionally, tax compliance ensures that governments receive their fair share of revenue, contributing to public services and infrastructure development.
Forex Compliance While Customer Onboarding
When onboarding customers, brokers shoulder the responsibility of upholding the highest standards of Forex compliance. The customer onboarding process is not just a series of administrative tasks; it is a crucial step in establishing a foundation of trust and transparency between brokers and traders. Verification of customer identities, the meticulous disclosure of risks, and unwavering adherence to regulatory guidelines lie at the heart of these processes.
Additionally, brokers must prioritize ongoing education during customer onboarding. Providing traders with resources and educational materials about Forex trading, risk management strategies, and market analysis equips them with the knowledge necessary to make informed decisions. Educated traders are more likely to navigate the complexities of the Forex market prudently, thereby reducing the likelihood of impulsive or emotionally-driven trades.
The Importance of Customer Due Diligence and KYC
Customer Due Diligence (CDD) and Know Your Customer (KYC) procedures are not mere formalities; they are the backbone of a secure trading environment. Conducting thorough due diligence on prospective clients is paramount in assessing the risks associated with them. By delving deep into their backgrounds, financial histories, and trading intentions, brokers gain invaluable insights. This process acts as a potent defense against fraudulent activities, ensuring that brokers engage exclusively with legitimate entities.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Steps in Forex Compliance
- Education and Training: Continuous education and training of staff to stay updated with changing regulations.
- Regular Audits: Conducting regular internal audits to ensure compliance with established standards.
- Communication: Transparent communication with clients about compliance requirements and changes in regulations.
- Collaboration with Compliance Experts: Collaborating with compliance experts to navigate complex regulatory landscapes effectively.
Identifying Compliance Risks and Red Flags
Brokers and traders must be vigilant in identifying compliance risks and red flags. Unusual trading patterns, discrepancies in documentation, or suspicious foreign currency transactions should be investigated promptly to maintain market integrity.
Smoothen Your Forex Compliance with Tookitaki
By embracing Forex compliance, traders and brokers create a secure and transparent trading environment, fostering trust among participants. Stay updated, adhere to regulations, and consider leveraging advanced solutions like Tookitaki to streamline your compliance processes. Remember, a compliant Forex market is a thriving Forex market.
Global Watchlist
In today's landscape, where business operations seamlessly cross international borders, and financial transactions extend across continents, the need for a robust compliance framework is more crucial than ever. At the forefront of this framework is the concept of a comprehensive global watchlist. This tool has evolved into an indispensable asset for organizations aiming to safeguard their operations, maintain regulatory compliance, and shield themselves against potential risks that can emerge from complex, cross-border business activities.
What is a Global Watchlist?
A global watchlist is a curated database containing information on individuals, entities, or countries that pose a potential risk due to involvement in illegal activities. This could range from money laundering and fraud to terrorism financing.
This comprehensive database acts as a preemptive measure, offering businesses a strategic means to identify and evaluate potential risks before they can adversely impact operations. Each entry in the global watchlist represents a red flag or a potential warning sign that necessitates closer scrutiny. By maintaining and regularly updating this repository, regulatory authorities, financial institutions, and businesses can stay ahead of emerging threats and swiftly adapt to the evolving landscape of financial and security risks.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
In the context of financial institutions and businesses, the global watchlist serves as a critical tool for due diligence. It enables organizations to screen their clients, partners, and transactions against the entries in the watchlist, ensuring that they comply with international regulations and uphold the highest standards of integrity. This proactive screening process not only aids in meeting legal obligations but also safeguards the reputation of the business and mitigates the financial and legal risks associated with inadvertent involvement in illicit activities.
The global watchlist is not static; it evolves alongside the dynamic nature of global risks. As regulatory frameworks change, and new threats emerge, the watchlist adapts to reflect the most current and relevant information. This ensures that businesses are equipped with the latest intelligence, empowering them to make informed decisions and maintain a vigilant stance against potential risks that may compromise their operations and ethical standing in the global marketplace.
Types of Global Watchlists
Global watchlists come in various forms, tailored to address different aspects of risk. Some common types include sanctions lists, politically exposed persons (PEP) lists, and regulatory watchlists. Each serves a unique purpose, collectively forming a robust defense against financial crimes and illicit activities.
1. Sanctions Lists:
Sanctions lists are a fundamental component of global watchlists, designed to identify and track individuals, entities, or even entire nations subject to economic or trade restrictions. These restrictions can be imposed by individual countries, international bodies, or coalitions of nations. The goal is to prevent these sanctioned parties from engaging in financial transactions that could contribute to activities such as terrorism, human rights abuses, or violations of international law. By screening against sanctions lists, businesses ensure compliance with international sanctions and avoid inadvertent involvement with entities subject to economic restrictions.
2. Politically Exposed Persons (PEP) Lists:
PEP lists specifically target individuals who hold prominent public positions or have connections to influential figures. These individuals, due to their roles in government, public service, or international organizations, may be susceptible to corruption, bribery, or other illicit financial activities. PEP lists help businesses identify and scrutinize relationships with these high-risk individuals, allowing for enhanced due diligence and risk mitigation. Screening against PEP lists is crucial for financial institutions and businesses to prevent the exploitation of influential connections for illicit gains.
3. Regulatory Watchlists:
Regulatory watchlists encompass a broader range of entities and activities, often dictated by specific industry regulations and compliance standards. These lists include entities that may not be explicitly covered by sanctions or PEP lists but are subject to specific regulatory scrutiny based on the nature of their business or operations. For example, financial institutions may refer to watchlists related to anti-money laundering (AML) or know your customer (KYC) regulations. By adhering to regulatory watchlists, businesses ensure compliance with industry-specific guidelines, thereby reducing the risk of financial impropriety and maintaining operational integrity.
4. Other Specialized Lists:
Beyond the aforementioned common types, global watchlists can extend to cover specialized areas of risk. This may include lists related to human trafficking, organized crime, cyber threats, and more. These specialized watchlists cater to the evolving nature of global risks, ensuring that businesses remain vigilant against emerging threats that may not be addressed by traditional categories. By incorporating a diverse range of watchlists into their screening processes, organizations build a comprehensive defense mechanism against a wide array of potential risks.
Global Watchlist Screening: How Does it Work?
Global watchlist screening involves cross-referencing individuals, entities, or transactions against the entries on the watchlist. Automated screening tools employ sophisticated algorithms and artificial intelligence to swiftly identify potential matches. This proactive approach helps organizations identify and mitigate risks before they escalate, ensuring compliance with regulatory requirements.
1. Cross-Referencing and Matching:
At the core of global watchlist check is the meticulous process of cross-referencing. This involves systematically comparing the data associated with individuals, entities, or transactions against the entries stored in the global watchlist. The data points include names, addresses, identification numbers, and other relevant information. By conducting this thorough examination, organizations aim to identify any potential matches with entries on the watchlist, indicating a possible association with high-risk activities.
2. Automated Screening Tools:
The sheer volume and complexity of global transactions necessitate the use of advanced technology to streamline the screening process. Automated screening tools play a pivotal role in efficiently and accurately scanning vast datasets against the entries in the watchlist. These tools leverage sophisticated algorithms and artificial intelligence (AI) to expedite the identification of potential matches. The advantage of automation lies in its ability to process large quantities of data at high speeds, significantly reducing the time and resources required for manual screening.
3. Sophisticated Algorithms:
The algorithms employed in global watchlist screening are designed to recognize not only exact matches but also variations in names, addresses, and other data points. This adaptability is crucial in overcoming challenges such as typographical errors, misspellings, or variations in data formats. The use of fuzzy matching algorithms allows screening tools to account for these discrepancies, ensuring a more comprehensive and accurate identification of potential matches.
4. Real-Time Updates:
The effectiveness of global watchlist screening relies on the timeliness of the information. Automated screening tools often integrate with databases that receive real-time updates from various regulatory bodies and international organizations. This ensures that organizations have access to the most current and relevant data, allowing them to stay ahead of emerging risks and comply with evolving regulatory requirements.
5. Proactive Risk Mitigation:
Global watchlist screening is inherently proactive, providing organizations with the means to identify and address potential risks before they escalate. By swiftly detecting matches with entries on the watchlist, businesses can take immediate actions, such as enhanced due diligence, further investigation, or even reporting suspicious activities to regulatory authorities. This proactive approach is crucial in maintaining the integrity of financial systems, preventing illicit transactions, and safeguarding against the reputational and financial consequences of inadvertent involvement in unlawful activities.
6. Ensuring Compliance with Regulatory Requirements:
One of the primary objectives of global watchlist screening is to ensure compliance with regulatory requirements. Many industries, especially financial institutions, are subject to stringent regulations related to anti-money laundering (AML), know your customer (KYC), and other compliance standards. By integrating automated screening tools into their processes, organizations can demonstrate a commitment to meeting these regulatory obligations, reducing the risk of legal repercussions and associated fines.
Why is Global Watchlist Screening Important?
Global watchlist screening is the frontline defense against financial crimes, money laundering, and terrorism financing. By adopting this preventive measure, businesses protect their reputation, financial stability, and adhere to international compliance standards.
1. Safeguarding Against Financial Crimes:
Global watchlist screening serves as the frontline defense against a spectrum of financial crimes that can jeopardize the integrity of businesses. It acts as a proactive shield, identifying individuals, entities, or transactions associated with money laundering, fraud, and other illicit financial activities. By preventing these activities at the outset, businesses protect their financial assets and contribute to the overall stability of the global financial system.
2. Mitigating Risks to Reputation:
One of the most significant assets a business possesses is its reputation. In an interconnected world where information travels swiftly, any association with financial impropriety can have profound and lasting effects on a company's standing. Global watchlist screening acts as a crucial component of risk management, helping organizations avoid inadvertent connections with high-risk individuals or entities. By doing so, businesses preserve their reputation, instill trust among stakeholders, and maintain a positive brand image.
3. Upholding International Compliance Standards:
In an era of increasing regulatory scrutiny, adherence to international compliance standards is non-negotiable. Global watchlist screening ensures that businesses follow rules related to preventing money laundering, knowing their customers, and adhering to sanctions. Failing to meet these standards can result in severe legal consequences, including hefty fines and sanctions. By adopting robust watchlist screening measures, organizations demonstrate their commitment to ethical business practices and align themselves with global regulatory expectations.
4. Preventing Terrorism Financing:
Global watchlist screening plays a pivotal role in preventing the flow of funds to entities associated with terrorism. By cross-referencing transactions against watchlists, businesses can identify and block financial activities linked to individuals or organizations involved in terrorism financing. This not only contributes to global security efforts but also positions businesses as responsible actors in the fight against illicit activities that pose a threat to national and international stability.
5. Legal Repercussions and Fines:
Failure to implement robust watchlist screening can have serious legal consequences. Regulatory bodies worldwide are increasingly stringent in enforcing compliance standards, and businesses that neglect proper screening may face legal actions and substantial fines. The cost of non-compliance can extend beyond financial penalties to include legal battles, operational disruptions, and, in extreme cases, the revocation of business licenses. Robust watchlist screening, therefore, acts as a preventive measure, reducing the risk of legal entanglements and associated financial penalties.
6. Proactive Risk Management:
Global watchlist screening is not merely a regulatory requirement; it is a proactive approach to risk management. By identifying and mitigating potential risks before they materialize, businesses safeguard their financial stability and protect the interests of stakeholders. This proactive stance not only aligns with ethical business practices but also positions organizations as responsible and trustworthy partners in the global business ecosystem.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
What is a Global Watchlist Screening Solution?
A global watchlist screening solution is a comprehensive software tool designed to streamline the screening process. These solutions often feature real-time updates, customizable risk thresholds, and user-friendly interfaces. By integrating these solutions into their systems, businesses can enhance the efficiency and accuracy of their compliance efforts.
How Tookitaki Can Help in Watchlist Screening
In the competitive landscape of compliance solutions, Tookitaki stands out as a leader in the field of global watchlist screening with its Smart Screening Solution. Offering cutting-edge technology, Tookitaki provides a holistic approach to risk management. Their platform not only ensures compliance but also adds value through advanced analytics, reducing false positives and optimizing the screening process.
Check Fraud
In today's financial landscape, check fraud poses a significant threat to individuals and businesses alike. In the initial half of 2014, scammers managed to steal a minimum of $9.4 million from commercial banks in Kenya. This article delves deep into check fraud, its various types, real-life examples, preventive measures, and how innovative tools like Tookitaki can play a pivotal role. Also read about Fraud Detection in Banking.
Types of Check Fraud
Check fraud encompasses various deceptive practices involving checks, leading to financial losses for individuals and businesses. Here are some common types of check fraud:
1. Forgery:
Description: Involves the creation of a fraudulent check signature. Perpetrators may steal a legitimate check and attempt to replicate the signature or create a completely fake check.
Example: Someone finds a lost check, forges the signature, and attempts to cash it.
2. Counterfeit Checks:
Description: Sophisticated criminals use advanced printing techniques to create counterfeit checks that closely resemble genuine ones. These checks can be challenging to distinguish without careful inspection.
Example: Criminals use high-quality printers to replicate checks with accurate bank logos and watermarks.
3. Account Hijacking:
Description: Fraudsters gain unauthorized access to a person's or business's account information, using it to create and cash fraudulent checks.
Example: Obtaining login credentials through phishing and then using the account details to create and cash fake checks.
4. Check Kiting:
Description: Involves taking advantage of the time it takes for a check to clear by creating a cycle of writing checks between two or more bank accounts with insufficient funds.
Example: Writing a check from Account A to Account B, then writing another check from Account B to Account A before the initial check clears.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
5. Altered Checks:
Description: Perpetrators modify a legitimate check by altering the payee name, the amount, or other crucial details to divert funds to themselves.
Example: Changing the written amount on a check from $100 to $1,000 before attempting to cash it.
6. Check Washing:
Description: Involves erasing or altering details on a legitimate check, such as the payee name or the written amount, often using chemicals.
Example: Criminals use chemicals to remove the ink from a payee's name on a check and replace it with their own name.
7. Remote Deposit Capture Fraud:
Description: Exploits the convenience of remote deposit capture, where individuals or businesses can deposit checks using mobile devices. Fraudsters submit counterfeit checks for remote deposits.
Example: Taking pictures of counterfeit checks and submitting them through a mobile banking app for deposit.
8. Identity Theft-Related Check Fraud:
Description: Involves using stolen identity information to open bank accounts or order checks in someone else's name for fraudulent transactions. Identity verification and a thorough document check is essential while opening a bank account or carrying out a transaction.
Example: Criminals use a victim's personal information to open a bank account and write fraudulent checks.
Real-Life Examples of Check Fraud
1. Texas Tycoon's Costly Gamble
Between 2004 and 2006, a Texan entrepreneur named Jeff Woodward orchestrated a clever but illegal financial game involving his motorsports and car dealership businesses. Woodward engaged in what's known as a check kiting scheme, juggling funds between four different bank accounts. Each day, either Woodward or his associates deposited checks they knew were bad into one account, and swiftly withdrew money from others.
To cover his tracks, Woodward personally signed half of these dubious checks, while instructing his employees to sign the rest. The grand total of these deceptive checks reached a staggering $114 million, resulting in hefty losses amounting to $1.6 million for the banks involved. Woodward's financial gambit didn't go unnoticed, and he eventually faced the consequences – a four-year federal prison sentence, five years of supervised release, and a hefty restitution order of $2.5 million.
2. Cleveland's High-Stakes Deception
In the heart of Cleveland, three enterprising young women orchestrated a check kiting scheme that played out like a high-stakes gamble. Their game resulted in a $165,000 windfall, but it came at a steep cost – $120,000 in losses for the banks involved.
The trio's modus operandi was deceptively simple yet effective. They persuaded unsuspecting individuals to open new checking accounts, promising lucrative returns. Once the accounts were set up, the women deposited checks they knew were either bad or counterfeit. Exploiting the time it takes for banks to catch on, they withdrew substantial amounts of cash at a local casino before the banks could flag the checks.
The scheme unfolded over 31 occasions, with the women managing to dodge detection until law enforcement caught wind of their activities. The FBI, along with assistance from the Ohio Casino Control Commission, investigated the case, leading to prosecution by Assistant U.S. Attorneys.
Reporting About Check Frauds
When it comes to checking fraud, swift and accurate reporting is akin to protect both individual and collective financial well-being. The process of reporting check fraud involves a series of crucial steps that empower individuals, businesses, and financial institutions to mitigate the damage caused by fraudulent activities.
1. Recognizing the Signs:
The first challenge lies in recognizing the signs of potential check fraud. This could include unusual transactions, unauthorized access to accounts, or the discovery of suspicious checks. Individuals must remain vigilant, regularly monitoring their bank statements and account activity to promptly identify any irregularities.
Also Read: Fraud Detection in Banking
2. Immediate Action:
Upon suspecting or confirming check fraud, taking immediate action is paramount. The affected individual or business should contact their bank or financial institution as soon as possible. Most institutions have dedicated fraud departments equipped to handle such incidents. Prompt communication allows the bank to initiate investigations promptly, potentially stopping further fraudulent transactions.
3. Providing Essential Information:
When reporting check fraud, providing comprehensive information is crucial. This includes details such as the date and amount of the fraudulent transaction, the check number, and any relevant information about the suspected perpetrator. The more detailed the information, the more efficiently the financial institution or law enforcement can pursue the case.
4. Collaborating with Law Enforcement:
In severe cases, reporting check fraud may involve collaboration with law enforcement agencies. Local police, the FBI, or other relevant authorities can take legal action against the perpetrators. It is important to file a police report, which serves as an official record of the incident and aids in the investigative process.
5. Working with Financial Institutions:
Cooperation with the affected financial institution is a key aspect of the reporting process. This involves providing any requested documentation or information to aid in their internal investigations. Financial institutions, armed with this information, can take preventive measures to strengthen their security protocols and protect other account holders.
6. Staying Informed:
Following the reporting of check fraud, staying informed about the progress of investigations and any developments is essential. Financial institutions may provide updates on the resolution of the case, and individuals should remain engaged in the process to ensure a satisfactory resolution.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Prevention Measures for Check Fraud
Check fraud is a pervasive threat, but with the right preventive measures in place, individuals and businesses can significantly reduce their vulnerability to these deceptive practices. Implementing a multi-faceted approach to check fraud prevention is crucial for maintaining financial integrity. Here's a detailed exploration of effective prevention measures:
1. Secure Your Checks:
Tamper-Evident Checks: Consider using tamper-evident checks that make any alteration or tampering immediately apparent.
Secure Storage: Store checks in a secure location, such as a locked cabinet or safe, minimizing the risk of unauthorized access.
2. Monitor Accounts Regularly:
Frequent Checkups: Regularly review bank statements and account activity. Timely detection of suspicious transactions allows for prompt action.
Leverage Alerts: Set up account alerts for unusual activities, such as large transactions or withdrawals, to receive immediate notifications.
3. Educate Employees and Individuals:
Training Programs: For businesses, conduct regular training programs to educate employees about the risks of check fraud and how to identify potential threats.
Public Awareness: Individuals should stay informed about common tactics used in check fraud and be cautious about sharing personal information.
4. Use Positive Pay Services:
Banks' Positive Pay Programs: Take advantage of banks' positive pay services that match checks presented for payment with a list of checks issued by the account holder. Any discrepancies trigger alerts.
5. Implement Dual Controls:
Two-Person Authorization: In business settings, consider implementing dual controls for financial transactions, requiring approval from two individuals for check-related activities.
Conclusion
In the relentless battle against check fraud, innovative technological solutions are essential for staying one step ahead of increasingly sophisticated criminals. One such cutting-edge ally in this fight is Tookitaki. This state-of-the-art platform harnesses the power of advanced technologies, including artificial intelligence (AI) and machine learning, to revolutionize check fraud prevention.
Read more about Leveraging Machine Learning for Fraud Detection.
Account Suspension
Introduction
Account suspension is a consequential action taken by service providers, platforms, or institutions to restrict access to an individual's or entity's account due to specific reasons. It serves as a protective measure to maintain security, enforce policies, and mitigate risks.
In this article, we will delve into the definition of account suspension, its impact on users and organizations, and the key reasons behind it. By understanding the concept and implications of account suspension, individuals and businesses can navigate online platforms and services more effectively.
Key Takeaways
- Account suspension is the temporary or permanent restriction of access to an individual's or entity's account.
- It is implemented to enforce policies, maintain security, and mitigate risks.
- Common reasons for account suspension include policy violations, fraudulent activities, abusive behavior, and security breaches.
- Account suspension can have significant consequences, such as loss of access to services, reputational damage, and financial implications.
- Users and organizations can prevent account suspension by adhering to platform guidelines, maintaining security measures, and practicing responsible online behavior.
Understanding Account Suspension
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a particular platform or service. It is a measure taken by service providers or administrators to enforce policies, maintain the integrity of the platform, and protect users. Account suspension is typically initiated in response to violations of terms of service, suspicious or fraudulent activities, abusive behavior, or security breaches. It serves as a means to maintain a safe and trusted environment for all users.
Implications of Account Suspension
Account suspension can have significant implications for individuals and organizations alike. The impact varies depending on the nature of the account and the services provided. Here are some common consequences of account suspension:
- Loss of Access: When an account is suspended, the user loses access to the platform or service associated with the account. This can disrupt communication, impede business operations, or limit the user's ability to connect with others.
- Reputational Damage: Account suspension can result in reputational damage, particularly if the suspension is publicly visible. It may give the impression of misconduct or non-compliance, affecting the user's credibility and trustworthiness.
- Financial Loss: For businesses or individuals who rely on online platforms for revenue generation, account suspension can lead to financial loss. It can disrupt sales, hinder customer relationships, and result in missed opportunities.
- Legal Consequences: In some cases, account suspension may be a result of legal violations or non-compliance with regulations. This can lead to legal consequences, including fines, penalties, or even legal action.
Reasons for Account Suspension
Account suspension can occur due to various reasons, all aimed at upholding the rules and policies of the platform or service provider. Here are some common reasons for account suspension:
- Policy Violations: Account suspension may be enforced when a user violates the terms of service or community guidelines set by the platform. This can include actions such as spamming, engaging in hate speech, or sharing inappropriate content.
- Fraudulent Activities: Accounts involved in fraudulent activities, such as phishing, identity theft, or financial scams, are subject to suspension. Platforms take such actions to protect users from potential harm and maintain trust within their communities.
- Abusive Behavior: Harassment, bullying, or any form of abusive behavior towards other users can lead to account suspension. Platforms prioritize creating safe and inclusive environments, and suspending accounts involved in such behavior is crucial in maintaining the well-being of their user base.
- Security Breaches: If an account is compromised or involved in a security breach, it may be suspended to prevent further unauthorized access or protect the platform's infrastructure. This proactive measure helps safeguard sensitive user data and maintain the overall security of the platform.
- Intellectual Property Infringement: Accounts found to be infringing upon intellectual property rights, such as unauthorized use of copyrighted material or trademark violations, can face suspension. Platforms take these actions to protect the rights of content creators and maintain a fair and legal environment.
- Violation of Financial Regulations: In cases where financial transactions are involved, non-compliance with anti-money laundering (AML) regulations or suspicious financial activities can result in account suspension. This measure is taken to prevent money laundering, terrorist financing, and other illicit financial practices.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
Prevention Methods for Account Suspension
While the risk of account suspension exists, there are proactive steps individuals and organizations can take to minimize the likelihood of such actions. Here are some prevention methods to consider:
- Familiarize Yourself with Platform Guidelines: Before using any platform or service, thoroughly read and understand their terms of service, community guidelines, and policies. Adhere to these guidelines to avoid violations that may lead to account suspension.
- Maintain Account Security: Protect your account by using strong and unique passwords, enabling two-factor authentication (2FA), and regularly updating your login credentials. Be cautious of phishing attempts and avoid sharing sensitive information with unauthorized parties.
- Engage in Responsible Online Behavior: Practice respectful and responsible online conduct. Avoid engaging in abusive or harassing behavior, adhere to copyright laws, and respect the privacy and rights of others.
- Stay Informed about Regulatory Requirements: If you are involved in financial transactions or operate a business that handles sensitive customer information, stay updated on relevant AML and financial regulations. Implement appropriate compliance measures to ensure adherence to these requirements.
- Regularly Monitor and Review Account Activity: Stay vigilant and monitor your account for any suspicious activity or unauthorized access. Report any anomalies to the platform or service provider immediately.
Conclusion
Account suspension is a significant measure implemented by platforms and service providers to maintain security, enforce policies, and protect users. Understanding the implications of account suspension and the common reasons behind it is crucial for individuals and organizations operating in the digital landscape. By adhering to platform guidelines, practicing responsible online behavior, and prioritizing account security, users can mitigate the risk of account suspension and safeguard their online presence.
Frequently Asked Questions
What is account suspension?
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a platform due to policy violations, security breaches, or abusive behavior.
What are the implications of account suspension?
Account suspension can lead to loss of access, reputational damage, financial losses, and potential legal consequences for individuals and businesses.
Why do accounts get suspended?
Accounts can be suspended for reasons such as policy violations, fraudulent activities, abusive behavior, security breaches, intellectual property infringement, and non-compliance with financial regulations.
How can individuals prevent account suspension?
To prevent account suspension, individuals should familiarize themselves with platform guidelines, maintain account security, engage in responsible online behavior, stay informed about regulatory requirements, and regularly monitor account activity.
Why is understanding account suspension important?
Understanding account suspension helps individuals and organizations navigate the digital landscape responsibly, minimize the risk of suspension, and protect their online presence.
Bribery
Introduction
In every corner of the globe, from business boardrooms to public offices, the spectre of bribery looms large. It's a malaise that pervades all sectors, undercutting fair competition, corroding trust, and impeding progress. By shedding light on this issue, we can understand the intricacies of bribery, recognize its many forms, learn from past cases, and contribute to efforts in combating this corrosive practice.
Financial institutions must be vigilant against bribery by implementing strong payment screening and robust identity verification.
Key Takeaways
- Bribery involves the exchange of something of value to influence the actions of those in power, contributing to corruption and distorting systems.
- Bribery can occur in both the public and private sectors, ranging from small-scale transactions to high-level corruption scandals.
- Combating bribery requires a strong legal framework, transparency, accountability, and robust ethics and compliance programs.
- Public sector bribery cases highlight the need for stringent enforcement and the prosecution of high-ranking officials involved in corrupt practices.
- Emphasizing ethics, promoting transparency, and fostering a culture of integrity are essential in preventing bribery and promoting a fair and equitable society.
Bribery: A Basic Definition
Bribery involves the giving, offering, receiving, or soliciting of something of value as a means to influence the actions of an individual or organization in a position of power. This illegal act distorts economic, political, and social systems, and is considered a significant form of corruption.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Working Mechanics of Bribery
Bribery often hinges on a quid pro quo relationship. A bribe-giver provides something of value to a bribe-taker in return for preferential treatment or illicit advantage.
Offering Bribes
This is the act of giving or promising to give something of value with the intention of influencing the behaviour of another party to gain an illicit advantage.
Accepting Bribes
This is the act of receiving or agreeing to receive something of value in exchange for acting or refraining from acting in a certain manner that benefits the bribe-giver.
Different Faces of Bribery
Public Sector Bribery
Public sector bribery involves corrupt transactions between individuals or businesses and public officials. This can range from small-scale 'grease payments' to large-scale bribes involving millions of dollars.
Private Sector Bribery
Private-sector bribery occurs within or between businesses and organizations. This could involve bribing competitors, suppliers, clients, or employees to gain an unfair advantage.
Bribery in the Real World: Notable Instances
Public Sector Cases
Public sector bribery has been witnessed at the highest levels of governance. High-ranking officials across the globe have faced accusations and trials, demonstrating the pervasive nature of this form of corruption.
Here are two recent public sector bribery cases:
- In 2020, Airbus agreed to pay over $3.9 billion in global penalties to resolve foreign bribery and ITAR case. The company admitted to a years-long campaign of corruption around the world, allowing rampant corruption to invade the U.S. system. Airbus falsely reported information about their conduct to the U.S. government for more than five years in order to gain valuable licenses to export U.S. military technology
- In 2021, a former executive of a financial services company, Asante Berko, was charged by the SEC with orchestrating a bribery scheme to help a client win a government contract to build and operate an electrical power plant in the Republic of Ghana. Berko was found guilty of violating anti-bribery, books and records, and international laws. The company agreed to pay more than $81 million to settle the charges
Private Sector Cases
Private sector bribery scandals have rocked large multinational corporations, shedding light on corrupt practices distorting free and fair market competition.
Here are two recent private-sector bribery cases
- In 2019, Walmart Inc. was charged by the SEC with violating the anti-bribery, books and records, and internal accounting provisions of the Foreign Corrupt Practices Act (FCPA). The charges stemmed from Walmart's failure to operate a sufficient anti-corruption compliance program for over a decade as the company expanded internationally. Walmart agreed to pay over $282 million to settle the charges brought by the SEC and the DOJ.
- In 2018, Cognizant, a multinational IT services company, faced charges for authorizing $2.5 million in bribe payments to a government official in India. Two former Cognizant officials, Gordon Coburn and Steven E. Schwartz, were charged in connection with the bribery scheme. The case highlighted the importance of preventing corruption in international business transactions.
Combating Bribery: Strategies for Prevention
Legal Framework
Strong anti-bribery laws and their stringent enforcement are vital in the fight against bribery. These laws should clearly define and criminalize all forms of bribery and provide for substantial penalties.
Transparency and Accountability
Organizations must foster a culture of transparency and accountability. Regular audits and clear reporting systems can help detect and deter bribery.
Ethics and Compliance Programs
Comprehensive ethics and compliance programs play a critical role in preventing bribery. They should provide clear guidelines on acceptable behavior and offer mechanisms for reporting suspected bribery.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Bribery and Money Laundering
Bribery involves the exchange of something of value to influence the actions of individuals or organizations, while money laundering is the process of making illegally obtained money appear legitimate. Both bribery and money laundering are illegal activities that undermine the integrity of economic, political, and social systems. Combating bribery and money laundering requires strong legal frameworks, effective enforcement, transparency, and international cooperation to prevent and punish these illicit practices.
Conclusion
Bribery, a complex and deeply entrenched issue, undermines social trust and economic progress. However, through comprehensive understanding and strategic countermeasures, it's possible to mitigate its effects. Each of us, from individual citizens to organizations and governments, can play a role in fostering a fair, equitable society that stands firm against the blight of bribery.
Suspicious Activity Report
The Suspicious Activity Report (SAR) is a critical tool in combating financial crimes and ensuring the integrity of the financial system. Financial institutions play a crucial role in identifying and reporting suspicious activities that may indicate potential money laundering, fraud, or other illicit activities. Any detected suspicious activity should be promptly reported through a suspicious activity report to combat potential money laundering or fraudster activities.
This article delves into the world of SARs, exploring what constitutes suspicious activity, the triggers for filing SARs, and the process that follows. By shedding light on SARs, we aim to raise awareness about their significance in maintaining financial security.
Key Takeaways
- Suspicious Activity Reports (SARs) are crucial documents filed by financial institutions to report potentially illicit activities.
- Triggers for filing SARs include unusual transactions, patterns, or behaviours that raise suspicions of money laundering, fraud, or terrorist financing.
- The responsibility of filing SARs lies with financial institutions, including banks, credit unions, and other regulated entities.
- SARs are confidential and protected by strict regulations to encourage reporting without fear of repercussions.
- After filing a SAR, law enforcement agencies and regulatory bodies review the report and take appropriate action.
Understanding Suspicious Activity Reports (SARs)
A suspicious activity, in the context of SARs, refers to transactions, patterns, or behaviours that deviate from the norm and raise suspicions of illicit or illegal activities. Some examples of suspicious activities that may trigger a SAR include:
- Unusually large cash deposits or withdrawals
- Frequent transactions just below the reporting threshold to avoid detection
- Structuring transactions to avoid triggering regulatory requirements
- Rapid movement of funds between multiple accounts
- Transactions involving high-risk jurisdictions or individuals associated with criminal activities
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Triggers for Filing a SAR
Financial institutions must file SARs when they detect activities that meet certain criteria indicating possible illicit activities. Some common triggers for filing SARs include:
- Unusual Transactions: Transactions that are significantly larger or more frequent than the customer's normal pattern may trigger a SAR. This could include large cash deposits, wire transfers to high-risk jurisdictions, or transactions inconsistent with the customer's profile.
- Red Flags and Suspicious Patterns: Financial institutions monitor customer accounts for suspicious patterns, such as frequent deposits followed by immediate withdrawals, round-figure transactions, or multiple transactions just below the reporting threshold. These patterns raise concerns and may trigger a SAR.
- Customer Behavior and Profile: Unusual customer behaviour, such as reluctance to provide identification documents, frequent changes in account information, or a sudden increase in account activity, can be indicators of suspicious activity warranting a SAR.
Filing a Suspicious Activity Report (SAR)
Financial institutions, including banks, credit unions, and other regulated entities, are responsible for filing SARs when they have reasonable grounds to suspect illicit activities. The filing process involves the following steps:
- Identification of Suspicious Activity: Financial institutions use sophisticated monitoring systems and compliance programs to identify potentially suspicious activities based on predefined red flags and regulatory requirements.
- Internal Review and Documentation: Once suspicious activity is identified, the institution conducts an internal review to gather additional information and evidence supporting the suspicion. This documentation is crucial for the SAR filing process.
- Preparing the SAR: Preparing the SAR is a crucial step in the process of filing a Suspicious Activity Report. It involves careful documentation and analysis of the suspicious activity detected by financial institutions. By following a systematic approach, institutions can ensure that all necessary information is gathered and reported accurately.
SAR Filing Process
The SAR filing process involves the following steps:
- Completing the SAR Form: Financial institutions use a standardized SAR form provided by regulatory authorities to ensure consistent reporting. The form includes details such as the nature of the suspicious activity, parties involved, transaction amounts, and any supporting documentation.
- Submitting the SAR: Once the SAR form is completed, it is submitted electronically or through other designated channels to the appropriate regulatory authority. The filing must adhere to strict timelines as mandated by regulatory requirements.
- Confidentiality and Compliance: SARs are treated with utmost confidentiality and are protected by privacy laws. Financial institutions are prohibited from disclosing the filing of a SAR to the customer or any other party. This confidentiality encourages reporting without fear of reprisal.
Consequences and Impact of SARs
Once a SAR is filed, it undergoes review and analysis by law enforcement agencies and regulatory bodies. The purpose is to determine the severity of the reported activity and initiate appropriate actions. Possible outcomes include:
- Investigation: SARs provide crucial information to law enforcement agencies, aiding them in initiating investigations into suspected financial crimes. These investigations may uncover broader networks and lead to the prevention or prosecution of illicit activities.
- Enhanced Monitoring: SARs contribute to the development of risk profiles and intelligence databases, enabling financial institutions and regulatory bodies to improve their monitoring systems and enhance their ability to detect and prevent future suspicious activities.
{{cta('31af77a9-1ccc-4abd-a9f1-28412872c7a2','justifycenter')}}
Financial Institution Obligations
Financial institutions have legal obligations and face potential consequences related to SARs:
- Compliance with Regulatory Requirements: Financial institutions must comply with the reporting obligations outlined by regulatory authorities. Failure to do so can result in penalties, fines, reputational damage, and even the loss of regulatory licenses.
- Risk Mitigation and Reputation: Effectively filing SARs demonstrates a commitment to combating financial crime and protecting the financial system's integrity. It helps safeguard the institution's reputation and build trust with customers, regulators, and the wider community.
Conclusion
Suspicious Activity Reports (SARs) play a crucial role in maintaining the integrity and security of the financial system. They serve as a mechanism for detecting and reporting potentially illicit activities, such as money laundering, fraud, and terrorist financing. Financial institutions are responsible for identifying and reporting suspicious activities, and SARs provide law enforcement agencies and regulatory bodies with valuable information for investigations and preventive measures.
By understanding the triggers for SARs, the filing process, and the consequences that follow, individuals and institutions can actively contribute to combating financial crimes and ensuring the stability of the financial landscape.
Operational Risk
Operational risk refers to the potential for losses arising from inadequate or failed internal processes, people, systems, or external events. It is a crucial aspect of risk management for banks and organizations. Effectively managing operational risk includes guarding against threats like data loss, wire fraud, and phishing.
In this article, we will explore the different types of operational risk, the significance of managing operational risk, and effective risk management strategies. Real-life examples of operational risk will illustrate its impact, and we will discuss the benefits of implementing sound risk management practices.
Key Takeaways
- Operational risk involves the potential for losses arising from internal processes, people, systems, or external events.
- Managing operational risk is crucial for organizations to mitigate financial losses, protect reputation, and ensure regulatory compliance.
- Operational risk in banks encompasses various risks specific to banking activities.
- The three pillars of operational risk management include risk identification and assessment, risk mitigation and control, and monitoring and reporting.
- Effective operational risk management involves proactive measures to identify, assess, mitigate, and monitor operational risks.
- Real-life examples highlight the impact of operational risk, such as data breaches, employee misconduct, system failures, and fraud.
- Benefits of effective operational risk management include reduced financial losses, enhanced efficiency, regulatory compliance, and a risk-aware culture.
Understanding Operational Risk
Operational risk is a critical aspect of banking that goes beyond credit and market risks. It refers to the probability of incurring financial losses due to internal or external factors affecting a bank's processes, systems, or people. This broad spectrum of risks can arise from a range of sources, such as inadequate internal controls, human error, technological breakdowns, legal and regulatory breaches, or unexpected events, among others. The challenge for banks is to manage operational risks proactively by identifying, assessing, mitigating, and monitoring them effectively. By doing so, banks can mitigate the negative impacts of operational risks and protect their reputation, customers, and shareholders.
A comprehensive operational risk management framework comprises three pillars: risk identification and assessment, risk mitigation and control, and monitoring and reporting. By implementing these pillars, banks can enhance their operational resilience, achieve better regulatory compliance, and foster a risk-aware culture that promotes accountability and transparency. Ultimately, effective operational risk management can help banks navigate the uncertain and complex environment they operate in and improve their overall performance and competitiveness.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Importance of Operational Risk
Operational risk is a multifaceted challenge that can have significant implications for organizations. Effective management of operational risk is crucial to mitigate the potential financial losses, reputational damage, and disruptions that can result from internal and external factors. It is also essential to maintain regulatory compliance and promote stability, resilience, and sustainable growth.
Organizations that prioritize operational risk management can implement proactive measures to identify, assess, mitigate, and monitor risks effectively. This approach can help them stay ahead of potential threats and respond quickly and efficiently to any incidents that may occur. It can also create a culture of risk awareness and promote accountability and transparency, which can enhance overall performance and competitiveness.
By managing operational risk, organizations can protect their customers, shareholders, and stakeholders while maintaining a strong reputation in the marketplace. They can also achieve better regulatory compliance and ensure that their operations remain stable and resilient in the face of unexpected events. Ultimately, effective operational risk management is crucial for organizations to thrive and achieve long-term success.
Types of Operational Risk
- Internal Fraud: Risks arising from fraudulent activities conducted by employees, such as embezzlement, theft, or unauthorized trading.
- External Fraud: Risks associated with fraudulent activities committed by external parties, including cyberattacks, identity theft, or counterfeiting.
- Employment Practices and Workplace Safety: Risks related to employment-related issues, such as discrimination, workplace accidents, or violations of labour laws.
- System and Process Failures: Risks stemming from failures or deficiencies in an organization's systems, processes, or technology infrastructure, leading to errors, disruptions, or data breaches.
Operational Risk in Banks
Operational risk in banks is a complex challenge that requires a multifaceted approach to risk management. Banks operate in a highly regulated and competitive environment, where any disruption or financial loss can have significant implications. Banks need to manage operational risks proactively by identifying, assessing, mitigating, and monitoring them effectively. This approach involves various risks specific to banking activities, such as credit risk, market risk, liquidity risk, legal and regulatory risk, and reputational risk.
Banks' complex operations, extensive customer interactions, and reliance on sophisticated systems create a wide range of risks that must be managed effectively. Therefore, banks need to have a robust operational risk management framework that incorporates the three pillars of risk identification and assessment, risk mitigation and control, and monitoring and reporting. By implementing these pillars, banks can enhance their operational resilience, achieve better regulatory compliance, and foster a risk-aware culture that promotes accountability and transparency.
Ultimately, effective operational risk management can help banks navigate the uncertain and complex environment they operate and improve their overall performance and competitiveness.
The Three Pillars of Operational Risk
Operational risk management is a complex and multifaceted process that requires a comprehensive framework to be effective. The three pillars of operational risk management, as outlined by the Basel Committee on Banking Supervision, provide a solid foundation for such a framework.
- The first pillar, risk identification and assessment, involves identifying potential operational risks and assessing their likelihood and potential impact. This step is crucial in developing an effective risk management strategy.
- The second pillar, risk mitigation and control, involves implementing measures to reduce the likelihood or impact of identified risks. This could include implementing internal controls, improving processes, or investing in new technology.
- The third pillar, monitoring and reporting, involves ongoing monitoring of risks and reporting of risk-related information to stakeholders. This step is essential in maintaining a proactive approach to risk management and ensuring that the organization is aware of any emerging risks.
Together, these three pillars provide a robust framework for effective operational risk management and can help organizations mitigate financial losses, protect reputation, and ensure regulatory compliance.
Operational Risk Management
To achieve effective operational risk management, organizations must take proactive measures to identify, assess, mitigate, and monitor operational risks. This requires the implementation of comprehensive risk management policies, conducting regular risk assessments to identify potential threats, establishing internal controls to mitigate risks, and fostering a risk-aware culture throughout the organization.
- Implementing risk management policies involves developing clear and concise guidelines that outline the organization's approach to operational risk management.
- Conducting regular risk assessments is crucial to identify potential operational risks and assess their likelihood and potential impact. This process involves reviewing all aspects of the organization's operations, including processes, procedures, systems, and personnel, to identify any potential risks.
- Establishing internal controls is one of the most critical components of operational risk management. These controls are designed to mitigate risks by reducing the likelihood or impact of identified risks.
- Fostering a risk-aware culture throughout the organization is also essential to effective operational risk management. This involves promoting a culture of risk awareness, where all employees are aware of the potential risks associated with their roles and responsibilities.
By implementing these proactive measures, organizations can effectively manage operational risk, reduce financial losses, enhance efficiency, ensure regulatory compliance, and foster a risk-aware culture that promotes accountability and transparency.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Benefits of Effective Operational Risk Management
Effective operational risk management is crucial for organizations to mitigate potential financial losses and ensure business continuity. By implementing robust operational risk management practices, organizations can reduce financial losses, enhance operational efficiency, maintain regulatory compliance, safeguard reputation, and foster a culture of risk awareness and accountability.
Reducing financial losses is one of the most significant benefits of effective operational risk management. Organizations can identify and mitigate potential risks before they turn into actual losses, thereby preserving financial resources. This, in turn, can enhance operational efficiency and enable organizations to invest in growth opportunities.
Maintaining regulatory compliance is another critical benefit of operational risk management. Organizations that comply with regulatory requirements can avoid fines and sanctions, protect their reputation, and maintain customer trust.
Safeguarding reputation is also crucial in today's highly competitive business environment. A single operational risk incident can damage an organization's reputation and erode customer trust, which can have long-term consequences. Effective operational risk management can help organizations minimize reputational damage and promote a positive image in the marketplace.
Finally, fostering a culture of risk awareness and accountability is essential to effective operational risk management. When all employees are aware of potential risks and their roles and responsibilities in mitigating them, organizations can create a risk-aware culture that promotes accountability and transparency. This, in turn, can enhance overall performance and competitiveness and help organizations achieve long-term success.
Conclusion
Operational risk poses significant challenges to banks and organizations. By understanding the different types of operational risk, recognizing its importance, and implementing robust risk management strategies, businesses can protect themselves from financial losses, reputational damage, and operational disruptions. The proactive identification, assessment, mitigation, and monitoring of operational risks enable organizations to enhance resilience, maintain regulatory compliance, and foster sustainable growth in an increasingly complex and interconnected business environment.
DNFBP
In the intricate world of financial transactions and regulatory compliance, the term DNFBP, or Designated Non-Financial Businesses and Professions, often surfaces, intertwining various sectors in the fight against money laundering and terrorist financing. While financial institutions have been the primary focus in combating these illicit financial activities, DNFBPs have emerged as crucial players, bridging gaps and strengthening the financial system against exploitation.
In this article, we aim to demystify DNFBP by exploring its meaning, categories, challenges, and the stringent FATF requirements that govern its operations. By doing so, we highlight its significance in Anti-Money Laundering (AML) and Counter-Financing of Terrorism (CFT).
Key Takeaways
- DNFBPs serve as crucial gatekeepers in the financial ecosystem, scrutinizing high-value transactions to identify and report suspicious activities related to money laundering and terrorist financing.
- The challenges faced by DNFBPs include managing compliance with varied AML and CFT regulations, implementing effective customer due diligence, maintaining transaction records, fulfilling reporting obligations, and ensuring continuous training and awareness among staff.
- FATF requirements for DNFBPs emphasize conducting thorough risk assessments, applying consistent customer due diligence measures, maintaining transaction and customer records, reporting suspicious transactions promptly, and establishing robust internal controls and policies.
- DNFBPs play a vital role in the fight against money laundering (AML) and terrorist financing (CFT) by adhering to regulations, managing risks, ensuring compliance, safeguarding their reputation, and strengthening global financial security.
- Ensuring adherence to AML and CFT regulations not only safeguards DNFBPs from potential legal and reputational risks but also fortifies the global financial system against the threats of illicit financial activities.
Definition of DNFBP
DNFBP stands for Designated Non-Financial Businesses and Professions, which refers to specific sectors and professions that, while not financial institutions, are recognized for being susceptible to being exploited for money laundering and terrorist financing purposes. The DNFBPs are not primarily engaged in financial activities but deal with money and assets that could potentially be used to launder money or finance terrorism.
They play a crucial role in identifying, assessing, and mitigating the risks associated with these illicit financial activities, ensuring that the economic channels they influence remain secure and compliant with global regulatory standards.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Categories of DNFBPs
DNFBPs encompass a diverse range of sectors and professions, each with its unique characteristics and potential vulnerabilities to illicit financial activities. The Financial Action Task Force (FATF), an intergovernmental body that sets international standards for combating money laundering and terrorist financing, identifies several categories of DNFBPs, which include:
- Casinos: Entities that engage in gaming and gambling activities, which involve significant cash transactions.
- Real Estate Agents: Professionals who deal with buying and selling of properties, often involving substantial amounts of money.
- Dealers in Precious Metals and Stones: Businesses that trade in high-value goods, which can be used to convert illicit cash into valuable assets.
- Lawyers, Notaries, and Other Independent Legal Professionals: Individuals who assist in buying and selling of property, managing client money, securities, and other assets, and other activities that may involve substantial value.
- Accountants: Professionals who manage financial records and transactions, which can potentially be manipulated for money laundering.
- Trust and Company Service Providers: Entities that provide services related to the creation and management of companies and trusts.
Each category, while diverse, plays a pivotal role in safeguarding the financial system by adhering to AML and CFT regulations and ensuring that their operations are not misused for illicit financial purposes.
Challenges Faced by DNFBPs
Designated Non-Financial Businesses and Professions (DNFBPs) often find themselves navigating through a tricky path filled with various challenges, especially when it comes to managing financial rules and staying compliant. Let’s break down some of the main hurdles they face:
- Managing Compliance: DNFBPs have to make sure they’re following a lot of different rules, both from their local area and international ones, related to Anti-Money Laundering (AML) and Countering Financing of Terrorism (CFT). These rules can be different in various places, making it quite a task to stay on top of them all.
- Customer Checks: They need to have strong processes in place to thoroughly check their customers' identities and understand the risks involved in dealing with them. This process, known as Customer Due Diligence (CDD), is crucial to avoid being unknowingly used for illegal financial activities.
- Keeping Records: DNFBPs must keep detailed and accurate records of all transactions and customer information. Not only does this information need to be precise, but it also needs to be stored in a way that follows data protection laws and can be easily accessed when needed.
- Reporting Properly: If they notice any suspicious transactions, DNFBPs need to report them to the right authorities promptly and accurately. This requires a well-organized reporting process and a sharp eye to spot any unusual activities.
- Training and Keeping Everyone Informed: It’s vital for DNFBPs to ensure that their team members and other involved parties are always up-to-date with the latest in regulatory changes and are skilled at spotting potential risks related to AML and CFT.
Addressing these challenges means that DNFBPs need to create and uphold a strong program that ensures they comply with all the necessary regulations, which is shaped according to their specific operations and the regulatory rules they need to follow. This isn’t a one-size-fits-all solution but needs to be customized to their particular situation and the regulations they are subject to.
FATF Requirements for DNFBPs
The Financial Action Task Force (FATF), which plays a crucial role in setting global standards for preventing illegal financial activities, has set some strict rules for Designated Non-Financial Businesses and Professions (DNFBPs) to follow. These rules are meant to strengthen their ability to prevent money laundering and terrorist financing. Let’s simplify these requirements:
- Assessing Risks: DNFBPs need to thoroughly check and understand the risks of money laundering and terrorist financing that are related to their operations and take steps to manage these risks.
- Checking Customers: DNFBPs must have processes in place to consistently check and verify their customers' details, especially those who might pose a higher risk, to prevent illegal activities.
- Keeping Records: They need to keep detailed records of all transactions and customer data for at least five years. This helps in investigations and ensures they are following all the necessary rules.
- Reporting Suspicious Activity: If DNFBPs notice any transactions or activities that seem suspicious, they need to report them to the relevant authorities as quickly as possible.
- Managing Risks Internally: DNFBPs should have their own internal rules and controls to effectively manage and minimize the identified risks. This includes having a specific officer in charge of ensuring they comply with Anti-Money Laundering (AML) rules and regularly checking their processes through audits.
By following these FATF requirements, DNFBPs not only make sure they are complying with the rules but also protect their operations from being misused by criminals for illegal financial activities.
Significance of DNFBPs in AML and CFT
Designated Non-Financial Businesses and Professions (DNFBPs) play a crucial role in preventing illegal financial activities like money laundering and terrorist financing (AML and CFT). Let's break down their importance in simpler terms:
- Checking Transactions: DNFBPs often handle transactions that involve large amounts of money, making them an important line of defense in spotting and reporting any suspicious activities.
- Reducing Risks: By following AML and CFT rules, DNFBPs help reduce the risks related to money laundering and terrorist financing, which protects not only their own operations but also the wider financial system.
- Following the Law: DNFBPs help maintain the integrity of the legal system by ensuring that all the transactions they handle follow the relevant laws and regulations.
- Safeguarding Their Reputation: By making sure they comply with AML and CFT rules, DNFBPs protect themselves from the potential damage to their reputation that could come from unintentionally being involved in illegal financial activities.
- Supporting Global Financial Stability: DNFBPs help keep the global financial system stable and secure by reducing the risks of money laundering and terrorist financing.
In essence, DNFBPs act as guardians within the financial ecosystem, ensuring transactions are legitimate, reducing risks of illegal activities, and thereby, contributing to the stability of global finance.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Conclusion
Navigating through the intricate realms of Anti-Money Laundering (AML) and Countering Financing of Terrorism (CFT), Designated Non-Financial Businesses and Professions (DNFBPs) stand as pivotal sentinels, safeguarding the financial ecosystem from the perils of illicit financial activities. The DNFBP meaning extends beyond its mere definition, embedding itself deeply into the realms of financial security, legal compliance, and operational integrity. While DNFBPs operate across varied sectors, their unified objective remains steadfast: to shield their operations and the broader financial system from being manipulated for money laundering and terrorist financing.
The challenges that DNFBPs encounter are multifaceted, intertwining regulatory, operational, and technological aspects. From ensuring stringent customer due diligence to navigating through a complex web of international and local regulations, DNFBPs must continuously evolve and adapt their strategies to effectively mitigate emerging risks. The FATF, through its meticulous requirements, provides a structured pathway for DNFBPs to fortify their AML and CFT defences, ensuring that they not only comply with regulatory mandates but also contribute significantly to global financial security.
In a world where financial transactions are becoming increasingly sophisticated and covert, DNFBPs, through their rigorous AML and CFT practices, act as robust barriers, disrupting illicit financial flows and safeguarding the integrity of the financial system. Their role transcends beyond mere compliance, emerging as crucial entities that uphold financial transparency, security, and integrity on a global scale.
Money Laundering
The term 'money laundering' is often shrouded in layers of intrigue and controversy, a covert activity known for its illegal nature and association with criminal enterprises. It essentially represents the nefarious process through which 'dirty' money, or funds accrued from illicit activities, is made to appear as though it were obtained legally. The act of money laundering has far-reaching consequences, serving as a critical enabler of crime and corruption on a global scale.
In order to thoroughly comprehend the ins and outs of money laundering, it is essential to break down the concept into simpler terms and explore its various facets. At its most fundamental level, money laundering involves taking money that has been earned from criminal activities and passing it through a sequence of transactions to obscure its original source. This gives the funds an appearance of legitimacy, thus 'laundering' the ill-gotten gains. Preventing money laundering necessitates a comprehensive approach involving payment screening, enhanced due diligence, and suspicious activity reporting.
{% module_block module "widget_2c7fd7fd-91d4-4048-9fd3-75ce1bb33842" %}{% module_attribute "child_css" is_json="true" %}{% raw %}{}{% endraw %}{% end_module_attribute %}{% module_attribute "css" is_json="true" %}{% raw %}{}{% endraw %}{% end_module_attribute %}{% module_attribute "definition_id" is_json="true" %}{% raw %}null{% endraw %}{% end_module_attribute %}{% module_attribute "description" is_json="true" %}{% raw %}"Money laundering is the process of disguising the origin of illegally obtained money by passing it through a sequence of transactions to make it appear as if it comes from a legitimate source. It involves taking \"dirty\" money and making it look \"clean.\""{% endraw %}{% end_module_attribute %}{% module_attribute "duration" is_json="true" %}{% raw %}{"seconds":0}{% endraw %}{% end_module_attribute %}{% module_attribute "field_types" is_json="true" %}{% raw %}{"choose_video_type":"choice","datetime_field":"datetime","description":"richtext","duration":"group","embed_url":"url","thumbnail":"image","title":"text","youtube_id":"text"}{% endraw %}{% end_module_attribute %}{% module_attribute "label" is_json="true" %}{% raw %}null{% endraw %}{% end_module_attribute %}{% module_attribute "module_id" is_json="true" %}{% raw %}154691535373{% endraw %}{% end_module_attribute %}{% module_attribute "path" is_json="true" %}{% raw %}"@marketplace/Bootstrap_Creative/Video_Object_Schema"{% endraw %}{% end_module_attribute %}{% module_attribute "schema_version" is_json="true" %}{% raw %}2{% endraw %}{% end_module_attribute %}{% module_attribute "smart_objects" is_json="true" %}{% raw %}[]{% endraw %}{% end_module_attribute %}{% module_attribute "smart_type" is_json="true" %}{% raw %}"NOT_SMART"{% endraw %}{% end_module_attribute %}{% module_attribute "tag" is_json="true" %}{% raw %}"module"{% endraw %}{% end_module_attribute %}{% module_attribute "title" is_json="true" %}{% raw %}"What is Money Laundering?"{% endraw %}{% end_module_attribute %}{% module_attribute "type" is_json="true" %}{% raw %}"module"{% endraw %}{% end_module_attribute %}{% module_attribute "wrap_field_tag" is_json="true" %}{% raw %}"div"{% endraw %}{% end_module_attribute %}{% module_attribute "youtube_id" is_json="true" %}{% raw %}"y9yx02XuoiE"{% endraw %}{% end_module_attribute %}{% end_module_block %}
Key Takeaways
- Money laundering is the process of disguising the origin of illegally obtained money by passing it through a sequence of transactions to make it appear as if it comes from a legitimate source. It involves taking "dirty" money and making it look "clean."
- The term "money laundering" originated from old gangster practices where criminals, who often owned cash-only businesses like laundromats, would mix the earnings from their illegal activities with their legitimate business earnings, using the cash-heavy nature of such businesses to hide the illicit funds.
- Factors that contribute to money laundering include the desire to profit from criminal activities, gaps in governance due to corrupt or weak institutional frameworks, and advancements in financial technologies and systems that allow swift and sometimes nearly undetectable cross-border transactions.
- AML refers to the laws, regulations, and procedures designed to prevent money laundering.
Origin of the term ‘Money Laundering’
Ever wondered where this term came from? Well, let's travel back in time. Imagine those old gangster movies where criminals ran illegal businesses. In the past, many criminals owned cash-only businesses like laundromats. They would mix the money they earned from illegal activities, such as smuggling or selling illegal items, with the earnings of their legal business.
Laundromats were used because they had lots of cash transactions, making it easier to blend in the illegal money. Hence, the term "money laundering" was born! Today, the methods have changed and become more complicated, but the goal remains the same: making illegal money look legal.
Understanding Money Laundering
Money laundering is a term that is often associated with illegal activities and financial crimes. But what does it actually mean?
Illegal Origins of Funds
Money laundering is the process of concealing the origins of illegally obtained money, typically by means of transfers involving foreign banks or legitimate businesses. This allows the funds to appear as if they have been obtained through legal means.
Money laundering can involve a variety of illegal activities, including drug trafficking, corruption, fraud, and tax evasion.
Methods of Money Laundering
There are several common methods used to launder money, including:
- Placement: This involves placing the illegal funds into the financial system, often through small deposits or purchases of monetary instruments.
- Layering: This step involves moving the funds through a series of complex financial transactions to obscure the paper trail.
- Integration: The final step involves reintroducing the funds into the economy as seemingly legitimate money, often through investments or purchases of high-value assets.
These methods are used to make it difficult for authorities to trace the original source of the funds, allowing criminals to enjoy the proceeds of their illegal activities without detection.
Read More: What is Money Laundering
Read More: Money Laundering Techniques
Causes of Money Laundering
A multitude of factors intersect to propagate the complex crime of money laundering. Prominent among these is the primal desire to profit from criminal activities. Individuals and organized crime groups who engage in illegal activities, such as drug trafficking or fraud, are driven by the prospect of substantial financial gain.
However, these ill-gotten wealth often attract the attention of law enforcement, making it imperative for criminals to mask the true source of these funds. This necessitates the process of money laundering, which provides the required veneer of legitimacy to the proceeds of crime, enabling criminals to enjoy their profits without raising alarms.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Another pivotal factor is the presence of corrupt or weak institutional frameworks. When regulatory bodies and law enforcement agencies lack the resources or the will to monitor and control financial transactions effectively, it creates fertile ground for money laundering to thrive. These gaps in governance allow illicit funds to seep unnoticed into the economy, thereby facilitating the perpetrators to continue their unlawful activities unhindered.
Finally, the relentless advancement and increasing sophistication of financial technologies and systems significantly influence the prevalence of money laundering. In today's globalized world, money can move across borders swiftly and, at times, almost undetectably.
Innovative financial instruments and digital technologies, while bringing efficiency and speed to legitimate transactions, also present novel opportunities for criminals to obscure the origins of their illicit funds. With every new technological breakthrough, money launderers find novel ways to exploit these advancements, adding further complexity to the already intricate landscape of this financial crime.
Examples of Money Laundering
Money laundering might sound like something out of a movie, but it happens in real life too. Here are some simple examples of money laundering:
1. Smurfing (Structuring)
Smurfing, also known as structuring, involves breaking down a large sum of money into smaller, less suspicious amounts and depositing them into various bank accounts over several transactions.
Example: A criminal organization has $1 million in illicit funds. To avoid detection, members deposit amounts less than $10,000 (to stay under the reporting threshold) into multiple bank accounts at different branches over several days. This makes it harder for authorities to trace the origin of the funds.
2. Trade-Based Money Laundering
Trade-based money laundering involves manipulating the value of goods and services in international trade to launder money. It can include over-invoicing, under-invoicing, or multiple invoicing of goods and services.
Example: A company in Country A sells a shipment of electronics to a company in Country B. The invoice for the shipment is deliberately overvalued. The company in Country B pays the inflated price, and the excess amount is then funneled back to the criminal organization in Country A, disguised as legitimate trade revenue.
3. Casino Money Laundering
Casinos can be used to launder money by converting illicit cash into casino chips, gambling minimally, and then cashing out the chips for a check or bank transfer.
Example: A criminal enters a casino with $500,000 in cash. They buy chips and play for a short time, ensuring they do not lose a significant amount. They then cash out the remaining chips and request a casino check. The money now appears as gambling winnings, making it harder to trace its illicit origins.
4. Real Estate Laundering
Criminals purchase real estate properties to launder money. The property can be bought with illicit funds, rented out to generate "clean" rental income, or sold to integrate the money back into the financial system.
Example: A drug trafficker buys a luxury apartment for $2 million in cash. Over time, they rent out the apartment and receive monthly rental payments. These rental incomes are reported as legitimate, and when the property is sold at a later date, the proceeds appear clean.
5. Shell Companies and Offshore Accounts
Shell companies are entities that exist only on paper and have no physical operations. They can be used to move money across borders and hide the true ownership of funds. Offshore accounts in jurisdictions with strict privacy laws also help in concealing the source of money.
Example: A corrupt politician creates a shell company in an offshore tax haven. They transfer $5 million in bribes to this company, then use the company's offshore account to purchase luxury goods or transfer funds to other accounts worldwide. This complex web of transactions makes it difficult to trace the money back to the politician.
What is Anti Money Laundering?
We've talked about money laundering, but there's also something called "Anti Money Laundering" or AML. AML is like the superhero trying to stop the villains from laundering their money. It involves a set of laws, regulations, and procedures aimed at stopping criminals from disguising illegally obtained funds as legal. For instance, banks might ask customers for more details when they try to deposit a large sum of money. This is a part of AML efforts to ensure that the source of the money is legit.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Tookitaki’s Anti-Money Laundering Suite
Every superhero needs their toolkit, and in the world of AML, Tookitaki offers just that! Tookitaki's Anti-Money Laundering Suite is like a detective that uses smart technology to spot suspicious activities. With its advanced systems, it can quickly verify customer identities and identify unusual behaviours and transactions that might indicate money laundering. This makes it easier for banks and other financial institutions to catch the bad guys in action and ensure that money laundering is curbed.
By understanding the definition of money laundering and how it works, we can better appreciate the efforts taken to stop it. It's crucial for the health of any economy to prevent illegal money from flowing into the system, and with advanced tools like Tookitaki, the fight against money laundering is getting stronger!
Embezzlement
Embezzlement is a serious financial crime that can devastate businesses and erode trust. It involves someone trusted with assets stealing them for personal gain. This blog will explain what embezzlement is, how it differs from similar crimes, and provide real-world examples. We'll also discuss how to prevent it in organizations and the role of technology in safeguarding assets.
Key Takeaways
- Embezzlement involves the misappropriation of assets entrusted to an individual or party, typically in a fiduciary role.
- It is considered a significant crime and often carries severe penalties, including substantial fines and imprisonment.
- The definition and understanding of embezzlement vary within the legal and accounting fields but ultimately converge on the aspects of trust, misappropriation, and fraudulent intent.
- Familiarity with the concept of embezzlement and its legal implications is crucial for both individuals and businesses to safeguard their financial interests.
What is Embezzlement?
Embezzlement Meaning and Legal Definition
Embezzlement is the act of stealing or misappropriating funds or property entrusted to someone's care, usually in a work or official capacity. Legally, it involves the fraudulent taking of personal property by someone to whom it was entrusted, such as an employee or public official. This crime is distinct from theft because the perpetrator initially has legal access to the property.
Types of Embezzlement
Embezzlement can take many forms, including:
- Skimming: Taking small amounts of money over time.
- Payroll Fraud: Creating fake employees or inflating hours worked.
- Vendor Fraud: Overcharging for goods or services or creating fake vendor accounts.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Embezzlement Meaning in Accounting
In accounting, the term 'embezzlement' is used to describe a specific category of financial fraud. It is a deceptive act typically carried out by an employee, usually someone holding a financial role or position within a company, who manipulates their position of trust to misappropriate company assets for personal gain.
This act of deceit often involves the deliberate manipulation of financial records or documents to disguise the theft of assets. It could range from creating fraudulent invoices that don't represent actual goods or services provided to doctoring expense reports to cover up the siphoning off of company funds. These actions are usually calculated and performed in such a way that makes detection difficult, hence allowing the perpetrator to avoid immediate suspicion and continue the fraudulent activities for an extended period.
Examples of Embezzlement
To gain a more in-depth understanding of the concept of embezzlement, it can be highly beneficial to take a closer look at real-world instances where this white-collar crime has been committed. Studying these cases can not only provide insights into the methods employed by the offenders but also shed light on the devastating impacts such actions can have.
The case of Bernie Madoff, infamous for orchestrating one of the largest and most impactful Ponzi schemes in history, is an especially telling example. His fraudulent activities caused billions of dollars in losses and sent shockwaves through the financial world. His actions brought his firm to its knees and had far-reaching effects on countless investors who placed their trust in him.
Similarly, the case of Richard Dausey, who was involved in the misappropriation of funds at Adelphia Communications, offers another glimpse into how embezzlement can occur. Dausey, in his role at Adelphia, was entrusted with the company's assets, yet he chose to misuse his position for personal gain. His actions had significant implications for the company, its employees, and shareholders, leading to substantial financial losses and a crisis of trust.
These cases, and others like them, are stark reminders of the potential magnitude of embezzlement. They showcase how such deceitful actions can wreak havoc on organizations, leaving in their wake a trail of financial devastation and a breakdown of trust that can take years, if not decades, to repair.
Embezzlement vs. Misappropriation of Funds
Key Differences Between Embezzlement and Misappropriation
While embezzlement and misappropriation both involve the misuse of funds, they are distinct crimes. Embezzlement specifically refers to the theft of assets by someone who has legal access to them. Misappropriation, on the other hand, is a broader term that includes any unauthorized use of funds or property, regardless of the perpetrator's initial access rights.
Common Scenarios and Examples
- Embezzlement Example: An employee diverts company funds into a personal account over time.
- Misappropriation Example: A manager uses company money to fund a personal project without authorization.
Is Embezzlement a Felony?
Indeed, the act of embezzlement is classified as a severe criminal offence, a felony in fact, in numerous legal jurisdictions across the globe. This categorisation stems from its inherent nature as a major financial crime involving the misappropriation of assets by individuals entrusted with their care.
The weight of the penalty that follows being convicted of embezzlement is typically commensurate with the scale or magnitude of the embezzled assets. In other words, the larger the value of the assets misappropriated, the stiffer the punishment will likely be. This could range from imposing substantial monetary fines that aim to deter such illicit activity to meting out long-term prison sentences that underscore the seriousness of the crime.
Read more on the differences between embezzlement and money laundering.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
How Embezzlement Occurs
Methods and Techniques Used in Embezzlement
Embezzlers use various techniques to steal funds or assets. Some common methods include:
- Skimming: Taking cash before it is recorded in the books.
- Check Tampering: Altering or forging checks to withdraw funds.
- Billing Schemes: Creating fake invoices or inflating expenses.
- Payroll Fraud: Adding ghost employees or inflating hours worked.
Case Studies and Real-world Examples
- A Trusted Employee: An accountant diverts client funds into personal accounts over several years, unnoticed until a routine audit.
- Nonprofit Organization: A treasurer of a nonprofit siphons donation funds for personal use, discovered only after a donor questions financial discrepancies.
Legal Consequences of Embezzlement
Penalties and Sentencing
The penalties for embezzlement can be severe, including fines, restitution, and imprisonment. The severity of the punishment often depends on the amount embezzled and the jurisdiction. In some cases, the convicted individual may also face civil penalties, such as forfeiture of assets and damages.
Preventing Embezzlement in Organizations
Best Practices for Businesses
To prevent embezzlement, businesses should implement strong internal controls, including:
- Segregation of Duties: Ensure that no single employee has control over all aspects of a financial transaction.
- Regular Audits: Conduct both scheduled and surprise audits to detect discrepancies early.
- Employee Background Checks: Perform thorough background checks during hiring to identify potential risks.
Implementing Strong Internal Controls
Strong internal controls are crucial in preventing embezzlement. These include:
- Access Controls: Limit access to financial systems to authorized personnel only.
- Transaction Reviews: Regularly review financial transactions and statements for irregularities.
- Whistleblower Policies: Establish a system for employees to report suspicious activities anonymously.
Role of Technology in Prevention
Advanced technologies such as artificial intelligence and machine learning can help detect unusual patterns and anomalies in financial transactions. Automated systems can flag suspicious activities in real time, reducing the risk of human error and enhancing overall security.
To protect your organization from financial crimes like embezzlement, consider Tookitaki's comprehensive anti-financial crime solutions. Talk to our experts and explore our FinCense platform to enhance your defences.
Ultimate Beneficial Owner
In the context of investments, assets, or properties, a beneficial owner is the individual or entity that enjoys the perks of ownership without necessarily being the registered owner. This means that while legal documents might display one name, the actual control, benefits, and risks associated with the asset lie with another party - the beneficial owner. Think of it as a hidden force behind the scenes, orchestrating financial moves and wielding influence, even though their name might not be on the paperwork.
Meaning of UBO
UBO or Ultimate Beneficial Owner (UBO) refers to the individual or entity that holds the true decision-making power and enjoys the financial benefits of an asset, investment, or property, despite not being the registered owner. This concept is crucial in today's intricate financial landscape, where ownership is often separated from control and economic interests.
Understanding Ultimate Beneficial Owner
Consider a scenario where a wealthy entrepreneur invests in a diverse portfolio of stocks. The shares might be held in the name of a company or trust, but the entrepreneur, who strategically maneuvers these investments, making crucial decisions and reaping profits, is the true beneficial owner. This intricate web of ownership is a common occurrence in today's complex financial landscape, where ownership is often separated from control and economic interests.
Read More: 3 Recent Developments on Ultimate Beneficial Ownership (UBO)
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Some Other Beneficial Owner Examples
Example 1: Real Estate Investments
Imagine a wealthy individual, Mr. A, who wants to invest in real estate properties without revealing his identity publicly. To maintain confidentiality, he establishes a shell company (a legal entity often used for anonymity) called ABC Real Estate Holdings LLC. On paper, the company is the legal owner of the properties, holding the titles and handling transactions. However, Mr. A is the beneficial owner. He decides which properties to buy or sell, collects rental income, and benefits from the properties' appreciation over time. This arrangement allows Mr. A to keep his real estate investments private while legally complying with ownership regulations.
Example 2: Offshore Investments and Tax Planning
A multinational corporation, XYZ Inc., operates in several countries, each with its own tax regulations. To optimize its tax liabilities legally, XYZ Inc. establishes subsidiaries in low-tax jurisdictions. These subsidiaries hold the legal ownership of various assets, such as patents, trademarks, or intellectual properties, on behalf of XYZ Inc. The subsidiaries are the legal owners, fulfilling legal requirements in those jurisdictions. However, XYZ Inc. is the beneficial owner, enjoying the profits generated from these assets. This structure enables the corporation to strategically manage its tax obligations and protect its intellectual properties while staying within the bounds of the law.
In both examples, the legal owners are entities (a company or a legal entity), while the beneficial owners are individuals (Mr. A) or another entity (XYZ Inc.) that enjoy the advantages and make decisions related to the assets.
Beneficial Ownership vs. Legal Ownership: Explained
Beneficial ownership and legal ownership are closely related concepts in the realm of finance, yet they have distinct differences that play a crucial role in various financial transactions.
Legal ownership refers to the individual or entity whose name appears on the official documents as the owner of an asset, property, or investment. In most situations, legal owners and beneficial owners are the same, meaning the person or organization listed on the paperwork also enjoys the benefits and responsibilities associated with the ownership. In many cases, legal owners act as trustees or nominal holders for the beneficial owners. These arrangements are common in trusts, investments, and corporate structures.
Similarities and Differences:
Similarities:
- Both legal and beneficial owners have a connection to the asset in question.
- Both legal and beneficial owners may have financial interests tied to the asset's performance.
Differences:
- Legal owners are named on the documents and might have legal control, but beneficial owners hold the true decision-making power and enjoy the financial benefits.
- In some instances, beneficial owners might prefer to remain anonymous, especially in properties or investments, where their identities are shielded behind legal entities. Legal owners, on the other hand, are publicly registered.
- When a legal entity opens a bank account, the bank must identify the beneficial owners to prevent money laundering and tax evasion. Legal ownership is the entity itself, but the beneficial owners are the individuals or entities controlling the funds and enjoying the financial benefits.
How to Identify Beneficial Owners?
Identifying beneficial owners requires a methodical and thorough approach, involving in-depth research and analysis. Here’s a detailed breakdown of the steps involved, focusing on understanding beneficial ownership agreements.
1. Utilizing Public Records and Corporate Documents:
Begin your investigation by examining public records and corporate documents related to the entity under scrutiny. These documents often contain valuable information about shareholders, annual reports, and filings with regulatory bodies. Scrutinize these records to identify individuals or entities associated with the organization.
2. Examining Regulatory Filings:
Carefully analyze regulatory filings submitted to government agencies or securities commissions. These filings offer crucial insights into corporate ownership. Look for any indications of intermediary entities or influential shareholders. Cross-referencing these filings can provide a clearer view of the ownership structure.
3. Investigating Ownership Structures:
Delve into the complex ownership structures of the entity, focusing on subsidiaries, trusts, and holding companies. Unraveling these structures is vital, as beneficial owners often hide behind layers of intermediaries. Look for patterns that suggest a chain of ownership, leading you closer to the ultimate beneficial owner.
4. Beneficial Ownership Agreements:
Entities occasionally enter into beneficial ownership agreements outlining rights, responsibilities, and benefit distribution among stakeholders. Although not always publicly accessible, these agreements can be obtained through legal channels, especially during legal disputes or regulatory investigations. Analyzing these agreements provides vital insights into beneficial owners and their ownership benefits distribution.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Also Read: Beneficial Ownership: A Deep Dive into FATF's Recommendation 24
Different Areas of Beneficial Ownership
- Business Enterprises: In the corporate world, understanding who truly owns and controls a company is vital for investors and regulators. Beneficial ownership sheds light on potential conflicts of interest and unethical practices.
- Real Estate: In the realm of property, especially high-value assets, identifying beneficial owners ensures transparency. This is crucial for combating money laundering and illegal property acquisitions.
- Trusts and Funds: Beneficial ownership in trusts and funds often involves intricate structures. Investigating these entities is essential for financial institutions and regulators to prevent fraudulent activities.
Importance of Beneficial Ownership Disclosure
Transparent disclosure of beneficial ownership is the cornerstone of a robust financial system. It enhances trust, facilitates fair market competition, and deters illicit financial activities. For instance, when governments enforce stringent beneficial ownership regulations, it becomes challenging for corrupt officials and criminals to hide their assets, promoting accountability and integrity.
Additionally, transparent beneficial ownership disclosure fosters investor confidence and encourages foreign investments. When investors have access to clear information about who truly controls and benefits from a company, they can make informed decisions, leading to a more stable and prosperous economy. Moreover, it strengthens regulatory oversight, allowing authorities to detect and prevent fraudulent schemes effectively. By promoting openness and honesty in financial dealings, beneficial ownership disclosure becomes a catalyst for sustainable economic growth and a fairer, more equitable society.
SWIFT Code
Navigating the vast landscape of international banking can sometimes feel like deciphering a complex puzzle. Amidst this complexity, there's a key piece that helps everything run smoothly: the SWIFT code. Imagine you're sending money to a friend in another country or receiving a payment from an overseas client. In such scenarios, you'll often come across this unique combination of letters and numbers known as the SWIFT code.
While it might sound technical and a bit intimidating at first, it's essentially a special identifier that banks use to communicate with each other across borders. In this guide, we'll break down the concept of the SWIFT code, making it easy to understand. We'll explore what it means, why it's so important, and how it ensures that your money reaches the right destination safely and efficiently in the vast world of global finance.
Key Takeaways
- SWIFT (Society for Worldwide Interbank Financial Telecommunication) provides a standardized system for banks globally to communicate, with SWIFT codes acting as unique identifiers for each bank.
- The SWIFT code is essential for ensuring that international money transfers reach the correct bank and branch, acting as a GPS for funds.
- Transaction monitoring in the SWIFT system observes money transfers for suspicious activities, flagging unusual patterns or transfers to high-risk locations.
- Transaction screening in SWIFT checks the details of both the sender and receiver against global sanction lists, screens for Politically Exposed Persons (PEPs), and scans for any negative news associated with the entities involved.
Swift Code Meaning
Imagine a vast web of banks spread across the globe, each needing to talk to the other securely and quickly. That's where SWIFT comes in. Standing for the Society for Worldwide Interbank Financial Telecommunication, SWIFT is like the postal service of the banking world. It offers a safe and standardized way for banks to exchange messages about money transfers. Now, for these messages to reach the right bank, they need an address, right? That's what the SWIFT code or BIC (Bank Identifier Code) is - a unique string of characters that acts as a bank's specific address in this vast network.
So, whenever you're sending money overseas or receiving funds from another country, this code ensures your money goes precisely where it's supposed to, just like how a postal address ensures your mail gets to your doorstep.
History of Swift Code
The history of the SWIFT code dates back to the 1970s when the Society for Worldwide Interbank Financial Telecommunication (SWIFT) was established. As international banking and financial transactions became more common, there was a need for a standardized system that could facilitate communication between banks across borders.
The SWIFT code was introduced as a unique identifier for each bank, acting as a crucial component in the global network of financial institutions. Just like a postal address ensures that your mail reaches its intended destination, the SWIFT code ensures that international money transfers reach the correct bank and branch.
Over the years, the SWIFT system has evolved to incorporate transaction monitoring and screening processes, which help detect suspicious activities and ensure compliance with global banking regulations. Today, the SWIFT code plays a vital role in the seamless and secure transfer of funds in the vast world of global finance.
When and Why You Need a SWIFT Code
Imagine you're planning a surprise trip to Paris and need to book a charming hotel you found. To secure your reservation, you decide to wire some money. But how do you make sure your money reaches that specific hotel's bank in Paris and not somewhere else? Enter the SWIFT code. This code is like a GPS for your money, guiding it to the correct bank overseas. Whether you're sending money to a loved one abroad or making a business transaction with an international partner, the SWIFT code is your go-to tool. It's like giving clear directions in the vast world of global banking.
On the flip side, if you're expecting money from overseas, you'd share your bank's SWIFT code with the sender. It's all about making sure every penny lands in the right place, safely and swiftly. Without the SWIFT code, it would be like sending a letter without an address - it could end up anywhere!
Role of SWIFT Code in International Transactions
Imagine the world of global banking as a massive, bustling city with roads leading to countless destinations. In this city, the SWIFT code is like a trusted GPS system, ensuring that every vehicle (or in this case, transaction) reaches its intended location safely. Just as you'd rely on a GPS to navigate unfamiliar roads, banks depend on the SWIFT code when sending money overseas. It's the unique address that pinpoints the exact bank and branch where the funds need to go. Think of it as giving clear directions to your money, ensuring it doesn't get lost in the vast city of international banking.
But the SWIFT code does more than just guide transactions. In our city analogy, it also acts as a communication tool, like a phone connecting different parts of the city. Banks, like residents of a city, need to talk to each other, especially when dealing with international transactions. They exchange vital information, double-check transaction details, and ensure everything aligns with global banking rules. This constant communication keeps the financial city's heartbeat steady, ensuring trust, transparency, and smooth operations in the intricate world of global finance.
Components of SWIFT Code
Imagine you're sending a letter to a friend who lives in a big city. You'd need their street address, city, state, and maybe even an apartment number to make sure your letter gets to the right place. Similarly, the SWIFT code is like an address for banks, but instead of streets and cities, it uses codes to pinpoint a bank's exact location worldwide.
A SWIFT Code includes:
- Bank Code (4 characters): Think of this as the name of the street where the bank lives. Just as 'Maple St.' might be a street's name, 'ABCD' could be a code for a specific bank like 'ABC Bank'.
- Country Code (2 characters): This is like the state or country in an address. So, 'US' tells us that the bank is in the United States.
- Location Code (2 characters): This is similar to the city or town in an address. It gives more specific details about where the bank is situated within the country.
- Branch Code (3 characters, optional): If our bank was an apartment complex, this would be the apartment number. It pinpoints a specific branch of the bank. If it's not there, it's like sending a letter to the main office or the main building of the apartment complex.
Using Transaction Monitoring to Detect Crimes in SWIFT Transfers
Imagine you're a security guard at a big event, and your job is to watch out for anyone who seems suspicious. You'd be on the lookout for people who act differently from the rest, right? Similarly, in the world of banking, there's a system in place that acts like this security guard, but for money transfers. This system is called transaction monitoring.
When money moves across countries using SWIFT transfers, it's like people moving in and out of our big event. Most of these transfers are just regular people doing regular things - like sending money to family or paying for a purchase. But sometimes, there might be someone trying to do something sneaky, like moving illegal money without getting caught. This is where transaction monitoring steps in. It watches all the money transfers, and if it sees something that looks odd - like someone transferring a lot of money many times quickly or sending money to places known for illegal activities - it raises an alarm. This way, banks can check these suspicious transfers more closely and stop any bad activities.
Using Transaction Screening to Detect Bad Actors in SWIFT Transfers
Transaction screening is another crucial layer of security in the SWIFT system. While transaction monitoring focuses on the nature and pattern of transactions, transaction screening zeroes in on the entities involved. This process involves:
- Checking Against Sanction Lists: Before a SWIFT transfer is approved, the details of the sender and receiver are screened against global sanction lists. These lists contain names of individuals, organizations, and countries that are barred from participating in international transactions due to various reasons, such as involvement in terrorism or other criminal activities.
- PEP (Politically Exposed Persons) Screening: Financial institutions also screen for PEPs - individuals who hold a significant public position and might be at a higher risk of being involved in bribery or corruption. This doesn't mean transactions involving PEPs are automatically flagged as suspicious, but they undergo a higher level of scrutiny.
- Adverse Media Screening: Modern screening tools also scan online news sources and databases to check if the entities involved in the transaction have been associated with any negative news or illicit activities in the past.
Conclusion
SWIFT codes play an indispensable role in the realm of international banking, ensuring that money transfers are both efficient and secure. While the system is designed to facilitate global commerce, it's equally equipped with robust mechanisms like transaction monitoring and screening to thwart financial crimes. As the world becomes increasingly interconnected, understanding the intricacies of SWIFT codes and their associated processes is paramount for both individuals and businesses participating in the global financial landscape.
Know Your Customer
In an increasingly interconnected and digital world, the importance of Know Your Customer (KYC) compliance cannot be overstated. KYC, be it traditional KYC or eKYC, is a vital process that financial institutions, businesses, and organizations undertake to verify the identities of their customers, assess potential risks, and ensure compliance with regulatory requirements. eKYC is a digital method of verifying the identity of customers remotely, without requiring them to visit a physical branch or submit physical documents.
A robust KYC process is the foundation for enhanced due diligence and preventing issues like money laundering or terrorist financing. This article delves into the key components of KYC, explores effective customer verification methods, and sheds light on the purpose and significance of KYC in today's business landscape.
Key Takeaways
- KYC comprises three essential components: customer identification, customer due diligence, and ongoing monitoring.
- Effective customer verification can be achieved through a combination of document verification, identity verification, and risk assessment.
- KYC serves multiple purposes, including mitigating the risk of financial crimes, preventing money laundering, and maintaining regulatory compliance.
- Stay updated with the latest KYC trends and requirements to ensure seamless compliance with the Patriot Act and other relevant regulations.
- Online KYC portals provide convenient and efficient solutions for verifying customer information and streamlining the KYC process.
- Corporates have specific KYC requirements that focus on beneficial ownership, corporate structure, and risk assessment.
The Three Components of KYC
KYC comprises three crucial components that form the foundation of effective customer identification and risk management.
- The first component is customer identification, which involves gathering accurate information about customers' identities through reliable documents or data sources.
- Customer due diligence is the second component, which involves assessing the risk associated with each customer and determining the level of scrutiny required. It includes evaluating the customer's background, financial activities, and potential risks.
- The third component is ongoing monitoring, which ensures continuous vigilance over customer accounts and transactions to identify any suspicious or abnormal activities that may arise over time.
Read More: Understanding the Meaning of KYC and its Difference with AML
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Verifying Customer KYC: Effective Methods
To verify customer KYC information, organizations employ various methods to ensure accuracy and reliability. Document verification involves validating identification documents such as passports, driver's licenses, or national identification cards to verify the customer's identity. Identity verification methods include biometric authentication, facial recognition, or knowledge-based authentication to validate the customer's claimed identity.
Additionally, risk assessment techniques are employed to evaluate the customer's risk profile based on factors such as their financial history, reputation, or involvement in illicit activities. These methods combined provide a robust framework for effective customer verification in the KYC process.
Understanding the Purpose of KYC
The purpose of KYC is multi-faceted, encompassing several critical objectives.
- Firstly, KYC aims to mitigate the risk of financial crimes by ensuring that businesses are aware of the identities and backgrounds of their customers, reducing the likelihood of fraudulent activities.
- Secondly, KYC plays a crucial role in preventing money laundering by identifying and reporting suspicious transactions that may be indicative of illicit funds.
- Lastly, KYC is essential for regulatory compliance, enabling organizations to adhere to legal and regulatory requirements set by governing bodies to maintain the financial system's integrity and safeguard against illicit activities.
Navigating the KYC Process: A Step-by-Step Guide
The KYC process follows a structured approach that involves several key steps. It begins with the completion of a comprehensive KYC form where customers provide their personal information, including identification details, contact information, and employment history. The next step involves submitting the necessary documents for verification, such as proof of identity, address, and financial statements.
Once submitted, these documents undergo thorough validation to ensure their authenticity. The final step is risk assessment and scoring, where the customer's information is assessed to determine their risk profile. This step involves evaluating factors such as their financial stability, reputation, and potential involvement in illegal activities.
Read More: A Guide to Perpetual KYC
KYC Requirements for Corporates: An Overview
When it comes to KYC requirements for corporates, there are specific considerations to ensure compliance and mitigate risks. Understanding beneficial ownership is crucial, as businesses need to identify and verify the individuals who ultimately own or control the corporate entity. This involves gathering information about significant shareholders, directors, and individuals with ultimate control or decision-making power.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Assessing corporate structure and control is another essential aspect, as it helps determine the organization's hierarchical setup, subsidiaries, and affiliates. Risk assessment is also a vital component, allowing businesses to evaluate the potential risks associated with corporate clients, such as their industry, geographic location, and exposure to regulatory scrutiny. By incorporating these requirements, corporates can strengthen their KYC processes and demonstrate transparency in their operations.
Conclusion
Know Your Customer (KYC) is a critical process in today's business landscape, serving to verify customer identities, mitigate risks, and ensure compliance with regulatory obligations. By understanding the three components of KYC, adopting effective verification methods, and recognizing its purpose in preventing financial crimes, businesses can maintain integrity and trust in their operations.
Following a step-by-step guide and adhering to specific requirements for corporates, enables organizations to navigate the complexities of KYC with ease. Embracing KYC as a comprehensive compliance measure empowers businesses to establish a robust framework for customer identification, due diligence, and ongoing monitoring, ensuring a secure and trustworthy environment for all stakeholders involved.
Insider Trading
Introduction
In the thrilling world of financial markets, insider trading stands as a controversial and often misunderstood concept. It brings up images of secretive deals, leaked confidential information, and serious legal repercussions.
Preventing insider trading includes monitoring for suspicious activity and practising enhanced due diligence on high-risk individuals. This article aims to demystify insider trading, explaining its workings, examining its variants, discussing some prominent cases, and looking at preventive measures.
Key Takeaways
- Insider trading involves trading securities based on non-public information, and it can be both legal and illegal, with the latter being punishable by law.
- Insider trading undermines market integrity and investor confidence, necessitating robust regulatory policies and corporate governance practices.
- Prominent cases of insider trading have led to significant changes in securities laws and regulations, highlighting the importance of transparency and accountability.
- Preventing insider trading requires measures such as regulatory policies, corporate governance practices, and whistleblower programs to encourage early detection and reporting.
- Understanding the complexities of insider trading helps promote fair and efficient markets, safeguarding investor interests and upholding financial system integrity.
Insider Trading: Decoding the Concept
Insider trading involves buying or selling a publicly-traded company's securities based on material, non-public information about the company. In many jurisdictions, this practice is illegal as it undermines investor confidence and disrupts market integrity.
The Intricacies of Insider Trading
Insider trading revolves around the possession and use of confidential, significant information not available to the public. Insiders who have access to such information have a potential unfair advantage in the market.
Possessing Insider Information
Insider information refers to material, non-public facts about a company. This information is considered "material" if it could potentially affect a company's stock price if disclosed.
Trading on Insider Information
This involves making trades based on insider information. It typically results in gains or avoidance of losses for the insider, at the expense of the general investing public.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Many Guises of Insider Trading
Legal Insider Trading
Legal insider trading occurs when corporate insiders—officers, directors, or employees—buy or sell shares in their own companies in accordance with securities laws and regulations.
Illegal Insider Trading
Illegal insider trading refers to the buying or selling of securities based on material, non-public information, in violation of a duty of trust. This form of insider trading is punishable by law.
Prominent Instances of Insider Trading
High-profile Legal Cases
The world has seen several high-profile insider trading cases, involving renowned business magnates and prestigious corporations. These cases have triggered sweeping changes in securities laws and regulations.
Here are two insider trading cases involving renowned business magnates and prestigious corporations:
- Sung Kook "Bill" Hwang, the founder and portfolio manager of Tiger Asia Management and Tiger Asia Partners, was charged by the SEC in 2012 for conducting insider trading schemes involving Chinese bank stocks. Hwang short sold three Chinese bank stocks based on confidential information received in private placement offerings, making $16.7 million in illicit profits. He and his firms agreed to pay $44 million to settle the SEC's charges.
- Bill Hwang, the owner of Archegos Capital Management, faced a significant downfall in 2021 when the private fund imploded, leaving global banks with losses of $10 billion. Hwang was accused of leveraging stock positions and artificially inflating their prices, resulting in massive losses for the banks. He pleaded guilty to wire fraud related to illegal trading of Chinese stocks and paid $44 million to settle U.S. insider trading charges.
Corporate Instances
Several corporations have also faced insider trading allegations. These instances have brought the issue to the forefront, necessitating robust corporate governance and transparency.
Here are two insider trading cases involving corporations:
- In 2020, the Securities and Exchange Commission (SEC) charged a former finance manager at Amazon.com Inc. and two family members with insider trading in advance of Amazon earnings announcements between January 2016 and July 2018. The family allegedly reaped illicit profits of approximately $1.4 million from their unlawful trading in Amazon securities.
- In 2012, the SEC charged the manager of two New York-based hedge funds with conducting a pair of trading schemes involving Chinese bank stocks and making $16.7 million in illicit profits. Sung Kook "Bill" Hwang, the founder and portfolio manager of Tiger Asia Management and Tiger Asia Partners, committed insider trading by short selling three Chinese bank stocks based on confidential information they received in private placement offerings.
Insider Trading and Money Laundering
Insider trading and money laundering are both financial crimes that undermine the integrity of financial markets. While insider trading involves the illegal use of non-public information for personal gain in securities trading, money laundering is the process of disguising the origins of illicitly obtained funds to make them appear legitimate. In some cases, individuals involved in insider trading may engage in money laundering activities to conceal the proceeds of their illegal trades.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Safeguarding Against Insider Trading: Effective Measures
Regulatory Policies
Robust regulatory policies, including disclosure requirements and trading restrictions, play a crucial role in preventing insider trading.
Corporate Governance
Good corporate governance practices, such as establishing clear trading policies for employees, can help deter insider trading within corporations.
Whistleblower Programs
Whistleblower programs encourage employees and other insiders to report suspected illegal activities, including insider trading, thereby facilitating early detection and prevention.
Conclusion
Insider trading is a complex phenomenon, standing at the intersection of ethics, law, and finance. By understanding its intricacies, acknowledging its diverse forms, learning from past instances, and implementing robust prevention measures, we can promote fair and efficient markets. Such vigilance ensures the protection of investor interests and upholds the integrity of financial systems.
Politically Exposed Person
In the world of finance and global transactions, the term "Politically Exposed Person" or PEP has become increasingly significant. PEPs are individuals who are or have been entrusted with a prominent public function, which can potentially put financial institutions at risk from money laundering and corruption-related activities. Therefore, understanding PEPs and the associated risks is crucial for compliance and maintaining the integrity of financial systems.
In this article, we’ll delve into the concept of PEPs and the risks involved. We will also explore the importance of PEP screening as part of a robust compliance program.
Key Takeaways
- Politically Exposed Persons (PEPs) are individuals who hold or have held significant public positions.
- PEPs are considered at a higher risk of engaging in corruption and money laundering due to their influence and access to public funds.
- Financial institutions and regulatory bodies have established strict guidelines to identify and manage PEP-related risks.
- Conducting PEP checks is essential to ensure compliance with anti-money laundering regulations and mitigate the potential risks associated with PEPs.
- PEP checks involve verifying an individual's political exposure, assessing their source of wealth, and monitoring their financial transactions.
What Is a Politically Exposed Person (PEP)?
A Politically Exposed Person is someone who holds or has held a high-profile position in government, often with substantial influence over policy and decision-making. Due to their status and the nature of their position, PEPs are at a higher risk of being involved in bribery and corruption. It's important to note that being a PEP does not imply wrongdoing. However, it does necessitate a higher degree of scrutiny in financial dealings.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Categories of PEPs
PEPs are usually categorized into the following:
- Foreign PEPs: Individuals who hold prominent public positions outside of the financial institution's country.
- Domestic PEPs: Individuals with significant public roles within the financial institution's country.
- International Organization PEPs: Persons who hold a position in international organizations, such as the United Nations or World Bank.
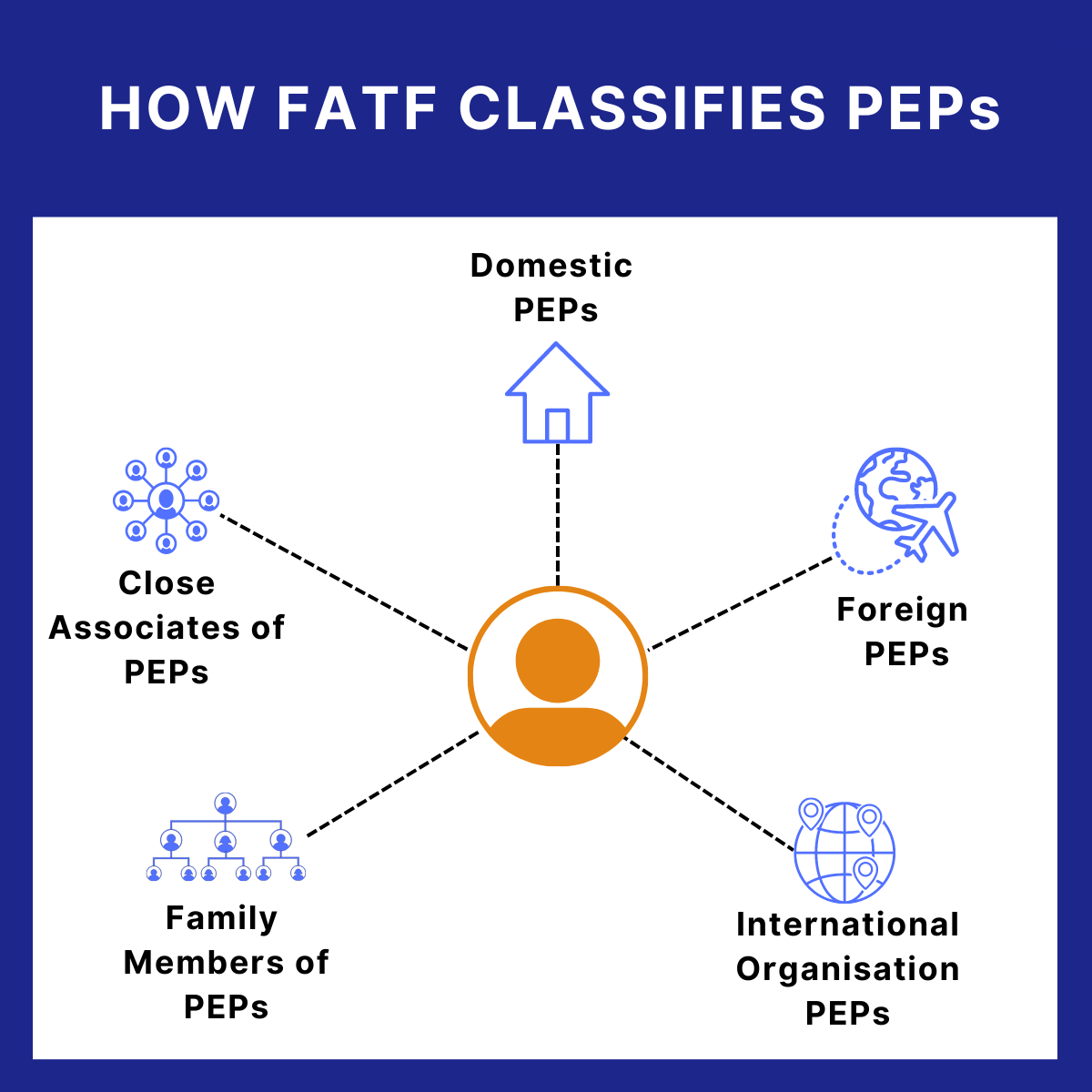
What is An Example of a Politically Exposed Person?
People who are politically exposed include:
- Heads of state or heads of government
- Senior government officials and politicians
- Officials from the military or the judiciary
- Senior officials from government-owned businesses
- Members of high-ranking political parties
- PEPs include close associates such as immediate family members and support employees
It’s tough to compile a list of politically exposed people because the criteria are so broad and differ from country to country. The Financial Action Task Force (FATF) makes periodic suggestions on PEPs, making a precise PEPs list even more difficult.
Most countries, on the other hand, base their PEP definitions on FATF recommendations, which categorises PEPs as follows:
Senior Government Officials
Current or former government officials who have been assigned to positions in the domestic government or in a foreign government could be politically exposed. This could include leaders of state or people in elected or unelected positions in the executive, legislative, administrative, military, or judicial departments.
Members of Political Parties
One category of PEPs is senior officials appointed to positions in major political parties in the United States or abroad.
Senior Executives
Individuals functioning as senior executives in government-owned commercial firms or international organisations, including directors or board members, may be labelled PEPs.
Relatives, Close Associates and Support Employees
PEPs might also include relatives and close associates (RCA). They include immediate family members such as spouses, parents, siblings, children and spouses’ parents and siblings. Support staff, especially of a government official, are also part of the list.
What Are the 4 Risk Levels for PEPs?
It is critical for financial institutions to understand the level of risk that their clients pose because this can influence how much scrutiny is applied to them as part of the risk-based strategy. Although the status of PEPs does not predict criminal activity, the heightened risk exposure it involves necessitates additional anti-money laundering and counter-terrorist financing (AML/CFT) protocols when establishing a commercial partnership.
It also means that these organisations must conduct ongoing monitoring to ensure that any changes in a PEP’s risk profile are not overlooked. The purpose of the PEP screening regulations is to prevent illegal behaviour.
Depending on one’s position, there are varying degrees of risk that a politically exposed person can bring.
High Risk Level 1
This category generally includes:
- Political party officials at the highest levels
- Members of Parliament (national and regional)
- Military, judicial, and law enforcement leaders, as well as members of the central bank board of directors
- Members of the government (national and regional)
Medium Risk level 2
This category includes:
- Military, judicial, and law enforcement officers at the highest levels
- High-ranking civil employees and officials from various governmental agencies and entities.
- Senior members of religious organisations
- Diplomats include ambassadors, consuls, and high commissioners, to name a few.
Medium Risk level 3
This risk category includes senior management and board of directors of state-owned businesses and organisations.
Low-Risk level 4
This category includes:
- Members of municipal, country, city, and district assemblies, as well as mayors
- International or supranational organisations’ senior leaders and functionaries
The Risks of Dealing with PEPs
Engaging with PEPs carries inherent risks due to their ability to influence public policy and control government resources. Here are some of the risks associated with PEPs:
Money Laundering and Corruption
PEPs can potentially abuse their position to embezzle funds, accept bribes, or be involved in other illicit financial activities. Their transactions may include large sums of money, which can be a red flag for money laundering.
Reputational Damage
If a financial institution is found to be involved with a PEP engaged in corrupt activities, it can suffer significant reputational damage. This can lead to a loss of customer trust and potential partnerships, as well as regulatory sanctions.
Regulatory Penalties
Failing to properly identify and screen PEPs can result in hefty fines and penalties from regulatory bodies. Financial institutions are expected to have adequate PEP screening processes in place to prevent money laundering and terrorist financing.
Who is Classed as Politically Exposed Persons (PEPs)
Identifying Politically Exposed Persons (PEPs) is a critical step for financial institutions and other entities to comply with anti-money laundering (AML) and counter-terrorism financing (CTF) regulations. PEPs are individuals who hold prominent positions in government, military, or international organizations, and their association with these positions exposes them to higher corruption and bribery risks. Here are key points to consider when identifying PEPs:
- Definition and Criteria: Various jurisdictions provide definitions and criteria to identify PEPs. These definitions typically encompass high-ranking government officials, heads of state, political party leaders, and senior executives in state-owned enterprises. The criteria may also extend to family members and close associates who could potentially exploit their connections.
- Reliable Data Sources: Financial institutions rely on reputable data sources to screen individuals and determine their PEP status. These sources include public registers, government databases, international organizations, and commercially available PEP databases. Accessing up-to-date and accurate information is crucial to ensure effective PEP identification.
- Enhanced Due Diligence (EDD): Financial institutions are required to implement enhanced due diligence measures for PEPs due to their higher risk profiles. This includes gathering additional information about the source of funds, business relationships, and the purpose of the transaction. EDD measures help identify and mitigate the potential risks associated with PEPs engaging in illicit activities.
- Ongoing Monitoring: Identifying PEPs is not a one-time process. Financial institutions must establish robust systems for ongoing monitoring of customer relationships. Regular screening of customer databases against updated PEP lists helps identify any changes in PEP status or new PEPs entering the system.
By effectively identifying PEPs, financial institutions and other entities can strengthen their AML and CTF frameworks, mitigate risks, and ensure compliance with regulatory obligations. Vigilance in PEP identification plays a vital role in safeguarding the integrity of the financial system and preventing illicit activities.
PEP Screening: A Critical Compliance Measure
PEP screening is the process of identifying and performing due diligence on individuals who may be considered PEPs. It's a preventive measure that helps financial institutions manage the risks associated with PEPs.
Elements of PEP Screening
- Identification: The first step is to identify whether a client or potential client is a PEP. This involves checking their name against various PEP lists and databases.
- Risk Assessment: Once identified, a risk assessment is conducted to determine the level of risk the PEP poses. Factors such as the PEP’s country of origin, the nature of the public position, and the level of authority can influence the risk level.
- Enhanced Due Diligence: For high-risk PEPs, enhanced due diligence procedures are carried out. This may include gathering additional information about their sources of wealth, business relationships, and the purpose of the intended business relationship with the financial institution.
Best Practices for PEP Screening
- Regularly update the PEP list and database to ensure all information is current.
- Train employees to recognize PEPs and understand the associated risks.
- Implement automated PEP screening systems to flag potential PEPs for further investigation.
- Document all PEP screening processes for accountability and regulatory compliance.
The Global Landscape of PEP Regulation
Regulations surrounding PEPs vary by country but are generally shaped by international bodies like the Financial Action Task Force (FATF). The FATF provides guidelines for the identification and treatment of PEPs, which member countries are expected to implement.
FATF Recommendations
The FATF recommends that financial institutions take reasonable measures to determine whether a customer or beneficial owner is a PEP. This involves obtaining senior management approval for establishing business relationships with PEPs, conducting enhanced ongoing monitoring, and ensuring that these measures are part of the institutions' Anti-Money Laundering (AML) and Countering Financing of Terrorism (CFT) policies.
Read More: Managing Politically Exposed Person Risks: Insights from FATF Guidance
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Challenges in PEP Identification and Screening
Despite the clear guidelines, financial institutions face challenges in PEP identification and screening.
Data Quality and Availability
Access to accurate and comprehensive data is essential for effective PEP screening. However, not all countries maintain detailed public records, which can hinder the identification process.
Evolving Regulatory Requirements
Regulations can change rapidly, and financial institutions must stay updated to remain compliant. Adapting to new requirements can be both time-consuming and resource-intensive.
Balancing Customer Experience and Compliance
While compliance is non-negotiable, it's also important not to hinder the customer onboarding experience. Finding the right balance between thorough screening and efficiency is a constant challenge.
Conclusion: Mitigating PEP-Related Risks
To mitigate the risks associated with PEPs, financial institutions must adopt comprehensive PEP screening processes as part of their wider compliance framework. By doing so, they protect themselves against involvement in corrupt activities, preserve their reputation, and contribute to the fight against global financial crime.
Tookitaki's Smart Screening solution helps screen customers and transactions accurately against sanctions, PEP, Adverse Media and other watchlists across 22+ languages in real time. It provides 90% accuracy of detection in real-time using 12 name-matching techniques on 7 customer attributes with a multi-stage matching mechanism and cross-lingual matching. To learn more about Tookitaki's screening solution, schedule a slot by clicking below.
Currency Transaction Report
Currency Transaction Reports (CTRs) play a vital role in combating money laundering and other financial crimes. Financial institutions must file CTRs to report certain transactions involving cash that exceed a specific threshold.
High-value transactions often trigger a currency transaction report as part of anti money laundering efforts. In this article, we will delve into the concept of Currency Transaction Reports, explore their requirements, examine examples of CTRs, discuss cash transaction report limits, and understand the implications when a CTR is filed.
Key Takeaways
- Currency Transaction Reports (CTRs) are filed by financial institutions to report cash transactions that exceed a specific threshold.
- CTRs are required to combat money laundering and other illicit financial activities.
- Financial institutions must comply with CTR requirements and report accurate information about the transactions.
- Cash transaction report limits vary by jurisdiction and may be subject to periodic updates.
- When a CTR is filed, regulatory authorities analyze the information and may take further action if suspicious activity is detected.
Understanding Currency Transaction Reports (CTRs)
Currency Transaction Reports (CTRs) are documents that financial institutions, such as banks, credit unions, and money service businesses, file with regulatory authorities to report specific cash transactions. CTRs are mandated by anti-money laundering (AML) regulations and help monitor and detect suspicious activities related to money laundering and other illicit financial practices.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Currency Transaction Report Requirements
Financial institutions are required to file a Currency Transaction Report with the appropriate regulatory authority, such as the Financial Crimes Enforcement Network (FinCEN) in the United States, when a cash transaction exceeds a certain threshold. The specific reporting threshold may vary by jurisdiction. For example, it is set at $10,000 in the US.
To comply with CTR requirements, financial institutions must collect and report information about the transaction, including the identities of the parties involved, the nature of the transaction, and the source and destination of the funds. Timely and accurate reporting is crucial to fulfilling regulatory obligations and supporting efforts to combat money laundering and terrorist financing.
Read More: Significance of Currency Transaction Reports in Banking
Examples of Currency Transaction Reports (CTRs)
Examples of Currency Transaction Reports can vary depending on the jurisdiction and reporting entity. However, a typical CTR includes information such as:
- Name, address, and identification details of the individual or entity conducting the transaction
Transaction date, time, and location - Transaction amount and currency
- Purpose of the transaction
- Identification details of any other individuals or entities involved in the transaction
The above details illustrate the type of information that may be included in a Currency Transaction Report, but the specific format and layout can differ across jurisdictions.
Cash Transaction Report Limits
Cash transaction report limits refer to the monetary threshold above which a financial institution must file a CTR. The exact threshold can vary by jurisdiction and may be subject to periodic updates or regulatory changes. Financial institutions must stay updated on the current cash transaction report limit in their jurisdiction to ensure compliance with reporting requirements.
What Happens When a CTR is Filed?
When a Currency Transaction Report is filed, it is submitted to the relevant regulatory authority, such as FinCEN. The regulatory authority analyzes the reported information and cross-references it with other financial intelligence and law enforcement databases. If the reported transaction raises suspicions of money laundering or other illicit activities, the regulatory authority may take further action, such as initiating an investigation or sharing the information with appropriate law enforcement agencies.
Financial institutions are legally obligated to maintain the confidentiality of the Currency Transaction Reports they file and are prohibited from disclosing their contents to the individuals involved in the reported transactions.
The Importance of CTRs in Combating Money Laundering
Currency Transaction Reports (CTRs) play a crucial role in the fight against money laundering and other illicit financial activities. By requiring financial institutions to report cash transactions above a certain threshold, CTRs help authorities monitor and detect suspicious activities that may indicate money laundering attempts. Here's why CTRs are important:
- Detection of Unusual Transaction Patterns: CTRs allow regulatory authorities to identify individuals or entities engaging in repetitive or unusual cash transactions. These patterns can indicate attempts to circumvent reporting requirements, disguise the true source of funds, or facilitate illicit activities.
- Identification of High-Risk Customers: By analyzing CTR data, regulatory authorities can identify customers or businesses with a high volume of cash transactions. This information helps in assessing the potential risks associated with these customers and initiating further investigations if necessary.
- Support for Investigations: CTRs provide a valuable source of information for law enforcement agencies and financial intelligence units. The data contained in these reports can be cross-referenced with other intelligence sources to uncover money laundering networks, trace illicit funds, and support criminal investigations.
- Deterrence and Prevention: The existence of CTR requirements acts as a deterrent to criminals engaging in large cash transactions. The knowledge that their activities may be reported and scrutinized reduces the attractiveness of cash-based money laundering schemes.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Practical Tips for Financial Institutions to Ensure CTR Compliance
Financial institutions must establish robust processes and controls to ensure compliance with Currency Transaction Report (CTR) requirements. Here are some practical tips to help institutions meet their reporting obligations:
- Staff Training and Awareness: Educate employees about CTR requirements, reporting thresholds, and the importance of accurate and timely reporting. Regular training sessions and updates on regulatory changes will help ensure that staff members are well-informed and equipped to fulfill their responsibilities.
- Robust Transaction Monitoring Systems: Implement advanced transaction monitoring systems that can identify cash transactions above the reporting threshold. These systems should be capable of collecting relevant information, generating CTRs automatically, and maintaining audit trails to demonstrate compliance.
- Data Quality Assurance: Establish processes to verify the accuracy and completeness of the data included in CTRs. Regularly review and validate the information to ensure its integrity and compliance with reporting standards.
- Internal Controls and Review Mechanisms: Implement strong internal controls, including segregation of duties, review procedures, and oversight mechanisms to ensure that CTRs are prepared, reviewed, and filed in a timely manner.
- Regulatory Compliance Monitoring: Continuously monitor regulatory developments and updates related to CTR requirements. Stay informed about changes in reporting thresholds, reporting formats, or other regulatory expectations to maintain compliance.
- Collaboration with Regulatory Authorities: Establish effective channels of communication and collaboration with regulatory authorities. Seek guidance, clarify reporting requirements, and promptly address any queries or concerns raised by the authorities.
By following these practical tips and ensuring a strong culture of compliance, financial institutions can fulfill their CTR reporting obligations effectively and contribute to the collective efforts in combating money laundering and other illicit financial activities.
Spoofing
We live in a time where our lives are deeply intertwined with the digital world, opening up a vast array of opportunities but also exposing us to new risks. "Spoofing" stands out as one of these risks, a cunning method used by cybercriminals to disguise themselves as safe and familiar figures in our electronic spaces.
This detailed guide will take you through the ins and outs of spoofing, explaining why it's important to be aware of, the various forms it can take, and how you can shield yourself from its deceitful manipulations.
Key Takeaways
- Spoofing is a deceptive practice used by cybercriminals to disguise communication from an unknown source as being from a known, trusted source.
- Spoofing attacks can take many forms, including email, caller ID, IP address, and GPS spoofing, each with its unique risks and implications.
- The consequences of spoofing can be severe, ranging from data breaches and financial loss to reputational damage and operational disruption.
- Preventing spoofing requires a combination of user awareness, robust security protocols, up-to-date technology, and organizational policies.
- Understanding the nuances of spoofing versus phishing is crucial in cybersecurity education and preventive strategies.
What is Spoofing?
In the world of cybersecurity, "spoofing" is when someone or something pretends to be something else in order to gain unauthorized benefits. It's like how a chameleon changes colors to match its environment, except, in the digital world, this disguise isn't used to hide from predators, but to trick and exploit others. Spoofing involves faking data to make a person, website, or program appear legitimate, allowing the spoofer to steal information, spread malware, or bypass access controls.
Importance of Spoofing Awareness
Being aware of spoofing is essential in today's digital world. Spoofing isn't just someone sending you a misleading email or message; it's a complex trick that can use many different ways to communicate, all designed to deceive. If someone falls for a spoofing scam, they might have their identity stolen, lose money, or give strangers access to private information. So, by knowing about spoofing and how it works, people and companies can spot when something's not right, stopping hackers before they cause harm.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Different Types of Spoofing Techniques
Spoofing can happen in many ways, each kind using its own sneaky methods. Here are a few spoofing examples:
- Email Spoofing: This is when someone changes an email's details to make it look like it's from someone else, usually to trick people into giving away private information. It's like a con artist using fake ID to convince you they're someone they're not.
- Caller ID Spoofing: This trick is when someone calls you but makes it look like the call is coming from another number. It's like someone calling you wearing a voice changer to sound like someone you trust.
- IP Spoofing: Here, the spoofer hides or changes their IP address (their internet location) to look like another computer or device. Imagine a burglar wearing a mask to look like your neighbor, so you let them into your house.
- GPS Spoofing: This type is about sending wrong signals to GPS systems to make them show the wrong location. It's as if someone gave you a map with fake directions, leading you to the wrong place.
- Website Spoofing: This happens when someone makes a fake website that looks exactly like a real one, trying to get you to enter your personal details. It's like a fake bank set up to collect people's money.
- ARP Spoofing: This one's a bit technical, but it's basically about sending fake "address" messages over a local internet network. This tricks the network into sending information to the wrong place. Imagine if someone fooled the mailman into delivering your mail to their house instead of yours.
Risks and Implications of Spoofing
Spoofing attacks pose significant risks, both for individuals and organizations:
- Data Theft: Imagine if someone could walk into your house and look through all your private papers without you knowing. That's what spoofing can do. It sneaks into private data like a thief, taking things like passwords, money details, or even personal secrets about customers.
- Financial Loss: Spoofing scams can trick people into sending money where it shouldn't go. It's like a magician who makes you think you're putting money in your pocket, but it ends up in theirs!
- Reputation Damage: If spoofing hits a company, it's not just about money or data. The trust people have in the company can break into pieces. Customers might walk away, and the law might come knocking. It's like if a friend lied to you, and even if they said sorry, it wouldn't be the same again.
- Network Compromise: IP spoofing is like a master of disguise for breaking into computer networks. It doesn't smash a window; it tricks the network into thinking it's a friend. Once inside, it can peek around, take what it wants, or even let other bad guys in.
- Disruption of Services: Some spoofers don't want to steal; they just want to see the world burn. They use spoofing to mess up services, like making a website stop working or slowing down the internet, just like someone causing a traffic jam on purpose.
Spoofing isn't just a prank; it's a serious trick that can turn things upside down for people and companies. It's a digital mask for trouble, hiding the true face of danger.
How to Prevent Spoofing
Securing yourself and your organization against spoofing attacks requires a robust and multi-faceted approach. Here's how you can strengthen your defenses:
- Education and Awareness: To effectively prevent spoofing, it is crucial to have a clear understanding of what it entails. Regular training sessions should be conducted for all members of your organization, providing them with insights into the various types of spoofing attacks and their modus operandi. It is essential for employees to be able to identify red flags, such as unexpected requests for sensitive information or messages from unfamiliar sources. Engaging in role-playing exercises can simulate potential scenarios, enabling staff to practice their response in a safe and controlled environment.
- Use of Technology: Fortify your digital presence by harnessing cutting-edge technology. Implement email filtering services that possess the capability to identify and thwart spoofed emails. Enhance your network security through the utilization of IP validation techniques, guaranteeing that each device connected to your network is duly authenticated. Elevate your defense mechanisms with the implementation of multi-factor authentication (MFA), an additional layer of security that mandates multiple forms of verification before granting access. This formidable barrier makes it exponentially more challenging for spoofers to infiltrate your system, even in the event that they manage to obtain user credentials.
- Regular Updates: It is of utmost importance to keep all systems up to date, as cybercriminals often take advantage of outdated software. This not only applies to your operating systems but also includes any applications and security software. By regularly scheduling updates and patches, you can effectively address security flaws and enhance overall protection against potential spoofing attacks.
- Verification Procedures: Do not simply accept any request without question, particularly if it includes sensitive information or requires immediate action. It is essential to establish standard procedures for verifying requests. This may involve callback procedures, where employees can contact the individual making the request on a verified number, or the implementation of multiple approvals for the release of funds or sensitive information.
- Incident Response Plan: Even with the best preventive measures in place, there is always a possibility of spoofing attacks. That is why it is crucial to have a well-defined incident response plan. This plan should clearly outline the necessary steps to be taken when a spoofing attempt is suspected, including documenting the incident, reporting it to the appropriate authorities, and effectively containing any potential threats. Regular drills and exercises can help ensure that everyone is well-prepared and knows their role in handling such situations.
By integrating these practices into your daily operations, you can create a robust defense system that not only prevents spoofing attacks but also minimizes their impact if they do occur. Remember, the key to security isn't just one big solution, but a series of small, consistent actions taken every day.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
In the digital age, where data is as valuable as currency, understanding and combating spoofing attacks are paramount. These deceptive maneuvers, capable of tricking even the vigilant eye, pose a constant threat to personal and organizational security. Awareness is the first line of defense, followed by technological safeguards and robust security policies. As technology evolves, so do the tactics employed by cybercriminals. Staying informed about the various forms of spoofing, their potential impacts, and the most effective prevention strategies is an ongoing necessity for securing digital assets in this ever-evolving cyber landscape.
Frequently Asked Questions (FAQs)
What is a spoofing attack?
A spoofing attack is when a malicious party impersonates another device or user on a network to launch attacks against network hosts, steal data, spread malware, or bypass access controls.
What is Spoofing vs. phishing?
Spoofing is a technique used in phishing attacks, where the attacker disguises themselves as a reputable entity or person in email headers or addresses, phone numbers, or websites. Phishing is a broader term for fraudulently obtaining private data.
Enhanced Due Diligence
Enhanced Due Diligence (EDD) is a crucial process in the field of risk management and compliance. It involves conducting a more comprehensive analysis of customer information to identify and assess any potential risks or threats associated with a particular individual or entity. In this article, we will explore what EDD is, how it differs from standard due diligence, the significance of EDD in risk management, and the challenges and best practices involved in implementing EDD.
What is EDD?
Enhanced Due Diligence, often referred to as EDD, is an advanced risk management process that delves deeper than standard due diligence measures to provide a comprehensive understanding of the risks associated with a customer or business relationship. While traditional due diligence focuses on verifying identity and conducting basic background checks, EDD takes a more in-depth approach by analyzing a wide range of factors.
When conducting Enhanced Due Diligence, financial institutions and businesses may look into the source of funds, beneficial ownership structures, politically exposed persons (PEPs) connections, and complex ownership hierarchies. This thorough investigation helps to uncover any potential vulnerabilities and ensures a more robust risk assessment process.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
One key aspect of EDD is the ongoing monitoring of high-risk customers or entities. This involves regularly updating customer information, conducting periodic reviews, and reassessing the level of risk associated with the relationship. By continuously monitoring these relationships, organizations can promptly identify any suspicious activities and take appropriate action to mitigate potential risks.
How Enhanced Due Diligence is Different from Customer Due Diligence
While both EDD and Customer Due Diligence (CDD) share the objective of assessing customer risk, they differ in the level of scrutiny and investigation conducted. Customer Due Diligence generally involves verifying the identity of the customer and assessing the risk associated with them based on their transactional behaviour.
In contrast, EDD requires a deeper level of analysis and investigation, often involving additional verification steps and information gathering. It is typically conducted for customers or business relationships that pose a higher risk based on factors such as their industry, geographical location, or the nature of their transactions.
Enhanced Due Diligence (EDD) is a crucial process in the realm of anti-money laundering (AML) and counter-terrorism financing (CTF) efforts. This advanced level of scrutiny goes beyond the basic identification and risk assessment conducted in Customer Due Diligence (CDD). EDD is essential for identifying and mitigating the risks associated with high-risk customers or transactions that could potentially involve money laundering or terrorist financing.
When conducting Enhanced Due Diligence, financial institutions and businesses may delve into a variety of factors to assess the level of risk posed by a customer. This can include analyzing the source of funds, reviewing the customer's business relationships, and evaluating the purpose of complex transactions. By gathering this additional information, organizations can gain a more comprehensive understanding of the potential risks involved and take appropriate measures to mitigate them.
EDD vs Standard Due Diligence: Key Differences
While standard due diligence measures are essential for customer onboarding, EDD aims to provide a more comprehensive view of the customer's risk profile. Some key differences between EDD and standard due diligence include:
- Scope: EDD involves a wider scope of investigation and analysis than standard due diligence.
- Verification Process: EDD requires additional verification steps and gathering of supporting documentation.
- Monitoring: EDD often involves ongoing monitoring of high-risk customers to detect any suspicious activities.
- Reporting: EDD may result in more detailed reports outlining the findings and risk assessment.
When it comes to standard due diligence, the focus is primarily on verifying the identity of the customer and ensuring compliance with regulations. This process usually involves checking official documents such as identification cards, passports, and proof of address. While this is crucial for establishing the basic information about a customer, it may not provide a complete picture of their risk level.
On the other hand, EDD goes beyond the surface-level checks and delves deeper into the customer's background, transaction history, source of funds, and overall behaviour. By conducting enhanced due diligence, financial institutions can better assess the potential risks associated with a customer and make informed decisions regarding the level of monitoring required.
Checklist for Enhanced Due Diligence
According to the Financial Action Task Force (FATF), financial institutions should employ a risk-based approach when they try to assess their customers for possible ties to money laundering and terrorist financing (ML/TF) activities. “Customer due diligence (CDD) processes should be designed to help banks understand who their customers are by requiring them to gather information on what they do and why they require banking services,” says the FATF.
The watchdog adds that enhanced monitoring should be required for higher-risk situations, while banks may decide to reduce the frequency and intensity of monitoring where the risks are lower. The amount and type of information obtained, and the extent to which this information is verified, must be increased in high-risk cases. It may also be simplified where the risk associated with the business relationship is lower.
The FATF has suggested banks “to draw up, and periodically update, customer risk profiles, which serve to help banks apply the appropriate level of CDD”.
It has recommended the following as practicable Enhanced Due Diligence procedures:
- Obtaining additional identifying information from a wider variety or more robust sources and using the information to inform the individual customer risk assessment
- Carrying out additional searches (for example, verifiable adverse media searches) to inform the individual customer risk assessment
- Commissioning an intelligence report on the customer or beneficial owner to understand the risk that the customer or beneficial owner may be involved in criminal activity
- Verifying the source of funds or wealth involved in the business relationship to be satisfied that they do not constitute the proceeds from crime
- Seeking additional information from the customer about the purpose and intended nature of the business relationship
High-Risk Customers That Require Enhanced Due Diligence
There are certain types of customers or business relationships that are considered higher risk and therefore require Enhanced Due Diligence. These may include:
- Politically Exposed Persons (PEPs): Individuals who hold prominent public positions or have connections to political figures.
- Foreign Customers: Customers or entities based in countries with a high risk of money laundering or corruption.
- Complex Corporate Structures: Companies with intricate ownership arrangements or offshore accounts that can be associated with illicit activities.
- Cash-Intensive Businesses: Businesses that primarily deal with large amounts of cash, such as casinos or money service providers.
Politically Exposed Persons (PEPs) are individuals who are more susceptible to being involved in bribery, corruption, or money laundering due to their influential positions. They may include government officials, senior executives of state-owned enterprises, or high-ranking military officers. PEPs pose a higher risk because their access to public funds and decision-making authority can make them targets for illicit financial activities.
Foreign customers from jurisdictions known for weak anti-money laundering regulations or high levels of corruption are also considered high-risk. These countries may lack transparency in their financial systems, making it easier for criminals to hide the origins of illicit funds. Financial institutions dealing with customers from these regions must exercise caution and conduct thorough due diligence to mitigate the risk of being unwittingly involved in money laundering schemes.
High-Risk Countries and Industries
Countries designated as high-risk by the FATF, necessitating heightened due diligence procedures, include:
- Albania
- Ghana
- Cambodia
- Zimbabwe
- Panama
- Nicaragua
- Barbados
- Senegal
- Myanmar
- Morocco
- Syria
- Botswana
- Mauritius
- Jamaica
- Burkina Faso
- Uganda
- Cayman Islands
- Iran
- Yemen
- Democratic People’s Republic of Korea (DPRK)
Certain industries inherently face a higher risk of financial crimes and illicit activities, underscoring the necessity for implementing EDD measures.
Examples of industries that necessitate the use of EDD are:
- Money Services Businesses (MSBs), given the susceptibility to money laundering and terrorist financing activities.
- Investment firms must conduct customer due diligence to detect suspicious behaviour, verify customer identities, and comply with AML regulations to ensure proper diligence in managing clients' finances.
- Casino and iGaming platforms, where the implementation of EDD measures helps prevent the laundering of illicit funds through gambling activities.
- Correspondent Banking, is identified as a high-risk sector where financial institutions establish relationships with foreign banks, making thorough EDD essential to combat money laundering and terrorist financing. Correspondent banking services typically involve funds transfer, settlement, check clearing, and wire transfers.
- Cryptocurrency exchanges, where the use of EDD is crucial due to the anonymity and global nature of cryptocurrency transactions, help to mitigate associated risks.
EDD Requirements for High-Risk Customers
When conducting Enhanced Due Diligence for high-risk customers, certain requirements need to be fulfilled to ensure a thorough assessment. These requirements may include:
- Obtaining additional identification documents and verifying their authenticity.
- Performing in-depth background checks on the individuals associated with the customer or entity.
- Reviewing the source of funds and conducting transaction monitoring for suspicious activities.
- Assessing the customer's reputation and industry standing through media searches, regulatory databases, and other reliable sources of information.
- Engaging in ongoing monitoring and periodic reviews to stay updated on any changes or potential risks.
Enhanced Due Diligence (EDD) is a critical process in the financial industry, especially when dealing with high-risk customers who may pose a greater threat of money laundering, fraud, or other illicit activities. By going beyond standard customer due diligence procedures, EDD helps financial institutions better understand the nature of their customers' transactions and assess the associated risks more effectively.
Furthermore, EDD requirements often involve conducting enhanced scrutiny on politically exposed persons (PEPs) and individuals from high-risk jurisdictions. This involves not only verifying their identities and sources of wealth but also understanding their connections to government officials or entities that may increase the risk of corruption or bribery.
The Importance of EDD in Risk Management
Enhanced Due Diligence plays a critical role in risk management for organizations. By conducting a thorough assessment of high-risk customers, businesses can better understand the potential risks they may be exposed to and develop appropriate risk mitigation strategies.
Moreover, implementing EDD measures demonstrates a commitment to regulatory compliance and integrity, which can enhance an organization's reputation and credibility in the eyes of regulators, clients, and stakeholders.
One key aspect of Enhanced Due Diligence is the use of advanced technological tools and data analytics to gather and analyze information about customers. This can include monitoring transaction patterns, conducting background checks, and utilizing artificial intelligence to identify potential red flags. By leveraging these cutting-edge technologies, organizations can enhance the effectiveness and efficiency of their risk management processes.
Furthermore, EDD goes beyond just identifying risks; it also involves developing tailored risk profiles for high-risk customers. These profiles provide a detailed overview of the customer's background, business activities, financial transactions, and any other relevant information. By creating comprehensive risk profiles, organizations can make more informed decisions about how to manage and mitigate potential risks effectively.
Challenges and Best Practices in EDD
Implementing Enhanced Due Diligence measures can pose certain challenges for organizations. These challenges include:
- Allocating Sufficient Resources: Conducting EDD requires adequate resources, both in terms of manpower and technology.
- Access to Information: Gathering accurate and up-to-date information can be challenging, particularly when dealing with international customers or complex corporate structures.
- Balancing Efficiency and Accuracy: Striking the right balance between conducting a thorough investigation and promptly onboarding customers is crucial.
Despite these challenges, there are several best practices organizations can follow to effectively implement EDD:
- Developing Robust Policies and Procedures: Establishing clear guidelines and frameworks for conducting EDD can streamline the process.
- Investing in Technology: Leveraging advanced technology solutions can automate and streamline certain aspects of the EDD process.
- Continuous Training: Providing ongoing training to employees involved in EDD can ensure they stay updated on regulatory requirements and best practices.
One additional challenge that organizations may face when implementing EDD is the evolving regulatory landscape. Regulations surrounding due diligence practices are constantly changing and becoming more stringent, requiring organizations to stay vigilant and adapt quickly to remain compliant. Keeping up with these regulatory changes can be time-consuming and may require organizations to frequently update their EDD processes and procedures.
Moreover, another best practice that can enhance the effectiveness of EDD is establishing strong relationships with third-party service providers. Collaborating with reputable and reliable external partners, such as data providers or investigative firms, can supplement internal EDD efforts and provide access to specialized expertise and resources. Building these partnerships can strengthen the overall due diligence process and help organizations uncover potential risks more effectively.
Conducting Enhanced Due Diligence
When conducting Enhanced Due Diligence, organizations should follow a systematic approach to ensure a thorough analysis. The following steps can be helpful:
- Identify the purpose and objective of the EDD process.
- Define the criteria for identifying high-risk customers.
- Gather the necessary information and supporting documentation.
- Conduct an in-depth analysis and assessment of the gathered information.
- Document the findings and risk assessment in a comprehensive report.
- Implement appropriate risk mitigation measures based on the identified risks.
- Perform ongoing monitoring and periodic reviews to detect any changes or emerging risks.
Enhanced Due Diligence (EDD) is a critical process that goes beyond standard due diligence procedures to assess and mitigate risks associated with high-risk customers or transactions. By conducting EDD, organizations can gain a deeper understanding of potential risks and take proactive measures to prevent financial crimes such as money laundering, terrorist financing, and fraud.
One key aspect of EDD is the use of advanced screening tools and technologies to enhance the accuracy and efficiency of the risk assessment process. These tools can help organizations analyze vast amounts of data from multiple sources, including customer profiles, transaction histories, and adverse media reports, to identify red flags and potential risks more effectively.
{{cta('f24d2361-d707-461c-b808-c29f64ebda60')}}
Enhanced Due Diligence with Tookitaki
Enhanced Due Diligence is a multifaceted process that involves thorough investigation and analysis of potential risks associated with high-risk customers or business relationships. It requires a combination of advanced technology, expert knowledge, and regulatory understanding to effectively identify and mitigate risks.
Tookitaki is a leading provider of advanced AI-powered Fraud Prevention and AML solutions that can help organizations streamline and enhance their EDD processes. Tookitaki's FinCense is an end-to-end anti-financial crime compliance solution that seamlessly integrates with the AFC Ecosystem, employing a federated learning model to train on real-world scenarios for unparalleled fraud detection. With FinCense, benefit from faster customer onboarding, continuous monitoring, and smart screening against PEP, Sanctions, and Adverse Media watchlists.
Simplify your compliance processes with our 360-degree customer risk profiles, reduce false positives with Smart Alert Management, and enhance team collaboration with our centralized Case Manager. Don't let financial crime put your operations at risk. Talk to our experts today and discover how Tookitaki's FinCense can provide fewer, higher-quality alerts and a robust FRAML management process for your business.
Jurisdiction of Citizenship
Introduction
Citizenship, the legal bond between an individual and a state, is more than just a status - it is a realm of rights, duties, and societal participation. It places the individual under the jurisdiction of the state, which denotes the state's power to govern and enforce laws over that individual.
Understanding a customer's jurisdiction of citizenship helps in assessing potential tax evasion risks and ensuring proper identity verification. This article will explore the complex world of citizenship jurisdiction, offering an overview, a deep dive into its workings, and illuminating its implications.
Key Takeaways
- Jurisdiction of citizenship is the legal authority that a state has over its citizens, regardless of their location, and it is based on the principle of nationality or citizenship.
- The jurisdiction of citizenship extends beyond the physical borders of a state, meaning that a state's laws can affect its citizens even when they are abroad, depending on the laws and treaties in place.
- The dynamics of citizenship jurisdiction start at birth when an individual acquires citizenship and becomes subject to the laws and civic duties of their country of citizenship.
- Dual citizenship brings added complexity as individuals are subject to the jurisdictions of multiple countries, and conflicting laws can create legal dilemmas.
- There are two main types of jurisdiction in the context of citizenship: territorial jurisdiction, and personal jurisdiction.
Jurisdiction of Citizenship: The Core Concept
Defining Jurisdiction of Citizenship
Jurisdiction of citizenship refers to the legal authority that a state exercises over its citizens, regardless of their location. This authority is based on the principle of nationality or citizenship, which dictates that a state has the right to regulate its citizens' behavior and afford them protection.
The Sphere of Influence
The jurisdiction of citizenship extends beyond the physical borders of a state. It means a state's laws can affect its citizens even when they are abroad, depending on the laws and treaties that exist between the involved countries.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Dynamics of Citizenship Jurisdiction
How it Works: From Birth to Death
The process starts at birth when one acquires citizenship, usually through jus soli (right of the soil) or jus sanguinis (right of blood). The individual becomes subject to the jurisdiction of their country of citizenship, which includes obeying its laws and fulfilling civic duties such as voting or compulsory military service.
Dual Citizenship and Its Implications
In the case of dual or multiple citizenships, a person is subject to the jurisdictions of all countries where they hold citizenship. It brings added layers of complexity as different nations' laws can sometimes contradict each other, leading to legal dilemmas.
Types of Jurisdiction in the Context of Citizenship
Territorial Jurisdiction
Territorial jurisdiction refers to a state's power to enforce laws within its geographical boundaries. It applies to all individuals within the territory, regardless of their citizenship status.
Personal Jurisdiction
Personal jurisdiction, on the other hand, is based on a state's power over its citizens, irrespective of where they are. It is this jurisdiction that can extend globally, provided there are no conflicting international laws or treaties.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Use Cases and Examples
Case Study: Extradition
Extradition treaties exemplify jurisdiction of citizenship. A country may request the return of its citizen who has committed a crime abroad. However, the foreign state will only comply if an extradition treaty exists.
Legal Rights and Protections
Citizens abroad can seek assistance and protection from their home country's diplomatic missions, illustrating the jurisdiction of citizenship in offering legal rights and safeguards.
Conclusion: Navigating the Jurisdictional Map
Understanding the jurisdiction of citizenship provides invaluable insights into the interplay between personal rights, state authority, and international law. As our world continues to globalize, and as people increasingly live, work, and hold assets across borders, understanding the full implications of one's jurisdiction of citizenship becomes not just a theoretical exercise, but a practical necessity.
From interpreting dual citizenship complexities to understanding our rights when abroad, the concept of jurisdiction offers a roadmap to navigate the increasingly intricate legal landscape of the global citizen.
Tax Evasion
Tax evasion is a common problem globally. It happens when people purposely hide or provide false information on their tax returns to avoid paying the full amount of taxes they owe. The scale of this problem is staggering, with recent estimates indicating that tax evasion costs governments around the globe approximately US$5 trillion over the next 10 years.
This huge number highlights how serious the problem is, underscoring the immediate importance of understanding tax evasion—its complexities and the real-world impact it has on both businesses and individuals. Reporting and preventing tax evasion involves thorough due diligence on customer activities and transactions.
Key Takeaways
- Tax evasion involves intentionally avoiding tax payment through underreporting income, inflating deductions, or hiding money offshore, and it carries severe legal consequences.
- Personal tax evasion occurs when individuals manipulate their finances to evade taxes, while corporate tax evasion involves corporations using various methods to avoid paying their fair share.
- High-profile cases of tax evasion involving individuals and corporations serve as reminders of the penalties associated with this crime and the need for effective enforcement.
- Transparency, accurate reporting, seeking legal advice, and robust legislation are essential in combating tax evasion and promoting compliance with tax laws.
- Curbing tax evasion contributes to societal development by ensuring governments receive the necessary revenue to fund public services and create a fair economic environment for all.
What is Tax Evasion?
Tax evasion involves the deliberate manipulation of financial information, where individuals or businesses intentionally understate their income, inflate deductions, or hide assets to deceive tax authorities. Unlike tax avoidance, which employs legal means to minimize tax liability, tax evasion operates in the shadows, relying on deception, fraud, and evasion of legal obligations.
The difference between tax avoidance and evasion is pivotal. Tax avoidance, while controversial, involves using legal strategies to reduce tax obligations, often by exploiting loopholes or utilizing incentives provided by tax laws. On the flip side, tax evasion involves a clear violation of the law, using dishonest methods to avoid paying the taxes owed. The repercussions are significant, including substantial fines, loss of assets, and the possibility of imprisonment for those proven guilty.
Understanding Tax Evasion Meaning
Tax evasion involves a variety of deceptive practices intended to manipulate financial records and evade rightful tax obligations. One common method is underreporting income, where individuals or businesses deliberately declare less income than they actually earn. By doing so, they reduce the taxable amount, ultimately paying lower taxes than they owe. Inflating deductions is another technique, where expenses are exaggerated or fabricated to decrease taxable income artificially. This deceptive tactic results in a reduced tax liability, allowing the evader to retain more money illicitly.
One of the most significant and eye-opening instances of high-profile tax evasion is exemplified by the Panama Papers scandal, which came to light in 2016. The release of the Panama Papers involved millions of documents from a Panamanian law firm called Mossack Fonseca. These documents exposed the offshore financial dealings of many politicians, celebrities, and business leaders.
Among the notable personalities implicated was Iceland's Prime Minister, Sigmundur David Gunnlaugsson. The leaked papers revealed that he owned a company in the British Virgin Islands, which he didn't disclose while holding a public office. This disclosure sparked public outrage and eventually pushed Gunnlaugsson to step down, proving how tax evasion can affect even the most influential individuals.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
What Qualifies as Tax Evasion?
Tax evasion involves a multitude of deceptive practices aimed at manipulating financial records and evading tax obligations. Understanding these qualifying acts is crucial for both individuals and businesses to recognize potential red flags and avoid engaging in illegal activities. Here are some of the acts that qualifies for tax evasion.
1. Falsifying Financial Statements:
Falsifying financial statements is a serious offense wherein individuals or businesses manipulate accounting records to understate their actual income or overstate their expenses. By presenting misleading financial information, tax evaders deceive tax authorities, leading to inaccurate tax assessments and reduced tax payments.
2. Creating Fake Deductions:
Creating fake deductions involves fabricating business expenses or charitable donations that never occurred. Tax evaders may generate fictitious invoices, receipts, or payment records to support these deductions, artificially lowering their taxable income. This tactic aims to reduce the tax liability, allowing evaders to retain a larger portion of their income unlawfully.
3. Hiding Income:
Hiding income is a fundamental form of tax evasion where individuals or businesses conceal sources of income from tax authorities. This can include unreported cash transactions, off-the-books income, or underreported sales. By keeping income hidden, evaders ensure that tax authorities remain unaware of their actual earnings, resulting in lower tax assessments.
4. Inflating Expenses:
Inflating expenses involves exaggerating legitimate business costs, such as supplies, salaries, or operational expenses, to reduce taxable income. When tax evaders increase their expenses, they're essentially lowering their profits on paper, thereby avoiding higher tax payments. This move not only causes financial setbacks for the government but also gives the evaders an unjust edge in the market.
5. Using Shell Companies to Hide Assets:
Shell companies are legal entities with little to no active business operations. Tax evaders take advantage of these entities by moving their money through them to hide who owns certain assets. Using complicated ownership setups and offshore accounts, people can conceal their assets, making it challenging for tax authorities to accurately follow the money trail. This strategy is often connected to money laundering schemes, making investigations even more complex.
Tax Evasion Examples
1. Smurfing:
Smurfing, also known as structuring, is a money laundering technique employed to evade reporting requirements and conceal the origins of illicit funds. Criminals engaged in illegal activities often deal with significant amounts of cash, making it challenging to deposit the money into financial institutions without triggering suspicion. To circumvent this obstacle, they break down large cash transactions into smaller, less conspicuous amounts that fall below the threshold for mandatory reporting.
2. Trade Mispricing:
Trade mispricing is a sophisticated method of tax evasion that involves manipulating the prices of goods and services in international transactions between related entities. In this scheme, businesses overstate the cost of imports or understate the value of exports, creating an artificial gap between the real market value and the reported value of the goods. As part of this strategy, they move their profits to places with lower taxes, decreasing the money they have to pay in high-tax areas. This trick takes advantage of variations in tax rules and pricing systems between countries, letting tax evaders move significant amounts of money without drawing attention.
3. Cryptocurrency Tax Evasion:
With the rise of digital currencies, tax evasion has found a new frontier in the form of cryptocurrency transactions. Cryptocurrencies provide a level of secrecy and simplicity in transactions across borders, making them attractive to tax evaders aiming to hide their income. Individuals and businesses may underreport or completely omit cryptocurrency transactions from their tax returns, evading taxes on significant profits made through these digital assets. Dealing with tax evasion through cryptocurrencies is a tricky challenge for tax authorities. It demands creative approaches and advanced technologies to trace and unveil these concealed financial activities.
Types of Tax Evasion
Tax evaders employ cunning methods to deceive tax authorities, with the IRS identifying two primary tactics they use:
1. Evasion of Assessment:
In this method, tax evaders knowingly file false returns, concealing income and making illegitimate deductions. This fraudulent activity results in an inaccurate tax assessment. It's important to note that mere negligence isn't enough to constitute evasion of assessment; the act must go beyond negligence. Tax evaders may go as far as transferring taxable assets in their books to mislead the IRS during tax assessment, amplifying the gravity of their attempt to deceive.
2. Evasion of Payment:
Evasion of payment occurs when a taxpayer attempts to conceal assets after the tax becomes due and owed. This tactic includes hiding money in the accounts of family members or foreign institutions, making it difficult for the IRS to track. It's important to differentiate between not being able to pay the owed amount and deliberately evading taxes. While financial constraints might lead to delays, deliberate actions to obscure the funds constitute evasion of payment.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Tax Evasion and Money Laundering
Tax evasion and money laundering are like secret allies in the world of financial crimes. Tax evaders often turn to money laundering techniques to make their illegally earned money look legitimate. They use strategies like splitting large sums of money into smaller amounts to obscure its origin. This makes it extremely challenging for authorities to trace the path of the money.
But it doesn't stop there—these individuals create complex webs of fake companies and offshore accounts, making it even tougher to catch them. The alliance between tax evasion and money laundering presents a substantial hurdle for law enforcement. Addressing this problem requires global teamwork, sophisticated investigative tools, and stringent regulations to unravel these dubious financial networks and uphold the integrity of global financial systems.
Understanding the gravity of this offense, the methods employed, and the real-life examples is essential for businesses and individuals to stay compliant with tax laws. By staying informed and adhering to legal practices, it is possible to create a financially transparent environment that benefits society as a whole.
Credit Card Cloning
What is Card Cloning?
Card cloning, also known as skimming, is a method used by fraudsters to steal credit card information. It involves copying the data from a legitimate credit card and transferring it onto a duplicate card. The cloned card can then be used to make unauthorized purchases or withdrawals.
This malicious act is carried out by criminals who use various techniques to obtain card details, including installing skimming devices on ATMs or point-of-sale (POS) terminals, or capturing card information through software vulnerabilities.
Skimming devices are often designed to be discreet and blend in with the legitimate card reader, making them difficult for unsuspecting individuals to detect. These devices can capture the magnetic stripe data from the card as it is swiped, allowing fraudsters to create a replica of the card. Additionally, criminals may also use hidden cameras to record the PIN entered by the cardholder, further enabling them to access the victim's funds.
It is essential for consumers to remain vigilant when using their credit or debit cards, especially in public places where skimming devices may be present. Checking for any unusual attachments or loose parts on ATMs or POS terminals before conducting a transaction can help prevent falling victim to card cloning. Furthermore, regularly monitoring bank statements for any unauthorized transactions and promptly reporting any suspicious activity to the financial institution can aid in mitigating the impact of card fraud.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
How does Cloning Work?
Cloning, in the context of payment cards, is a devious technique that exploits vulnerabilities in the payment card system. It involves the replication of a card's data and its transfer onto a counterfeit card, which can then be used for fraudulent transactions. The intricate process behind card cloning is a fascinating blend of technology, cunning, and criminal ingenuity.
Magnetic Stripe
The traditional magnetic stripe, found on the back of credit cards, contains vital account information that facilitates transactions. Unfortunately, this magnetic stripe has proven to be a weak point in terms of security. Crafty criminals have devised various methods to exploit this vulnerability and obtain the sensitive data stored on the stripe.
One such method involves the use of skimming devices. These devices, cleverly disguised as legitimate card readers, are placed over the actual card reader at ATMs or payment terminals. When an unsuspecting victim swipes their card, the skimming device stealthily captures the magnetic stripe data, allowing the criminal to create a clone of the card.
To protect yourself against magnetic stripe cloning, it is crucial to remain vigilant and exercise caution when using ATMs or card terminals. If a device appears suspicious or tampered with, it is best to find an alternative means of making your transaction.
EMV Chip
EMV chips, also known as chip cards or smart cards, represent a more secure alternative to magnetic stripes. These tiny chips embedded within the card generate a unique code for each transaction, making it significantly more challenging for fraudsters to create counterfeit cards.
However, even the seemingly impenetrable EMV chips have not been entirely immune to the cunning tactics of criminals. Instances have arisen where these unscrupulous individuals have tampered with the chip reader or employed advanced techniques to extract the chip data. This serves as a reminder that, despite the enhanced security measures, it is essential to remain cautious and inspect card readers before using them.
Contactless Tap
In recent years, contactless payment methods, such as NFC-enabled cards or mobile wallets, have gained immense popularity. These convenient methods utilize radio frequency identification (RFID) technology to wirelessly transmit payment information, eliminating the need for physical contact between the card and the payment terminal.
While contactless payment offers a seamless and efficient experience, it is not entirely immune to cloning attempts. Resourceful criminals have developed specialized equipment capable of intercepting the communication between the card and the payment terminal. By doing so, they can clandestinely clone the card's data and exploit it for unauthorized transactions.
As the world of payment card technology continues to evolve, so do the methods employed by criminals seeking to exploit its vulnerabilities. Staying informed, exercising caution, and adopting best practices are essential in safeguarding ourselves against the ever-present threat of card cloning.
Cloning of Credit and Debit Cards
Credit and debit cards are both susceptible to cloning. The cloning process involves copying the card's data, including the card number, expiration date, and cardholder's name.
Once the data is obtained, criminals can encode it onto a blank card, creating an exact replica of the original. This cloned card can then be used to conduct fraudulent transactions or withdraw money from the cardholder's account.
It is important for cardholders to be vigilant and protect their cards from potential cloning attempts. One common method used by criminals to obtain card data is through skimming devices. These devices are often discreetly installed on legitimate card readers, such as ATMs or gas station pumps, to capture the card information when it is swiped.
Additionally, cardholders should regularly monitor their account activity for any unauthorized transactions and report any suspicious activity to their financial institution immediately. By staying informed and taking proactive measures, individuals can reduce the risk of falling victim to card cloning scams.
Use of Cloning for Fraud and Money Laundering
Cloning of credit and debit cards is not simply a means to make unauthorized purchases. It is often linked to more sophisticated criminal activities, such as fraud and money laundering.
Fraudsters use cloned cards to make high-value purchases, often targeting expensive electronics or luxury items. They can also use cloned cards to withdraw cash from ATMs, especially in regions with weaker security measures.
Moreover, criminals involved in money laundering may use cloned cards to transfer funds to different accounts, making it difficult to trace the origins of the illicit money.
Cloning technology has become increasingly advanced, allowing criminals to create near-perfect replicas of credit and debit cards. These cloned cards often contain stolen information obtained through data breaches or skimming devices installed on ATMs or point-of-sale terminals.
Furthermore, fraudsters may employ sophisticated techniques such as carding forums and online marketplaces to sell cloned card information to other criminals, creating a vast network of illicit transactions that span across borders and jurisdictions.
Statistics on Credit Card Cloning
The statistics on credit card cloning highlight the prevalence of this cybercrime in certain regions.
Credit card cloning, also known as skimming, is a serious issue that poses a threat to individuals' financial security. It involves the unauthorized copying of credit card information to create a duplicate card for fraudulent transactions. The rise of digital transactions has made it easier for cybercriminals to engage in such illegal activities, leading to significant financial losses for both consumers and financial institutions.
Singapore
- In 2019, there were over 2,000 reported cases of credit card fraud in Singapore, with an estimated loss of SGD 6.6 million.
- The majority of these cases involved card cloning or skimming.
- Authorities in Singapore have been actively working to combat credit card fraud through public awareness campaigns and enhanced security measures.
Singapore's proactive approach to tackling credit card fraud includes the implementation of advanced fraud detection technologies and collaboration with international law enforcement agencies to track down cybercriminals operating across borders. Additionally, financial institutions in Singapore regularly update their security protocols to stay ahead of evolving cyber threats, providing consumers with a safer digital payment environment.
Philippines
- In the Philippines, credit card fraud is also a significant concern, with a rising number of reported cases.
- In 2020, the Philippine National Police-Anti-Cybercrime Group recorded over 800 cases of credit card fraud.
- These cases involved various methods, including card cloning and online scams targeting credit card users.
- Law enforcement agencies in the Philippines continue to collaborate with financial institutions to investigate and prevent credit card cloning.
As the Philippines grapples with the increasing sophistication of cybercriminal tactics, efforts are being made to enhance cybersecurity awareness among the general public. Educational campaigns on safe online practices and the importance of securing personal financial information are being conducted to empower individuals to protect themselves from falling victim to credit card cloning schemes. Collaboration between government agencies, law enforcement, and the private sector remains crucial in the ongoing battle against cybercrime in the Philippines.
Tips to Safeguard Yourself Financially
To protect yourself from credit card cloning and financial fraud, it is crucial to adopt certain security measures.
In today's digital age, where online transactions and contactless payments are the norm, safeguarding your financial information is more important than ever. By being vigilant and proactive, you can reduce the risk of falling victim to fraudulent activities.
Opt for contactless payment
Consider using contactless payment methods, such as mobile wallets or cards with NFC technology. These methods are more secure than traditional magnetic stripe transactions. With contactless payments, your card information is encrypted, making it harder for fraudsters to intercept and misuse your data.
Furthermore, many contactless payment systems require biometric authentication or a unique PIN, adding an extra layer of security to your transactions.
Inspect any card reader you use
Before inserting your card into an ATM or POS terminal, inspect it for any suspicious attachments or signs of tampering. Criminals often install skimming devices or cameras to capture card details and PIN numbers. By being observant and checking for any irregularities, you can protect yourself from falling victim to such scams.
Additionally, when entering your PIN at an ATM or point-of-sale terminal, shield the keypad with your hand to prevent any potential onlookers from stealing your information.
Monitor your credit card account
Regularly review your credit card statements to identify any unauthorized transactions. If you notice any suspicious activity, report it to your bank immediately. By keeping track of your expenses and verifying each transaction, you can quickly spot any discrepancies and take swift action to address them.
Sign up for alerts
Many financial institutions offer transaction alerts via SMS or email. Enroll in these services to receive real-time notifications about any activity on your credit card. These alerts can help you stay informed about your account activity and promptly detect any unusual or unauthorized transactions.
Stick to bank ATMs
Whenever possible, use ATMs located within bank premises. These ATMs are typically more secure and less likely to be compromised by skimming devices. Avoid using standalone ATMs in secluded or poorly lit areas, as they are often targeted by fraudsters looking to install skimmers.
Additionally, consider using ATMs that are monitored by security cameras or security personnel, as these provide an added layer of protection against potential threats.
Use a chip reader
If a merchant offers the option to insert your card into a chip reader rather than swiping it, choose the chip reader. EMV chips provide an extra layer of security against cloning. Chip cards generate a unique code for each transaction, making it harder for fraudsters to replicate your card information and commit fraudulent activities.
By following these best practices and staying informed about the latest security measures, you can safeguard your financial information and protect yourself from potential threats in the digital landscape.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
What to do in Case Your Credit Card is Cloned?
If you suspect that your credit card has been cloned or compromised, it is important to take immediate action.
Contact your credit card issuer or bank and report the unauthorized transactions. They will guide you through the necessary steps to protect your account, such as canceling the cloned card and issuing a new one. Additionally, file a police report to document the incident and assist in any investigation.
Remember, staying informed and proactive is key to safeguarding yourself against the ever-evolving threats of credit card cloning.
Furthermore, it is advisable to monitor your credit card statements regularly for any unusual activity. By reviewing your transactions frequently, you can quickly spot any discrepancies and address them promptly. In addition, consider setting up transaction alerts on your account to receive notifications for every purchase made with your card, adding an extra layer of security.
In the event of credit card cloning, it is crucial to update your online account passwords and PIN numbers to prevent further unauthorized access. Choose strong, unique passwords for each account and enable two-factor authentication whenever possible. By strengthening your account security measures, you can reduce the risk of falling victim to fraudulent activities.
As you take steps to protect yourself from the threats of credit card cloning, remember that prevention is just as crucial as the response. Tookitaki's FinCense offers an innovative and comprehensive suite of anti-money laundering and fraud prevention tools designed for both fintechs and traditional banks. By integrating with the AFC Ecosystem and utilizing a federated learning model, FinCense delivers fewer, higher quality fraud alerts and enables real-time compliance with AML and Fraud regulations. From speeding up customer onboarding with our Onboarding Suite to enhancing investigation efficiency with our Case Manager, Tookitaki's FinCense is your ally in building a robust defense against financial crime. Don't let fraudsters outsmart your security measures. Talk to our experts today and stay one step ahead in the fight against credit card cloning and other financial threats.
Money Services Business
Introduction
In today's globalized world, Money Services Businesses (MSBs) play an increasingly pivotal role in facilitating financial transactions. This article will delve into the intricacies of MSBs, unpacking their functionalities, types, and associated benefits and risks. By understanding the MSB landscape, we can better appreciate its role in shaping the global financial ecosystem. Operating a legitimate money services business requires adherence to compliance governance and customer due diligence practices.
Key Takeaways
- Understanding the definition and purpose of MSBs
- Comprehending the functioning of MSBs
- Identifying different types of MSBs and their services
- Exploring the application and benefits of MSBs
- Recognizing the challenges and risks associated with MSBs
- Examining preventive measures and regulatory compliances
The Basics: Defining Money Services Businesses
Money Services Business: What Does It Mean?
A Money Services Business (MSB) is a legal term used to describe businesses that transmit or convert money. As financial intermediaries, they facilitate various financial services, including money transfers, currency exchange, and check cashing services.
The Role of MSBs
MSBs play a critical role in the global financial ecosystem by enabling financial transactions, particularly for individuals who may not have access to traditional banking services. They contribute significantly to financial inclusion, offering accessible and often cost-effective financial services.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Inside the MSB: A Look at the Mechanism
How Does an MSB Function?
An MSB functions as a financial intermediary, providing services that allow money to be transmitted or converted. This process involves receiving money from a customer, processing the transaction as per the service requested (for example, currency conversion or money transfer), and delivering the result, either to the customer or to a designated recipient.
Types of Money Services Businesses
Differentiating MSBs
MSBs offer a variety of services, often categorized into different types based on the nature of these services:
- Money Transmitters: These businesses transfer funds from one location to another, often globally.
- Currency Exchangers: They offer currency exchange services, converting one currency to another.
- Check Cashing Providers: These MSBs cash checks for customers, converting the written document into physical currency.
Use Cases and Advantages of MSBs
MSBs in Action
MSBs are critical in many situations, such as facilitating remittances for migrant workers, enabling tourists to convert currencies, or providing check cashing services for unbanked individuals. They promote financial inclusion by offering services that are accessible, easy to use, and often less expensive than traditional banks.
The Benefits of MSBs
MSBs offer several advantages, including accessibility for unbanked populations, convenience of service, and often lower transaction costs. They also contribute to the economy by enabling the flow of funds globally and domestically.
Challenges, Risks and Preventive Measures
Understanding the Risks
While MSBs offer significant benefits, they also pose risks, particularly concerning money laundering and financing terrorism. Their services can be misused to move illicit funds, posing regulatory and reputational risks.
Navigating the Challenges
To mitigate these risks, MSBs are subject to regulatory oversight and must adhere to strict anti-money laundering (AML) and counter-financing of terrorism (CFT) laws. They are required to implement robust AML programs, which include customer identification, transaction monitoring, and reporting suspicious activities.
Regulatory Compliance and MSBs
Adhering to Regulatory Standards
MSBs are obligated to follow various national and international regulations to ensure the legitimacy of their operations and prevent illicit activities. These include Know Your Customer (KYC) procedures, suspicious activity reporting, and maintaining detailed financial records.
Compliance: An Ongoing Effort
Compliance isn't a one-time affair. It requires constant updating and enforcement. For MSBs, this involves continuous monitoring of transactions, conducting regular audits, and periodically updating their compliance programs to keep up with regulatory changes.
Emerging Trends and the Future of MSBs
MSBs in a Digital World
With the advent of digital technologies, many MSBs have started to offer digital and mobile services, allowing users to transact anytime, anywhere. This digital transformation is not only making MSBs more convenient but also expanding their reach to previously unbanked or underbanked populations.
Future Outlook: Embracing Innovation
As the MSB sector continues to evolve, we can expect to see further innovation and growth. Emerging technologies like blockchain and artificial intelligence could provide new opportunities for MSBs, improving the efficiency and security of their services.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
The Importance of MSBs in Financial Ecosystem
The Indispensable Role of MSBs
MSBs play an essential role in the global financial ecosystem, providing services that traditional banking institutions often do not. They play a significant part in promoting financial inclusion, supporting the economic life of many people around the world.
Making a Difference: MSBs and Financial Inclusion
By offering accessible, cost-effective services, MSBs provide an essential lifeline for individuals without access to traditional banking. This is particularly evident in developing countries, where MSBs enable individuals to receive remittances, cash checks, and convert currencies.
Conclusion: A Thriving, Evolving Sector
The Money Services Business landscape is a dynamic, evolving sector that plays a crucial role in the world economy. As we move forward into an increasingly digital financial landscape, the importance of MSBs will likely continue to grow. Regulatory compliance, technological innovation, and a focus on financial inclusion will shape the future of the MSB sector, creating a thriving industry ready to meet the demands of the 21st-century economy.
Jurisdiction of Residence
The jurisdiction of residence plays a crucial role in determining an individual's or business's tax obligations. Whether you're an individual looking to understand how the Internal Revenue Service (IRS) determines residency or a business navigating tax implications in various jurisdictions, having a clear understanding of the concept is essential.
Determining a customer's jurisdiction of residence is vital for accurate tax reporting and complying with jurisdiction of citizenship regulations. In this article, we will explore the intricacies of the jurisdiction of residence, including factors that influence tax residency, source jurisdiction, tax country of residence, and the significance of principal place of residence in taxation.
Key Takeaways
- The jurisdiction of residence is a critical factor in determining tax obligations for individuals and businesses.
- The IRS uses various factors to determine an individual's tax residency, including the substantial presence test, green card test, and first-year choice.
- Source jurisdiction refers to the country or region where income is earned or generated and plays a role in determining tax obligations.
- Tax country of residence refers to the jurisdiction where an individual is considered a resident for tax purposes based on specific criteria, such as physical presence or domicile.
- Principal place of residence in taxation refers to the primary location where an individual or business conducts their economic activities, which can have tax implications.
- Understanding the jurisdiction of tax residence is crucial for individuals and businesses to comply with tax laws, avoid penalties, and effectively plan their tax strategies.
Factors Influencing Tax Residency
IRS Determination of Residency
The IRS employs specific tests to determine an individual's tax residency. The substantial presence test is based on the number of days an individual spends in the United States over a three-year period. The green card test applies to individuals who are lawful permanent residents. Additionally, the first-year choice allows individuals who meet specific criteria to be treated as U.S. residents for their first year of arrival.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Source Jurisdiction and Tax Obligations
Source jurisdiction refers to the country or region where income is earned or generated. When it comes to tax obligations, income derived from a particular source jurisdiction may be subject to taxation in that jurisdiction. Double taxation can occur if the same income is taxed by both the source jurisdiction and the jurisdiction of residence. To mitigate this, countries often have double taxation avoidance agreements in place.
Understanding Tax Country of Residence
Tax country of residence refers to the jurisdiction where an individual is considered a resident for tax purposes. The determination of tax residency is influenced by factors such as physical presence and domicile. Physical presence refers to the number of days an individual spends in a specific jurisdiction, while domicile relates to a person's permanent home. Tax treaties between countries may also impact the determination of tax country of residence.
Significance of Principal Place of Residence in Taxation
The principal place of residence plays a crucial role in taxation, particularly for individuals and businesses with activities in multiple jurisdictions. The principal place of residence refers to the primary location where an individual or business conducts their economic activities. It can have significant tax implications, as different jurisdictions may apply different tax rates and regulations. Properly identifying and understanding the principal place of residence is essential for accurate tax reporting and compliance.
Navigating Tax Obligations
Importance of Jurisdiction Codes and Tax Jurisdiction Lookup
Jurisdiction codes are alphanumeric codes that identify specific tax jurisdictions. These codes are used for administrative purposes and help determine the applicable tax laws and regulations for a particular location. Tax jurisdiction lookup tools assist individuals and businesses in finding the correct tax jurisdiction based on geographical or administrative boundaries. Accurately identifying the relevant tax jurisdiction is crucial for fulfilling tax obligations accurately.
Tax Considerations for International Students
International students face unique tax considerations, particularly in determining their country of tax residence. Factors such as the duration of stay, visa status, and tax treaties between countries come into play. Reporting requirements and potential implications on scholarships and grants further add complexity to the tax obligations of international students. Understanding these considerations is vital to ensure compliance with tax laws and avoid any potential penalties.
Tax Implications for H-1B Visa Holders
H-1B visa holders, as non-U.S. citizens working in the United States, face specific tax implications. They are subject to dual tax obligations, requiring compliance with tax laws both in their home country and the host country. Tax treaty benefits can help avoid double taxation, and understanding reporting requirements and compliance obligations is crucial. Proper tax planning can ensure H-1B visa holders optimize their tax situation while remaining compliant with tax laws.
Compliance and Reporting Requirements
Filing Tax Returns in the Relevant Jurisdictions
To meet tax obligations, individuals and businesses must file tax returns in the jurisdictions where they are deemed tax residents or have income-generating activities. Filing tax returns accurately and on time is essential to avoid penalties and maintain compliance with tax laws. Understanding the specific requirements and deadlines for each jurisdiction is crucial for fulfilling reporting obligations effectively.
Reporting Foreign Financial Accounts
Individuals and businesses with foreign financial accounts may have additional reporting requirements. The Foreign Account Tax Compliance Act (FATCA) requires certain individuals and entities to report their foreign financial accounts to the IRS. This includes filing FinCEN Form 114, also known as the Foreign Bank Account Report (FBAR), and disclosing information about the accounts, such as their location and maximum value. Compliance with these reporting requirements is essential to avoid penalties and ensure transparency in financial matters.
Common Mistakes to Avoid in Tax Reporting
When it comes to tax reporting, several common mistakes can lead to errors or omissions on tax returns. These mistakes include incorrect calculations, failure to report all sources of income, overlooking deductions and credits, and improper record-keeping. It is crucial to review tax returns thoroughly, seek professional advice if needed, and ensure accurate reporting to avoid potential audits or penalties.
Penalties and Consequences of Non-Compliance
Non-compliance with tax laws and reporting obligations can result in significant penalties and consequences. These penalties can include fines, interest charges, and even criminal charges in severe cases of tax evasion. It is vital to understand and fulfill all tax obligations to avoid these negative consequences and maintain a good standing with tax authorities.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Seeking Professional Guidance
Importance of Consulting Tax Professionals
Navigating the complexities of tax laws and obligations can be challenging for individuals and businesses. Seeking professional advice from tax professionals, such as certified public accountants (CPAs) or tax advisors, can provide valuable insights and guidance. Tax professionals have the expertise and knowledge to interpret tax laws, identify tax-saving opportunities, and ensure compliance with reporting requirements.
Working with International Tax Advisors
For individuals and businesses with international tax considerations, collaborating with international tax advisors is crucial. These advisors specialize in cross-border tax matters and possess in-depth knowledge of international tax laws, treaties, and compliance requirements. They can help individuals and businesses optimize their tax strategies, minimize tax liabilities, and navigate the complexities of international taxation.
Conclusion
Understanding the jurisdiction of residence and its impact on tax obligations is essential for individuals and businesses. Factors such as IRS determinations of residency, source jurisdiction, tax country of residence, and principal place of residence in taxation all play significant roles in determining tax liabilities and compliance requirements. Navigating tax obligations involves understanding jurisdiction codes, tax jurisdiction lookup tools, and complying with reporting requirements.
Seeking professional guidance, particularly from tax professionals with expertise in international taxation, can provide valuable assistance in managing tax responsibilities effectively. By staying informed and proactive in fulfilling tax obligations, individuals and businesses can ensure compliance with tax laws and optimize their tax situations.
Payment Screening
As we venture deeper into the digital era, the risk of fraudulent transactions and money laundering grows. To combat these risks, two crucial tools in the banking sector have emerged: payment screening and transaction monitoring. These twin pillars uphold the integrity of financial institutions and protect the banking ecosystem.
Implementing robust payment screening practices is essential to prevent fraudster activities, such as wire fraud and involvement in money laundering activities.
Key Takeaways
- Understanding the difference between payment screening and transaction monitoring
- Deciphering the purpose of screening in banking
- Exploring the role of payment transaction monitoring in AML
- Discovering the transaction screening process
What is Payment Screening?
Payment screening, a key component of the AML process, involves scrutinizing every payment made through a bank to ensure they are compliant with regulatory norms. The screening process verifies customer details against global databases and sanction lists, helping identify high-risk entities and preventing illegal fund transfers.
What is Transaction Monitoring?
Transaction monitoring, on the other hand, tracks and analyzes a customer's transactions over time. It seeks to identify patterns of behaviour that deviate from the norm and may indicate fraudulent activity. Transaction monitoring supports the detection of money laundering, terrorist financing, and other illicit financial activities.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Unravelling the Intricacies: Payment Screening vs Transaction Monitoring
While both payment screening and transaction monitoring play vital roles in AML compliance, they serve distinct purposes.
Payment Screening: A Preventive Shield
Payment screening functions as a preventive measure. By cross-referencing customer details with global databases and sanction lists, banks can promptly intercept suspicious transactions before they occur. It's like a checkpoint that every transaction must pass, ensuring that no illicit funds infiltrate the system.
Transaction Monitoring: A Detective Lens
Transaction monitoring, conversely, works like a detective, constantly scanning a customer's transaction history for anomalies. This process aids in identifying complex money laundering schemes that may initially evade detection, contributing to the bank's long-term security.
The Role of Name Screening in AML
Name screeninginvolves matching a customer's name against sanction lists and politically exposed persons (PEPs) databases. This process helps identify high-risk customers and fortify the bank's defence against potential financial crime.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
The Transaction Screening Process
Transaction screening encompasses several steps, including:
- Initial transaction monitoring, where customer transactions are observed in real time.
- Setting up alerts for any anomalies or suspicious patterns identified.
- Investigation and analysis of these alerts to discern whether they indicate illicit activity.
- Reporting suspicious transactions to regulatory authorities via Suspicious Activity Reports (SARs).
Conclusion
In an age where financial crime poses a growing threat, payment screening and transaction monitoring form the first line of defence for banks worldwide. By understanding their distinct roles and learning to deploy these tools effectively, financial institutions can uphold integrity, protect their customers, and contribute to a safer, more secure banking ecosystem.
Due Diligence
Introduction
A stitch in time saves nine. This old adage holds particularly true in the realm of financial transactions, business deals, and legal matters. Here, that crucial 'stitch' comes in the form of 'Due Diligence', a rigorous process that aids in making informed decisions. Thorough due diligence practices encompass enhanced due diligence, payment screening, and identity verification among others to prevent various financial crimes. The present article seeks to delve into the world of due diligence, its workings, types, and significant use cases.
Key Takeaways
- Due diligence is a meticulous process conducted to gather information, assess risks, and make informed decisions before entering into agreements or transactions.
- It involves thoroughly reviewing financial records, regulatory compliance, operational processes, and other relevant data to identify potential risks and benefits.
- The primary purpose of due diligence is to mitigate risks, ensure legal compliance, and contribute to effective decision-making by providing a detailed understanding of the matter at hand.
- There are various types of due diligence, including financial due diligence for assessing a company's financial health, legal due diligence for reviewing legal aspects, and operational due diligence for evaluating operational capabilities.
- Due diligence plays a crucial role in Mergers and Acquisitions (M&A) by helping acquirers understand the target company's value and structure the deal efficiently. It is also essential in real estate transactions for verifying ownership, assessing property conditions, and analyzing investment profitability.
- By conducting thorough due diligence, individuals and businesses can prevent unexpected surprises, minimize risks, and make informed decisions that align with their goals and protect their interests.
Due Diligence: A Crucial Prerequisite for Informed Decisions
Understanding Due Diligence
Due diligence is an investigative process carried out by individuals or businesses to confirm the facts and assess the potential risks before entering into an agreement or a transaction. It can involve a variety of tasks, such as reviewing financial records, understanding regulatory compliance, or examining the operational processes of a business.
The Underlying Rationale
The central premise of due diligence is the exercise of care that a reasonable person is expected to take before entering into an agreement or a contractual obligation. The process offers a detailed insight into the matter at hand, helping to mitigate risks, ensure legal compliance, and contribute to effective decision-making.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Inner Workings of Due Diligence
How it Unfolds
A typical due diligence process involves the collection and evaluation of comprehensive quantitative and qualitative data. The process starts with the identification of areas that require scrutiny. Relevant data are then collected from various sources, which are subsequently analyzed to identify potential risks and benefits, verifying the accuracy of the given information.
The Players Involved
The due diligence process often involves multiple stakeholders, including the party conducting the due diligence (buyer/investor), the party being examined (seller/business), and professionals like lawyers, accountants, and financial advisors who aid in the evaluation process.
Classifying Due Diligence: An Array of Types
Financial Due Diligence
Financial due diligence involves a thorough analysis of a company's financials, including assets, liabilities, income, and expenses. It serves to validate the company's financial health and growth prospects.
Legal Due Diligence
Legal due diligence entails the review of all legal aspects of a company. It includes assessing contracts, intellectual property, employment laws, and potential litigation.
Operational Due Diligence
Operational due diligence examines the operational aspects of a company, such as the quality of management, IT systems, and production capabilities. It aims to understand whether the company's operations can sustain and propel its business model.
Use Cases: The Due Diligence Difference
Due Diligence in Mergers and Acquisitions
In Mergers and Acquisitions (M&A), due diligence is a critical step that helps the acquirer understand the target company's value, reveal potential deal-breakers, and structure the deal efficiently.
Role in Real Estate Transactions
Due diligence is essential in real estate transactions. It involves verifying ownership, assessing property condition, reviewing zoning laws, and analyzing the profitability of the investment.
{{cta('f24d2361-d707-461c-b808-c29f64ebda60','justifycenter')}}
Prevention: Mitigating Risks through Due Diligence
Through careful evaluation of potential risks, due diligence acts as a preventive measure that mitigates risks. It minimizes the chances of encountering unexpected surprises post the agreement or transaction, thereby serving as an insurance policy against uninformed decision-making.
Looking ahead, we can anticipate that due diligence will increasingly leverage technology. With the advent of artificial intelligence and machine learning, future due diligence processes could become more streamlined, accurate, and efficient, shaping the future of informed decision-making.
The Indispensable Role of Due Diligence
In conclusion, due diligence is a crucial component in a myriad of fields, particularly where significant financial transactions or agreements are involved. It serves as a protective shield that ensures informed decision-making and minimizes risks associated with such dealings. By adopting a systematic approach to due diligence, businesses and individuals can safeguard their interests and make confident strides towards their goals.
Name Screening
In the ever-evolving landscape of financial transactions, the need for robust anti-money laundering (AML) measures has become paramount. Financial institutions face increasing regulatory requirements to prevent money laundering, terrorist financing, and other illicit activities. One essential component of AML and Know Your Customer (KYC) processes is name screening.
Thorough name screening procedures aid in identifying individuals associated with identity theft, wire fraud, or other illicit activities. This article delves into the world of name screening, exploring its importance, processes, regulations, and the significant role it plays in enhancing compliance and mitigating financial risks.
Understanding Name Screening in AML
Name screening plays a crucial role in the realm of anti-money laundering (AML) by helping financial institutions identify potential risks and comply with regulatory requirements. It is a process of cross-checking names against various databases and watchlists to detect any matches that may indicate a risk or legal restriction. By understanding the concept and importance of name screening, financial institutions can strengthen their AML efforts and contribute to a more secure financial system.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Definition and Importance of Name Screening
Name screening is a vital practice in AML that involves comparing names against databases and watchlists to identify individuals or entities associated with risks or legal restrictions. Its importance lies in the fact that it helps prevent money laundering, terrorist financing, fraud, and other financial crimes. By conducting thorough name screenings, financial institutions can ensure compliance with regulatory requirements and mitigate potential risks to their operations and reputation.
Types of Name Screening
There are different types of name screening that financial institutions may employ based on their specific needs and regulatory requirements. These include screening against government sanctions lists, politically exposed persons (PEPs) lists, internal watchlists, and adverse media databases. Each type of screening serves a distinct purpose in identifying different categories of risk, and a comprehensive screening approach may involve multiple types of screenings to ensure thorough risk assessment.
The purpose of conducting AML screening
AML screening is performed to fulfil three main objectives.
- Assessing risks
- Compliance with sanctions
- Safeguarding against regulatory penalties
Individuals listed on sanctions or other watchlists pose a significant risk to businesses, especially those identified as politically exposed persons (PEPs). PEPs have a higher propensity for engaging in financial crimes like corruption and bribery. As a result, banks and financial institutions are mandated to conduct thorough screenings of each customer to pinpoint high-risk profiles and avoid entering into transactions with them.
When is AML screening necessary?
Businesses must conduct AML screening of their customers in various scenarios.
- It is essential for companies to conduct AML screening not only during the account opening process but also regularly as the risk levels of customers can evolve over time.
- Additionally, AML screening should be integrated into the employment processes of businesses.
- It is also mandatory for companies to perform screening of the ultimate beneficial owner of any firm they engage with.
Conducting AML Screening
Name screening finds practical application in various aspects of financial institutions' operations, particularly in preventing money laundering, enhancing KYC processes, and mitigating fraud and financial crimes. By incorporating name screening into their workflows, financial institutions can strengthen their due diligence measures, identify potential risks associated with customers or transactions, and take appropriate actions to mitigate those risks.
To conduct AML screening, financial institutions must gather essential data such as the full name and date of birth of their clients. Subsequently, utilizing an AML screening solution such as Tookitaki's Smart Screening, the individual's name undergoes thorough screening against sanctions and watchlists to confirm no matches are found.
Use Cases of Name Screening
Name screening is extensively used to prevent money laundering and terrorist financing activities. By screening the names of customers, beneficiaries, and related parties against government sanctions lists and watchlists, financial institutions can identify individuals or entities with known links to illicit activities and take appropriate measures to prevent their involvement.
Enhancing KYC processes is another prominent use case for name screening. By conducting comprehensive screenings during customer onboarding, financial institutions can verify the identities of customers, assess their risk profiles, and ensure compliance with regulatory requirements. This enables institutions to better understand their customers, identify any potential red flags, and maintain a robust KYC framework.
Moreover, name screening plays a crucial role in mitigating fraud and other financial crimes. By cross-referencing names against adverse media databases and internal watchlists, financial institutions can identify individuals or entities associated with previous fraudulent activities or negative reputations. This helps in preventing fraudulent transactions, protecting the institution's assets, and maintaining trust with legitimate customers.
Best Practices for Effective Name Screening
To ensure the effectiveness of name screening processes, financial institutions should adhere to best practices that enable thorough and accurate screenings.
Conducting Comprehensive Name Screening
Financial institutions should conduct comprehensive name screenings that cover a wide range of data sources, including government sanctions lists, PEPs lists, internal watchlists, and adverse media databases. By incorporating multiple data sources, institutions can increase the chances of detecting potential risks and identifying individuals or entities with connections to illicit activities.
Utilizing Advanced Screening Technologies
Advanced screening technologies, such as automated screening software, can greatly enhance the efficiency and effectiveness of name-screening processes. These technologies utilize sophisticated algorithms and fuzzy matching techniques to accurately identify potential matches, even in cases of misspellings, aliases, or phonetic similarities. By leveraging these technologies, financial institutions can streamline their screening operations and reduce the risk of false negatives or false positives.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Implementing Risk-Based Approaches
A risk-based approach to name screening involves assessing the level of risk associated with each customer or transaction and applying appropriate screening measures accordingly. High-risk customers or transactions should undergo more rigorous and extensive screening processes, while low-risk cases can be subject to less stringent screening requirements. This approach allows institutions to allocate their resources effectively and focus on the areas of highest risk.
Regularly Updating Data Sources
Financial institutions should ensure that their data sources for name screening are up-to-date and regularly refreshed. Government sanctions lists, PEPs lists, and watchlists are constantly updated with new entries and revisions. By regularly updating their data sources, institutions can stay current with the latest information and improve the accuracy of their screening results.
Establishing Clear Policies and Procedures
Clear policies and procedures should be established to guide the name-screening process within financial institutions. These policies should outline the responsibilities of different stakeholders, the frequency of screenings, the escalation process for potential matches, and the actions to be taken in case of suspicious findings. Institutions can ensure consistency and standardization in their name screening practices by having well-defined policies and procedures.
Read More: Harnessing AML Screening Solutions for Compliance
Challenges and Considerations in Name Screening
While name screening is a crucial tool in AML efforts, there are several challenges and considerations that financial institutions should be aware of.
False Positives and False Negatives
One of the challenges in name screening is the possibility of false positivesand false negatives. False positives occur when a name match is flagged as suspicious, but upon further investigation, it is determined to be a false alarm. False negatives, on the other hand, happen when a potentially risky name is not identified during the screening process. Balancing the need for accurate identification of risks with minimizing false alarms is a continuous challenge for financial institutions.
Data Quality and Accuracy
The effectiveness of name screening heavily relies on the quality and accuracy of the data sources used. Inaccurate or incomplete data can lead to missed matches or false reassurances. Financial institutions should ensure the reliability and integrity of their data sources and consider using reputable providers or conducting periodic data quality assessments.
Cross-Border Considerations
In an increasingly globalized financial landscape, cross-border transactions pose additional challenges for name screening. Different jurisdictions may have varying sanctions lists or regulatory requirements, and the coordination of screening efforts across borders can be complex. Financial institutions should navigate these challenges by staying updated on international regulations, establishing partnerships or information-sharing agreements with relevant authorities, and implementing robust cross-border screening processes.
Privacy and Data Protection
Name screening involves the processing of personal data, and financial institutions must adhere to strict privacy and data protection regulations. Institutions should implement measures to safeguard customer information, ensure compliance with data protection laws, and obtain necessary consents and authorizations for data processing activities related to name screening.
Conclusion
Name screening plays a vital role in AML efforts by helping financial institutions identify potential risks, comply with regulatory requirements, and protect the integrity of the financial system. By understanding the concept and importance of name screening, institutions can effectively detect individuals or entities associated with money laundering, terrorist financing, and other illicit activities.
In conclusion, name screening is a critical component of AML efforts, enabling financial institutions to identify and mitigate potential risks. By implementing effective name-screening practices, institutions can contribute to a safer financial system, protect themselves from legal and reputational risks, and uphold their commitment to regulatory compliance and customer protection.
Sanctions Lists
Sanctions lists play a critical role in global compliance efforts, aiming to promote international security, deter illicit activities, and protect national interests. Among these lists, the Office of Foreign Assets Control (OFAC) sanctions list holds particular significance, especially in the United States.
Regular checks against sanctions lists are essential to prevent transactions related to bribery, corruption, or blackmail. This article provides an in-depth understanding of sanctions lists, with a focus on OFAC and its implications for global businesses. We will explore the types of sanctions, OFAC's role, and how organizations can navigate compliance requirements. Additionally, we will discuss the OFAC SDN list, UN sanctions list, and the process of conducting sanctions list searches.
Key Takeaways
- Sanctions lists serve as a vital tool to enforce international regulations and deter illicit activities.
- The Office of Foreign Assets Control (OFAC) sanctions list is crucial for compliance within the United States. OFAC maintains various sanctions lists, including the Specially Designated Nationals (SDN) list
- The four primary types of sanctions are diplomatic, economic, military, and trade restrictions.
- List-based sanctions involve the inclusion of individuals, entities, and countries on specific sanction lists.
- Conducting sanctions list searches is essential for organizations to ensure compliance and avoid engaging with sanctioned entities.
- The United Nations (UN) sanctions list complements OFAC's efforts and aims to promote global peace and security.
- Compliance with sanctions lists is critical for businesses to mitigate legal, financial, and reputational risks.
- Organizations can utilize advanced technology and compliance solutions to streamline sanctions list screening processes and enhance overall compliance.
Understanding Sanctions Lists: Promoting Global Security
Sanctions lists serve as powerful tools to promote global security and deter illicit activities. These lists are established by international bodies and regulatory authorities to impose restrictions on countries, entities, and individuals involved in activities deemed harmful or threatening. By implementing sanctions, nations aim to discourage behaviours such as terrorism, money laundering, weapons proliferation, and human rights violations.
Understanding the purpose and scope of sanctions lists is crucial for organizations to navigate the complex landscape of global compliance and contribute to a safer and more secure world.
Office of Foreign Assets Control (OFAC) Sanctions List
The Office of Foreign Assets Control (OFAC) sanctions list holds significant importance, particularly within the United States. OFAC is responsible for enforcing economic and trade sanctions imposed by the U.S. government. The OFAC sanctions list includes individuals, entities, vessels, and countries that are subject to various restrictions, including asset freezes, travel bans, and trade embargoes.
Compliance with OFAC regulations is essential for businesses operating within the U.S. jurisdiction to avoid engaging in transactions with sanctioned entities and to prevent legal and financial consequences.
Exploring the Four Types of Sanctions
Sanctions can take different forms, and understanding the four primary types of sanctions is crucial for compliance governance.
- Diplomatic sanctions involve the imposition of travel bans, diplomatic isolation, or limitations on diplomatic relations.
- Economic sanctions restrict financial transactions, trade, and investment activities with targeted entities or countries. Military sanctions involve embargoes on arms sales and military cooperation.
- Trade restrictions impose limitations on imports or exports of specific goods or services.
By comprehending the different types of sanctions, organizations can navigate compliance requirements effectively and ensure they are not inadvertently violating any restrictions.
List-Based Sanctions: Targeting Entities and Individuals
List-based sanctions are a common mechanism used to identify and target specific entities and individuals involved in illicit activities or posing a threat to national security. These lists include the names of designated individuals, organizations, vessels, or countries subject to various restrictions. Compliance with list-based sanctions requires organizations to screen their business partners, customers, and suppliers against these lists to ensure they are not engaging in prohibited activities. Maintaining updated and accurate information on list-based sanctions is crucial to prevent inadvertent association with sanctioned entities.
The OFAC SDN List: Identifying Designated Entities and Individuals
The Specially Designated Nationals (SDN) list maintained by OFAC is a vital component of the U.S. sanctions regime. The SDN list includes individuals, organizations, and entities considered to be engaged in activities contrary to U.S. national security or foreign policy interests. Being listed on the SDN list imposes severe restrictions, including asset freezes and prohibitions on engaging in financial transactions with U.S. persons or entities. Organizations must conduct thorough screening against the SDN list to ensure compliance with OFAC regulations and mitigate the risk of engaging with sanctioned parties.
UN Sanctions List: Collaborative Efforts for Global Peace and Security
In addition to national sanctions lists, the United Nations (UN) maintains its own sanctions list to foster global peace and security. The UN sanctions list aims to address threats to international peace and security, such as terrorism, arms proliferation, and violations of human rights. UN member states are obligated to implement and enforce these sanctions, which include asset freezes, travel bans, and arms embargoes.
Compliance with the UN sanctions list is essential for organizations with international operations to ensure they are not inadvertently supporting or engaging with entities or countries subject to UN sanctions.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Conducting Effective Sanctions List Searches
Conducting comprehensive sanctions list searches is a critical aspect of compliance governance to ensure organizations are aware of and can mitigate risks associated with sanctioned entities. Utilizing advanced technology and compliance tools, organizations can perform sanctions list searches to screen business partners, customers, and suppliers against various sanctions lists, including those maintained by OFAC and the UN.
These searches help identify potential matches and alerts organizations to take appropriate actions, such as conducting enhanced due diligence or refraining from engaging in transactions with sanctioned entities. Regular and thorough sanctions list searches are essential to maintain compliance, safeguard reputation, and mitigate the risk of financial and legal consequences.
Importance of Compliance with Sanctions
Compliance with sanctions lists is not only a legal obligation but also crucial for protecting an organization's reputation and maintaining trust among stakeholders. Failure to comply with sanctions regulations can result in severe penalties, including fines, loss of licenses, and damage to an organization's reputation. Non-compliance can also lead to restrictions on international trade and business relationships, hindering growth opportunities. By prioritizing compliance with sanctions lists, organizations demonstrate their commitment to ethical business practices, risk mitigation, and upholding international security and stability.
Read More: Common Challenges in Sanctions Screening
Navigating Complex Sanctions Landscapes: Expertise and Due Diligence
Given the intricate and constantly evolving nature of sanctions regimes, navigating complex sanctions landscapes requires expertise and due diligence. Organizations should establish robust compliance programs that include regular training, comprehensive risk assessments, and strong internal controls. It is essential to stay updated on regulatory changes, new sanctions designations, and emerging risks. Engaging qualified professionals with expertise in sanctions compliance can provide valuable guidance and support to ensure effective compliance governance.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Conclusion
Complying with sanctions lists is crucial for organizations operating in the global landscape. Understanding the intricacies of OFAC, UN, and list-based sanctions is essential to ensure adherence to international regulations and mitigate risks. By conducting thorough sanctions list searches, implementing robust compliance measures, and leveraging advanced technology, businesses can navigate the complex compliance landscape and protect themselves from legal and reputational repercussions. Embracing a proactive approach to sanctions list compliance is paramount for fostering trust, maintaining global partnerships, and contributing to a secure and compliant business environment.
Terrorist Financing
Terrorism remains a significant global concern, and one of the critical factors that fuels its activities is financing. Terrorist organizations rely on financial resources to sustain their operations, recruit members, and carry out devastating attacks. Understanding the concept of terrorist financing is vital for combating this threat effectively.
Financial institutions play a crucial role in preventing terrorist financing by maintaining strong payment screening practices. This article aims to shed light on the complex nature of terrorist financing, providing insights into examples, key features, and the distinction between terrorist financing and money laundering. By unraveling these intricacies, we can develop a deeper understanding of the threat landscape and strengthen our efforts to combat terrorism.
Key Takeaways
- Terrorist financing is the process of providing financial support to terrorist organizations.
- Examples of terrorist financing include illicit donations, trade-based money laundering, and exploitation of charitable organizations.
- Key features of terrorist financing include source diversity, use of informal financial systems, and layering and integration techniques.
- Terrorist financing differs from money laundering in terms of motives, legal frameworks, end use of funds, and reversibility of the process.
- Combating terrorist financing requires international cooperation, robust regulatory measures, technological innovations, and public awareness initiatives.
What is Terrorist Financing?
Terrorist financing refers to the process of providing financial resources or support to terrorist organizations or individuals involved in terrorist activities. It involves the movement and management of funds to facilitate terrorist acts, including recruitment, training, weapons procurement, and operational logistics. Terrorist financing encompasses a range of activities, from soliciting donations from sympathetic individuals to engaging in illicit financial transactions and exploiting legitimate financial systems.
Examples of Terrorist Financing
Examples of terrorist financing vary widely and can include both legal and illegal sources. One common example is the exploitation of charitable organizations, where funds raised for humanitarian purposes are diverted to support terrorist activities. Trade-based money laundering, involving the manipulation of international trade transactions, is another method used to finance terrorism. Additionally, the use of illicit donations, kidnapping for ransom, and involvement in illegal activities such as drug trafficking and smuggling are frequently employed to generate funds for terrorist organizations.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Key Features of Terrorist Financing
Terrorist financing exhibits several key features that distinguish it from other forms of illicit financial activities. Source diversity is a crucial aspect, as terrorist organizations often rely on a variety of funding sources to minimize detection and disruption. The use of informal financial systems, such as hawala networks or underground banking, enables funds to be moved covertly and outside the purview of traditional financial institutions. Layering and integration techniques, involving multiple transactions and complex financial structures, are employed to obfuscate the origin and destination of funds, making it challenging to trace and identify the sources of financing.
Source Diversity
Terrorist financing sources can range from legitimate sources, such as donations from sympathizers or state sponsors, to illicit activities like drug trafficking, arms smuggling, and extortion. The diverse nature of these funding sources helps terrorist organizations avoid dependency on a single channel and reduces the risk of detection by authorities. They may exploit legal businesses, charities, or even engage in legitimate employment to camouflage their illicit activities and create a facade of legitimacy.
Use of Informal Financial Systems
Informal financial systems, such as hawala or hundi, play a significant role in terrorist financing. These systems operate outside the traditional banking sector and rely on trust and networks of brokers to facilitate money transfers. Hawala transfers involve the movement of funds without physically crossing borders, making them difficult to track. Terrorist organizations exploit these networks due to their speed, low cost, and ability to operate in regions with limited or weak regulatory oversight, allowing them to move funds globally with minimal scrutiny.
Layering and Integration
Layering and integration are techniques used to disguise the origin and ownership of funds involved in terrorist financing. Layering involves conducting multiple transactions through different accounts and financial institutions to complicate the money trail. Funds are moved across various jurisdictions, making it challenging for authorities to trace the path and identify the true source. Integration involves merging illicit funds with legitimate economic activities, such as investments in businesses or real estate, to legitimize the proceeds and further obscure their origin.
Understanding the Difference: Terrorist Financing vs. Money Laundering
Terrorist financing and money laundering are distinct but interconnected processes. While both involve the movement of illicit funds, they differ in their purpose and the underlying criminal activities. Terrorist financing specifically aims to provide financial support to terrorist organizations or individuals involved in terrorism, while money laundering focuses on concealing the true origin of proceeds derived from various criminal activities. The primary distinction lies in the motives, legal frameworks, end use of funds, and the potential for reversibility of the process.
Motives and Objectives
The motives behind terrorist financing are ideological or political in nature, aimed at promoting a specific cause or ideology through acts of violence. In contrast, money laundering is driven by financial gain and seeks to legitimize illicit proceeds by making them appear as if they come from legitimate sources.
Legal Frameworks
Terrorist financing and money laundering are addressed by separate legal frameworks, although there are overlaps in some aspects. International conventions, such as the United Nations Security Council resolutions and the Financial Action Task Force (FATF) recommendations, provide guidance and standards for combating both terrorist financing and money laundering. However, there are specific regulations and laws dedicated to each crime, recognizing their unique characteristics and the need for targeted measures to prevent and detect them.
End Use of Funds
The end use of funds distinguishes terrorist financing from money laundering. Terrorist financing aims to provide financial resources for terrorist acts, including the planning and execution of attacks, recruitment and training of individuals, and the logistical support required for these activities. Money laundering, on the other hand, focuses on disguising the illicit origin of funds and integrating them into the legitimate economy, without necessarily having a specific purpose tied to terrorism or violent acts.
Reversibility
While money laundering involves the process of reversing the trail of illicit funds to make them appear legitimate, terrorist financing generally lacks this reversibility. Funds used for terrorist activities are typically directed towards their intended purpose and are unlikely to be reintegrated into the legal financial system. This distinction highlights the unique challenge of preventing terrorist financing, as once funds have been used for terrorism, they often cannot be "cleaned" or reclaimed for legitimate purposes.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Is Terrorism Financing the Same as Reverse Money Laundering?
Terrorism financing and reverse money laundering are not the same, although they share some similarities in terms of the movement of funds. Terrorism financing refers specifically to the act of providing financial support to terrorist activities, while reverse money laundering refers to the process of making legitimate funds appear illicit.
Reverse money laundering is often associated with attempts to disguise the proceeds of legal activities as illegal, with the aim of evading taxes or circumventing financial regulations. In contrast, terrorism financing involves the deliberate use of funds to support acts of violence and terrorism.
Conclusion
Terrorist financing poses a significant threat to global security, as it enables terrorist organizations to carry out their operations by providing them with the necessary financial resources. The diverse sources of funding, use of informal financial systems, and the techniques employed to disguise the origin of funds make detecting and combating terrorist financing a complex challenge.
Understanding the key features and differences between terrorist financing and money laundering is crucial for developing effective strategies and regulatory measures to disrupt the financial networks that support terrorism. By enhancing international cooperation, implementing robust legal frameworks, and leveraging advanced technologies, authorities and financial institutions can work together to detect, prevent, and deter terrorist financing, contributing to the global fight against terrorism.
Identity Verification
Identity verification is a crucial process that ensures individuals are accurately identified and their personal information is secure. In this article, we will delve into the concept of identity verification, its significance in various contexts, the different methods used for verifying personal identity, and the rise of online identity verification services. Strong identity verification processes are crucial for preventing identity theft, phishing, and other forms of fraudster activities. By understanding the importance of identity verification, individuals and organizations can enhance security and prevent fraudulent activities.
Key Takeaways
- Identity verification is the process of confirming an individual's identity and is crucial for preventing fraud and ensuring trust.
- Methods for identity verification include document-based verification, biometric verification, knowledge-based verification, and two-factor authentication.
- Online identity verification services provide secure and convenient methods for verifying identity remotely.
- Identity verification companies offer solutions tailored to specific industries and use cases.
- Free identity verification services are available online, but caution should be exercised when choosing platforms to protect personal information.
- Different types of identity verification cater to varying levels of security requirements.
Understanding Identity Verification
Identity verification is a crucial aspect of modern-day life, particularly in the digital age where online transactions are the norm. The process of verifying someone's identity is multifaceted and involves a range of techniques and technologies. One of the most common methods involves verifying personal information such as name, date of birth, and address, and cross-referencing it with public records and databases. Other techniques may include biometric verification such as fingerprint or facial recognition, or the use of security questions to confirm an individual's identity.
Regardless of the method used, the primary aim of identity verification is to establish trust and prevent identity theft or fraudulent activities. With the rise of cybercrime and online fraud, identity verification has become essential in safeguarding personal and financial information. Thankfully, many reliable and secure online identity verification services are available today, providing a convenient and efficient means of verifying identity remotely.
{{cta('a862d50f-c12a-43f6-9dd1-25a35e1fae85','justifycenter')}}
Importance of Identity Verification
Identity verification is a fundamental aspect of modern life, serving as a critical tool for safeguarding personal and financial information. It is central to various scenarios, including financial transactions, employment screening, regulatory compliance, and age verification for age-restricted products or services. Identity verification services help individuals, organizations, and online platforms establish trust and prevent identity-related risks and fraud.
In the digital age, where online transactions are the norm, identity verification has become even more critical. The rise of cybercrime and online fraud makes it essential to ensure that individuals are who they claim to be. Fortunately, there are reliable and secure online identity verification services available today, providing convenient and efficient means of verifying identities remotely.
The importance of identity verification cannot be overstated, as it helps protect both individuals and organizations from identity-related risks and fraud. By verifying an individual's identity, organizations can reduce the risk of financial loss, reputational damage, and legal exposure. Moreover, it helps establish trust, which is crucial for creating long-term relationships with customers and other stakeholders. There are identity verification requirements in the area of AML compliance too.
Therefore, it is crucial to emphasize the significance of identity verification in all relevant scenarios. Whether it is for online transactions, employment screening, or regulatory compliance, identity verification is essential for ensuring safety, security, and trust.
Methods for Verifying Personal Identity
- Document-based Verification: This method involves verifying personal identity using official documents such as passports, driver's licenses, or national identification cards.
- Biometric Verification: Biometric identity verification uses unique physical or behavioural characteristics, such as fingerprints, facial recognition, or voice recognition, to confirm an individual's identity.
- Knowledge-based Verification: Knowledge-based verification relies on asking specific questions that only the individual would know the answers to, such as personal details or historical information.
- Two-Factor Authentication (2FA): Two-factor authentication combines multiple identity verification methods to enhance security, such as a password and a unique verification code sent to a registered device.
Online Identity Verification
With the increasing prevalence of online transactions, the need for secure and reliable online identity verification services has grown exponentially. These services utilize a range of advanced methods to confirm an individual's identity remotely, including document verification, facial recognition, and database checks. Online identity verification companies offer tailored solutions for specific industries and use cases, ensuring the highest level of security and convenience for their customers.
Document verification involves the use of official identification documents such as passports, driver's licenses, or national identification cards to confirm an individual's identity. Biometric verification, on the other hand, uses unique physical or behavioural characteristics such as fingerprints, facial recognition or voice recognition to verify identity. Knowledge-based verification relies on asking specific questions that only the individual would know the answers to, such as personal details or historical information. Two-factor authentication combines multiple identity verification methods, such as a password and a unique verification code sent to a registered device, to enhance security.
Online identity verification services have proven to be convenient and efficient, providing individuals and organizations with a secure means of verifying identity remotely. However, caution should be exercised when choosing a platform to protect personal information. Free identity verification services are available online, but they may not offer the same level of security and reliability as paid services. It is crucial to choose a reputable and trusted online identity verification service to ensure the protection of personal and financial information.
Types of Identity Verification
Identity verification is not a one-size-fits-all solution, as different scenarios require varying levels of security and assurance. Basic identity verification is often sufficient for low-risk transactions, such as accessing basic services or opening a social media account. Enhanced identity verification, on the other hand, involves additional document checks and may be required for more sensitive transactions, such as applying for a loan or opening a bank account.
For high-security applications, such as border control or national security, identity verification must meet the highest level of assurance. This may involve multiple layers of verification, including biometric identification and background checks. Furthermore, identity verification may also vary depending on the industry or use case, with specialized solutions tailored to meet specific requirements.
Regardless of the scenario, identity verification is crucial in ensuring safety, security, and trust. By verifying an individual's identity, organizations can reduce the risk of financial loss, reputational damage, and legal exposure, while also protecting personal and financial information. With the availability of reliable and secure online identity verification services, verifying identity remotely has become more convenient and efficient than ever before.
Identity Verification Companies and Solutions
Identity verification services are increasingly being implemented by various companies across different industries to ensure compliance with regulations and enhance user security. Companies like Binance and Roblox have recognized the importance of establishing trust and preventing identity-related risks and fraud, and have therefore integrated identity verification measures into their platforms.
Binance, a cryptocurrency exchange platform, has implemented a strict Know Your Customer (KYC) policy to verify the identity of its users and prevent fraudulent activities. Users are required to submit official identification documents and undergo biometric verification, ensuring that only legitimate users can access the platform's services.
Roblox, a popular online gaming platform, has also implemented identity verification measures to protect its young user base. The platform has introduced a parental consent system, requiring parents or guardians to verify their identity and provide consent for their children to access certain features.
These companies are just a few examples of the diverse range of industries and use cases that can benefit from identity verification services. By establishing trust and preventing identity-related risks and fraud, identity verification helps protect individuals and organizations alike, providing a secure and reliable means of verifying identity remotely.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Free Identity Verification Online
While free identity verification services may seem like an attractive option, it is crucial to exercise caution when choosing a platform. Not all free services offer the same level of security and reliability as paid services, and some may even pose a risk to personal and financial information. It is important to choose a reputable and trusted platform to ensure the protection of sensitive information. Additionally, it is essential to read the terms and conditions carefully and understand how the platform handles personal data.
Overall, while free identity verification services may be a convenient option, it is crucial to prioritize security and choose a platform that can guarantee the highest level of protection for personal and financial information.
Conclusion
Identity verification is a vital aspect of personal and online security. By adopting robust identity verification methods and leveraging trusted online identity verification services, individuals and organizations can enhance trust, protect against identity theft, and ensure compliance with regulatory standards. Understanding the different methods and platforms available for identity verification empowers individuals to make informed decisions and safeguard their personal information in an increasingly digital world.
Phishing
Introduction
In today's digital age, phishing attacks have become increasingly prevalent and sophisticated. Phishing is a deceptive technique used by cybercriminals to trick individuals into revealing their sensitive information, such as login credentials, financial details, or personal data.
In this article, we will explore the concept of phishing, understand its various forms, examine real-life examples, and provide practical tips to prevent falling victim to these malicious attacks.
Key Takeaways
- Phishing attacks are deceptive techniques used by cybercriminals to trick individuals into revealing sensitive information.
- Different types of phishing attacks include email phishing, spear phishing, smishing, vishing, and whaling.
- Learning from real-life phishing examples can help individuals and organizations understand the tactics employed by attackers.
- Preventing phishing attacks requires strengthening cybersecurity awareness, verifying the legitimacy of emails and websites, avoiding clicking on suspicious links, keeping software updated, and implementing two-factor authentication (2FA).
Understanding Phishing: Unmasking the Threat
Insider trading involves buying or selling a publicly traded company's securities based on material, non-public information about the company. In many jurisdictions, this practice is illegal as it undermines investor confidence and disrupts market integrity.
Types of Phishing Attacks: Recognizing the Tactics
- Email Phishing: The most common form of phishing, attackers send deceptive emails that appear to be from legitimate sources. These emails typically contain links to fake websites or malicious attachments designed to collect sensitive information.
- Spear Phishing: This targeted phishing technique involves personalized messages sent to specific individuals or organizations. Attackers gather detailed information about their targets to create convincing emails tailored to their interests or roles.
- Smishing (SMS Phishing): In this type of attack, phishing messages are sent via SMS or text messages. Victims are often tricked into clicking on malicious links or sharing personal information by responding to seemingly urgent or important messages.
- Vishing (Voice Phishing): Vishing involves phone calls from scammers posing as trusted individuals or institutions. They use social engineering techniques to convince victims to disclose confidential information or perform certain actions.
- Whaling: Whaling targets high-profile individuals or senior executives within organizations. Attackers tailor their phishing attempts to exploit their positions and authority to gain access to sensitive data or financial resources.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Real-Life Phishing Examples: Learning from Notorious Cases
Examining real-life phishing examples can provide insights into the sophistication of these attacks and the potential consequences for victims. Notable cases include the phishing attack on Yahoo in 2014, where cybercriminals gained access to user accounts, compromising millions of personal records. Another example is the "CEO fraud" phishing scam, where attackers impersonate company executives to trick employees into transferring funds to fraudulent accounts.
How to Prevent Phishing Attacks: Essential Strategies
- Strengthening Cybersecurity Awareness: Educate yourself and your organization about phishing threats, common tactics used by attackers, and the importance of vigilance in detecting and avoiding phishing attempts.
- Verifying the Legitimacy of Emails and Websites: Be cautious when opening emails or clicking on links. Verify the sender's email address and check for signs of suspicious or misspelt domain names. Hover over hyperlinks to preview the URL before clicking.
- Avoiding Clicking on Suspicious Links: Exercise caution when encountering unfamiliar or unexpected links. Be wary of unsolicited requests for personal information or urgent actions. Instead of clicking on the provided link, manually enter the website address into your browser.
- Keeping Software and Devices Updated: Regularly update your operating systems, applications, and antivirus software to ensure you have the latest security patches and protection against known vulnerabilities.
- Implementing Two-Factor Authentication (2FA): Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a unique code sent to your mobile device, in addition to your password.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
By being proactive, vigilant, and adopting best practices to protect yourself against phishing attacks, you can significantly reduce the risks of falling victim to these malicious activities.
Neobanking
The banking landscape has experienced a significant transformation with the emergence of neobanking. Neobanks, also known as digital banks or challenger banks, are innovative financial institutions that operate entirely online. They offer a range of banking services through user-friendly mobile applications, challenging the traditional brick-and-mortar banking model. The rise of neobanking platforms emphasizes the need for strong compliance governance and know your customer (KYC) practices to prevent issues like money laundering.
In this article, we will delve into the concept of neobanking, explore different types of neobanks, examine the biggest players in the industry, discuss the distinction between neobanks and digital banks, and shed light on how neobanking is revolutionizing banking for small and medium-sized enterprises (SMEs).
Key Takeaways
- Neobanking is revolutionizing the banking industry, offering seamless digital experiences through mobile applications.
- Neobanks cater to diverse customer segments, including individuals, SMEs, and specific industries.
- Leading neobanks globally include Chime, Varo, Aspiration, Current and Revolut.
- Neobanks differentiate themselves from digital banks through their exclusive digital presence and customer-centric approach.
- Neobanking is empowering SMEs with tailored financial services, simplified processes, and real-time insights, allowing them to focus on business growth.
Understanding Neobanking: A Digital Banking Revolution
Neobanking is a disruptive force in the banking industry, reshaping the way individuals and businesses interact with financial services. Unlike traditional banks, neobanks operate solely online, leveraging advanced technology to deliver seamless, user-centric banking experiences. Neobanks provide a wide range of financial services through intuitive mobile applications, including account management, payments, savings, lending, and more.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Types of Neobanking: Tailored Solutions for Diverse Needs
Neobanks cater to various customer segments and offer tailored solutions to meet their specific needs. Let's explore some common types of neobanks:
- Neobanks for Individuals: These neobanks focus on providing convenient and customer-centric banking services to individual consumers. They offer features like easy account setup, budgeting tools, automated savings, and personalized financial insights.
- Neobanks for SMEs: Neobanks are also revolutionizing banking for small and medium-sized enterprises. SME neobanks provide specialized financial services tailored to the unique requirements of small businesses. These services may include seamless payment processing, invoicing, expense management, lending, and real-time financial analytics.
- Neobanks for Specific Industries: Some neobanks target specific industries, such as freelancers, gig economy workers, or international travellers. These neobanks design their services to address these niche customer segments' specific financial needs and pain points.
The Biggest Neobanks: Leading the Digital Banking Revolution
The neobanking sector is rapidly growing, with several key players leading the digital banking revolution. Here are some of the biggest neobanks globally:
- Chime: Chime is a US-based neobank founded in 2013. It boasts over 12 million customers and offers mobile-only banking services, including checking and savings accounts without monthly fees.
- Varo: Varo is another prominent US neobank with approximately 5.4 million account holders. It provides a range of financial services, including checking and savings accounts.
- Current: Current is a US neobank that has gained popularity with around 4.6 million account holders. It offers mobile banking solutions and accounts tailored for teens and young adults.
- Aspiration: Aspiration, based in the United States, is recognized as one of the largest neobanks, serving millions of customers. It provides banking and investment services with a focus on sustainability and social impact.
- Revolut: Revolut is a UK-based neobank that has expanded globally and gained a significant user base. It offers various financial services, including multi-currency accounts, international money transfers, and cryptocurrency trading.
These neobanks have gained significant market share and customer trust by offering innovative solutions, exceptional user experiences, and competitive pricing.
Neobank vs. Digital Bank: What Sets Neobanks Apart?
While neobanks and digital banks share similarities, there are some key distinctions between the two. Neobanks are exclusively digital and typically operate without any physical branches. They leverage technology to provide seamless and personalized experiences to customers. On the other hand, digital banks are often traditional banks that have expanded their services to include online platforms, retaining some physical branches alongside their digital offerings.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Neobanking for SMEs: Empowering Small Businesses
Neobanking is transforming the banking landscape for SMEs by addressing their unique challenges and offering tailored solutions. SME neobanks provide efficient and cost-effective banking services that enable small businesses to manage their finances effectively. With streamlined processes, simplified lending, and real-time financial insights, SME neobanks empower entrepreneurs to focus on growing their businesses while leaving the banking complexities to the experts.
As neobanking continues to reshape the banking landscape, customers are benefiting from enhanced convenience, personalized experiences, and innovative financial solutions. Whether it's individuals seeking seamless banking experiences or SMEs looking for specialized services, neobanks are paving the way for a digital banking revolution.
Compliance Governance
Compliance governance plays a pivotal role in ensuring organizations adhere to regulatory requirements, mitigate risks, and maintain ethical practices. By establishing robust frameworks and structures, businesses can effectively manage governance, risk, and compliance (GRC) activities. Effective compliance governance involves regular assessments of operational risk, including vulnerabilities to phishing.
This article provides valuable insights into the governance function in compliance, the distinction between governance and compliance, and the importance of a compliance governance framework.
Additionally, it explores the integration of GRC, job descriptions in the field, certifications, cybersecurity considerations, and examples of governance risks. By embracing compliance governance, organizations can foster a culture of integrity and accountability while safeguarding their reputation and long-term sustainability.
Key Takeaways
- Governance function in compliance focuses on establishing policies, procedures, and controls to ensure regulatory compliance and ethical conduct within an organization.
- Governance and compliance are interconnected but distinct concepts. Governance refers to the overall management and oversight of an organization, while compliance focuses specifically on adherence to laws, regulations, and industry standards.
- A compliance governance framework provides a structured approach to managing compliance activities, including risk assessment, policy development, training, monitoring, and reporting.
- Integrating governance, risk management, and compliance activities (GRC) enables organizations to streamline processes, enhance decision-making, and improve overall operational efficiency.
- Cybersecurity is an integral aspect of compliance governance, as organizations need to protect sensitive data, prevent data breaches, and comply with data privacy regulations.
- Governance risks can manifest in various forms, such as conflicts of interest, inadequate oversight, non-compliance, and reputational damage. Identifying and managing these risks is essential for effective governance and risk mitigation.
Understanding the Governance Function in Compliance
The governance function in compliance is responsible for establishing and maintaining policies, procedures, and controls that ensure an organization's adherence to regulatory requirements, industry standards, and ethical practices. It involves developing a robust compliance framework, defining accountability structures, and monitoring compliance activities. By understanding the governance function in compliance, organizations can effectively manage risks, promote transparency, and foster a culture of integrity.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Differentiating Governance and Compliance: Exploring Their Roles
Governance and compliance are interrelated concepts but serve distinct roles within an organization. Governance refers to the overall management and oversight of the organization, including strategic decision-making, setting objectives, and defining policies. On the other hand, compliance focuses specifically on adherence to laws, regulations, and industry standards. While governance sets the direction and framework, compliance ensures that the organization operates within legal and ethical boundaries.
The Significance of a Compliance Governance Framework
A compliance governance framework provides a structured approach to managing compliance activities within an organization. It outlines the policies, procedures, and controls necessary to achieve compliance objectives. This framework includes risk assessment processes, policy development and communication, training programs, monitoring and reporting mechanisms, and a remediation and continuous improvement system.
A well-designed compliance governance framework enables organizations to proactively identify and address compliance risks, promote consistency across departments, and demonstrate a commitment to regulatory compliance.
Integration of Governance, Risk, and Compliance (GRC)
The integration of governance, risk, and compliance activities, often referred to as GRC, aims to streamline processes and enhance overall organizational efficiency. By combining these three components, organizations can effectively identify, assess, and mitigate risks, align strategies with compliance requirements, and optimize resource allocation. GRC integration promotes a holistic approach to managing governance, risk, and compliance, enabling organizations to make informed decisions, improve accountability, and proactively respond to regulatory changes.
Job Descriptions in Governance, Risk, and Compliance
The field of governance, risk, and compliance offers diverse job opportunities for professionals with specialized expertise. Job descriptions in this field vary and may include compliance officers, risk managers, governance specialists, internal auditors, and legal advisors. These professionals play a crucial role in ensuring organizational compliance, managing risk exposure, conducting audits, developing compliance programs, and providing guidance on regulatory matters. Job descriptions often require a combination of skills such as knowledge of relevant regulations, strong analytical abilities, effective communication, and the ability to navigate complex organizational structures.
Certifications in Governance, Risk, and Compliance
Certifications in governance, risk, and compliance demonstrate expertise and a commitment to professional development in the field. Various organizations offer certifications that validate individuals' knowledge and skills in areas such as compliance management, risk assessment, ethics, and governance practices. These certifications not only enhance credibility but also provide individuals with a competitive edge in the job market and open doors to career advancement opportunities.
Cybersecurity Considerations in Compliance Governance
In the digital age, cybersecurity has become an integral aspect of compliance governance. Organizations must protect sensitive data, prevent data breaches, and comply with data privacy regulations. Compliance governance frameworks should include robust cybersecurity measures, such as secure information systems, regular vulnerability assessments, data encryption, employee awareness training, and incident response plans. By integrating cybersecurity into compliance governance, organizations can safeguard their data assets, maintain customer trust, and mitigate cybersecurity risks.
Examples of Governance Risks: Identifying and Mitigating Challenges
Governance risks can manifest in various forms and pose challenges to organizations. Examples include conflicts of interest, inadequate oversight, non-compliance with regulations, reputational damage, and unethical behaviour. It is crucial for organizations to identify and assess these risks, implement appropriate controls and processes, and establish mechanisms for monitoring and mitigating governance risks. By addressing these challenges, organizations can strengthen their governance practices, maintain stakeholder confidence, and mitigate potential negative impacts.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
The Role of Governance, Risk, and Compliance in Ensuring Ethical Practices
Governance, risk, and compliance (GRC) play a pivotal role in fostering ethical practices within organizations. By establishing transparent governance structures, assessing and managing risks, and complying with relevant laws and regulations, organizations can create an environment that promotes integrity and ethical behaviour. GRC frameworks provide the necessary guidelines and mechanisms to prevent fraud, corruption, and other unethical activities. This helps organizations build trust with stakeholders, protect their reputations, and contribute to sustainable business practices.
Compliance Governance Salary: Factors and Considerations
The salary range for professionals working in compliance governance can vary depending on various factors. These factors include the level of expertise and experience, the size and industry of the organization, the geographical location, and the specific responsibilities of the role. Professionals with specialized certifications and advanced knowledge in governance, risk, and compliance may command higher salaries. Additionally, organizations that prioritize compliance and risk management as strategic priorities tend to offer competitive compensation packages to attract top talent in the field.
By understanding the importance of compliance governance and its various components, organizations can establish effective frameworks, mitigate risks, and foster a culture of integrity and ethical practices.
Optical Character Recognition
In the digital age, where data is paramount, Optical Character Recognition (OCR) emerges as a pivotal technology, bridging the gap between data extraction and actionable insights. As financial institutions grapple with the complexities of ensuring compliance while safeguarding against illicit activities, OCR provides the path towards enhanced data accuracy, streamlined operations, and fortified defence mechanisms against financial crimes.
This article delves into the meaning of OCR, exploring its integral role in Know Your Customer (KYC) processes and Anti-Money Laundering (AML) risk assessments. It will also unravel the intricacies, applications, and challenges of OCR in the financial landscape.
Key Takeaways
- Optical Character Recognition (OCR) plays a crucial role in enhancing Know Your Customer (KYC) processes by accurately extracting data from documents, ensuring streamlined and compliant operations.
- While OCR offers numerous advantages in data extraction and verification, it presents challenges such as dependency on document quality and ensuring the security of the extracted data.
- Implementing strategic solutions, such as additional data verification steps and utilizing advanced OCR technologies, can navigate through OCR-related challenges in KYC processes effectively.
- The strategic implementation and continuous evolution of OCR technology are imperative in fortifying financial institutions against illicit activities and ensuring adherence to regulatory compliance in KYC and AML endeavours.
Meaning of OCR or Optical Character Recognition
Optical Character Recognition, commonly abbreviated as OCR, is a technology that translates different types of documents, such as scanned paper documents, PDF files, or images captured by a digital camera, into editable and searchable data. OCR is not just a technological marvel but a catalyst that empowers various industries, especially the financial sector, by automating document digitization, enhancing data retrieval, and bolstering data-driven strategies.
OCR: Beyond Simple Scanning
While scanning creates a picture of a document, OCR goes a step further. It recognizes the characters on the scanned image, converting them into machine-encoded text. This conversion facilitates the editing, searching, and sharing of the document’s content, making the data accessible and actionable.
The Multifaceted Applications of OCR
From automating data entry processes to enhancing accessibility for visually impaired individuals, OCR’s applications are vast and varied. In the financial sector, OCR is particularly lauded for its role in streamlining KYC processes and fortifying AML initiatives.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
How Does OCR Work?
The OCR process is like teaching a computer to read. Imagine you have a picture of a page from a book and you want to convert the words in that picture into typed text that you can edit, search, and work with on your computer. OCR helps do exactly that!
It looks at the shapes and patterns of the text in the image, such as letters and words, and converts them into text that can be edited and read by machines. This is super useful because it means we can take scanned documents, photos of documents, or even text superimposed on an image, and convert it into a format that’s easy to work with and analyze.
So, in simple steps: OCR takes an image, examines it to identify the shapes of letters and numbers, and then converts these into digital text. This technology is especially handy in various sectors, like finance and healthcare, where loads of information need to be digitized and analyzed for better and swift decision-making processes. Here are the steps involved in the OCR process:
Image Acquisition
The journey begins with acquiring an image, which could be a scanned document, a photograph, or any other form of image-based data.
Pre-processing
The image undergoes pre-processing to enhance its quality, involving noise reduction, binarization, and deskewing, ensuring optimal accuracy during character recognition.
Character Recognition
OCR algorithms then identify and recognize characters within the pre-processed image, translating them into machine-readable text.
Post-processing
Post-processing involves refining the recognized text, correcting potential errors, and enhancing the accuracy of the output.
Data Utilization
The converted text is now ready to be utilized, be it for data entry, information retrieval, or feeding into data analytics models.
Leveraging OCR for KYC and AML
In the financial realm, where KYC and AML compliance is paramount, OCR technology stands out as a formidable ally, ensuring that customer data is accurately extracted, verified, and utilized to safeguard against illicit financial activities.
OCR: A Shield Against Financial Crimes
OCR aids in combating financial crimes by automating the extraction of customer data from physical documents, thereby enhancing the accuracy and efficiency of KYC and AML processes. By swiftly converting document data into a digital format, OCR facilitates seamless customer verification and risk assessment, ensuring that financial institutions remain compliant and vigilant against potential threats.
Streamlining Customer Onboarding
The utilization of OCR in KYC processes not only expedites customer onboarding by automating data extraction but also ensures that the data is accurate and reliable, thereby minimizing the risk of onboarding fraudulent entities.
How Does OCR Help in KYC Processes?
OCR technology plays a pivotal role in KYC processes, ensuring that customer data is accurately extracted, verified, and stored, thereby streamlining customer onboarding and ongoing due diligence.
Automated Data Extraction
OCR automates the extraction of customer data from documents, reducing manual data entry and enhancing data accuracy.
Swift Customer Verification
By converting document data into a digital format, OCR facilitates swift and accurate customer verification, ensuring compliance and enhancing customer experience.
Enhanced Data Management
OCR ensures that customer data is easily retrievable and manageable, thereby streamlining ongoing customer due diligence and risk management.
Bolstering AML Compliance
With accurate and readily available customer data, financial institutions can effectively assess customer risk and ensure adherence to AML regulations.
Limitations of OCR in KYC Processes
While OCR is transformative, it is not without limitations, especially in the context of KYC processes where accuracy is paramount.
Accuracy Concerns
OCR may not always deliver 100% accurate results, especially with poor-quality images or complex documents.
Language and Font Limitations
OCR may struggle with certain languages, scripts, or fonts, potentially impacting data extraction accuracy.
Technological and Financial Barriers
Implementing OCR may require technological advancements and financial investments, which may be barriers for some institutions.
Dependence on Document Quality
OCR's effectiveness can be hindered by the quality of the documents scanned, where smudges, low resolution, or faded text might compromise the accuracy of data extraction.
Security and Privacy Concerns
Ensuring the security and privacy of the data processed through OCR is crucial, especially when dealing with sensitive customer information in KYC processes.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Navigating Through OCR Challenges in KYC
Despite its limitations, the strategic implementation of OCR can significantly enhance KYC processes, provided that financial institutions navigate through its challenges adeptly.
Implementing Data Verification
Incorporating additional data verification steps can mitigate the risks associated with OCR inaccuracies, ensuring that extracted data is reliable and accurate.
Utilizing Enhanced OCR Solutions
Leveraging advanced OCR solutions that are capable of handling various languages, fonts, and document qualities can enhance data extraction capabilities.
Ensuring Data Security
Implementing robust data security protocols ensures that customer data processed through OCR is safeguarded against potential breaches.
Conclusion
In wrapping up, Optical Character Recognition (OCR) has indeed become a game-changer in the financial world, particularly in enhancing Know Your Customer (KYC) and Anti-Money Laundering (AML) protocols. It's like a digital eye that reads and understands customer documents, making data handling not only efficient but also secure, which is pivotal in protecting financial establishments from being misused for shady transactions.
However, it's not a one-size-fits-all solution. While it brings a lot of benefits to the table, it’s essential to recognize and navigate through its limitations wisely. Thus, ensuring that OCR is seamlessly woven into KYC and AML processes, while also addressing its challenges, is key to fortifying financial institutions against potential risks and ensuring steadfast compliance in the ever-evolving financial landscape.
Account Suspension (Clone)
Introduction
Account suspension is a consequential action taken by service providers, platforms, or institutions to restrict access to an individual's or entity's account due to specific reasons. It serves as a protective measure to maintain security, enforce policies, and mitigate risks.
In this article, we will delve into the definition of account suspension, its impact on users and organizations, and the key reasons behind it. By understanding the concept and implications of account suspension, individuals and businesses can navigate online platforms and services more effectively.
Key Takeaways
- Account suspension is the temporary or permanent restriction of access to an individual's or entity's account.
- It is implemented to enforce policies, maintain security, and mitigate risks.
- Common reasons for account suspension include policy violations, fraudulent activities, abusive behavior, and security breaches.
- Account suspension can have significant consequences, such as loss of access to services, reputational damage, and financial implications.
- Users and organizations can prevent account suspension by adhering to platform guidelines, maintaining security measures, and practicing responsible online behavior.
Understanding Account Suspension
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a particular platform or service. It is a measure taken by service providers or administrators to enforce policies, maintain the integrity of the platform, and protect users. Account suspension is typically initiated in response to violations of terms of service, suspicious or fraudulent activities, abusive behavior, or security breaches. It serves as a means to maintain a safe and trusted environment for all users.
Implications of Account Suspension
Account suspension can have significant implications for individuals and organizations alike. The impact varies depending on the nature of the account and the services provided. Here are some common consequences of account suspension:
- Loss of Access: When an account is suspended, the user loses access to the platform or service associated with the account. This can disrupt communication, impede business operations, or limit the user's ability to connect with others.
- Reputational Damage: Account suspension can result in reputational damage, particularly if the suspension is publicly visible. It may give the impression of misconduct or non-compliance, affecting the user's credibility and trustworthiness.
- Financial Loss: For businesses or individuals who rely on online platforms for revenue generation, account suspension can lead to financial loss. It can disrupt sales, hinder customer relationships, and result in missed opportunities.
- Legal Consequences: In some cases, account suspension may be a result of legal violations or non-compliance with regulations. This can lead to legal consequences, including fines, penalties, or even legal action.
Reasons for Account Suspension
Account suspension can occur due to various reasons, all aimed at upholding the rules and policies of the platform or service provider. Here are some common reasons for account suspension:
- Policy Violations: Account suspension may be enforced when a user violates the terms of service or community guidelines set by the platform. This can include actions such as spamming, engaging in hate speech, or sharing inappropriate content.
- Fraudulent Activities: Accounts involved in fraudulent activities, such as phishing, identity theft, or financial scams, are subject to suspension. Platforms take such actions to protect users from potential harm and maintain trust within their communities.
- Abusive Behavior: Harassment, bullying, or any form of abusive behavior towards other users can lead to account suspension. Platforms prioritize creating safe and inclusive environments, and suspending accounts involved in such behavior is crucial in maintaining the well-being of their user base.
- Security Breaches: If an account is compromised or involved in a security breach, it may be suspended to prevent further unauthorized access or protect the platform's infrastructure. This proactive measure helps safeguard sensitive user data and maintain the overall security of the platform.
- Intellectual Property Infringement: Accounts found to be infringing upon intellectual property rights, such as unauthorized use of copyrighted material or trademark violations, can face suspension. Platforms take these actions to protect the rights of content creators and maintain a fair and legal environment.
- Violation of Financial Regulations: In cases where financial transactions are involved, non-compliance with anti-money laundering (AML) regulations or suspicious financial activities can result in account suspension. This measure is taken to prevent money laundering, terrorist financing, and other illicit financial practices.
Prevention Methods for Account Suspension
While the risk of account suspension exists, there are proactive steps individuals and organizations can take to minimize the likelihood of such actions. Here are some prevention methods to consider:
- Familiarize Yourself with Platform Guidelines: Before using any platform or service, thoroughly read and understand their terms of service, community guidelines, and policies. Adhere to these guidelines to avoid violations that may lead to account suspension.
- Maintain Account Security: Protect your account by using strong and unique passwords, enabling two-factor authentication (2FA), and regularly updating your login credentials. Be cautious of phishing attempts and avoid sharing sensitive information with unauthorized parties.
- Engage in Responsible Online Behavior: Practice respectful and responsible online conduct. Avoid engaging in abusive or harassing behavior, adhere to copyright laws, and respect the privacy and rights of others.
- Stay Informed about Regulatory Requirements: If you are involved in financial transactions or operate a business that handles sensitive customer information, stay updated on relevant AML and financial regulations. Implement appropriate compliance measures to ensure adherence to these requirements.
- Regularly Monitor and Review Account Activity: Stay vigilant and monitor your account for any suspicious activity or unauthorized access. Report any anomalies to the platform or service provider immediately.
Conclusion
Account suspension is a significant measure implemented by platforms and service providers to maintain security, enforce policies, and protect users. Understanding the implications of account suspension and the common reasons behind it is crucial for individuals and organizations operating in the digital landscape. By adhering to platform guidelines, practicing responsible online behavior, and prioritizing account security, users can mitigate the risk of account suspension and safeguard their online presence.
Frequently Asked Questions
What is account suspension?
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a platform due to policy violations, security breaches, or abusive behavior.
What are the implications of account suspension?
Account suspension can lead to loss of access, reputational damage, financial losses, and potential legal consequences for individuals and businesses.
Why do accounts get suspended?
Accounts can be suspended for reasons such as policy violations, fraudulent activities, abusive behavior, security breaches, intellectual property infringement, and non-compliance with financial regulations.
How can individuals prevent account suspension?
To prevent account suspension, individuals should familiarize themselves with platform guidelines, maintain account security, engage in responsible online behavior, stay informed about regulatory requirements, and regularly monitor account activity.
Why is understanding account suspension important?
Understanding account suspension helps individuals and organizations navigate the digital landscape responsibly, minimize the risk of suspension, and protect their online presence.
Account Suspension (Clone)
Introduction
Account suspension is a consequential action taken by service providers, platforms, or institutions to restrict access to an individual's or entity's account due to specific reasons. It serves as a protective measure to maintain security, enforce policies, and mitigate risks.
In this article, we will delve into the definition of account suspension, its impact on users and organizations, and the key reasons behind it. By understanding the concept and implications of account suspension, individuals and businesses can navigate online platforms and services more effectively.
Key Takeaways
- Account suspension is the temporary or permanent restriction of access to an individual's or entity's account.
- It is implemented to enforce policies, maintain security, and mitigate risks.
- Common reasons for account suspension include policy violations, fraudulent activities, abusive behavior, and security breaches.
- Account suspension can have significant consequences, such as loss of access to services, reputational damage, and financial implications.
- Users and organizations can prevent account suspension by adhering to platform guidelines, maintaining security measures, and practicing responsible online behavior.
Understanding Account Suspension
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a particular platform or service. It is a measure taken by service providers or administrators to enforce policies, maintain the integrity of the platform, and protect users. Account suspension is typically initiated in response to violations of terms of service, suspicious or fraudulent activities, abusive behavior, or security breaches. It serves as a means to maintain a safe and trusted environment for all users.
Implications of Account Suspension
Account suspension can have significant implications for individuals and organizations alike. The impact varies depending on the nature of the account and the services provided. Here are some common consequences of account suspension:
- Loss of Access: When an account is suspended, the user loses access to the platform or service associated with the account. This can disrupt communication, impede business operations, or limit the user's ability to connect with others.
- Reputational Damage: Account suspension can result in reputational damage, particularly if the suspension is publicly visible. It may give the impression of misconduct or non-compliance, affecting the user's credibility and trustworthiness.
- Financial Loss: For businesses or individuals who rely on online platforms for revenue generation, account suspension can lead to financial loss. It can disrupt sales, hinder customer relationships, and result in missed opportunities.
- Legal Consequences: In some cases, account suspension may be a result of legal violations or non-compliance with regulations. This can lead to legal consequences, including fines, penalties, or even legal action.
Reasons for Account Suspension
Account suspension can occur due to various reasons, all aimed at upholding the rules and policies of the platform or service provider. Here are some common reasons for account suspension:
- Policy Violations: Account suspension may be enforced when a user violates the terms of service or community guidelines set by the platform. This can include actions such as spamming, engaging in hate speech, or sharing inappropriate content.
- Fraudulent Activities: Accounts involved in fraudulent activities, such as phishing, identity theft, or financial scams, are subject to suspension. Platforms take such actions to protect users from potential harm and maintain trust within their communities.
- Abusive Behavior: Harassment, bullying, or any form of abusive behavior towards other users can lead to account suspension. Platforms prioritize creating safe and inclusive environments, and suspending accounts involved in such behavior is crucial in maintaining the well-being of their user base.
- Security Breaches: If an account is compromised or involved in a security breach, it may be suspended to prevent further unauthorized access or protect the platform's infrastructure. This proactive measure helps safeguard sensitive user data and maintain the overall security of the platform.
- Intellectual Property Infringement: Accounts found to be infringing upon intellectual property rights, such as unauthorized use of copyrighted material or trademark violations, can face suspension. Platforms take these actions to protect the rights of content creators and maintain a fair and legal environment.
- Violation of Financial Regulations: In cases where financial transactions are involved, non-compliance with anti-money laundering (AML) regulations or suspicious financial activities can result in account suspension. This measure is taken to prevent money laundering, terrorist financing, and other illicit financial practices.
Prevention Methods for Account Suspension
While the risk of account suspension exists, there are proactive steps individuals and organizations can take to minimize the likelihood of such actions. Here are some prevention methods to consider:
- Familiarize Yourself with Platform Guidelines: Before using any platform or service, thoroughly read and understand their terms of service, community guidelines, and policies. Adhere to these guidelines to avoid violations that may lead to account suspension.
- Maintain Account Security: Protect your account by using strong and unique passwords, enabling two-factor authentication (2FA), and regularly updating your login credentials. Be cautious of phishing attempts and avoid sharing sensitive information with unauthorized parties.
- Engage in Responsible Online Behavior: Practice respectful and responsible online conduct. Avoid engaging in abusive or harassing behavior, adhere to copyright laws, and respect the privacy and rights of others.
- Stay Informed about Regulatory Requirements: If you are involved in financial transactions or operate a business that handles sensitive customer information, stay updated on relevant AML and financial regulations. Implement appropriate compliance measures to ensure adherence to these requirements.
- Regularly Monitor and Review Account Activity: Stay vigilant and monitor your account for any suspicious activity or unauthorized access. Report any anomalies to the platform or service provider immediately.
Conclusion
Account suspension is a significant measure implemented by platforms and service providers to maintain security, enforce policies, and protect users. Understanding the implications of account suspension and the common reasons behind it is crucial for individuals and organizations operating in the digital landscape. By adhering to platform guidelines, practicing responsible online behavior, and prioritizing account security, users can mitigate the risk of account suspension and safeguard their online presence.
Frequently Asked Questions
What is account suspension?
Account suspension refers to the temporary or permanent restriction of access to an individual's or entity's account on a platform due to policy violations, security breaches, or abusive behavior.
What are the implications of account suspension?
Account suspension can lead to loss of access, reputational damage, financial losses, and potential legal consequences for individuals and businesses.
Why do accounts get suspended?
Accounts can be suspended for reasons such as policy violations, fraudulent activities, abusive behavior, security breaches, intellectual property infringement, and non-compliance with financial regulations.
How can individuals prevent account suspension?
To prevent account suspension, individuals should familiarize themselves with platform guidelines, maintain account security, engage in responsible online behavior, stay informed about regulatory requirements, and regularly monitor account activity.
Why is understanding account suspension important?
Understanding account suspension helps individuals and organizations navigate the digital landscape responsibly, minimize the risk of suspension, and protect their online presence.
Encryption
Encryption is a fundamental concept in the field of data security. It involves the process of converting information into a code or cipher to protect it from unauthorized access. In this article, we will explore the basics of encryption, its importance in data security, the difference between encryption and hashing, end-to-end encryption in messenger apps, encrypted messages, the most secure encryption algorithm, challenges and controversies surrounding encryption, and future trends in encryption technology.
The Basics of Encryption
Encryption is a crucial method used in cybersecurity to protect sensitive information from unauthorized access. It plays a vital role in ensuring data confidentiality and integrity, especially when transmitted over networks or stored on devices. By encrypting data, organizations and individuals can mitigate the risk of data breaches and unauthorized surveillance.
One of the key aspects of encryption is its reliance on encryption algorithms, which are complex mathematical formulas designed to transform plaintext data into ciphertext. These algorithms are carefully crafted to withstand various cryptographic attacks and ensure the security of the encrypted data. Common encryption algorithms include Advanced Encryption Standard (AES), Rivest-Shamir-Adleman (RSA), and Data Encryption Standard (DES).
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Aside from encryption algorithms, encryption also involves the use of encryption keys. These keys are essentially strings of data that determine the encryption and decryption process. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption utilizes a pair of keys – a public key for encryption and a private key for decryption.
When data is encrypted, it undergoes a transformation that renders it unreadable without the corresponding decryption key. This transformation results in ciphertext, which appears as a seemingly random sequence of characters. To access the original plaintext data, the recipient must possess the correct decryption key to reverse the encryption process and reveal the information.
Importance of Encryption in Data Security
Encryption plays a crucial role in ensuring the confidentiality, integrity, and authenticity of data. It provides a strong defense against unauthorized access and protects sensitive information from theft or misuse. In today's digital world, where data breaches and cyber-attacks are becoming increasingly common, encryption is an essential tool for safeguarding sensitive data.
Encryption helps to secure various types of information, including personal data, financial transactions, passwords, and sensitive business data. Without encryption, this information would be vulnerable to interception or manipulation by malicious individuals.
One of the key aspects of encryption is the use of cryptographic algorithms to convert plaintext data into ciphertext, making it unreadable to anyone without the proper decryption key. This process ensures that even if data is intercepted during transmission or storage, it remains secure and confidential. Advanced encryption standards, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), are widely used to protect data across different platforms and systems.
Moreover, encryption is not limited to data at rest or in transit; it also plays a vital role in securing communication channels. End-to-end encryption, for example, ensures that messages sent between parties are only accessible to the sender and the intended recipient, preventing eavesdroppers or hackers from intercepting and deciphering the information. This level of protection is especially critical in industries such as healthcare, finance, and government, where the confidentiality of communications is paramount.
What is the Difference Between Encryption and Hashing
While encryption and hashing are both techniques used to secure data, they serve different purposes. Encryption is a reversible process where data can be converted from its original form to an unreadable format and then decrypted back to its original state. This process involves the use of an encryption key to encode and decode the data, ensuring that only authorized parties can access the information. Encryption is widely used to protect sensitive data during transmission over networks or while stored on devices.
Hashing, on the other hand, is a one-way process that converts data into a fixed-size string of characters, known as a hash value. This hash value is unique to the input data, meaning that even a small change in the original data will result in a completely different hash value. Unlike encryption, hashing is not meant to be reversed. It is commonly used to verify the integrity of data by comparing the hash value of the original data with the hash value of the modified data. If the hash values match, it indicates that the data has not been tampered with. Hashing is commonly used in password storage, digital signatures, and data verification.
Encryption and hashing are fundamental tools in the field of cybersecurity, each serving a specific purpose in protecting data from unauthorized access and ensuring its integrity. While encryption focuses on confidentiality by scrambling data to make it unreadable without the proper decryption key, hashing emphasizes data integrity by generating unique hash values that can be used to verify the authenticity of information. By understanding the differences between encryption and hashing, organizations can implement appropriate security measures to safeguard their data effectively.
What is End-to-End Encryption in Messenger Apps
End-to-end encryption is a security feature implemented in messaging applications that ensures that the content of the messages remains encrypted from the moment they are sent until they reach the intended recipient. This means that only the sender and recipient can decrypt and read the messages, preventing potential eavesdroppers or intermediaries from accessing the message content.
End-to-end encryption provides a high level of privacy and security for sensitive conversations. However, it is important to note that even with end-to-end encryption, the metadata, such as the sender and recipient information, may still be accessible to the messaging service provider. Therefore, it is essential to choose messaging apps that prioritize user privacy and implement robust encryption practices.
One of the key aspects of end-to-end encryption is the use of public and private keys to secure the communication between users. When a message is sent, it is encrypted using the recipient's public key, which only the recipient's private key can decrypt. This ensures that even if the message is intercepted during transmission, it remains secure and unreadable to anyone other than the intended recipient.
Additionally, end-to-end encryption also protects the messages from being accessed by the messaging service provider itself. This means that the company behind the messaging app cannot read the contents of the messages, adding an extra layer of security and privacy for users. It is important for users to understand the encryption methods used by different messaging apps to make informed decisions about the security of their communications.
What is an Encrypted Message
An encrypted message is a piece of information that has been encoded using an encryption algorithm and can only be decrypted by the intended recipient who possesses the appropriate decryption key. Encrypted messages are often used to protect the confidentiality of sensitive information during transmission or storage.
Encrypting messages ensures that even if unauthorized individuals gain access to the data, they will not be able to understand its content without the decryption key. This provides an additional layer of security, especially when communicating over untrusted networks or storing data in the cloud.
One of the most common encryption techniques used for securing messages is the Advanced Encryption Standard (AES). AES is a symmetric key encryption algorithm that operates on fixed-size blocks of data and is considered highly secure. It uses a key of varying lengths (128, 192, or 256 bits) to encrypt and decrypt data, making it suitable for a wide range of applications.
Another important aspect of encrypted messages is the concept of end-to-end encryption. This means that the data is encrypted on the sender's device and can only be decrypted by the recipient, ensuring that no intermediaries can access the plaintext message. End-to-end encryption is crucial for maintaining privacy and security in communication platforms, such as messaging apps and email services.
What is the Most Secure Encryption Algorithm
The security of an encryption algorithm depends on various factors, including its design, implementation, and the size of the encryption key used. Currently, the most widely used and trusted encryption algorithms include Advanced Encryption Standard (AES), RSA, and Elliptic Curve Cryptography (ECC).
AES is a symmetric encryption algorithm that has become the de facto standard for secure communication. It is widely adopted due to its efficiency and robustness. AES operates on fixed block sizes of 128 bits and supports key sizes of 128, 192, or 256 bits, making it highly versatile for different security requirements. The algorithm itself consists of multiple rounds of substitution, permutation, and mixing of the input data to create the encrypted output, providing a strong defense against various cryptographic attacks.
RSA, on the other hand, is an asymmetric encryption algorithm used for key exchange and digital signatures. It relies on the mathematical complexity of factoring large prime numbers to ensure security. RSA encryption involves the use of a public key for encryption and a private key for decryption, enabling secure communication between parties without the need to share a secret key beforehand. The strength of RSA lies in the difficulty of factoring the product of two large prime numbers, which forms the basis of the security of the algorithm.
ECC is also an asymmetric encryption algorithm that offers stronger security with shorter keys compared to RSA. ECC is based on the algebraic structure of elliptic curves over finite fields, providing a high level of security with smaller key sizes. This makes ECC particularly suitable for resource-constrained environments where computational power and memory are limited. The efficiency of ECC in terms of key size and computational complexity has led to its widespread adoption in modern cryptographic systems, especially in applications where low power consumption and high performance are crucial.
It is important to note that the security of encryption algorithms is not static and is subject to advancements in technology and cryptographic attacks. Therefore, it is crucial to regularly update encryption algorithms and keys to maintain strong security.
Challenges and Controversies Surrounding Encryption
While encryption provides a critical layer of security, it is not without its challenges and controversies. One of the major challenges is the balance between privacy and law enforcement needs. Encryption can make it difficult for law enforcement agencies to access information related to criminal activities, hindering their investigative efforts.
There have been ongoing debates about whether encryption should have backdoors or weakened security measures to allow authorities to bypass encryption in certain situations. However, implementing such measures could potentially weaken the overall security and privacy of encrypted systems, making them more susceptible to abuse and exploitation by malicious actors.
Another challenge is the proper implementation and adherence to encryption standards. Weak encryption implementations or vulnerabilities in the encryption process can render the entire system insecure. It is crucial for organizations and individuals to follow best practices and ensure that encryption is implemented correctly and regularly updated to address emerging threats.
Future Trends in Encryption Technology
Encryption technology is continuously evolving to keep pace with emerging threats and advancements in computing power. Some of the future trends in encryption technology include:
- Post-Quantum Cryptography (PQC): As quantum computing evolves, it may pose a threat to current encryption algorithms. PQC aims to develop encryption algorithms that are resistant to attacks from quantum computers.
- Homomorphic Encryption: Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. This would enable data analysis and processing while maintaining privacy.
- Zero-Knowledge Proofs: Zero-knowledge proofs allow one party to prove knowledge or possession of certain information without revealing the information itself. This can have applications in authentication and privacy-enhancing technologies.
- Hardware-Based Encryption: Encryption algorithms implemented in specialized hardware can provide increased security and performance. Hardware-based encryption solutions can offer protection against physical attacks and side-channel attacks.
- Blockchain and Encryption: Blockchain technology can leverage encryption to secure transactions and ensure the integrity of data stored in the blockchain.
These future trends indicate that encryption technology will continue to play a crucial role in safeguarding data and privacy in an increasingly interconnected and digital world.
{{cta('fe388833-defc-42f1-b10c-50057ad59ac1','justifycenter')}}
In conclusion, encryption is a vital tool in data security. It ensures the confidentiality, integrity, and authenticity of sensitive information. The basics of encryption involve converting data into an unreadable format using encryption algorithms and keys. Encryption is essential for protecting personal and business data from unauthorized access.
As we embrace the complexities of encryption in securing data and communications, it's equally crucial to address the sophisticated threats in the financial sector. Tookitaki's FinCense is at the forefront of combating financial crimes with its advanced end-to-end operating system, designed to empower fintechs and traditional banks.
FinCense's federated learning model and integration with the AFC Ecosystem enhance the detection of financial crimes, providing a robust defense against money laundering and fraud. With tools like the Onboarding Suite, FRAML, Smart Screening, Customer Risk Scoring, Smart Alert Management, and Case Manager, Tookitaki offers a comprehensive solution for maintaining compliance and managing risks effectively. Don't let financial crime undermine the integrity of your institution. Talk to our experts today and fortify your defences with Tookitaki's cutting-edge FinCense platform.
Chargeback Fraud
Introduction
In the fast-paced world of online transactions, businesses face not only the opportunities of e-commerce but also the challenges of chargeback fraud. Chargebacks occur when a customer disputes a transaction and requests a refund directly from their credit card issuer. The issue has been growing at a rapid pace in the e-commerce market, leading to significant losses for online merchants. To avoid these losses, this article explores the common causes of chargeback fraud, its impact on businesses, and essential chargeback fraud prevention strategies.
Key Takeaways
- Chargeback fraud is a growing concern that affects businesses, financial institutions, and consumers, leading to financial losses, damaged reputations, and legal consequences.
- To combat chargeback fraud effectively, it's crucial to understand the step-by-step process employed by fraudsters, including the concept of "friendly fraud" where legitimate consumers dispute transactions they authorized.
- Engaging in chargeback fraud is illegal in many jurisdictions, and perpetrators can face criminal charges, emphasizing the need for ethical financial practices.
- Implementing robust transaction monitoring systems, verification processes, and enhanced customer communication can significantly reduce the risk of chargeback fraud.
- In case of a chargeback fraud incident, it's important to gather evidence, engage with payment processors and acquiring banks, and possibly seek legal assistance to navigate the complex resolution process.
Common Causes of Chargeback Fraud
Chargeback fraud can be initiated for various reasons, ranging from legitimate disputes to malicious intent. Some common causes include:
1. Identity Theft:
Identity theft is a prevalent cause of chargeback fraud, where fraudsters gain unauthorized access to a customer's personal information. This can occur through various means, such as phishing attacks, data breaches, or hacking. Once armed with the victim's credentials, the fraudster proceeds to make purchases using the compromised identity. From the perspective of the affected individual, these unauthorized transactions lead to chargebacks when they dispute the purchases they did not make.
2. Friendly Fraud:
Friendly fraud occurs when a customer falsely claims they did not authorize a transaction or did not receive the purchased goods or services. Unlike traditional fraud, friendly fraud often involves customers making genuine purchases but later changing their minds or forgetting about the transaction. This type of fraud can be unintentional, with customers not realizing the impact of initiating a chargeback.
3. Unauthorized Transactions:
Stolen credit card information is a common tool for fraudsters to make unauthorized purchases. Whether obtained through skimming devices, data breaches, or other illicit means, stolen card details enable fraudsters to conduct transactions without the knowledge or consent of the cardholder. When the rightful cardholder discovers the unauthorized charges, they may initiate chargebacks to reclaim their funds.
4. False Claims:
False claims involve customers making untrue statements about the quality of products or services received, leading to chargebacks. This can stem from misunderstandings, buyer's remorse, or, in some cases, intentional exploitation of the chargeback system. Businesses often face challenges in proving the legitimacy of their products or services when confronted with these false claims.
Understanding these common causes is crucial for businesses to implement effective prevention strategies and maintain a secure and trustworthy e-commerce environment.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Impact of Chargeback Fraud
The consequences of chargeback fraud extend beyond financial losses. Businesses may experience:
1. Immediate Financial Losses:
Chargebacks result in immediate financial losses for merchants. When a chargeback is initiated, the disputed funds are withdrawn from the merchant's account, often accompanied by additional chargeback fees. This sudden loss can disrupt cash flow, hinder day-to-day operations, and impact profitability, especially for small and medium-sized businesses.
2. Increased Operational Costs:
Dealing with chargebacks requires time, effort, and resources. Merchants must invest in customer support to address chargeback disputes, investigate the validity of claims, and compile evidence to present to payment processors. These additional operational costs can strain a business's resources and divert attention from core activities.
3. Reduced Profit Margins:
As chargeback fees and operational costs accumulate, businesses may find their profit margins gradually eroding. This can be particularly challenging for businesses operating on thin margins, making it essential to proactively manage and prevent chargeback fraud.
4. Higher Processing Fees:
A high frequency of chargebacks may lead to increased processing fees imposed by payment processors. Processors often charge merchants higher fees or designate them as high-risk if they consistently experience chargeback issues. Elevated processing fees further contribute to the financial burden on businesses.
5. Reputational Damage:
Perhaps one of the most insidious impacts of chargeback fraud is the potential harm to a business's reputation. Frequent chargebacks can be perceived as a sign of poor service or unreliable products, eroding customer trust and loyalty. Negative reviews and word-of-mouth publicity can spread, further tarnishing the brand image.
6. Loss of Merchandise or Services:
In cases of friendly fraud, where customers falsely claim non-receipt of goods or services, businesses not only lose the transaction value but also the actual products or services provided. This double loss compounds the financial impact of chargeback fraud.
7. Risk of Account Termination:
Acquiring banks and payment processors may view businesses with a high chargeback rate as risky. In extreme cases, this can lead to the termination of merchant accounts, cutting off the business's ability to process payments. Finding alternative payment solutions can be challenging and may come with higher fees.
Chargeback Fraud Prevention Strategies
Chargeback fraud prevention requires a proactive approach that combines technology, clear communication, and monitoring. Let's explore effective strategies to boost your business against the threats of chargeback fraud:
1. Implement Advanced Verification Systems:
Invest in robust authentication mechanisms to verify the identity of customers. Multi-factor authentication, CAPTCHA tests, and biometric authentication are effective tools to ensure that only authorized users can complete transactions.
2. Utilize Address Verification Services (AVS):
AVS checks if the address you give matches the one the card company has on record. Implementing AVS helps detect discrepancies in addresses, a potential red flag for fraudulent transactions.
3. Employ 3D Secure Technology:
3D Secure adds an extra layer of security to online transactions by requiring customers to enter a password or a one-time code. This technology helps authenticate the cardholder during the transaction, reducing the risk of unauthorized purchases.
4. Educate Customers:
Clear communication with customers is pivotal. Clearly convey product/service details, terms of purchase, and refund policies during the checkout process. This transparency helps manage customer expectations and reduces the likelihood of disputes.
5. Secure Payment Processing:
Ensure that your payment processing systems are secure and compliant with Payment Card Industry Data Security Standard (PCI DSS). Regularly update your systems to protect against vulnerabilities and potential breaches.
6. Monitor Unusual Activity:
Employ real-time monitoring tools to scrutinize transactions for unusual patterns or high-risk behavior. Automated systems can flag transactions that deviate from typical customer behavior, allowing for swift investigation.
7. Establish Communication Channels:
Provide accessible and responsive customer support channels. Encourage customers to reach out with concerns or issues before resorting to chargebacks. A timely and helpful response can often resolve disputes without escalating to chargebacks.
8. Utilize Fraud Prevention Services:
Leverage fraud prevention services offered by payment processors and third-party providers. These services use advanced algorithms and machine learning to identify potentially fraudulent transactions.
9. Set Clear Policies:
Clearly outline your business's policies regarding refunds, returns, and chargebacks on your website. Having transparent policies reduces misunderstandings and gives customers clear guidance on the proper procedures to follow.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Best Practices for Merchants
1. Transparent Policies:
Transparency in policies is crucial for managing customer expectations and minimizing the likelihood of chargebacks. Merchants should clearly articulate their policies regarding refunds, returns, and chargebacks on their websites. This includes providing information on:
- Refund Procedures: Clearly outline how customers can request refunds, the conditions under which refunds are granted, and the timeline for processing refunds.
- Return Policies: Specify the process for returning products, including any associated costs, conditions for returns, and the timeframe within which returns are accepted.
- Chargeback Procedures: Communicate how chargebacks are handled, the circumstances under which customers can initiate chargebacks, and the steps they should take before resorting to this option.
By ensuring that customers are well-informed about these policies from the outset, merchants reduce the risk of misunderstandings that could lead to disputes and chargebacks.
2. Robust Product Descriptions:
Detailed and accurate product descriptions play a crucial role in managing customer expectations and preventing disputes. Merchants should:
- Provide Comprehensive Information: Ensure that product listings include detailed information about features, specifications, sizes, colors, and any other relevant details.
- Include High-Quality Images: Use high-quality images that accurately represent the product. Multiple images from different angles can help customers visualize the product more effectively.
- Specify Terms and Conditions: Clearly state any terms and conditions associated with the product, such as warranty information, return policies, and potential limitations.
- Highlight Unique Selling Points: Showcase the unique selling points of the product to emphasize its value and differentiate it from similar offerings in the market.
By offering a comprehensive and honest portrayal of products, merchants empower customers to make informed purchasing decisions, reducing the likelihood of dissatisfaction and subsequent chargebacks.
̌3. Monitor Chargeback Ratios:
Monitoring chargeback ratios is an essential practice for merchants to identify and address potential issues promptly. Here's how merchants can effectively manage this aspect:
- Set Thresholds: Establish acceptable chargeback ratios for your business. This threshold may vary depending on industry standards, payment processors, and specific agreements with financial institutions.
- Regularly Analyze Data: Regularly analyze chargeback data to identify patterns, spikes, or trends. This proactive approach allows merchants to spot issues before they escalate and take preventive measures.
- Investigate Causes: When chargeback ratios exceed acceptable levels, conduct thorough investigations to understand the causes. Look for commonalities among disputed transactions and address root causes, whether they stem from customer dissatisfaction, fraud, or operational issues.
- Adjust Fraud Prevention Strategies: Use insights gained from chargeback data to refine and enhance fraud prevention strategies. This may involve updating security protocols, incorporating new technologies, or adjusting internal processes to minimize chargeback risks.
By actively monitoring chargeback ratios and taking proactive measures based on the data, merchants can effectively manage and mitigate the impact of chargeback fraud on their businesses.
Conclusion
Chargeback fraud poses a significant threat to businesses, but with proactive chargeback fraud prevention strategies and best practices, merchants can mitigate risks and protect their bottom line. By prioritizing security, transparency, and customer education, businesses can foster a safer and more trustworthy online environment for both buyers and sellers.
Correspondent Banking
Correspondent banking plays a crucial role in facilitating global financial transactions and maintaining stability in the global economy. As the world becomes increasingly interconnected, correspondent banking has become an essential part of the international banking system. In this article, we will explore the definition, functions, and significance of correspondent banking, as well as its impact on the global economy. We will also discuss the challenges facing correspondent banking and the future of this vital banking practice.
Understanding Correspondent Banking
Definition and Basic Functions of Correspondent Banking
Correspondent banking refers to the relationship between two banks that allows them to provide services on behalf of each other in different geographic locations. In this system, one bank, known as the correspondent bank, holds deposits and performs transactions on behalf of another bank, referred to as the respondent bank. The correspondent bank acts as an intermediary, providing banking services to the respondent bank's clients in foreign markets.
The key function of correspondent banking is to facilitate cross-border transactions by enabling banks to access financial services in foreign jurisdictions without requiring a physical presence. This arrangement allows banks to offer their clients services such as international payments, trade financing, and foreign currency exchange.
The Role of Correspondent Banks in Financial Transactions
Correspondent banks play a crucial role in enabling financial transactions between banks and their clients across borders. They provide a range of services that include but are not limited to, clearing payments, issuing letters of credit, and facilitating trade financing. Correspondent banks act as a bridge, connecting banks from different countries and facilitating seamless international transactions.
Furthermore, correspondent banks often have extensive networks and expertise in dealing with regulatory frameworks and compliance requirements in various jurisdictions. This knowledge and infrastructure make them valuable partners for banks operating in multiple countries.
Let's dive deeper into the world of correspondent banking and explore some specific examples of how correspondent banks facilitate international transactions. For instance, imagine a small business in the United States that wants to import goods from a supplier in China. Without a correspondent bank, the U.S. business would face numerous challenges, such as navigating complex foreign exchange regulations and finding a reliable payment method that the Chinese supplier accepts.
However, with the help of a correspondent bank, the U.S. business can leverage their relationship to make the transaction smoother. The correspondent bank can assist in converting the U.S. dollars into Chinese yuan, ensuring that the payment is made in the local currency. Additionally, the correspondent bank can issue a letter of credit to the Chinese supplier, guaranteeing that the payment will be made once the goods are delivered as agreed. This added layer of trust and security provided by the correspondent bank helps mitigate risks for both parties involved in the transaction.
Another example of the role of correspondent banks in facilitating financial transactions is in the realm of international trade financing. When a company wants to expand its operations globally, it often requires additional funding to support its growth. Correspondent banks can assist by providing trade financing solutions, such as issuing documentary credits or providing pre-export financing. These services enable businesses to access the necessary capital to finance their international trade activities, ensuring smooth operations and growth.
In conclusion, correspondent banking plays a vital role in enabling cross-border transactions and facilitating international trade. By acting as intermediaries, correspondent banks connect banks from different countries, provide essential services, and navigate complex regulatory landscapes. Their expertise and networks make them valuable partners for banks and businesses operating in the global marketplace.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Global Impact of Correspondent Banking
Facilitating International Trade and Investment
Correspondent banking plays a vital role in facilitating international trade and investment by providing the necessary financial infrastructure. Through correspondent relationships, banks can offer trade finance services, such as letters of credit, which ensure payment security and facilitate smooth international trade transactions. These services enable businesses to access global markets and drive economic growth.
Additionally, correspondent banking supports foreign direct investment by helping businesses establish banking relationships in host countries. This allows investors to navigate local financial systems and facilitates efficient movement of funds across borders.
Correspondent banking networks are intricate webs of financial institutions that work together to facilitate global transactions. These networks often span across continents, connecting banks in different countries to ensure seamless cross-border financial services. The relationships established through correspondent banking are built on trust and reliability, essential for the smooth functioning of international trade and investment.
Promoting Financial Inclusion and Stability
Correspondent banking plays a significant role in promoting financial inclusion in underserved regions. By providing access to global financial services, correspondent banking helps individuals and businesses in remote or developing areas to participate in the global economy.
Moreover, correspondent banking contributes to financial stability by facilitating secure and efficient cross-border payments. The ability to make timely and reliable international transactions helps maintain confidence in the global financial system, reducing the risk of disruptions.
Financial institutions involved in correspondent banking adhere to strict regulatory standards to ensure the security and integrity of cross-border transactions. Compliance with anti-money laundering (AML) and know your customer (KYC) regulations is crucial to prevent illicit financial activities and maintain the stability of the global financial system. By upholding these regulatory requirements, correspondent banks contribute to building a more transparent and secure financial environment for international trade and investment.
Challenges in Correspondent Banking
Regulatory and Compliance Issues
Correspondent banking faces various regulatory and compliance challenges due to the complex nature of cross-border transactions. Banks must comply with anti-money laundering (AML) and know-your-customer (KYC) regulations, which require extensive due diligence and screening processes. Meeting these obligations can be resource-intensive for both correspondent and respondent banks, especially when dealing with multiple jurisdictions.
Furthermore, regulatory frameworks differ across countries, posing challenges for correspondent banks to navigate and ensure compliance. These differences can create additional complexities and costs for banks operating in multiple jurisdictions.
Expanding on the regulatory challenges, it is crucial for correspondent banks to stay updated on evolving regulations and compliance requirements. This necessitates continuous monitoring of regulatory changes and investing in training programs to ensure staff awareness and adherence to the latest standards.
Risks and Mitigation in Correspondent Banking
Correspondent banking also carries inherent risks, such as the possibility of money laundering, terrorist financing, and sanctions violations. Banks must implement robust risk management frameworks and internal controls to mitigate these risks effectively.
Additionally, correspondent banks need to carefully manage counterparty risks associated with their respondent banks. Due diligence is essential to assess the financial stability, reputation, and compliance track record of respondent banks.
Moreover, technological advancements have introduced new risks in correspondent banking, such as cybersecurity threats and data breaches. Correspondent banks must invest in secure technology infrastructure and regularly conduct cybersecurity audits to safeguard sensitive financial information and prevent unauthorized access.
The Future of Correspondent Banking
Technological Innovations and Their Impact
The future of correspondent banking lies in embracing technological innovations to streamline processes and enhance efficiency. New technologies such as blockchain and digital identity verification systems have the potential to revolutionize correspondent banking by simplifying cross-border transactions and reducing costs.
Blockchain, a decentralized and transparent ledger technology, can provide secure and immutable records of transactions, eliminating the need for intermediaries and reducing the time and cost associated with cross-border transfers. Additionally, digital identity verification systems can enhance security by ensuring the authenticity of individuals involved in financial transactions, mitigating the risk of fraud and identity theft.
Furthermore, advancements in artificial intelligence and data analytics can aid in identifying suspicious patterns and enhancing compliance efforts, thereby strengthening the integrity of correspondent banking. By leveraging machine learning algorithms, banks can analyze vast amounts of data to detect potential money laundering activities or other illicit transactions, ensuring regulatory compliance and safeguarding the financial system.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Evolving Trends in Global Banking Practices
As the global banking landscape evolves, correspondent banking must adapt to changing market dynamics and customer expectations. This includes addressing the increasing demand for real-time payments, improving customer experience, and embracing sustainable banking practices.
Real-time payments have become a necessity in today's fast-paced world, where individuals and businesses expect instant and seamless transactions. Correspondent banks can leverage technological advancements to offer real-time payment solutions, enabling customers to transfer funds across borders instantaneously, enhancing convenience and reducing transactional friction.
Moreover, correspondent banking must continue to foster collaboration and partnerships between banks, regulators, and other stakeholders to address emerging challenges collectively. By working together, financial institutions can develop standardized processes, share best practices, and establish robust risk management frameworks, ensuring the stability and resilience of the global financial system.
Furthermore, sustainable banking practices are gaining traction as environmental, social, and governance (ESG) considerations become increasingly important. Correspondent banks can play a vital role in promoting sustainable finance by incorporating ESG factors into their lending and investment decisions, supporting environmentally friendly projects, and encouraging responsible business practices.
In conclusion, correspondent banking plays a crucial role in the global economy, facilitating cross-border transactions, promoting financial inclusion, and supporting international trade and investment. While facing regulatory challenges and inherent risks, correspondent banking continues to evolve, embracing technological advancements to enhance efficiency and sustainability. By staying abreast of evolving trends and adopting innovative solutions, correspondent banking can continue to contribute to the growth and stability of the global economy.
As correspondent banking continues to evolve and adapt to the demands of the global economy, the need for robust anti-money laundering and fraud prevention measures has never been greater. Tookitaki's FinCense offers an innovative solution, providing an end-to-end operating system designed to enhance the efficiency and effectiveness of financial crime detection and prevention. With our Onboarding Suite, FRAML capabilities, Smart Screening, Customer Risk Scoring, Smart Alert Management (SAM), and Case Manager, Tookitaki is at the forefront of safeguarding the integrity of the global financial system. Embrace the future of correspondent banking with reduced risks and improved compliance. Talk to our experts today to learn how FinCense can empower your institution to stay ahead in a rapidly changing banking landscape.
Tokenization
Introduction
Tokenization has emerged as a powerful technology that enhances security, simplifies transactions, and facilitates asset digitization. In this article, we will explore the concept of tokenization and its applications in different domains. From cryptocurrency and NLP to banking and asset tokenization, we will uncover how this innovative approach revolutionizes industries by transforming traditional systems into more secure and efficient ones.
Key Takeaways
- Tokenization converts sensitive data into unique tokens, enhancing security and privacy.
- Tokenization finds applications in cryptocurrency, NLP, banking, and asset digitization.
- It enables fractional ownership, increased liquidity, and simplified transactions.
- Tokenization examples include stablecoins, loyalty program tokens, and tokenized credit cards.
- Tokenization offers benefits such as improved security, efficiency, and asset accessibility.
What is Tokenization?
Tokenization is the process of converting sensitive data, such as payment card information or personal identifiers, into unique tokens. These tokens hold no intrinsic value and act as a reference to the original data, stored securely in a tokenization system.
Tokenization in Cryptocurrency
In the realm of cryptocurrency, tokenization refers to the representation of real-world assets or services using digital tokens on a blockchain. This enables fractional ownership, increased liquidity, and efficient transfer of assets while ensuring transparency and security.
Tokenization in Natural Language Processing (NLP)
Tokenization plays a crucial role in NLP, where it involves breaking down textual data into smaller units, typically words or subwords. This process enables language understanding, sentiment analysis, and various other NLP tasks by providing structured input for machine learning algorithms.
Tokenization in Banking
Tokenization has revolutionized banking by enhancing security in payment transactions. By replacing sensitive cardholder data with unique tokens, the risk of data breaches and fraud is significantly reduced. Tokenization also enables seamless mobile payments and simplifies recurring transactions.
Tokenization of Assets
Asset tokenization involves representing physical assets, such as real estate or artwork, as digital tokens on a blockchain. This enables fractional ownership, increased liquidity, and easier transfer of assets, unlocking new investment opportunities and streamlining complex processes.
Tokenization Examples
Examples of tokenization include stablecoins in the cryptocurrency space, where tokens are pegged to a stable asset like fiat currency, and loyalty program tokens, which represent rewards and incentives within a system. Additionally, the tokenization of credit cards has become prevalent in mobile payment solutions.
Key Benefits of Tokenization
Tokenization offers several benefits, including enhanced security, reduced risk of data breaches, increased efficiency in transactions, improved liquidity and accessibility to assets, and simplified compliance with regulations.
Challenges and Considerations
While tokenization brings numerous advantages, challenges such as regulatory compliance, interoperability, and scalability need to be addressed. Organizations must also ensure the protection of tokenization systems and maintain data integrity.
Conclusion
Tokenization represents a transformative approach that enhances security, streamlines transactions, and digitizes assets across various industries. By leveraging tokenization, organizations can unlock new possibilities and address challenges in today's rapidly evolving digital landscape. As the technology continues to evolve, we can expect further innovation and adoption of tokenization to shape the future of finance, security, and asset management.
Return Fraud
Introduction
Return fraud is a deceptive practice that involves returning merchandise for illegitimate purposes, often resulting in financial losses for retailers and businesses. This article sheds light on the intricacies of return fraud, examining its various methods, potential legal implications, and the measures businesses can take to prevent and detect such fraudulent activities.
We explore real-life examples, discuss the concept of return fraud, and provide insights into cross-retailer return policies. By understanding the tactics employed in return fraud and implementing effective prevention strategies, businesses can safeguard their financial well-being and maintain trust with their customers.
Key Takeaways
- Return fraud involves deceptive practices aimed at returning merchandise for unauthorized purposes, leading to financial losses for businesses.
- Examples of return fraud include returning stolen items with a receipt, buying something and returning a different item, and cross-retailer return schemes.
- Return fraud can have legal consequences, with some cases considered as felonies depending on the jurisdiction and the value of the fraud.
- Wardrobing fraud is a specific form of return fraud where individuals purchase items for temporary use and then return them for a refund.
- Cross-retailer return policies, although convenient for customers, can pose challenges for businesses in preventing return fraud.
- Implementing stringent return policies, verifying receipts, conducting thorough inspections, and leveraging technology can help businesses mitigate the risk of return fraud.
The Scope of Return Fraud
Understanding Return Fraud
Return fraud encompasses deceptive practices where individuals exploit return policies to obtain refunds or exchanges for unauthorized purposes. It involves various tactics aimed at deceiving retailers and businesses, resulting in financial losses.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Real-Life Examples of Return Fraud
Numerous instances of return fraud have been documented, shedding light on the diversity of fraudulent practices. These examples include individuals returning stolen items with a receipt, purchasing one item and returning a different, often lower-priced item, and engaging in wardrobing fraud by using items temporarily and returning them for a refund.
The Financial Impact on Businesses
Return fraud has significant financial implications for businesses, leading to revenue losses, increased operational costs, and reduced profitability. The costs associated with restocking, inventory shrinkage, and fraudulent refunds can be substantial, affecting the overall health and sustainability of businesses.
Exploring Return Fraud Methods
Returning Stolen Items with a Receipt
This method involves individuals stealing merchandise and attempting to return it with a valid receipt to receive a refund or exchange. It exploits the return policy by making it difficult for businesses to differentiate between legitimate and fraudulent returns.
Buying and Returning Different Items
In this tactic, fraudsters purchase an item, often of higher value, and then attempt to return a different item, usually of lesser value, while presenting the original receipt. This technique aims to deceive businesses and obtain a refund or an exchange that results in a financial advantage for the fraudster.
Wardrobing Fraud
Wardrobing refers to the practice of purchasing items, such as clothing or electronics, for temporary use and then returning them for a refund. This form of return fraud relies on exploiting lenient return policies that accept returns of used or slightly worn items.
Cross-Retailer Returns
Some fraudsters exploit cross-retailer return policies by purchasing items from one retailer and returning them to a different retailer to obtain a refund. This scheme takes advantage of varying return policies and can be challenging for businesses to detect and prevent.
Legal Consequences of Return Fraud
Return Fraud and the Law
Return fraud is considered a form of theft and deception, and the legality of such actions varies depending on jurisdiction. Laws are in place to protect businesses from fraudulent returns and hold perpetrators accountable for their actions.
Return Fraud as a Felony or Misdemeanor
The severity of legal consequences for return fraud depends on factors such as the value of the fraud, the intent of the perpetrator, and the jurisdiction's laws. In some cases, return fraud can be classified as a felony, which carries more severe penalties than a misdemeanour offence.
Prosecution and Penalties
Perpetrators of return fraud can face criminal charges, fines, restitution, and even imprisonment. The prosecution and penalties associated with return fraud aim to deter individuals from engaging in fraudulent activities and protect the interests of businesses and consumers.
Preventing Return Fraud
Implementing Stringent Return Policies
Businesses can establish clear and comprehensive return policies that outline eligibility criteria, time limits, and conditions for returns. These policies should include measures to deter fraudulent returns and protect the business from financial losses.
Verifying Receipts and Product Conditions
: Thoroughly verifying receipts and inspecting the condition of returned items can help detect fraudulent returns. Implementing processes to ensure the accuracy and authenticity of receipts and examining product conditions can be crucial in identifying potential return fraud.
Thorough Inspections and Inventory Management
Conducting meticulous inspections of returned items, including checking for tampering or signs of wear, can help businesses identify fraudulent returns. Efficient inventory management systems can track returns, flag suspicious patterns, and provide valuable data for analysis.
Utilizing Technology and Data Analytics
Implementing advanced technology solutions and data analytics can enhance fraud detection capabilities. Automated systems can analyze customer behaviour, transaction patterns, and return history to identify potential fraudulent activities and patterns.
Training and Education
Providing comprehensive training to employees on return fraud awareness, detection techniques, and proper handling of returns can significantly contribute to prevention efforts. Educating staff about common return fraud schemes and equipping them with the knowledge to identify red flags can help minimize the occurrence of fraudulent returns.
Collaboration and Information Sharing
Collaboration between businesses, industry associations, and law enforcement agencies can facilitate the exchange of information and best practices for combating return fraud. Sharing intelligence on known fraudsters, suspicious activities, and emerging trends can strengthen prevention strategies and improve overall fraud detection efforts.
Building Consumer Trust and Customer Service
Transparent Communication
Building consumer trust begins with transparent communication regarding return policies, procedures, and expectations. Clear and accessible information about eligibility, timelines, and conditions for returns can help establish a fair and consistent approach, reducing the opportunity for fraudulent activities.
Providing Excellent Customer Service
Exceptional customer service can contribute to preventing return fraud by fostering positive relationships with customers. Promptly addressing concerns, providing accurate product information, and resolving issues effectively can discourage fraudulent behaviour and promote a trustworthy shopping environment.
Balancing Fraud Prevention and Customer Experience
While implementing fraud prevention measures, it is essential to strike a balance between preventing return fraud and maintaining a positive customer experience. Streamlining return processes, offering hassle-free returns for legitimate cases, and providing personalized support can enhance customer satisfaction while mitigating the risk of fraudulent activities.
Conclusion
In conclusion, return fraud poses significant challenges for businesses, resulting in financial losses and operational disruptions. Understanding the various methods employed by fraudsters, the legal consequences involved, and implementing robust prevention strategies are crucial in combatting return fraud. By establishing stringent return policies, leveraging technology, educating employees, and fostering customer trust, businesses can minimize the impact of return fraud and maintain a secure and trustworthy retail environment.
Return fraud poses significant challenges for retailers and businesses, leading to financial losses and erosion of trust. By familiarizing themselves with the various methods employed in return fraud, understanding the legal consequences, and implementing robust prevention strategies, businesses can mitigate the risks associated with fraudulent returns.
Through stringent policies, staff training, and the adoption of technology-driven solutions, organizations can protect themselves and their customers, ensuring a secure and trustworthy shopping experience. By staying vigilant and continually improving their anti-fraud measures, businesses can combat return fraud and maintain a strong position in the marketplace.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Frequently Asked Questions
What is Return Fraud?
Return fraud involves deceptive practices where individuals exploit a retailer's return policy to gain unauthorized refunds or exchanges, leading to financial losses for businesses.
Can you give some real-life examples of Return Fraud?
Examples include returning stolen items with a receipt, buying a high-value item and returning a lower-value item, and "wardrobing," where items are used temporarily and then returned.
How does Return Fraud impact businesses financially?
Businesses face revenue losses, increased operational costs, and reduced profitability due to the costs associated with restocking, inventory shrinkage, and fraudulent refunds.
What is the "Returning Stolen Items with a Receipt" method?
This involves stealing merchandise and then attempting to return it with a valid receipt, exploiting the return policy and making it hard for businesses to differentiate between legitimate and fraudulent returns.
How does the "Buying and Returning Different Items" method work?
Fraudsters purchase a high-value item and attempt to return a different, lower-value item using the original receipt, deceiving businesses for financial gain.
What is Wardrobing Fraud?
Wardrobing involves purchasing items like clothing or electronics for temporary use and then returning them for a refund, exploiting lenient return policies.
What is Cross-Retailer Returns?
This involves buying items from one retailer and returning them to another, exploiting varying return policies between retailers.
Is Return Fraud illegal?
Yes, return fraud is considered a form of theft and deception, and laws are in place to protect businesses and hold perpetrators accountable.
Is Return Fraud a Felony or a Misdemeanor?
The classification depends on the value of the fraud, the intent, and jurisdictional laws. It can be either a felony, which carries more severe penalties, or a misdemeanour.
What are the penalties for Return Fraud?
Penalties can include criminal charges, fines, restitution, and even imprisonment.
How can businesses prevent Return Fraud?
Businesses can implement stringent return policies, verify receipts and product conditions, use technology and data analytics, and train employees to detect fraudulent returns.
What role does technology play in preventing Return Fraud?
Advanced technology solutions and data analytics can analyze customer behaviour, transaction patterns, and return history to identify potentially fraudulent activities.
How can employee training help prevent Return Fraud?
Comprehensive training equips employees with the knowledge to identify red flags and handle returns properly, contributing to prevention efforts.
How can transparent communication build consumer trust?
Clear information about return policies and procedures helps establish a fair and consistent approach, reducing opportunities for fraudulent activities.
How does customer service contribute to preventing Return Fraud?
Exceptional customer service fosters positive relationships, discouraging fraudulent behaviour and promoting a trustworthy shopping environment.
How can businesses balance fraud prevention and customer experience?
Businesses should streamline return processes, offer hassle-free returns for legitimate cases, and provide personalized support to enhance customer satisfaction while mitigating fraud risks.
Fraud Investigation
Introduction
Fraud is a pervasive problem that poses significant risks to individuals, businesses, and society as a whole. To combat this threat, the field of fraud investigation plays a crucial role in uncovering the truth, bringing perpetrators to justice, and mitigating future risks. In this article, we delve into the world of fraud investigation, exploring the process, job opportunities, and notable examples of financial fraud cases.
We also examine the distinction between blue-collar and white-collar crimes, shedding light on their characteristics and impact. Whether you are considering a career in fraud investigation or seeking to enhance your understanding of this critical field, this article provides valuable insights into the multifaceted nature of fraud investigations.
Key Takeaways
- Fraud investigation is a comprehensive process that plays a crucial role in detecting and deterring fraudulent activities.
- The financial fraud investigation process involves key stages such as evidence gathering, interviews, and financial record analysis.
- Job opportunities in fraud investigation offer diverse roles and responsibilities requiring specific skills and qualifications.
- Blue-collar crimes are crimes of opportunity, characterized by offences like embezzlement and identity theft.
- White-collar crimes are crimes of deception, often involving complex schemes and high-profile cases.
- Continuous learning and professional development through financial fraud investigation courses can enhance knowledge and skills in the field.
Understanding Fraud Investigation
Fraud investigation is a multifaceted process aimed at uncovering fraudulent activities and holding perpetrators accountable. It involves a series of key stages, including evidence gathering, interviews with relevant parties, and meticulous analysis of financial records. By following this comprehensive process, investigators can piece together the puzzle of fraudulent schemes, identify responsible individuals or entities, and build a strong case for prosecution.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Exploring Job Opportunities in Fraud Investigation
The field of fraud investigation offers a range of job opportunities for individuals interested in pursuing a career in combating financial fraud. Fraud investigators play a critical role in various industries, working closely with law enforcement agencies, government organizations, and private companies. Their responsibilities include conducting investigations, collecting evidence, collaborating with legal teams, and providing expert testimony. Successful fraud investigators possess a combination of skills, such as analytical thinking, attention to detail, knowledge of financial systems, and proficiency in investigative techniques.
Unraveling Blue-Collar Crimes: Crimes of Opportunity
Blue-collar crimes refer to offences that arise from opportunities within a person's immediate environment. These crimes are typically committed by individuals seeking personal gain through illegal means. Examples of blue-collar crimes include embezzlement, identity theft, insurance fraud, and petty theft. Fraud investigation plays a crucial role in detecting and investigating these crimes, uncovering evidence, and ensuring that the perpetrators face appropriate legal consequences.
Decoding White-Collar Crimes: Crimes of Deception
White-collar crimes are typically non-violent offences committed by individuals in positions of trust or authority, often involving complex schemes to deceive victims. Examples of white-collar crimes include securities fraud, insider trading, money laundering, and corporate fraud. The investigation of white-collar crimes requires specialized knowledge, as they often involve intricate financial transactions, document forgery, and manipulation of corporate structures. Fraud investigators utilize sophisticated techniques, such as forensic accounting and digital forensics, to uncover evidence and build cases against those responsible for these crimes.
Read More: The Role of Technology in Fraud Investigations
Enhancing Knowledge and Skills: Financial Fraud Investigation Courses
Continuous learning and professional development are crucial in the field of financial fraud investigation. Various courses and certifications are available to enhance knowledge and skills in this domain. These educational programs cover topics such as fraud detection techniques, investigative methodologies, legal frameworks, and emerging trends in financial crimes. By pursuing these courses, professionals can stay updated with the latest tools and strategies in fraud investigation, enabling them to make a more significant impact in combating financial fraud and protecting individuals and organizations from potential threats.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
Fraud investigation is a dynamic and essential process that plays a pivotal role in safeguarding individuals, businesses, and society from financial crimes. By understanding the intricacies of the fraud investigation process, exploring job opportunities, and distinguishing between blue-collar and white-collar crimes, individuals can gain valuable insights into this complex field. Moreover, pursuing relevant courses and certifications in financial fraud investigation can enhance knowledge and skills, enabling professionals to make a meaningful impact in the fight against fraud. As fraud continues to evolve in the digital age, it is imperative to stay informed, adapt to new challenges, and contribute to a safer and more secure financial landscape through effective fraud investigation.
Frequently Asked Questions
What is Fraud Investigation?
Fraud investigation is a comprehensive process aimed at identifying and prosecuting fraudulent activities. It involves gathering evidence, conducting interviews, and analyzing financial records to build a strong case against perpetrators.
What Job Opportunities Exist in Fraud Investigation?
The field offers various roles in law enforcement agencies, government organizations, and private companies. Responsibilities include conducting investigations, collecting evidence, and providing expert testimony. Key skills include analytical thinking, attention to detail, and knowledge of financial systems.
What are Blue-Collar Crimes?
Blue-collar crimes are offenses that arise from immediate opportunities and are usually committed for personal gain. Examples include embezzlement, identity theft, and insurance fraud. Fraud investigation is crucial for detecting and prosecuting these crimes.
How Do Blue-Collar and White-Collar Crimes Differ?
While blue-collar crimes are crimes of opportunity, white-collar crimes are crimes of deception, often involving complex schemes and committed by individuals in positions of trust. Examples of white-collar crimes include securities fraud and money laundering.
What Techniques are Used in White-Collar Crime Investigations?
Investigating white-collar crimes often involves specialized techniques like forensic accounting and digital forensics due to the complexity of the schemes involved.
Are There Courses Available for Financial Fraud Investigation?
Yes, various courses and certifications are available to enhance knowledge and skills in fraud detection techniques, investigative methodologies, and legal frameworks. These courses help professionals stay updated with the latest tools and strategies.
Why is Continuous Learning Important in Fraud Investigation?
As fraud evolves, especially in the digital age, staying updated with the latest tools, techniques, and legal frameworks is crucial for effective investigation and prosecution.
What are the Key Skills Required for a Successful Fraud Investigator?
Analytical thinking, attention to detail, knowledge of financial systems, and proficiency in investigative techniques are some of the key skills required.
What is the Role of Fraud Investigators in Society?
Fraud investigators play a critical role in safeguarding the interests of individuals, businesses, and society by detecting, investigating, and prosecuting fraudsters.
How Can Individuals Contribute to a Safer Financial Landscape?
By understanding the intricacies of fraud investigation, exploring career opportunities in the field, distinguishing between types of crimes, and investing in continuous education, individuals can contribute to a safer and more secure financial environment.
Digital Signatures
Introduction
Digital signatures play a crucial role in modern-day communication and transactions, ensuring data integrity, authenticity, and non-repudiation. In this article, we will explore the concept of digital signatures, understand how they work, discover their applications in cryptography, and learn how to create and verify digital signatures. Understanding digital signatures is essential for enhancing data security and trustworthiness in the digital age.
Key Takeaways
- Digital signatures verify the authenticity and integrity of digital data.
- They are created using asymmetric encryption techniques and provide non-repudiation.
- Digital signatures enhance data integrity and trustworthiness in electronic transactions and communication.
- Examples of digital signatures include signing PDFs, validating software integrity, and securing online transactions.
- Digital signatures play a vital role in cryptography, ensuring secure communication and establishing trust.
What Are Digital Signatures?
A digital signature is a cryptographic mechanism that verifies the authenticity and integrity of digital data. It provides a digital equivalent of a handwritten signature, ensuring that the data has not been tampered with and can be traced back to the signatory.
How Digital Signatures Work
Digital signatures are created using asymmetric encryption techniques. The signatory uses their private key to encrypt a hash of the data, generating a unique digital signature. The recipient can then use the signatory's public key to decrypt and verify the signature, ensuring the data's integrity and authenticity.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Benefits and Applications of Digital Signatures
Digital signatures offer several benefits, including data integrity, non-repudiation, and authentication. They are widely used in electronic documents, email communication, online transactions, and government applications to ensure secure and trustworthy interactions.
Examples of Digital Signatures
Examples of digital signatures include signing PDF documents, electronically signing contracts and agreements, verifying software integrity, and validating online transactions. Digital signatures provide a reliable and tamper-evident method of establishing the origin and integrity of digital content.
Creating a Digital Signature
Creating a digital signature typically involves generating a cryptographic key pair, consisting of a private key and a corresponding public key. Software tools and platforms enable users to sign digital documents using their private key, which can be securely stored.
Verifying a Digital Signature
To verify a digital signature, the recipient uses the signatory's public key to decrypt and validate the signature. If the decrypted signature matches the hash of the received data, the signature is considered valid, ensuring the data's integrity and authenticity.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
Digital Signatures in Cryptography
Digital signatures are an essential component of cryptographic protocols, providing mechanisms for secure key exchange, message integrity, and non-repudiation. They play a crucial role in secure communication, digital certificates, and establishing trust in online transactions.
Digital Signature Standards and Certificates
Various standards and protocols govern digital signatures, including the RSA and DSA algorithms. Digital certificates, issued by trusted certification authorities (CAs), are used to bind a public key to an individual or organization, providing additional trust and authenticity.
Conclusion
Digital signatures are a powerful tool in the digital world, providing assurance of data integrity, authenticity, and non-repudiation. By understanding how digital signatures work, their applications, and the process of creating and verifying them, individuals and organizations can enhance the security and trustworthiness of their digital interactions. Embracing digital signatures is crucial for safeguarding sensitive information, protecting against fraud, and ensuring reliable digital communication.
Trust & Safety
Introduction
Trust and safety are paramount in today's digital landscape, where users rely on online platforms for various purposes. Whether it's e-commerce, social media, or sharing economy platforms, establishing trust and maintaining safety are critical for fostering positive user experiences.
In this article, we will delve into the concept of trust and safety, explore its components, discuss its significance in various industries, and highlight best practices to ensure a secure and reliable environment for all stakeholders.
Key Takeaways
- Trust and safety encompass measures and practices aimed at creating a secure and reliable online environment.
- The three components of trust and safety are risk assessment, policy development, and enforcement/response.
- Best practices include user verification, content moderation, transparency, and continuous monitoring.
- Trust and safety are important in e-commerce, sharing economy, social media, and online payment industries.
- Trust and safety certifications validate platforms' commitment to user safety.
- Trust and safety professionals play a critical role in implementing and improving trust and safety measures.
Definition of Trust & Safety: Establishing Confidence and Security
Trust and safety refer to the measures and practices implemented to create a secure and reliable environment for users engaging in online platforms, services, and transactions. It encompasses strategies, policies, and tools designed to protect users from risks, such as fraud, harassment, misinformation, and other harmful activities. Trust and safety efforts aim to build confidence, foster positive user experiences, and safeguard the integrity of online ecosystems.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Components of Trust & Safety: Building Blocks for Security
Trust and safety comprise three key components that work together to establish a secure environment:
- Risk Assessment: Conducting thorough risk assessments is essential to identify potential threats and vulnerabilities within the platform or service. This involves analyzing user behavior, transaction patterns, content moderation, and other relevant factors to proactively detect and mitigate risks.
- Policy Development: Developing comprehensive policies and guidelines sets the framework for acceptable user behavior and establishes rules to prevent misconduct. These policies often cover areas such as content moderation, community guidelines, data privacy, and dispute resolution processes.
- Enforcement and Response: Implementing robust enforcement mechanisms and response protocols is crucial to address policy violations and security breaches promptly. This includes employing content moderation systems, user reporting mechanisms, and dedicated trust and safety teams to investigate and take appropriate actions when incidents occur.
Trust & Safety Best Practices: Ensuring a Secure Environment
To ensure trust and safety within online platforms, the following best practices should be considered:
- User Verification: Implement a robust user verification process to authenticate the identities of users and minimize the risk of fraudulent activities.
- Content Moderation: Employ effective content moderation practices to prevent the dissemination of harmful, illegal, or inappropriate content. This involves using automated tools, artificial intelligence, and human moderators to review and remove violating content.
- Transparency and Communication: Foster transparency by clearly communicating platform policies, rules, and guidelines to users. Provide accessible channels for users to report issues and seek assistance, and ensure timely and clear communication regarding trust and safety matters.
- Continuous Monitoring: Regularly monitor platform activities, user behavior, and emerging trends to identify new risks and adapt trust and safety measures accordingly. Stay updated with industry standards and collaborate with relevant authorities and organizations to address evolving threats.
Trust & Safety in Different Industries: Examples of Application
Trust and safety principles find application across various industries, including:
- E-commerce: Online marketplaces and retailers prioritize trust and safety to protect buyers and sellers from fraud, counterfeit products, and unauthorized transactions.
- Sharing Economy: Trust and safety are crucial in sharing economy platforms such as ride-sharing and accommodation-sharing services to ensure the safety and security of both service providers and users.
- Social Media: Social media platforms employ trust and safety measures to combat harassment, hate speech, and the spread of misinformation to create a positive and inclusive online environment.
- Online Payments: Trust and safety play a significant role in online payment systems to protect users' financial information and prevent fraudulent transactions.
Trust & Safety Certifications: Recognizing Excellence
Trust and safety certifications provide a way to validate and recognize platforms and organizations that prioritize user safety. These certifications often involve rigorous assessments of trust and safety practices, policies, and infrastructure. By obtaining such certifications, platforms can demonstrate their commitment to maintaining a secure environment and instilling confidence in their users. Examples of trust and safety certifications include ISO 27001, SOC 2, and PCI-DSS, which assess various aspects of data security, privacy, and risk management.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Trust & Safety Professionals: Safeguarding User Confidence
Trust and safety professionals play a crucial role in maintaining a secure and reliable online environment. These professionals are responsible for developing and implementing trust and safety strategies, policies, and enforcement mechanisms. They analyze user behavior, monitor platform activities, respond to incidents, and collaborate with relevant stakeholders to enhance trust and safety practices. Additionally, they stay updated with industry trends and emerging risks, ensuring continuous improvement and adaptation of trust and safety measures.
Conclusion: Upholding Trust and Ensuring Safety
Trust and safety are foundational elements for any successful online platform or service. By prioritizing the establishment of trust, implementing robust safety measures, and fostering transparent communication, organizations can create a secure environment that instills confidence in their users. The proactive detection of risks, the enforcement of policies, and the collaboration with trust and safety professionals are essential for effectively addressing potential threats. As the digital landscape continues to evolve, trust and safety will remain vital in building sustainable and trustworthy online ecosystems.
Referral Fraud
Introduction
In the digital age, businesses rely heavily on word-of-mouth marketing to expand their customer base and boost sales. Referral programs have become a popular way to incentivize customers to refer their friends and acquaintances, but with the rise of referral fraud, businesses need to be vigilant. Referral fraud refers to the deceptive practice of manipulating referral programs for personal gain, often at the expense of businesses and their genuine customers.
This article delves into the intricacies of referral fraud, explores the legal implications, and provides actionable strategies to safeguard your business from this fraudulent activity.
Key Takeaways
- Referral fraud involves the manipulation of referral programs to generate fake or illegitimate referrals, often resulting in financial losses and reputational damage for businesses.
- Preventing referral fraud requires a multi-faceted approach, including robust fraud detection systems, strict referral program guidelines, and proactive monitoring of suspicious activities.
- Legality of referral programs may vary depending on jurisdiction, and businesses must ensure compliance with applicable laws and regulations.
- Education and awareness play a vital role in preventing referral fraud, both among businesses and their customers.
- Proactive measures such as referral program audits, referral validation techniques, and stringent referral terms and conditions can help mitigate the risk of referral fraud
Understanding Referral Fraud
Referral fraud is a deceptive practice that involves manipulating referral programs for personal gain. In this type of fraud, individuals exploit the referral system by generating fake or illegitimate referrals. By doing so, they aim to benefit from the rewards or incentives offered by businesses, often at the expense of genuine customers and the reputation of the company. Understanding the intricacies of referral fraud is crucial for businesses to effectively detect and prevent such fraudulent activities.
What is Referral Fraud?
Referral fraud refers to the act of intentionally gaming the referral program to gain undeserved benefits. It can take various forms, such as creating fake accounts, generating false referrals, or colluding with others to exploit the system. The primary goal of referral fraudsters is to obtain rewards or discounts without genuinely referring new customers to the business. By deceiving the referral program, they undermine the integrity of the program and can cause financial losses and reputational damage to the businesses targeted.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Types of Referral Fraud
Referral fraud can manifest in different ways, and understanding the various types is essential for businesses to effectively combat this deceptive practice. One common type is the fake referral trick, where fraudsters create fictitious accounts or use misleading information to generate referrals that are not genuine. Another type involves the use of fake referral generators, which are automated tools designed to produce fake referrals on a large scale. Referral abuse is another form of fraud where individuals manipulate the referral program by exploiting loopholes or engaging in unethical practices to maximize their benefits.
The Impact of Referral Fraud
Referral fraud can have significant consequences for businesses that fall victim to such deceptive activities. One of the major impacts is financial losses. When fraudsters exploit referral programs, businesses may end up giving away rewards or discounts without acquiring new customers or generating the expected revenue. Additionally, referral fraud can cause reputational damage, as customers and the public lose trust in the integrity of the business. Negative word-of-mouth and online reviews can harm the brand's image and hinder future customer acquisition efforts.
Preventing and Combating Referral Fraud
Preventing and combating referral fraud requires a proactive approach and the implementation of robust strategies. One essential step is to establish and maintain fraud detection systems that can identify suspicious referral activities. Automated monitoring and analytics tools can help detect patterns and anomalies in referral data, allowing businesses to flag potentially fraudulent behavior. Verifying IP addresses can also provide insights into the legitimacy of referrals by checking for multiple referrals originating from the same IP.
Setting Clear Referral Program Guidelines
To prevent referral fraud, businesses need to establish clear guidelines for their referral programs. This includes defining the terms and conditions of the program, outlining eligibility criteria, and specifying the rewards and incentives on offer. By setting transparent rules, businesses can deter fraudsters and ensure that genuine referrals are rewarded appropriately. Verification and validation processes can be implemented to confirm the authenticity of referrals before granting rewards.
Proactive Monitoring of Suspicious Activities
Proactive monitoring is vital in detecting and preventing referral fraud. Businesses should closely monitor referral activities for any unusual patterns or anomalies. Unusual referral patterns, such as a sudden influx of referrals from specific sources or a high number of referrals from the same IP address, may indicate fraudulent behaviour. Anomalous user behaviour, such as multiple referrals from a single user account, should also raise red flags. By actively monitoring and investigating suspicious activities, businesses can take swift action to mitigate the risk of referral fraud.
Legality of Referral Programs
The legality of referral programs may vary depending on jurisdiction, and businesses must ensure compliance with applicable laws and regulations. It is crucial to understand the legal landscape surrounding referral programs, including any specific requirements or restrictions imposed by authorities. Jurisdictional variations may exist in terms of disclosure requirements, privacy considerations, and the permissible types of incentives. Businesses should consult legal professionals to navigate the legal aspects of referral programs and ensure they adhere to the relevant regulations.
Detecting and Investigating Referral Fraud
Detecting and investigating referral fraud requires a systematic approach and diligent monitoring of referral program data. Businesses should leverage advanced analytics and fraud detection tools to identify potential fraudulent activities. By analyzing referral patterns, referral sources, user behaviour, and other relevant data points, businesses can pinpoint suspicious activities and flag them for further investigation. It is essential to establish internal processes and resources dedicated to investigating and addressing referral fraud cases promptly.
Taking Action Against Referral Fraud
Once referral fraud is detected and verified, businesses must take swift and decisive action to address the fraudulent activities. This may involve removing illegitimate referrals, revoking rewards or incentives, and implementing appropriate penalties for those involved in the fraud. Communicating with affected customers and stakeholders transparently is crucial to maintaining trust and demonstrating a commitment to combating referral fraud. Additionally, businesses should continuously improve their fraud prevention measures, update referral program guidelines, and educate users about the importance of ethical referral practices.
Educating Users on Ethical Referral Practices
Education plays a vital role in preventing referral fraud. By providing clear guidelines and educating users about ethical referral practices, businesses can foster a community of genuine and responsible referrers. Users should be informed about the consequences of fraudulent activities, the importance of referring actual customers, and the value of maintaining the integrity of the referral program. Regular communication, tutorials, and reminders can help reinforce these messages and promote a culture of honesty and fairness within the user base.
Collaborating with Fraud Prevention Experts
In the fight against referral fraud, businesses can benefit from collaborating with fraud prevention experts and industry professionals. These experts possess specialized knowledge and experience in detecting and combating fraudulent activities. They can provide valuable insights, guidance, and best practices to help businesses stay ahead of evolving fraud techniques. Collaboration can take the form of consultations, workshops, or partnerships with organizations specializing in fraud prevention and detection.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
Referral fraud poses a significant threat to businesses, impacting their revenue, reputation, and customer trust. By understanding the nature of referral fraud, implementing robust fraud detection systems, setting clear guidelines, and staying compliant with applicable laws, businesses can protect themselves and their customers from this deceptive practice. It is crucial to remain vigilant, educate stakeholders, and foster a culture of integrity to maintain the effectiveness and credibility of referral programs. By taking proactive measures and working collectively as a community, we can combat referral fraud and create a safer and more trustworthy business environment.
Frequently Asked Questions
What is Referral Fraud? Referral fraud is the deceptive manipulation of referral programs to gain unearned rewards or benefits, often at the expense of businesses and genuine customers.
How Does Referral Fraud Impact Businesses?
Referral fraud can lead to financial losses and reputational damage for businesses, as they may give away rewards without gaining new customers or revenue.
What are the Types of Referral Fraud?
Types of referral fraud include creating fake accounts, generating false referrals, using automated referral generators, and exploiting loopholes in the referral program.
How Can Businesses Prevent Referral Fraud?
Businesses can prevent referral fraud by implementing robust fraud detection systems, setting clear referral program guidelines, and proactively monitoring for suspicious activities.
Is Referral Fraud Illegal?
The legality of referral fraud varies by jurisdiction, but it is generally considered deceptive and unethical, and businesses must comply with applicable laws when setting up referral programs.
Blackmail
Introduction
Blackmail has long been a menace, shaking the foundations of society, and threatening personal and professional lives. This complex and pernicious crime frequently eludes the grasp of the law due to its covert nature, which makes understanding and prevention all the more critical.
Identifying and reporting potential cases of blackmail involves a combination of name screening, payment screening, and identity verification. This comprehensive guide offers a deep dive into the intricate world of blackmail, shedding light on its mechanics, forms, applications, and most importantly, the steps one can take to ward off such threats.
Key Takeaways
- Blackmail involves threatening to disclose damaging information about an individual unless certain demands, often of a monetary nature, are met. It preys on fear, guilt, and shame to manipulate victims into compliance.
- Blackmail can take different forms, including traditional blackmail, cyber blackmail, and commercial blackmail. Each form targets different victims and utilizes various methods to extract compliance or payment.
- Examples of blackmail include personal blackmail, which threatens to reveal embarrassing secrets, and corporate blackmail, which targets large companies to gain financial advantage or damage their reputation.
- Prevention of blackmail requires personal vigilance, such as being cautious about the information shared and practicing strong cybersecurity measures. Seeking legal help is crucial if one suspects they are a victim of blackmail.
- Understanding the dynamics and proactive prevention measures empowers individuals to protect themselves from the threats of blackmail. By staying informed and taking necessary precautions, one can mitigate the risks associated with this harmful practice.
Defining Blackmail
Blackmail is the act of threatening to reveal potentially harmful information about an individual unless certain demands, typically of monetary nature, are met. These threats can affect various aspects of a person's life, including personal relationships, professional standing, or public image.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Mechanics of Blackmail
The Cycle of Blackmail
Blackmail operates in a cyclical pattern, starting with the collection of compromising information, followed by threat issuance, and often, the subsequent compliance of the victim, fearful of potential repercussions.
Psychological Dynamics
Blackmail is as much a psychological weapon as a criminal act. It exploits the fear, guilt, and shame of victims, creating a sense of dread that often leads to compliance with the blackmailer's demands.
Different Forms of Blackmail
Traditional Blackmail
This is the most recognizable form of blackmail, where the perpetrator threatens to disclose damaging information unless their demands are met.
Cyber Blackmail
With the advent of the digital age, blackmail has also taken on a virtual form. Cyber blackmail, or cyber extortion, involves threats to leak sensitive digital data or launch a cyber attack unless a ransom is paid.
Commercial Blackmail
Commercial blackmail targets businesses, threatening to damage a company's reputation, disclose trade secrets, or disrupt operations unless the blackmailer's demands are satisfied.
Instances of Blackmail: Learning from Examples
Personal Blackmail
Personal blackmail can involve threatening to reveal embarrassing secrets, past mistakes, or intimate photographs or videos. Such instances underscore the importance of privacy and trust.
Corporate Blackmail
Large corporations are common targets of blackmail due to their abundant resources and reputation concerns. One example is a threat to expose fraudulent practices unless a hefty sum is paid.
{{cta('7bbac0d9-4da7-4f3e-ae1b-55b62911072e','justifycenter')}}
Proactive Prevention of Blackmail
Personal Vigilance
The first step in prevention is personal vigilance. Be cautious about the information you share, both offline and online. Remember that once information is out, it can't be taken back.
Cybersecurity Measures
As cyber blackmail becomes more common, maintaining strong cybersecurity has never been more critical. Regularly update your software, use strong, unique passwords, and be wary of phishing attempts.
Legal Help
Understanding the legalities related to blackmail can be a deterrent for potential blackmailers. If you suspect that you're a victim of blackmail, seek legal advice promptly.
Conclusion
Blackmail is a grave threat that requires understanding and proactive measures to combat effectively. By being vigilant, practising strong cybersecurity, and seeking legal counsel when necessary, one can protect oneself from falling prey to this insidious crime. Knowledge is power, and in the case of blackmail, it is the most potent weapon in the arsenal of prevention.
Mortgage
Introduction
A journey towards owning a home often begins with understanding the realm of mortgages. Mortgages are an integral part of the real estate sector, playing a vital role in facilitating homeownership. Offering a mortgage involves a thorough look-back review to prevent issues like tax evasion and assess inherent risk associated with the applicant. Through this comprehensive guide, we aim to decode the intricate world of mortgages, equipping readers with the knowledge to navigate the mortgage maze successfully.
Key Takeaways
- Mortgages play a crucial role in homeownership and the real estate market, providing individuals with an opportunity to purchase a property even if they don't have immediate financial capability.
- Mortgage agreements outline terms and conditions, and repayment structures include both the principal loan amount and accrued interest.
- Different types of mortgages, such as fixed-rate and adjustable-rate mortgages, offer various benefits and considerations.
- Prospective homeowners need to consider the risks and considerations associated with mortgages, including the possibility of foreclosure and the long-term financial commitment.
- Pre-approval, affordability calculations, and comparing mortgage options are crucial steps to navigate the mortgage process effectively.
- Credit scores play a significant role in mortgage approval and the interest rates offered.
- The down payment size affects mortgage terms and conditions, with a larger down payment potentially leading to lower monthly payments, better interest rates, and the avoidance of private mortgage insurance (PMI).
Demystifying Mortgages: A Closer Look
Definition: What is a Mortgage?
A mortgage is a type of loan used to finance the purchase of a property. The purchased property itself serves as collateral, which the lender can seize if the borrower defaults on loan payments.
Role in Homeownership and Real Estate
Mortgages provide a pathway to homeownership, particularly for individuals who may not have the immediate financial capability to buy a property outright. By making homeownership more accessible, mortgages drive activity in the real estate market and contribute to economic growth.
The Mortgage Mechanism: How it Works
Mortgage Agreements: Terms and Conditions
In a mortgage agreement, the borrower promises to repay the loan amount, along with interest, over a predetermined period. Failure to adhere to the agreed repayment schedule can lead to foreclosure, where the lender seizes the property to recover the outstanding loan amount.
Repayment Structures
Mortgages typically have a structured repayment schedule. Payments often include a portion of the principal loan amount and accrued interest. Over time, as the principal decreases, homeowners gradually gain equity in their property.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Decoding Mortgage Types
Fixed-Rate Mortgages
Fixed-rate mortgages come with an interest rate that remains constant throughout the loan term. This type of mortgage offers predictability in monthly payments, shielding borrowers from potential interest rate fluctuations.
Adjustable-Rate Mortgages
Adjustable-rate mortgages (ARMs), have interest rates that adjust periodically, often annually, based on market conditions. ARMs may offer lower initial interest rates compared to fixed-rate mortgages, but they also carry the risk of increased payments if rates rise.
Government-Insured Mortgages
Government-insured mortgages, such as FHA and VA loans, offer opportunities for specific borrower groups, including first-time homebuyers and military veterans. These loans often have competitive interest rates and lower down payment requirements.
Mortgage Use Cases: Pros and Cons
Realizing Homeownership Dreams
Mortgages allow individuals to become homeowners without paying the full property price upfront. They offer the chance to build equity over time and potentially benefit from property value appreciation.
Risks and Considerations
Despite their advantages, mortgages come with risks, including the possibility of foreclosure. A mortgage is a long-term financial commitment, often spanning several decades. Borrowers must consider their financial stability and ability to meet future payments.
Navigating the Mortgage Maze: Tips and Prevention Methods
Mortgage Pre-Approval
Obtaining pre-approval for a mortgage gives prospective buyers an idea of how much they might be eligible to borrow. It also shows sellers that buyers are serious, potentially strengthening their position in negotiations.
Affordability Calculations
Understanding what is affordable is crucial when considering a mortgage. Potential borrowers should calculate their debt-to-income ratio and consider future income stability. They should also take into account potential increases in living expenses and plan for unexpected costs.
Comparing Mortgage Options
Lender Selection
Choosing a lender is a significant step in the mortgage process. Potential borrowers should compare offerings from multiple lenders to find the best fit. Factors to consider include interest rates, loan terms, and customer service reputation.
Loan Term
The loan term affects both the monthly payments and the total cost of the mortgage. Shorter loan terms generally have higher monthly payments but lower total costs due to less accrued interest. Longer terms have lower monthly payments but more interest over time.
Interest Rates
Interest rates greatly influence the affordability of the mortgage. Even a small rate difference can translate into a significant amount over the life of the loan. Borrowers should be aware of current market rates and whether those rates are expected to rise or fall in the near future.
The Impact of Credit Scores on Mortgages
Importance of Credit Scores
Credit scores play a crucial role in the mortgage process. They influence not only loan approval but also the interest rate on the mortgage. Borrowers with higher credit scores typically receive more favourable rates.
Improving Credit Scores
Improving one's credit score can lead to better mortgage terms. Strategies for improving credit scores include making timely payments on all debts, keeping credit card balances low, and avoiding new debt in the months leading up to the mortgage application.
{{cta('bdd96089-cde2-43f3-95a3-3f6d7b74af38','justifycenter')}}
The Role of Down Payments in Mortgages
Down Payment Basics
The down payment is the upfront amount a homebuyer pays towards the property purchase. It is usually expressed as a percentage of the property's total price. The remaining amount is financed through the mortgage.
Impact on Mortgage Terms
The size of the down payment can impact the mortgage's terms and conditions. A larger down payment can lead to lower monthly payments, a better interest rate, and potentially avoiding the need for private mortgage insurance (PMI).
Conclusion
Mortgages are a significant financial tool that can make homeownership a reality. By understanding the nuances of mortgages, potential homeowners can navigate the process effectively, making well-informed decisions that align with their financial situation and homeownership goals. While the journey may seem complex, with the right knowledge and guidance, any potential homeowner can unravel the mortgage maze.
Understanding mortgages, from their mechanism to their various types, equips potential homeowners with the knowledge to make informed decisions. While mortgages offer a pathway to homeownership, potential borrowers must also consider the associated risks and responsibilities. By learning about different mortgage types, recognizing their use cases, and implementing preventive measures, one can navigate the mortgage maze with confidence.
Look-Back Review
In the fast-paced world of finance, maintaining regulatory compliance is pivotal. One tool that aids financial institutions in achieving this is the Look-Back Review. This retrospective process offers insights into past transactions, helping detect inconsistencies and ensure adherence to evolving regulatory norms.
Key Takeaways
- Grasping the definition and purpose of the Look-Back Review
- Understanding the Look-Back Review process
- Identifying the role of the Look-Back Review in regulatory compliance
- Recognizing the advantages and potential challenges of the Look-Back Review
Look-Back Review: The Basics
In its simplest terms, a Look-Back Review involves examining past transactions to detect any irregularities or non-compliance with regulatory norms. It's a powerful tool in the financial institution's arsenal, allowing for the identification and rectification of previous oversights or gaps in the institution's compliance program.
The Purpose of the Look-Back Review
The Look-Back Review serves two key purposes: to ensure that past transactions align with current regulatory requirements, and to strengthen future compliance efforts. By analyzing past transactional patterns, institutions can fine-tune their risk detection capabilities, enhancing their defenses against financial malpractice.
The Look-Back Review: How it Works
Step-by-Step Process
Conducting a Look-Back Review involves several stages:
- Identification of the Review Period: This is the timeframe in which the transactions occurred and will be analyzed. It could be a few months to a few years, depending on regulatory requirements or the institution's discretion.
- Data Compilation: Transactional data within the review period is compiled for analysis.
- Analysis of Transactions: Using tools like statistical modeling and pattern recognition, transactions are scrutinized for regulatory compliance.
- Reporting: Findings are documented and reported to relevant parties, typically management or regulatory authorities.
When conducting a look-back review, consider assessing transactions for potential issues related to money laundering and suspicious activity reporting (SAR).
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Use Cases of the Look-Back Review
Enhancing Compliance Programs
Look-Back Reviews help financial institutions identify past lapses in compliance, allowing for continuous improvement of their compliance programs. This ensures institutions are better equipped to meet evolving regulatory norms.
Remediation Efforts
In cases where non-compliance is identified, Look-Back Reviews facilitate remediation by pinpointing exactly where and when the breach occurred. This allows for targeted corrective actions.
Benefits and Potential Challenges
Benefits
The Look-Back Review helps financial institutions maintain compliance, avoid hefty penalties, and protect their reputation. By continually enhancing their compliance programs, they can ensure robust defence against financial crimes.
Challenges
However, Look-Back Reviews can be time-consuming and require significant resources. The process also demands technical expertise to accurately analyze transaction data. These challenges necessitate a balanced approach, leveraging technology and expert personnel to conduct efficient and effective reviews.
Conclusion
Look-Back Reviews play a crucial role in ensuring regulatory compliance in the financial sector. While the process may be complex, the benefits it offers in terms of risk mitigation and compliance enhancement are invaluable. As regulatory environments continue to evolve, Look-Back Reviews will remain a significant tool in safeguarding financial institutions and fostering trust within the financial ecosystem.
Customer Due Diligence
Customer Due Diligence (CDD) is a crucial process for financial institutions aiming to prevent money laundering and other financial crimes. It involves verifying a customer's identity, assessing their risk level, and continuously monitoring their transactions. In this blog, we will explore the importance of CDD, the steps involved, and how cutting-edge technologies can enhance your institution's compliance efforts.
What is Customer Due Diligence (CDD)?
Customer Due Diligence (CDD) is the process by which financial institutions gather and evaluate information about a customer to assess the risk they pose. This involves verifying the customer's identity, understanding their financial activities, and determining if they engage in any suspicious behaviour. CDD is a key component of Anti-Money Laundering (AML) regulations, helping institutions prevent illegal activities like money laundering and fraud.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Importance of Customer Due Diligence
CDD Prevents Financial Crimes
Customer Due Diligence plays a crucial role in preventing financial crimes, such as money laundering and terrorist financing. By thoroughly understanding who their customers are, financial institutions can identify and mitigate potential risks.
Legal and Financial Risks of Non-Compliance
Failing to comply with CDD requirements can lead to severe penalties, both legal and financial. Institutions risk damaging their reputation and losing trust if they do not properly implement CDD processes.
Types of Customer Due Diligence
Simplified Due Diligence (SDD)
Simplified Due Diligence is applicable in cases where the risk of money laundering or terrorist financing is considered low. This type of due diligence requires fewer verification procedures, making it more streamlined and less burdensome for businesses. However, it is essential to conduct periodic reviews to ensure continued eligibility for SDD.
Standard Due Diligence (STDD)
Standard Due Diligence is the most common type of due diligence conducted by businesses. It involves comprehensive customer identification, risk assessment, and ongoing monitoring. STDD is applicable to most customers and forms the foundation of a robust CDD process.
Enhanced Due Diligence (EDD)
Enhanced Due Diligence (EDD) refers to the comprehensive process of gathering and analyzing additional information about customers or business entities that pose higher risk levels. The primary purpose of EDD is to obtain a deeper understanding of the customer's background, business operations, sources of funds, and potential risk factors.
Differences Between Customer Due Diligence (CDD) and Enhanced Due Diligence (EDD)
When to Use Enhanced Due Diligence
Enhanced Due Diligence (EDD) is necessary when a customer is deemed high-risk. This includes situations where the customer is from a high-risk country or is involved in complex transactions. EDD involves a deeper investigation and more stringent monitoring compared to standard CDD.
In practice, EDD might involve scrutinising the source of funds or conducting more frequent transaction reviews. For example, a politically exposed person (PEP) would require EDD due to their higher risk of being involved in financial crime.
How to Perform Effective Customer Due Diligence
Step-by-Step Guide to the CDD Process
Customer Due Diligence begins with verifying the customer's identity, which is a fundamental step to ensure you know who you are dealing with. This typically involves collecting documents like passports, utility bills, or other official identification. Verification helps confirm that the customer is who they claim to be, reducing the risk of fraudulent activities.
Once the identity is verified, the next step is creating a detailed risk profile for the customer. This involves assessing various factors, such as the customer’s geographical location, the type of business they are involved in, and their transaction history. By understanding these aspects, financial institutions can better predict potential risks and take appropriate measures to mitigate them.
Ongoing monitoring is the third crucial step in the CDD process. After establishing a customer's risk profile, institutions must continuously monitor their transactions for any signs of unusual activity. This is important because risks can evolve over time, and ongoing monitoring helps detect any changes in a customer's behaviour that may indicate a shift in risk level.
Best Practices for Implementing CDD
To implement Customer Due Diligence effectively, a risk-based approach is essential. This means that not all customers are treated equally; higher-risk customers should undergo more thorough scrutiny. For instance, customers from countries with weaker anti-money laundering regulations may require additional checks compared to those from countries with stricter controls.
Leveraging advanced technology is also critical in enhancing the CDD process. Tools like artificial intelligence and machine learning can help automate and streamline identity verification and risk assessment. These technologies can process large volumes of data quickly and accurately, identifying patterns that may not be obvious through manual checks. This not only improves efficiency but also reduces the likelihood of human error.
Challenges in Customer Due Diligence and How to Overcome Them
Managing Complex Ownership Structures
One of the significant challenges in Customer Due Diligence is dealing with complex ownership structures, particularly in corporate customers. These structures can involve multiple layers of ownership, including shell companies or trusts, making it difficult to identify the true beneficial owner. Without clear visibility into the ownership hierarchy, financial institutions risk unknowingly facilitating money laundering or other illegal activities.
To overcome this challenge, institutions should adopt enhanced due diligence (EDD) practices for complex entities. This might involve deeper investigations into the ownership structure, including verifying the identities of all individuals involved, no matter how many layers are present. Leveraging technology that specialises in tracing and mapping ownership structures can also be invaluable in gaining a clear understanding of the customer’s true risk profile.
Staying Compliant with Evolving Regulations
Regulations around Customer Due Diligence are constantly evolving, as governments and regulatory bodies strive to close loopholes and respond to new threats. Keeping up with these changes can be challenging for financial institutions, especially those operating in multiple jurisdictions with different regulatory requirements. Failure to comply with the latest regulations can lead to significant fines, legal consequences, and damage to an institution’s reputation.
To manage this, institutions should invest in continuous training for their compliance teams, ensuring they are always up-to-date with the latest regulations and best practices. Additionally, using adaptable compliance software that can be easily updated in response to regulatory changes can help institutions stay compliant. Regular audits and reviews of CDD processes are also crucial to ensure ongoing adherence to regulations and to identify any areas that may need improvement.
How Customer Due Diligence Protects Against Money Laundering and Other Financial Crimes
Customer Due Diligence serves as a critical line of defence against money laundering. By thoroughly vetting customers during onboarding and continuously monitoring their transactions, financial institutions can detect and prevent the flow of illicit funds. Effective CDD processes help ensure that the institution is not being used as a conduit for laundering money, thus protecting its reputation and maintaining regulatory compliance.
In addition to preventing money laundering, CDD plays a crucial role in counter-terrorism financing (CTF). By identifying and assessing the risk profiles of customers, institutions can flag and investigate suspicious activities that may indicate the funding of terrorist activities. This proactive approach helps mitigate the risk of the institution being involved in criminal activities and contributes to global security efforts.
Customer Due Diligence in Different Industries
Customer Due Diligence in Banking
In the banking sector, Customer Due Diligence plays a critical role in preventing financial crimes such as money laundering and fraud. Banks are required to establish the identity of their customers, verify the source of their funds, and assess their risk profiles. Robust CDD measures help banks maintain regulatory compliance, protect their reputation, and ensure the integrity of the financial system.
Customer Due Diligence in Financial Services
Beyond traditional banking, financial service providers, such as investment firms and insurance companies, also implement Customer Due Diligence procedures. These institutions need to understand the financial backgrounds of their clients, assess their risk tolerance, and ensure compliance with regulatory frameworks. By conducting thorough CDD, financial service providers can make informed decisions, tailor their services, and mitigate potential risks.
{{cta('f24d2361-d707-461c-b808-c29f64ebda60','justifycenter')}}
How Can Tookitaki Enhance CDD?
Customer Due Diligence (CDD) is a fundamental aspect of AML compliance, essential for preventing financial crimes like money laundering and terrorism financing. By implementing thorough CDD processes, financial institutions can protect themselves from legal risks and maintain their reputations. As the financial landscape evolves, adopting advanced technologies like AI will be crucial in enhancing CDD practices and staying ahead of emerging threats.
These technologies enable financial institutions to stay ahead of emerging threats and regulatory changes, ensuring comprehensive and effective risk management. Platforms like Tookitaki’s FinCense leverage collective intelligence and advanced analytics to provide unparalleled risk coverage and real-time responsiveness, making them indispensable tools in the fight against financial crime.
Explore how Tookitaki’s FinCense Platform can revolutionise your CDD processes. Stay compliant, reduce risks, and safeguard your institution against financial crime.
White Collar Crime
Have you ever wondered about the unseen culprits, those who don’t need masks or
weapons to wreak havoc?
Step into the captivating realm of white-collar crime, where deception lurks behind polished corporate exteriors and the battleground shifts to the sophisticated offices of corporate giants. In a digital era where technology and finance merge seamlessly, unravelling the complexities of these financial wrongdoings becomes paramount. White-collar crime, representing non-violent yet impactful financial transgressions, lies at the core of this exploration.
Key Takeaways
- DNFBPs serve as crucial gatekeepers in the financial ecosystem, scrutinizing high-value transactions to identify and report suspicious activities related to money laundering and terrorist financing.
- The challenges faced by DNFBPs include managing compliance with varied AML and CFT regulations, implementing effective customer due diligence, maintaining transaction records, fulfilling reporting obligations, and ensuring continuous training and awareness among staff.
- FATF requirements for DNFBPs emphasize conducting thorough risk assessments, applying consistent customer due diligence measures, maintaining transaction and customer records, reporting suspicious transactions promptly, and establishing robust internal controls and policies.
- DNFBPs play a vital role in the fight against money laundering (AML) and terrorist financing (CFT) by adhering to regulations, managing risks, ensuring compliance, safeguarding their reputation, and strengthening global financial security.
- Ensuring adherence to AML and CFT regulations not only safeguards DNFBPs from potential legal and reputational risks but also fortifies the global financial system against the threats of illicit financial activities.
What is White Collar Crime?
White collar crime are non-violent, financially motivated offenses committed by individuals, businesses, or government professionals. These crimes, often conducted within office settings, involve deceit, concealment, or violation of trust, and are primarily driven by financial gain.
The number of white-collar crimes has been on the surge globally. In Hong Kong, officials reported a 45% increase in white collar crimes in 2022, compared to the year before. In 2019, India experienced an 80% growth rate in white collar crimes. To stop the increase in white collar crimes, it is crucial to have an understanding of what is white collar crime and its types.
Understanding and Types of White-Collar Crimes
In the digital age, comprehending what is white-collar crime and its diverse array of types is pivotal for businesses, individuals, and law enforcement agencies alike. Here are some of the common types of white-collar crimes.
- Embezzlement: One of the most common forms, embezzlement involves the misappropriation of funds entrusted to an individual, leading to significant financial losses for organizations.
- Insider Trading: A practice prevalent in the stock market, insider trading occurs when individuals trade stocks based on non-public, confidential information, resulting in unfair advantages and market manipulation.
- Fraud: Fraud is characterized by a multitude of deceptive strategies, where individuals or entities manipulate information or resort to deceitful practices to secure personal or financial advantages. Financial systems need to continuously identify patterns of fraudulent activities to prevent economic damage.
- Identity Theft: In the digital era, identity theft has become increasingly sophisticated. Criminals use stolen identities for various financial crimes, causing severe repercussions for victims.
- Corporate Espionage: This type involves stealing trade secrets, intellectual property, or confidential information from one company to benefit another, leading to unfair competition and financial losses.
Understanding what is white collar crime extends beyond mere awareness; it requires vigilance, education, and stringent measures to prevent and combat these offenses. By recognizing what is the most common white-collar crime, businesses and individuals can fortify their defenses against these sophisticated financial crimes, ensuring a safer, more secure corporate environment.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
White Collar Crime Examples
You might ask what is an example of white collar crime. Well, one example of white-collar crime is price collusion, a practice where corporations conspire to fix prices of goods or services. This unethical move aims to secure artificially high profits while stifling fair market competition, a detrimental blow to both consumers and competitors.
Another example includes manipulating test reports for pharmaceutical products to fraudulently obtain manufacturing licenses. In this scheme, corrupt individuals manipulate data to meet regulatory standards, masking potentially dangerous products behind a veil of false legitimacy. This not only endangers public health but also exposes the pharmaceutical industry to ethical and legal issues.
Furthermore, white-collar criminals may resort to substituting cheap, defective materials for costlier components specified in the construction of vital infrastructure such as roads or buildings. Despite charging clients for high-quality materials, these deceitful practices compromise the structural integrity of projects, posing risks to public safety.
Real-Life Examples of White Collar Crime
- Wells Fargo Fake Accounts Scandal (2016)
Employees at Wells Fargo, one of the largest banks in the United States, were found to have opened millions of unauthorized bank and credit card accounts in customers' names. This deceptive practice was driven by aggressive sales targets and incentives, leading employees to engage in fraudulent activities without customers' knowledge or consent. The scandal resulted in a fine of $185 million, led to the resignation of top executives, and damaged the bank's reputation. - Volkswagen Emissions Scandal (2015):
Volkswagen deliberately installed software in their vehicles to manipulate emissions tests, presenting false data about their cars' environmental impact. This white-collar crime resulted in billions of dollars in fines, legal actions, and damage to the company's reputation for violating environmental standards. - Bernie Madoff's Ponzi Scheme (2008):
Bernie Madoff orchestrated one of the largest Ponzi schemes in history, defrauding investors of billions of dollars. He promised high returns but used new investors' funds to pay returns to earlier investors, creating a facade of a profitable investment business. The scheme unraveled in 2008, causing significant financial losses to many individuals and organizations.
Impact of What Collar Crime
Beyond monetary losses, the repercussions of these crimes reverberate across economies and societies, shaping public trust and economic stability.
- Economic Downturn: White-collar crimes, such as corporate fraud and embezzlement, can trigger economic downturns, leading to job losses, reduced investments, and diminished consumer confidence. Such downturns affect businesses of all scales, from small enterprises to multinational corporations, amplifying economic instability.
- Consumer Trust Erosion: Fraudulent activities erode consumer trust in businesses and financial institutions. When consumers lose faith in the integrity of these entities, it leads to decreased spending, hampering economic growth and recovery efforts.
- Legal Costs and Reputational Damage: Businesses involved in white-collar crime scandals face exorbitant legal fees and fines, draining resources that could be used for innovation and growth. Additionally, the long-lasting reputational damage can deter potential investors and customers, hindering business expansion.
- Impact on Small Businesses: Small businesses, often lacking robust security measures are particularly vulnerable to white-collar crimes. Incidents like online fraud and identity theft can cripple these enterprises, leading to closures and job losses in local communities.
- Social Inequality: White-collar crimes exacerbate social inequalities by siphoning resources away from public services. When corporations avoid paying taxes or participate in fraudulent activities, it diminishes the resources allocated for education, healthcare, and social welfare programs. This disproportionately impacts vulnerable communities, limiting their access to essential services and support.
- Global Economic Impact: With the rise of digital transactions and interconnected financial markets, white-collar crimes can have global implications. A major financial fraud in one country can send shockwaves through international markets, destabilizing economies worldwide.
White Collar Crime and Money Laundering
From a money laundering perspective, white-collar crimes often intertwine with illicit financial activities. Criminal organizations exploit their ill-gotten gains by laundering money through seemingly legitimate businesses, concealing the origins of their funds. This intricate web of deception involves complex financial transactions, making it challenging for authorities to trace and seize unlawfully acquired assets. Money laundering plays a significant role in the continuation of white-collar crimes while also driving a continuous cycle of fraud and deceit through its contribution to other criminal activities.
Detection and Prevention of White-Collar Crime
Understanding what is white collar crime is essential, but it is equally crucial to adopt proactive strategies that detect potential threats and prevent these sophisticated offenses from tarnishing the integrity of businesses. Here are some of the ways to detect and prevent white collar crimes.
- Data Analytics and AI: Leveraging advanced data analytics and artificial intelligence (AI) technologies are paramount in detecting fraudulent activities. AI algorithms can sift through vast datasets, identifying anomalies and flagging suspicious transactions in real time, allowing for immediate intervention. The Anti-Money Laundering (AML) suite and Anti-Financial Crime (AFC) Ecosystem products offered by Tookitaki helps in combating white collar crimes efficiently.
- Whistleblower Programs: Establishing robust whistleblower programs within organizations encourages employees and stakeholders to report suspicious or unethical activities. Whistleblower anonymity guarantees a safe environment for reporting, acting as a valuable tool in uncovering internal white-collar crimes.
- Employee Education and Training: Educating employees about the nuances of white-collar crimes and common fraud tactics is a foundational step. Regular training programs empower staff to recognize potential threats, making them the first line of defense in preventing internal offenses.
- Internal Controls and Audits: Implementing stringent internal controls, coupled with regular audits, ensures transparent financial practices. These measures not only deter potential white-collar criminals within the organization but also provide crucial insights into areas susceptible to exploitation.
- Regulatory Compliance: Staying up-to-date with new regulatory activities and compliance standards are vital. Compliance not only mitigates legal risks but also nurtures an environment of accountability, deterring both internal and external fraudulent activities.
{{cta('dea13f0a-4218-49bd-b1e7-70414104d5d5','justifycenter')}}
Conclusion
In the world of white-collar crime, awareness is the strongest shield. By understanding its intricacies, businesses can fortify their defenses and protect their integrity. From detecting fraud with advanced technologies, such as those provided by Tookitaki, to foster a culture of transparency and compliance, the path forward is clear. Vigilance and education are the best tools against these unseen adversaries.
Frequently Asked Questions (FAQs)
What is white collar crime?
White-collar crime comprises non-violent offenses motivated by financial gain, typically perpetrated by either individuals or groups of professionals.
What are the most common types of white collar crimes?
Common types include embezzlement, insider trading, fraud, bribery, and identity theft.
How do white collar crimes impact the economy and society?
White collar crimes lead to financial losses, increased costs for consumers, job losses, and reduced trust in institutions.
What role do regulatory agencies play in combating white collar crime?
Regulatory agencies enforce laws, conduct investigations, and implement measures to prevent and punish white collar crimes.
How are white collar crimes typically investigated?
Investigations involve data analysis, whistleblowing, and collaboration between law enforcement and regulatory agencies.
Human Trafficking
A despicable transgression of basic human rights, human trafficking stands as a dark reality looming over the global landscape. This reprehensible act, responsible for inflicting unimaginable distress and torment upon countless individuals, spans across continents, penetrating communities far and wide. The essence of this horrifying practice boils down to the illicit trafficking of innocent people, treating them as mere commodities for the purpose of exploitation and for reaping unwarranted commercial benefits.
The ramifications of human trafficking are manifold, leading to an array of social, psychological, and physical consequences for those unfortunate enough to fall prey to this clandestine trade. As victims, these individuals are subjugated to severe maltreatment that can encompass physical abuse, psychological trauma, forced labour, sexual exploitation, and other forms of inhumane treatment.
To embark on an effective course to combat and eventually eradicate this persistent issue, it is imperative first to cultivate a profound understanding of the underlying causes of human trafficking. This necessitates dissecting the various socio-economic, political, and cultural factors that foster an environment conducive to the flourishing of this illicit trade. Issues such as poverty, unemployment, political instability, armed conflict, and gender discrimination often serve as catalysts, creating vulnerabilities that traffickers ruthlessly exploit.
The complexity of human trafficking extends beyond its causes; it takes various forms depending on the purpose of exploitation. This ranges from forced labour and debt bondage, where victims are made to work under threat or coercion without just compensation, to sex trafficking and child exploitation, which involve the commercial sexual exploitation of adults and children, respectively. Understanding these types gives a wider perspective into the multifaceted nature of human trafficking, highlighting the necessity for equally diverse and tailored solutions.
Additionally, an examination of the statistics pertaining to human trafficking further underlines the magnitude and global reach of the problem. These numerical figures, reflecting the number of victims, their age and gender distribution, the share of transnational and domestic trafficking, and more, provide a stark illustration of the pervasiveness and severity of the issue.
Lastly, it is vital to focus on the lived experiences of victims through the lens of real-world examples and case studies. Such a personal and tangible insight into the harsh realities faced by victims of human trafficking allows for the cultivation of empathy and a better understanding of the urgent need for action. Financial institutions play a role in combating human trafficking by employing stringent identity verification processes and promptly reporting suspicious activity.
Key Takeaways
- Human trafficking is a global issue affecting millions of people, with victims often forced into sexual exploitation or labour.
- Key causes of human trafficking include poverty, lack of education, political instability, and natural disasters.
- There are various types of human trafficking, including sex trafficking, forced labour, and debt bondage.
- Victims often come from vulnerable groups, including children, women, refugees, and the economically disadvantaged.
- Addressing human trafficking requires a comprehensive, global response that includes legal, social, and economic strategies.
- By raising awareness and strengthening preventative measures, we can contribute to the fight against this horrific crime and help protect vulnerable populations.
Understanding Human Trafficking
At its very essence, the nefarious act of human trafficking represents a contemporary manifestation of slavery, an anachronistic but nonetheless persisting evil that has managed to permeate into our modern society. This reprehensible practice, underpinned by an array of manipulative tactics, thrusts its victims into situations that are nothing short of indentured servitude, effectively robbing them of their basic human rights and freedoms.
These coercive tactics are often an insidious blend of deception and force. In some instances, traffickers cunningly prey on the vulnerabilities of their victims, presenting them with false promises of a better life, only to ensnare them into their illicit trade. In other situations, brute force is employed, brutally stripping victims of their autonomy and thrusting them into a life of enforced servitude.
Upon their capture, these victims, stripped of their freedoms, find themselves ensnared in a variety of exploitative circumstances. Among the most pervasive forms of exploitation is sexual servitude. This form of trafficking capitalises on the vulnerability and desperation of its victims, thrusting them into the commercial sex trade where they are repeatedly abused and degraded.
Another frequent form of human trafficking is forced labour, which sees victims coerced into performing arduous work in inhumane conditions, often without adequate compensation. This form of exploitation is not industry-specific and spans multiple sectors such as agriculture, construction, domestic work, and manufacturing.
There are also instances where victims are forced into various other forms of servitude, such as forced marriage or the illicit organ trade. These forms, while not as prevalent as sexual exploitation or forced labour, still represent a significant proportion of human trafficking cases and contribute to the overall grim reality of this illicit trade.
Human trafficking is a gross violation of human dignity and rights, plunging its victims into a life of servitude, exploitation, and suffering against their will. It stands as a chilling testament to the depths of human cruelty and ruthlessness, making it an issue of grave concern that calls for immediate and concerted global action.
Statistics on Human Trafficking
A careful examination of global human trafficking statistics paints a stark and disquieting picture. Data gathered from reputable sources such as the United Nations Office on Drugs and Crime (UNODC) suggests that this egregious crime is a pervasive issue that knows no boundaries—geographical, social, or economic.
UNODC reports shed light on the extensive reach of human trafficking. The crime has been reported in a staggering total of 148 nations. This figure alone underscores the global prevalence of this illicit trade, demonstrating how it spans countries, continents, and oceans, cutting across cultures and societies, and impacting economies of every scale, from the most impoverished to the most affluent.
What's more, these reports expose the vast numbers of people ensnared in this horrifying practice. An estimated 25 million individuals across the globe find themselves victimised by human trafficking. To comprehend the magnitude of this figure, one might envision the entire population of a mid-sized country, every single man, woman, and child, subjected to such gross human rights violations. The sobering reality is that these millions of victims are not mere statistics but individuals with their dreams, aspirations, and potential brutally stripped away by their captors.
In essence, the reach of human trafficking extends to every corner of the globe, infiltrating every continent and affecting every economic structure. It is a crime of immense proportions that leaves millions of lives blighted in its wake. And while statistics can begin to quantify the scope of this dire human rights issue, they can scarcely convey the depth of individual suffering that defines each instance of human trafficking.
Causes of Human Trafficking
This illicit trade in human lives thrives on a complex interplay of factors, each contributing to the creation of a fertile breeding ground for traffickers to operate.
One of the primary driving forces behind human trafficking is the spectre of poverty. In areas stricken by extreme financial hardship, individuals and families may be lured by deceptive promises of well-paid work or better living conditions, making them easy prey for unscrupulous traffickers.
Another significant factor is the lack of access to quality education. Without the empowerment that comes from knowledge and learning, individuals may lack the awareness to identify potential traps set by traffickers or may be unable to access better, safer opportunities, thus falling into the hands of these criminals.
Political instability also plays a considerable role in this grim tableau. In regions where the rule of law is weak or non-existent, where governments are unstable or corrupt, the resulting power vacuums and lack of legal enforcement can be ruthlessly exploited by human traffickers.
Similarly, areas afflicted by armed conflict become vulnerable hotspots for this illicit activity. The chaos, displacement, and social disruption caused by wars and civil unrest often lead to a rise in trafficking as opportunistic criminals exploit vulnerable conditions.
Lastly, natural disasters contribute to the problem as well. Following an earthquake, flood, or other catastrophes, the ensuing chaos, desperation, and infrastructure damage create an environment ripe for exploitation by human traffickers.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
Types of Human Trafficking
There exist different manifestations of human trafficking, which are contingent on the nature of exploitation. Some of the prevailing categories include sex trafficking, forced labour, and debt bondage, whereas less familiar types are composed of forced matrimony and organ trafficking.
Furthermore, it is important to recognize that victims of human trafficking can come from any background, gender, age, or ethnicity. The practice of trafficking humans is a severe violation of human rights and has significant physical and psychological effects on its victims.
To combat human trafficking, international laws and national legislation have been established to protect individuals from being exploited. It is also crucial to raise awareness and educate communities about the dangers associated with human trafficking to prevent people from becoming victims in the first place.
It is the responsibility of each individual to become informed about the issue of human trafficking and to take action to help those who are affected. Together, we can work towards eradicating this heinous crime and ensuring a safer and more just world for all.
Victims of Human Trafficking
Victims of human trafficking may have varying origins. However, certain groups who are more susceptible to exploitation tend to suffer a disproportionate impact. Such groups include children, women, refugees, and persons who face economic disadvantage.
It is important to note that human trafficking can occur within countries, across borders, and even online. In recent years, there has been a growing recognition of the severity of this global issue and efforts to combat it have intensified. By raising awareness, increasing law enforcement efforts, providing support to victims, and addressing the root causes, we can work towards eradicating this heinous crime and protecting those who are at risk.
{{cta('f24d2361-d707-461c-b808-c29f64ebda60','justifycenter')}}
Human Trafficking Cases and Examples
Human trafficking is a grave issue that affects millions of people worldwide. By examining real-life cases and examples, we can gain a deeper understanding of the harrowing realities faced by victims and the challenges they encounter in their journey towards freedom and recovery.
1. Case Study: Maria's Story
Maria, a young woman from a poverty-stricken region, fell victim to human traffickers promising her a better life abroad. Instead, she was forced into labour exploitation and subjected to physical and emotional abuse. After a courageous escape, Maria found refuge in a support organization that helped her rebuild her life.
2. Example: Forced Commercial Sexual Exploitation
In countless instances, vulnerable individuals, including children and women, are coerced or deceived into engaging in commercial sexual activities against their will. This form of trafficking involves the use of physical and psychological control to exploit victims for financial gain.
3. Case Study: The Plight of Child Laborers
Child labour is a distressing consequence of human trafficking, affecting millions of children worldwide. Many are forced into hazardous work environments, denied education, and subjected to physical harm. Efforts by organizations and governments to combat child labor are vital in providing these children with a chance for a better future.
4. Example: Debt Bondage
Debt bondage is a prevalent form of human trafficking, particularly in industries such as agriculture and domestic work. Victims are trapped in a cycle of debt, forced to work tirelessly to repay inflated sums, often enduring harsh living conditions and exploitation.
5. Case Study: The Resilience of Survivors
Despite the immense challenges faced by survivors of human trafficking, their stories of resilience and strength inspire hope. Many survivors go on to become advocates, helping raise awareness, support fellow survivors, and drive change in policies and practices.
These real-life cases and examples highlight the urgent need for concerted efforts to combat human trafficking. By understanding the complexities and horrors of this crime, we can work towards creating a safer and more just world for all.
Addressing Human Trafficking
Addressing human trafficking requires a comprehensive, global response. This includes strengthening legal frameworks, enhancing victim support services, improving law enforcement and judicial capacities, raising public awareness, and addressing the root causes.
Inherent Risk
In the realm of risk assessment and management, the concept of inherent risk plays a critical role. Inherent risk refers to the level of risk that exists in an activity, process, or organization without considering any internal controls or risk mitigation efforts. It is the baseline level of risk inherent in the nature of the business or operation itself.
Understanding inherent risk is essential for auditors, risk managers, and decision-makers to evaluate and address potential risks effectively. Assessing the inherent risk in certain financial transactions can help tailor appropriate levels of customer due diligence to prevent issues like embezzlement. This article will delve into the concept of inherent risk, its implications, and how it is managed in various contexts.
Key Takeaways
- Inherent risk refers to the level of risk that exists in an activity or process before considering any internal controls or risk mitigation efforts.
- It plays a vital role in risk management, enabling organizations to identify and prioritize potential risks.
- Inherent risk should be distinguished from residual risk, which represents the remaining risk after implementing controls.
- Auditors assess inherent risk to determine appropriate audit procedures and resource allocation.
- Factors such as industry dynamics, regulatory requirements, and complexity of operations influence the level of inherent risk.
- Managing complex inherent risks requires robust risk management frameworks, advanced technologies, and a risk-aware culture.
The Definition and Significance of Inherent Risk
Inherent risk represents the level of risk inherent in an activity or process before considering any controls or risk mitigation measures. It is an essential component of risk assessment, providing a foundation for identifying and prioritizing potential risks.
Inherent risk takes into account factors such as the nature of the business, industry-specific risks, external influences, and internal vulnerabilities. Recognizing and evaluating inherent risk allows organizations to develop appropriate risk management strategies and allocate resources effectively.
Examples of Inherent Risk
To grasp the concept of inherent risk more effectively, let's explore a few examples across different industries:
- Financial Industry: Inherent risk in a financial institution may include exposure to market volatility, credit default risk, and potential regulatory changes.
- Manufacturing Sector: Inherent risk in a manufacturing process may involve equipment failure, supply chain disruptions, and product quality issues.
- Information Technology: Inherent risk in IT operations may encompass cybersecurity threats, data breaches, and system vulnerabilities.
Inherent Risk in Risk Management
Inherent risk is a fundamental consideration in risk management processes. It helps identify areas of high risk that require special attention and resources. By understanding inherent risk, organizations can tailor risk mitigation strategies and control activities to address specific vulnerabilities and reduce the overall level of risk. Effective risk management involves a systematic approach to evaluating, monitoring and responding to inherent risks.
Inherent Risk vs Residual Risk
It is important to differentiate between inherent risk and residual risk. While inherent risk refers to the risk level before implementing controls, residual risk represents the risk that remains after applying controls or mitigation measures. Residual risk considers the effectiveness of controls and provides insights into the overall risk exposure despite risk mitigation efforts.
Inherent Risk in Auditing
Auditors play a crucial role in assessing inherent risk as part of the audit process. Evaluating inherent risk helps auditors determine the nature, timing, and extent of audit procedures necessary to obtain reasonable assurance about the accuracy of financial statements. Auditors assess inherent risk factors, such as industry complexity, management integrity, and regulatory changes, to develop appropriate audit strategies and allocate resources efficiently.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
Factors Influencing Inherent Risk
Several factors can influence the level of inherent risk within an organization or process. These factors include industry dynamics, regulatory requirements, the complexity of operations, the competence of personnel, technological advancements, and the economic environment. Understanding these factors enables organizations to prioritize risk management efforts and allocate resources effectively.
Control Risk vs Inherent Risk
Control risk and inherent risk are interrelated but distinct concepts in risk assessment. While inherent risk focuses on the risk level before controls, control risk relates to the risk that internal controls may not prevent or detect a material misstatement. Evaluating control risk involves assessing the effectiveness of existing controls in mitigating inherent risk.
Managing Inherent Risk Complexity
Inherent risk can vary in complexity based on the nature of the business and industry. Organizations must develop strategies to manage complex inherent risks effectively. This may involve implementing robust risk management frameworks, adopting advanced technologies, enhancing internal controls, and fostering a risk-aware culture within the organization.
Understanding and effectively managing inherent risk is crucial for organizations across various industries. By comprehending its implications and adopting appropriate risk management strategies, businesses can proactively address potential risks, protect their assets, and make informed decisions to achieve their objectives.
Drug Trafficking
Drug trafficking, a dangerous and illegal trade, is causing immense harm worldwide. Criminals smuggle huge amounts of drugs. According to estimates, $32 billion worth of drugs are smuggled across countries. This affects millions of lives globally. This data, gathered from sources such as the United Nations Office on Drugs and Crime (UNODC), paints a grim picture of the scale of this problem.
In this article, we will explore what is drug trafficking meaning. Furthermore, we’ll also explore how it is linked to money laundering. Let's uncover the truth behind drug trafficking and learn how we can work together to make our communities safer.
Key Takeaways
- Drug Trafficking's Global Impact: With an estimated $32 billion in drugs smuggled annually, drug trafficking poses a major international challenge, affecting millions of lives and requiring global efforts to combat it.
- Connection to Money Laundering: The massive profits from drug trafficking are often laundered, with criminals using sophisticated techniques to disguise illegal gains as legitimate funds.
- Role of International Organizations: Agencies like UNODC, INTERPOL, WCO, DEA, and OAS play crucial roles in fighting drug trafficking and money laundering through intelligence sharing, training, and international cooperation.
- Innovative AML Strategies: Advanced AML methods, including AI and ML technologies, are key in detecting and disrupting the financial networks behind drug trafficking.
- Comprehensive Compliance Measures: Financial institutions implement enhanced surveillance, AML screening, CDD, risk assessment models, and behavioral analytics to combat drug trafficking-related money laundering.
What is Drug Trafficking?
Drug trafficking involves the illegal trade, transportation, and distribution of narcotics and controlled substances across international borders and within countries. Economic disparities and lack of employment opportunities in certain regions are among the common causes of drug trafficking.
Illicit activities don't just benefit organized crime. They also harm communities by causing more violence, addiction, and social instability. Global law enforcement agencies have a tough job trying to stop this. So it's crucial to come up with new strategies and work together to tackle the widespread impact of drug trafficking.
Now that you know about drug trafficking meaning, let us discuss the connection between drug trafficking and money laundering.
Drug Trafficking and Money Laundering
Drug trafficking and money laundering form a sophisticated web of criminal activity. The vast profits generated from drug trafficking are often tainted and need to be legitimized through money laundering techniques. Money laundering is the process of camouflaging illegal proceeds as legal funds. This enables criminals to utilize their ill-gotten gains without raising suspicion.
To make their operations successful, drug traffickers use different tactics. They invest in real businesses, get involved in real estate deals, and use financial institutions to move money secretly. Additionally, they employ intricate networks of shell companies, offshore accounts, and intermediaries to obfuscate the origins of their money, making it challenging for authorities to trace. To know how it is done, consider the below scenario.
Imagine a drug trafficking syndicate operating internationally, smuggling narcotics across borders and selling them illicitly. The profits amassed from these illegal activities are substantial but inherently suspicious. To legitimize these funds and integrate them into the legal economy, the criminals’ resort to money laundering techniques.
First, they invest in seemingly legitimate businesses, such as restaurants or retail outlets. By doing this, they blend their unlawfully earned money with the legitimate profits from these businesses. This makes it hard for authorities to tell the difference between legal and illegal income.
Next, the criminals engage in real estate transactions, purchasing luxury properties using the tainted money. These properties serve as assets, and their value appreciates over time, allowing the criminals to increase their wealth while appearing to be legitimate property owners.
Simultaneously, they exploit financial institutions, transferring funds internationally through a complex web of accounts. Offshore accounts and shell companies are established, creating layers of anonymity that makes it difficult for investigators to trace the original source of the funds.
In response to this pervasive issue, governments have enacted stringent laws and regulations. Financial institutions are mandated to implement various measures. This includes thorough customer due diligence, constant transaction monitoring, and reporting any suspicious activities to law enforcement agencies. These regulations enable authorities to detect and thwart money laundering attempts.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d')}}
International Organizations Against Drug Trafficking
A multitude of international organizations is dedicated to combating drug trafficking, promoting cooperation between nations, and implementing strategies to eradicate this global menace. These organizations are crucial. They help share intelligence, encourage collaboration, and support nations in their efforts to combat crimes related to drugs.
- United Nations Office on Drugs and Crime (UNODC): UNODC takes a multifaceted approach to tackle drug trafficking and money laundering. They provide technical assistance to member states, assisting them in strengthening their legal frameworks, law enforcement capacities, and international cooperation mechanisms.
- INTERPOL: INTERPOL plays a vital role in combating drug trafficking and money laundering by facilitating international police cooperation. They coordinate joint operations, share intelligence, and provide operational support to member countries.
- World Customs Organization (WCO): WCO focuses on strengthening customs administrations globally to intercept drug shipments and combat money laundering. They provide training and technical assistance to customs officers, enhancing their capabilities in detecting concealed narcotics and illicit financial transactions at borders.
- Drug Enforcement Administration (DEA): DEA operates internationally to disrupt and dismantle major drug trafficking organizations. They conduct undercover operations, gather intelligence, and collaborate with foreign law enforcement agencies to target key individuals and networks involved in drug trafficking and money laundering.
- Organization of American States (OAS): OAS focuses on strengthening the institutional capacities of member states to combat drug trafficking and money laundering. They provide technical assistance, policy guidance, and support in developing comprehensive strategies to address the root causes of these issues.
Agencies like the IRS, Federal Reserve, and Treasury. FinCEN, are also at the forefront of combating financial crimes like money laundering. FinCEN, operating under the United States Treasury, utilizes advanced artificial intelligence technology to analyze Currency Transaction Reports (CTRs). These reports are mandatory filings for individuals receiving cash payments exceeding $10,000.
Combating Drug Trafficking with AML Methods And Technologies
Anti-Money Laundering (AML) methods have become instrumental in the fight against drug trafficking. By using sophisticated analytics, AI and ML, authorities can spot patterns and trace illegal money movements. This helps in breaking up criminal networks. Here are some of the ways to combat drug trafficking with AML methods and technologies.
- Enhanced Surveillance: Financial institutions need to employ advanced monitoring systems. These systems are essential for spotting irregular transactions associated with drug trafficking. They work by identifying deviations from normal customer behavior. These deviations might include large cash transfers or transactions to high-risk nations. When anomalies are detected, swift investigations and corrective measures are initiated by vigilant financial organizations.
- Artificial Intelligence (AI) and Machine Learning (ML): Leveraging advanced AI and ML technologies, financial organizations analyze vast financial datasets. These technologies identify intricate patterns and anomalies indicative of money laundering connected to drug trafficking. By recognizing these red flags, authorities can take prompt action, disrupting criminal networks and safeguarding the integrity of financial systems.
- AML Screening: During onboarding, financial institutions screen applicants rigorously. Conventional matching engines may yield false positives. However, utilizing multi-dimensional algorithms that combine essential entity data with external information enhances the accuracy of matching outcomes. This approach minimizes errors, ensuring precise identification of potential risks related to drug trafficking and money laundering.
- Customer Due Diligence (CDD): Implementation of CDD measures allows businesses and financial institutions to authenticate customer identities. It also assists in evaluating their risk levels. This examination helps in identifying possible money laundering transactions connected to drug trafficking.
- Risk Assessment Models: Financial institutions utilize risk assessment models to detect high-risk customers and transactions susceptible to money laundering. This also includes those associated with drug trafficking. By focusing resources on these risk areas, institutions can focus on combating illicit activities. This, therefore, ensures AML compliance.
- Behavioral Analytics: Financial institutions use behavioural analytics to study customer behaviour. This also helps in detecting anomalies that might indicate involvement in drug trafficking-related money laundering. By understanding typical customer behaviour, deviations from these patterns become apparent. This enables timely intervention and prevention of illicit financial activities.
{{cta('827dede2-4566-4bf7-a73a-e939b4337e6d','justifycenter')}}
In conclusion, drug trafficking and money laundering are closely intertwined criminal activities that have significant social and economic consequences. Drug trafficking refers to the illegal production, distribution, and sale of drugs, while money laundering involves disguising the proceeds from these illegal activities to make them appear legitimate. The connection between drug trafficking and money laundering is evident as drug traffickers seek to conceal the vast amounts of money generated from their illicit activities.
By understanding this connection, law enforcement agencies and policymakers can develop effective strategies to disrupt and dismantle drug trafficking networks and prevent the flow of illegal funds. Additionally, raising public awareness about the dangers of drug trafficking and its connection to money laundering is essential in promoting a society free from the harms caused by these criminal activities. Ultimately, by understanding the complexities of drug trafficking and money laundering, we can work towards a safer and more secure future for our communities.
Red Flags
Money laundering is a serious and complex issue that poses threats not only to individual organizations but also to economies and societies as a whole. In this comprehensive guide, we will delve into the various aspects of money laundering, including its definition, impact on the economy, legal frameworks, red flags, and the role of financial institutions in combating this criminal activity. Additionally, we will explore advanced techniques and technologies that can aid in the identification and prevention of money laundering.
Understanding Money Laundering
Money laundering refers to the process of disguising the origins of illegally obtained money or assets and making them appear legitimate. It allows individuals and criminal organizations to profit from their illegal activities without drawing attention from law enforcement agencies. To effectively identify money laundering red flags, it is crucial to have a clear understanding of the basics of this illicit practice.
Definition and Basics of Money Laundering
Money laundering typically involves three stages: placement, layering, and integration. During the placement stage, illicit funds are introduced into the financial system. These funds may come from various criminal activities, such as drug trafficking, fraud, or corruption. In the layering stage, the source of the funds is concealed by creating complex transactions and moving funds between multiple accounts and jurisdictions. Finally, in the integration stage, the laundered money is reintroduced into the legitimate economy, making it difficult to trace its illicit origins.
Understanding these three stages is essential for comprehensively identifying money laundering red flags. By recognizing abnormal financial patterns and transactions, authorities and financial institutions can take appropriate action to combat this illicit activity.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Legal Framework Against Money Laundering
To combat money laundering effectively, both international and national efforts are required. International anti-money laundering (AML) standards provide a framework for cooperation and coordination among countries, ensuring a unified approach in the fight against this illicit activity. Additionally, nations enact their own laws and regulations to address specific money laundering risks within their jurisdictions.
Money laundering is a complex and pervasive issue that poses significant challenges to the global financial system. The process involves disguising the origins of illegally obtained funds, making them appear legitimate. This not only enables criminals to enjoy the proceeds of their illicit activities but also threatens the integrity and stability of financial institutions worldwide.
International Anti-Money Laundering Standards
Different organizations and initiatives work towards establishing international AML standards. The Financial Action Task Force (FATF) is one such organization that sets guidelines and promotes effective implementation of measures to combat money laundering and terrorist financing globally. Its recommendations encompass various areas, including customer due diligence, record-keeping, and reporting suspicious transactions.
In addition to the FATF, regional bodies such as the European Union and the Egmont Group also play crucial roles in setting and enforcing AML standards. These organizations facilitate information sharing and collaboration among member countries, strengthening the collective response to money laundering activities across borders.
National Laws and Regulations
Beyond international standards, nations develop their own laws and regulations to confront money laundering within their borders. These laws aim to enhance transparency, promote international cooperation, and provide authorities with the necessary tools to detect and prevent money laundering activities. Financial institutions play a crucial role in complying with these laws and reporting any suspicious transactions that may indicate money laundering.
Furthermore, some countries have established specialized financial intelligence units (FIUs) to analyze and disseminate information related to potential money laundering activities. These units serve as central hubs for receiving, processing, and sharing reports of suspicious transactions, enhancing the effectiveness of anti-money laundering efforts at the national level.
Recognizing the Red Flags of Money Laundering
Effectively identifying money laundering requires vigilance and a keen eye for suspicious activities. By recognizing the red flags associated with money laundering, individuals, financial institutions, and authorities can take necessary steps to investigate and deter illicit financial flows.
Unusual Financial Transactions
Unusual or complex financial transactions often indicate potential money laundering. These transactions may involve large cash deposits or withdrawals, frequent transfers between multiple accounts, or transactions involving high-risk jurisdictions or entities. By closely monitoring such activities, financial institutions can identify potential money laundering attempts and report them to appropriate authorities for further investigation.
Suspicious Customer Behavior
Customers displaying suspicious behavior can raise red flags for money laundering. This may include individuals who consistently make large transactions without an apparent legitimate source of income, exhibit reluctance to provide necessary identification, frequently change personal or business details, or insist on conducting transactions involving third parties without a valid reason. Financial institutions should be alert to such behavior and conduct thorough due diligence before engaging in any transactions.
Inconsistent Business Operations
Inconsistent business operations can also signal potential money laundering activities. Unusual fluctuations in revenue or expenses, sudden changes in business models or customer base, or a lack of transparency in the ownership structure of businesses may indicate attempts to disguise the illicit origins of funds. By carefully examining these inconsistencies, financial institutions can mitigate the risks associated with money laundering and protect themselves from unwitting involvement in criminal activities.
Furthermore, it is important to note that money laundering techniques are constantly evolving. Criminals are becoming increasingly sophisticated in their methods, making it crucial for individuals and institutions to stay updated on the latest trends and techniques used in money laundering. This includes being aware of new technologies and platforms that may be exploited by money launderers, such as cryptocurrencies and online payment systems.
Additionally, collaboration between different stakeholders is essential in combating money laundering. Financial institutions, law enforcement agencies, and regulatory bodies need to work together to share information and intelligence, as well as develop effective strategies to detect and prevent money laundering. This collaboration can help create a robust and coordinated response to the ever-changing landscape of financial crime.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
In conclusion, recognising the red flags of money laundering is a critical step in combating this illicit activity. By being vigilant and staying informed, individuals and institutions can play a crucial role in safeguarding the integrity of the financial system and preventing criminals from profiting from their illegal activities.
As you've learned from this guide, staying ahead of money laundering requires not only vigilance but also advanced tools that evolve with the tactics of financial criminals. Tookitaki's FinCense platform offers an innovative solution to the complex challenges of anti-money laundering and fraud prevention. With our federated learning model and comprehensive suite of tools, including Onboarding Suite, FRAML, Smart Screening, Customer Risk Scoring, Smart Alert Management (SAM), and Case Manager, Tookitaki is equipped to help fintechs and traditional banks identify and respond to financial crime effectively. Our system provides fewer, higher quality alerts, ensuring that your institution can focus on genuine threats and maintain compliance with ease. Don't let your guard down against money laundering—talk to our experts today and learn how FinCense can fortify your financial crime prevention strategies.
Ponzi Schemes
A Ponzi scheme is a deceptive investment operation where the operator generates returns for older investors through revenue paid by new investors. This is instead of legitimate business activities or profit earned through financial trading. Operators entice new participants by offering higher returns than other investments in the form of short-term returns that are either abnormally high or unusually consistent.
Initially, a Ponzi scheme can seem quite sustainable, especially if a consistent flow of new investors contributes to the pool of funds. Typically, these schemes will collapse under their own weight as the earnings, which are required to fulfill the promised returns to earlier investors, become dependent on an ever-increasing influx of money from new investors. This unsustainable model eventually unravels, often leaving many investors out of pocket.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Ponzi Scheme vs Pyramid Scheme
The confusion between Ponzi and pyramid schemes arises from their structural similarities, as both rely on incoming funds from new recruits to pay previous participants. However, a pyramid scheme is more of a business model that requires participants to contribute upfront fees for the opportunity to sell a product or service and recruit others to do the same. The primary way to make money in a pyramid scheme is through recruitment, not sales.
In contrast, Ponzi schemes purport to be legitimate investment strategies without a real product or service. They simply shuffle the money of new investors to pay earlier investors, which can make them appear as successful and solvent operations. Pyramid schemes often collapse when it becomes impossible to recruit new members, whereas Ponzi schemes fail when the flow of new investment isn't enough to cover promised payouts.
Key Differences
- Recruitment: Pyramid schemes explicitly require participants to recruit others to earn profits, while Ponzi schemes promise returns on investments.
- Flow of Money: In Ponzi schemes, returns are paid from the investments of new investors. In pyramid schemes, the money flows upwards from new recruits to senior members.
- Sustainability: While both schemes are unsustainable, Ponzi schemes can potentially last longer as they do not rely on exponential growth through recruitment.
- Facade of Legitimacy: Ponzi schemes often masquerade as legitimate investment opportunities, while pyramid schemes are more straightforwardly about recruitment.
How Do Ponzi Schemes Work?
Ponzi schemes are typically orchestrated by individuals who can convince investors of their trustworthiness and financial acumen. They often claim to have access to innovative or secret investment strategies that are supposed to yield high financial returns. The reality, however, is that the returns are not coming from any investment or business activities, but directly from the cash flow provided by new investors.
Early investors may indeed receive high returns, which persuades them to invest more money and attract others to the scheme. These returns are not a sign of a legitimate operation but are specifically designed to build trust and to lure more investors into the scheme. The illusion of a successful investment continues as long as there is a steady stream of new investors whose funds can be used to pay earlier investors.
As the scheme expands, the operator may have to engage in a variety of tactics to maintain the illusion of a legitimate operation, which can include producing false account statements, staging elaborate events to demonstrate success, or other deceptive practices. In the end, most schemes implode when it becomes impossible to recruit enough new investors to continue to pay the promised returns, or when the operators siphon off the money for personal use and exit the scheme.
Signs of a Ponzi Scheme
Spotting a Ponzi scheme can be challenging, as they're often veiled under the guise of legitimate and attractive investment opportunities. However, some telltale signs may point to the fraudulent nature of an investment. One of the most notable red flags is the promise of high returns with little to no risk; investments that offer rewards that are significantly higher than the market average are often suspect.
Additionally, if the investment strategy is overly complex or secretive, and if the investor is having difficulty understanding how the returns are generated, there is a chance it might be a Ponzi scheme. Legitimate investments will typically provide detailed information and documentation, including the associated risks, which Ponzi schemes often lack. Moreover, if you're facing aggressive tactics to invest or a sense of urgency to commit funds, be wary.
Another red flag is if the investment is not registered with financial regulatory authorities. Unregistered investments might indicate that the scheme is operating outside the scrutiny of regulatory bodies, making it easier for fraudsters to operate undetected. It's essential to check whether the investment and its operators are properly registered with the appropriate agencies.
Famous Ponzi Schemes
The Original Ponzi Scheme: Charles Ponzi
Charles Ponzi, the namesake of the scheme, promised investors a 50% return within 45 days in the early 20th century. He claimed to exploit price discrepancies in international reply coupons used for overseas postage. However, Ponzi was paying returns using the capital from new investors. His scheme collapsed within a year, causing massive financial losses for investors and catapulting Ponzi into infamy.
Bernie Madoff's Ponzi Scheme
Bernie Madoff's Ponzi scheme, one of the largest in history, serves as a stark reminder of how these scams can persist over time. Madoff, a respected financier and former chairman of NASDAQ, exploited his reputation to attract a vast number of investors. He convinced them that he was using a sophisticated investment strategy called the "split-strike conversion strategy," which he claimed would consistently generate profits. However, no such strategy was in place, and the returns were simply the result of new investors' capital being used to pay earlier investors.
Madoff's scheme ran for decades, defrauding thousands of individuals, charities, and other entities before its collapse during the 2008 financial crisis. The scale of the fraud was unprecedented, and the fallout was immense, with many investors losing their entire life savings and Madoff being sentenced to 150 years in prison.
OneCoin
OneCoin is an example of a modern Ponzi scheme that capitalized on the cryptocurrency craze. Founded by Ruja Ignatova, OneCoin masqueraded as a new cryptocurrency that would rival Bitcoin. Investors were promised big returns and were persuaded to buy educational material and tokens for a currency that, in reality, had no blockchain or true value. The scheme was marketed globally, with persuasive rhetoric and grand events to create an illusion of legitimacy and growth.
The scheme collapsed after investigations revealed the fraudulent nature of OneCoin, leading to arrests and charges for several people involved. However, Ignatova disappeared and remains at large, with the lost funds estimated to be in the billions.
Enron
Enron's case is often cited alongside Ponzi schemes due to the similar deceptive practices used to defraud investors. The company was a titan in the energy sector and was lauded for its innovation and financial performance. However, the reality was that Enron's success was built on an elaborate web of accounting loopholes and poor financial reporting, which allowed the company to hide its mounting debt and failures from investors and regulators.
When the truth about Enron's finances came to light, the company's stock price plummeted, leading to its bankruptcy and the loss of billions of dollars for investors. The scandal resulted in significant reforms in accounting and corporate governance regulations, including the passage of the Sarbanes-Oxley Act.
Why Do Ponzi Schemes Fail?
Ponzi schemes, despite their initial allure and seemingly profitable returns, are destined to fail. The collapse of a Ponzi scheme is inevitable due to its inherent flaws and unsustainable structure. Let’s delve into the reasons behind the failure of Ponzi schemes and understand the mechanics that lead to their downfall.
Reliance on New Investments
The fundamental flaw in a Ponzi scheme is its reliance on new investments to pay returns to earlier investors. This creates a perpetual need for new investors to sustain the scheme and ensure that returns can be paid to existing participants.
Exponential Growth is Impossible
For a Ponzi scheme to continue indefinitely, it would require exponential growth in the number of new investors. However, exponential growth is practically impossible to maintain, and eventually, the scheme struggles to attract enough new capital to meet its obligations.
Increasing Financial Obligations
As the scheme grows, the financial obligations to existing investors also escalate. The returns promised to investors are not generated from profitable business activities but are instead derived from the capital of new investors, creating a financial deficit that widens as the scheme expands.
Loss of Trust
Once investors begin to suspect the legitimacy of the scheme, trust erodes, and they may start withdrawing their investments. This loss of trust can trigger a cascade of withdrawals, causing the scheme to collapse as it becomes impossible to pay the promised returns.
Regulatory Intervention
Ponzi schemes often come under scrutiny from regulatory bodies. Once irregularities are detected, regulatory bodies may intervene, shutting down the scheme and potentially prosecuting the perpetrators.
Protecting Yourself from Ponzi Schemes
Investing wisely means doing your due diligence before committing any funds. Ask for detailed information about the investment, including how the returns are generated, and insist on receiving official documentation. An independent financial advisor can provide a second opinion and help assess the legitimacy of the investment.
Remaining skeptical about investments that offer guarantees of high returns is crucial. High returns typically come with high risks, and any legitimate financial advisor will be upfront about this reality. Additionally, if you feel pressured to make an investment decision quickly, it's wise to step back and consider why such urgency is necessary.
Finally, verify that the investment and its promoters are registered with the appropriate financial regulatory bodies. Regulatory agencies offer tools and resources to check the registration status of investments and the individuals or firms offering them.
Red Flags and Warning Signs
- Guaranteed High Returns: Be wary of investments promising high returns with no risk. High returns typically come with high risks.
- Overly Consistent Returns: Investments that yield consistently positive returns despite market fluctuations warrant scrutiny.
- Complex Strategies: If the investment strategy is unclear or too complex to understand, it might be a cover for fraudulent activities.
- Unregistered Investments: Legitimate investments are often registered with regulatory bodies. Ensure to verify their authenticity.
- Issues with Payments: Delays in receiving returns or difficulties in withdrawing your money are glaring red flags.
Preventive Measures to Shield Against Ponzi Schemes
- Research and Verification: Before investing, conduct thorough research and verify the legitimacy of the investment opportunity and the entities involved.
- Seek Professional Advice: Engage with financial advisors to evaluate the viability and legitimacy of the investment.
- Diversify Investments: Avoid putting all your eggs in one basket. Diversifying investments can mitigate potential risks.
- Be Skeptical: Adopt a skeptical approach towards offers that seem too lucrative and question the feasibility of the promised returns.
- Report Suspicious Activities: If you encounter or are approached by a potential Ponzi scheme, report it to regulatory authorities.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
Conclusion
Ponzi schemes are sophisticated frauds that can operate under the guise of legitimate investment opportunities. They rely on a constant influx of new investors to pay returns to earlier ones, creating an illusion of a successful business. However, these schemes are destined to fail, leaving many investors with significant financial losses.
FinCense, developed by Tookitaki, represents a revolutionary approach to combating financial crime, including Ponzi schemes. The solution is powered by a tech-enabled community platform that connects financial experts across various sectors, promoting collaboration to enhance the prevention and protection against financial crimes. To learn more about the capabilities of our solution, schedule a slot with one of our experts.
DoS Attacks
Introduction
In the ever-evolving field of cybersecurity, understanding potential threats is the first line of defence. One such threat that has caused significant disruptions over the years is the Denial-of-Service (DoS) attack. This type of cyber-attack seeks to make a computer, network, or service unavailable to its intended users by overwhelming the target's resources.
Key Takeaways
- Denial-of-Service (DoS) attacks are cyber threats aiming to render a network, system, or machine unavailable by overwhelming it with traffic or exploiting system vulnerabilities.
- DoS attacks can be broadly classified into volume-based attacks, protocol attacks, application layer attacks, and Advanced Persistent DoS (APDoS).
- Notable DoS attacks, such as those against Dyn and GitHub, have caused significant disruption to major internet platforms and services.
- Strategies to mitigate DoS attacks include adopting redundancy, leveraging DoS protection services, staying updated with patches and system upgrades, and incorporating Intrusion Prevention Systems (IPS).
What Is a Denial-of-Service (DoS) Attack?
A Denial-of-Service (DoS) attack is a cyber assault in which the attacker seeks to render a network, system, or machine unavailable by overwhelming it with illegitimate requests or traffic, thereby denying legitimate users access. This disruption can range from mild service slowdowns to complete outages, affecting the target's functionality.
How Do DoS Attacks Work?
The fundamental mechanism behind a DoS attack lies in its intent to exhaust the target's resources. This can be achieved in various ways: by flooding the network with traffic to consume all available bandwidth or by sending requests that exploit system vulnerabilities, forcing the target into a state of non-functionality. In most cases, these requests are illegitimate and disguised to appear as normal, further complicating the detection process.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
The Different Types of DoS Attacks
DoS attacks can be classified into several types based on the techniques used. Here are four of the most common ones:
- Volume-Based Attacks: The aim here is to saturate the bandwidth of the targeted site. Examples include ICMP floods and UDP floods.
- Protocol Attacks: These attacks focus on exploiting vulnerabilities in the target's resources, like servers or load balancers. Examples include SYN floods and Ping of Death.
- Application Layer Attacks: These attacks target specific aspects of an application or service. HTTP floods are a common example.
- Advanced Persistent DoS (APDoS): This is a more advanced form of DoS, where the attacker uses multiple attacking systems and different attack vectors.
Notable Examples of DoS Attacks
Understanding real-world scenarios can help contextualize the severity of DoS attacks. Here are a few instances where such attacks caused significant disruption:
- The Dyn Attack: In October 2016, the Domain Name System (DNS) provider Dyn was hit by a massive DoS attack that caused major internet platforms and services to be unavailable to users across Europe and North America.
- The GitHub Attack: In 2018, GitHub, a popular platform for software developers, experienced a DoS attack that momentarily disrupted its service.
{{cta('54d94e33-111d-4863-bfa1-067a6d3c59ff','justifycenter')}}
Mitigating the Threat of DoS Attacks
While DoS attacks can be challenging to counteract due to their versatility and complexity, certain strategies can help mitigate the potential damage:
- Adopt Redundancy: By spreading resources across multiple systems or geographical locations, you reduce the likelihood of a DoS attack taking down your entire operation.
- Leverage DoS Protection Services: Numerous third-party services specialize in identifying and mitigating DoS attacks. These services typically have advanced traffic filtering capabilities that can differentiate between legitimate and illegitimate traffic.
- Stay Updated: Keeping your systems and software updated is crucial. Regular patches and updates often address known vulnerabilities that could be exploited during a DoS attack.
- Incorporate Intrusion Prevention Systems (IPS): These systems can identify potentially malicious traffic and stop it before it affects your network.
Conclusion
In the era of digital connectivity, cyber threats like Denial-of-Service (DoS) attacks pose significant challenges. Understanding the mechanisms behind these attacks, recognizing their various forms, and knowing how to respond can help organizations protect their systems and data from this enduring cyber menace. As with all cybersecurity efforts, staying informed and prepared is the most effective defence against DoS attacks.
Money Mule
In today's digital age, criminals constantly seek new ways to carry out illegal financial transactions. One method that has gained significant attention is the use of money mules. Money mules play a crucial role in facilitating the movement of illicit funds, often unknowingly becoming a part of criminal networks.
Preventing individuals from becoming unwitting money mules requires educating customers about the risks and promoting customer due diligence. In this article, we will delve into the concept of money mules, their operations, the risks involved, and what you can do to protect yourself from becoming entangled in these illegal activities.
Key Takeaways
- Money mules are individuals who are recruited by criminals to transfer stolen funds or launder money through their bank accounts.
- Money mules are often lured into these activities through deceptive job advertisements, social media, or personal connections.
- Engaging in money mule activities is illegal and can result in severe consequences, including criminal charges and imprisonment.
- Money mules may be caught through various means, including financial institution monitoring, law enforcement investigations, and public awareness campaigns.
- If you suspect that you have become a victim of money laundering or have unknowingly participated as a money mule, it is essential to take immediate action and report the incident to the authorities.
What is a Money Mule?
Money mules are a critical link in the chain of illegal financial transactions, and criminals often target vulnerable individuals who may be unaware of the consequences of their actions. These individuals may be enticed with the promise of easy money or coerced through threats or blackmail. Once recruited, they are instructed to transfer funds through their own bank accounts or other means, which allows the criminals to avoid detection and launder the illicit funds.
Unfortunately, money mules are often left to face the legal consequences of their actions, which can include fines, imprisonment, and a tarnished reputation. It is crucial for individuals to be aware of the risks associated with becoming a money mule and to report any suspicious activity to the authorities. Financial institutions also play a vital role in detecting and preventing money mule activity through robust anti-money laundering measures and enhanced due diligence procedures.
Do Money Mules Get Paid?
Money mules are often enticed by criminals through the offer of a lucrative share of the illicit funds they assist in transferring. These individuals are tempted with the allure of quick and effortless wealth, as their financial vulnerabilities become exploited and false promises are used as bait. The criminals strategically manipulate the money mules by appealing to their desires for financial gain, ultimately ensnaring them in their illegal activities.
What Happens if You Are a Money Mule?
Becoming a money mule may seem like an easy way to make some quick cash, but the consequences can be severe. If you unknowingly participate in money laundering and other illegal activities, you are putting yourself at risk of criminal charges, imprisonment, and financial penalties. It is crucial to understand that pleading ignorance of the illegal nature of your actions will not protect you from legal repercussions.
You could end up with a criminal record that will follow you for the rest of your life, affecting your future job prospects and personal relationships. Don't let greed blind you to the potential dangers of becoming a money mule. Stay vigilant and always verify the legitimacy of any financial transactions you are involved in.
How Do Money Mules Get Caught?
Law enforcement agencies and financial institutions employ various techniques to detect and apprehend money mules. These include sophisticated monitoring systems, transaction analysis, and collaboration between international authorities. Unusual financial activities, large cash deposits or transfers, and patterns that match typical money mule behaviour can raise red flags and trigger investigations.
Victim of Money Laundering: What to Do
If you suspect that you have become a victim of money laundering or if you unknowingly participated in illegal activities as a money mule, it is crucial to take immediate action. Contact your local law enforcement authorities and provide them with all the relevant information and evidence. Cooperate fully with the investigation and seek legal advice to protect your rights and mitigate any potential legal consequences. Remember, reporting the crime is essential for stopping illicit financial activities and safeguarding yourself from further harm.
Protecting Oneself and Taking Action
Recognizing and Avoiding Money Mule Recruitment
To protect oneself from becoming involved in money mule activities, it is crucial to be vigilant and informed. Recognizing the signs of recruitment tactics, such as unsolicited job offers, requests to use personal bank accounts for transactions or promises of easy money, can help individuals avoid falling into the trap. Being cautious about sharing personal information online and maintaining a healthy scepticism towards offers that seem too good to be true can significantly reduce the risk of becoming a money mule.
Reporting Suspicious Activities
If you suspect that you or someone you know may be involved in money mule activities, it is essential to report the situation to the appropriate authorities. Contact your local law enforcement agency or financial institution to provide them with the necessary information and evidence. By reporting suspicious activities, you can help law enforcement agencies disrupt money mule networks, protect others from falling victim, and contribute to the fight against financial crime.
Seeking Support and Assistance
If you have been victimized or inadvertently become involved in money mule activities, it is crucial to seek support and assistance. Reach out to local support organizations, helplines, or legal professionals who can provide guidance and help you navigate through the situation. Remember, you are not alone, and there are resources available to help you break free from the cycle of illegal activities and move towards a brighter and more secure future.
Detecting and Combating Money Mule Activities
Identifying Money Mule Patterns
Detecting money mule activities requires a combination of advanced technology, data analysis, and vigilant financial institutions. By monitoring transaction patterns, anomalies, and red flags, banks and law enforcement agencies can identify potential money mule operations. Key indicators include frequent large cash deposits or withdrawals, multiple transactions to unrelated accounts, and transfers to high-risk countries. By analyzing these patterns and establishing effective risk-based detection systems, financial institutions can play a vital role in preventing money mule activities.
Collaborative Efforts and Information Sharing
Combating money mule activities requires collaboration and information sharing among financial institutions, law enforcement agencies, and regulatory bodies. By exchanging intelligence and sharing best practices, stakeholders can stay ahead of evolving money mule tactics and networks. International cooperation is particularly crucial, given the global nature of these illicit operations. Collaborative initiatives, such as the Egmont Group, facilitate the exchange of financial intelligence and foster joint efforts to combat money mule activities on a global scale.
Public Awareness and Education
Raising public awareness about the risks and consequences of becoming involved in money mule activities is an essential component of prevention. Educational campaigns can provide information about the recruitment tactics used by criminals, the legal implications, and the impact on individuals and society. By promoting financial literacy and teaching individuals how to recognize and avoid falling victim to money mule schemes, we can empower the public to protect themselves and report suspicious activities to the relevant authorities.
Conclusion
You can protect yourself and others from falling victim to the illegal activities of money mules. It is important to remain alert and vigilant, being cautious of any job offers or promises of easy money that seem too good to be true. By reporting any suspicious activity to law enforcement agencies or financial institutions, you can help disrupt money mule networks and contribute to the fight against financial crime.
It is also crucial to seek support and assistance if you have been victimized or inadvertently become involved in money mule activities. Remember, by taking these steps, you are not only protecting yourself but also helping to safeguard the integrity of the financial system. Let's work together to combat money laundering and keep our communities safe.
Deepfake Scams
What Are Deepfake Scams?
Deepfake scams are a new breed of fraud where criminals use artificial intelligence (AI) to create fake videos, voices, or images that mimic real people. These fakes are so convincing that they can impersonate CEOs, loved ones, or even public officials — in real-time or through recorded content, to deceive and defraud victims.
Unlike phishing emails or traditional spoofing, deepfake scams attack what we trust most: faces, voices, and human presence.
It’s not just about tricking the mind — it’s about tricking the senses.
Why Deepfakes Work So Well
Deepfakes hijack our most basic trust instincts. When we see someone’s face or hear their voice, our brain assumes it’s authentic — especially if it comes from a familiar source. Scammers exploit this trust to push people into high-stakes decisions, like transferring funds or sharing sensitive data.
Here’s how they do it:
- Visual Authority: “You saw the CFO in the video — it must be real.”
- Vocal Familiarity: “That voice sounded just like my boss.”
- Contextual Deception: “The call was about our M&A — only insiders would know that.”
Deepfake scams aren’t just clever. They’re contextual, immersive, and dangerously persuasive.
Common Types of Deepfake Scams
1. Executive Deepfake Scam
A finance team receives a video call or voice message from what looks and sounds like their CEO or CFO, requesting an urgent fund transfer. But it’s an AI-generated impersonation designed to bypass verification checks.
2. Voice Cloning Fraud
A scammer records a few seconds of someone’s voice (often found online) and uses AI to generate a full conversation. Victims receive a call or voicemail that sounds exactly like someone they trust — asking them to act fast.
3. Celebrity Endorsement Scams
Deepfake videos of famous personalities are used to promote fake investment platforms, often on social media. Victims are lured in by the familiar face and voice, unaware the entire endorsement is AI-generated.
4. Romance Scams Using Deepfakes
Scammers create highly realistic fake profiles using AI-generated images and voices. Victims are drawn into emotional relationships through chats, voicemails, or even pre-recorded video messages, and eventually convinced to send money.
5. Fake Job Interviews and HR Scams
Impersonating recruiters or executives using deepfake video/voice, scammers conduct fake interviews to collect personal information or trick victims into paying for fake onboarding services.
6. KYC and Onboarding Fraud
Synthetic identities — built using deepfaked selfies, documents, and live videos — are used to bypass video KYC and open accounts at banks, fintech platforms, or exchanges.
7. Legal and Inheritance Fraud
Victims are contacted by fake “lawyers” or “government officials” through deepfaked video calls or voice notes, claiming an inheritance or legal matter is pending — but upfront payments or processing fees are required.
Real-World Example
In 2025, a finance director at a multinational company authorised a US$499,000 payment during a video call with what appeared to be senior executives. The Zoom call looked and sounded authentic — but the entire meeting was fake, powered by deepfake avatars of the CFO and other leaders. By the time the fraud was discovered, the money was gone.
Red Flags: How to Spot a Deepfake Scam
- A video or voice message feels real but comes with urgent financial requests
- Lip movements don’t match speech perfectly in video calls
- Visuals look “too smooth” or robotic in low light
- “Executives” insist on secrecy or bypassing standard approval flows
- Unusual payment instructions from known contacts or sudden account changes
Protecting Yourself and Your Organisation
For Individuals:
- Always verify high-value requests using a known, secure channel
- Don’t assume video calls are proof of identity — confirm separately
- Avoid sharing personal audio or video publicly if possible
- Use multi-factor authentication and account limits
- Report suspicious calls, videos, or messages immediately
For Financial Institutions:
- Implement real-time behavioural analytics to detect unusual patterns
- Train staff, especially finance and operations, on deepfake red flags
- Enforce strict multi-person approvals for large payments
- Use deepfake detection software during KYC and onboarding
- Collaborate across the industry through shared threat intelligence
Conclusion: Fighting Fraud in the Age of Synthetic Reality
Deepfake scams represent a dangerous leap in the evolution of financial crime. They don’t just trick systems — they exploit people, emotions, and perception. And they’re getting more convincing by the day.
That’s why the future of fraud detection must be smarter, faster, and collective.
Tookitaki’s FinCense platform is purpose-built to stay ahead of this shift.
How FinCense Helps:
- Typology-Driven Detection: Flags patterns typical of deepfake scams, like urgent transfers, high-value requests, and synthetic identities
- Federated Intelligence: Continuously updated with real-world scenarios from global institutions via the AFC Ecosystem
- AI Simulation & Testing: Allows institutions to simulate deepfake scenarios and stress-test their controls
- Smart Case Narration: Helps compliance officers detect and respond quickly to unusual events using contextual insights
When identity can be faked and fraud moves at the speed of AI, detection can’t afford to be reactive.
It needs to be intelligent, collaborative, and relentless.
Because in the world of deepfake scams, even the most familiar face might be a fraud.
Digital Banking Fraud
In recent years, digital banking has become an increasingly popular way for individuals and businesses to manage their finances. With the convenience of online banking, however, comes the risk of digital bank fraud. Criminals are constantly finding new ways to exploit vulnerabilities in digital banking systems, making it crucial for individuals and institutions to be aware of the different types of digital bank fraud and how to prevent them.
How do Digital Bank Frauds Happen?
Digital bank fraud occurs when criminals gain unauthorized access to personal or financial information through various means. One common method is through phishing emails, where fraudsters pose as legitimate institutions and request sensitive information, such as login credentials, from unsuspecting victims. These emails often appear convincing, prompting recipients to click on disguised links or attachments that initiate the fraud.
Another way digital bank fraud occurs is through malware, a type of malicious software that can infiltrate computers or mobile devices. Once installed, malware can record keystrokes, capture login credentials, and access sensitive information without the user's knowledge or consent. Fraudsters can also intercept communication between users and financial institutions, gaining access to login information or transaction details.
{{cta('4129950d-ed17-432f-97ed-5cc211f91c7d','justifycenter')}}
Furthermore, digital bank fraud can also take place through social engineering tactics, where scammers manipulate individuals into divulging confidential information. This can happen through phone calls, text messages, or even social media interactions, where fraudsters use psychological manipulation to trick victims into sharing sensitive data.
Additionally, digital bank fraudsters may exploit vulnerabilities in online banking systems or mobile applications to gain unauthorized access to accounts. They can use techniques such as session hijacking or cross-site scripting to bypass security measures and steal sensitive information or initiate fraudulent transactions.
Types of Digital Bank Frauds
There are several different types of digital bank fraud, each with its unique tactics and objectives. Understanding these types can help individuals and institutions identify potential threats and take appropriate preventive measures.
Let's dive deeper into the world of digital bank fraud and explore a couple more types that can pose a significant risk to your financial security.
Credit Card Fraud
Credit card fraud occurs when unauthorized transactions are made using someone else's credit card information. This can happen through various channels, such as skimmed card data, stolen or lost cards, or online purchases made with stolen card details.
Identity Theft
Identity theft is another common form of digital bank fraud. In this scenario, criminals steal personal information, such as social security numbers or dates of birth, to assume someone else's identity. Once the fraudsters have this information, they can open fraudulent bank accounts, apply for loans, or perform other illicit financial activities.
Phishing Attacks
Phishing attacks involve fraudsters using deceptive tactics, such as emails or text messages, to trick individuals into revealing their personal or financial information. These messages often appear to be from a legitimate source, such as a bank or payment provider, and prompt recipients to click on a link or enter their credentials on a fake website.
Account Takeover
In an account takeover, fraudsters gain access to a victim's online banking account and take control of their funds. They may use various methods, such as credential stuffing or brute force attacks, to guess or obtain login credentials. Once they have control, they can transfer funds, make unauthorized purchases, or change the account information.
Now that we have covered the previously mentioned types of digital bank fraud, let's explore two additional types that are becoming increasingly prevalent in today's digital landscape.
Mobile Banking Fraud
With the rise of smartphones and mobile banking apps, fraudsters have adapted their tactics to target users on these platforms. Mobile banking fraud can involve malware-infected apps, fake banking apps, or even SIM card swapping. These methods allow fraudsters to gain unauthorized access to your mobile banking account, compromising your financial security.
Ransomware Attacks
Ransomware attacks have become a significant threat to both individuals and financial institutions. In these attacks, fraudsters use malicious software to encrypt a victim's files or lock them out of their devices. They then demand a ransom in exchange for restoring access. If successful, these attacks can disrupt banking operations, compromise customer data, and cause significant financial losses.
By familiarizing yourself with these additional types of digital bank fraud, you can stay one step ahead of the fraudsters and protect your financial well-being. Remember to always be vigilant, regularly monitor your accounts, and report any suspicious activity to your bank immediately.
Risks and Challenges
Digital bank fraud poses significant risks to individuals and financial institutions alike. For individuals, falling victim to fraud can result in financial losses, damage to credit scores, and potential legal implications. Financial institutions face reputational damage, regulatory scrutiny, and financial liabilities if they fail to implement adequate security measures.
One of the key challenges in combating digital bank fraud is the ever-evolving tactics employed by fraudsters. As technology advances, fraudsters adapt their techniques to exploit new vulnerabilities and bypass existing security measures. This requires individuals and institutions to stay vigilant, continuously update their security systems, and educate themselves on the latest threats.
Moreover, the rise of digital banking and online transactions has created a borderless environment for fraudsters to operate in. With the global nature of the internet, fraudsters can launch attacks from anywhere in the world, making it difficult for law enforcement agencies to track and apprehend them. This international aspect of digital bank fraud adds another layer of complexity to combating this type of crime.
Additionally, the increasing interconnectedness of devices through the Internet of Things (IoT) has opened up new avenues for fraudsters to exploit. Hackers can target not only traditional banking systems but also interconnected smart devices, such as wearables and home appliances, to gain access to personal information and financial data. This expanding attack surface requires a holistic approach to security that encompasses not just banking systems but all connected devices to mitigate the risks effectively.
Compliance to Prevent Digital Bank Frauds
To mitigate the risks of digital bank fraud, financial institutions are subject to various compliance regulations and guidelines. These measures help ensure that institutions have robust security measures in place to protect customers' personal and financial information.
Compliance may include implementing multi-factor authentication, encrypting sensitive data, monitoring and detecting suspicious activities, and adhering to industry best practices in customer authentication and fraud prevention.
One crucial aspect of compliance in preventing digital bank fraud is the regular training and education of employees. Financial institutions invest in educating their staff about the latest fraud tactics, cybersecurity threats, and compliance requirements. This ongoing training helps employees stay vigilant and informed, enabling them to identify and respond to potential fraud attempts effectively.
Moreover, compliance also involves conducting regular security assessments and audits to evaluate the effectiveness of existing fraud prevention measures. These assessments often include penetration testing, vulnerability scans, and security audits to identify weaknesses in the system and address them promptly. By proactively assessing security controls, financial institutions can strengthen their defenses against evolving fraud schemes and cyber threats.
Aftermath of a Digital Bank Fraud
Experiencing a digital bank fraud can be a traumatic and disorienting experience. Victims may face financial hardships, emotional distress, and difficulties in restoring their stolen identities or recovering lost funds.
Financial institutions also bear some responsibility in assisting customers affected by digital bank fraud. They typically have protocols in place to investigate fraudulent activities, reimburse victims for unauthorized transactions, and support them in recovering their accounts and rebuilding their trust in the banking system.
Moreover, the impact of digital bank fraud extends beyond just the immediate financial loss. Victims often find themselves grappling with feelings of violation and vulnerability, knowing that their personal information has been compromised. The sense of betrayal by cybercriminals can linger long after the fraud has been discovered and rectified.
In response to the rising threat of digital bank fraud, financial institutions are constantly updating their security measures and investing in advanced technologies to detect and prevent fraudulent activities. This ongoing battle between cybercriminals and banks has led to the development of sophisticated fraud detection algorithms and real-time monitoring systems to safeguard customers' accounts.
{{cta('c2265f53-7251-4b3c-91d7-20ef8707a8f3','justifycenter')}}
How can Tookitaki help?
Tookitaki is a leading provider of Anti-Money Laundering (AML) and Fraud Prevention solutions for financial institutions. Using advanced machine learning algorithms and artificial intelligence, Tookitaki helps banks and other financial organizations detect and prevent digital bank fraud.
Their solutions enable proactive monitoring of customer transactions, identification of suspicious patterns, and real-time fraud alerts. By leveraging data analytics and automation, Tookitaki empowers financial institutions to stay ahead of fraudsters and minimize the risks associated with digital bank fraud.
Furthermore, Tookitaki's platform is designed to adapt and evolve with the changing landscape of financial crime. The system continuously learns from new data and trends, enhancing its ability to detect emerging fraud patterns and schemes. This proactive approach ensures that financial institutions are equipped with the most up-to-date tools to combat digital bank fraud effectively.
In conclusion, digital banking fraud is a prevalent and evolving threat that individuals and institutions must take seriously. By understanding the different types of digital bank fraud, implementing robust security measures, and leveraging advanced technology solutions like those offered by Tookitaki, individuals and financial institutions can safeguard themselves against the risks and challenges of digital bank fraud.
Don't let the threat of digital banking fraud undermine your financial security or the integrity of your financial institution. With Tookitaki's FinCense, you can harness the power of an end-to-end operating system designed for the detection and prevention of financial crimes. Our innovative federated learning model, integrated with the AFC Ecosystem, offers a collaborative approach to identifying unique financial crime attacks. Talk to our experts today and stay one step ahead of digital bank fraud.

